A few handy queries to ask Active Directory
I just wanted to do a random DS related post .
These are a few useful constructed attributes. A constructed attribute is one which is not directly stored in the AD, but is constructed specifically when requested. More info on MSDN I'm sure..
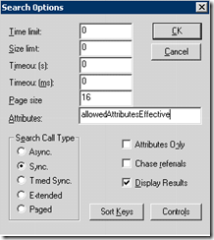
Some useful ones are … AllowedAttributesEffective, msds-replvaluemetadata, and Tokengroups
In the schema they are defined as:
CN=Allowed-Attributes-Effective,CN=Schema,CN=Configuration
CN=ms-DS-Repl-Value-Meta-Data,CN=Schema,CN=Configuration
CN=Token-Groups,CN=Schema,CN=Configuration
Note the systemFlags - FLAG_ATTR_IS_CONSTRUCTED
Getting 1 entries:
>> Dn: CN=Allowed-Attributes-Effective,CN=Schema,CN=Configuration,DC=rlo,DC=local
2> objectClass: top; attributeSchema;
1> cn: Allowed-Attributes-Effective;
1> distinguishedName: CN=Allowed-Attributes-Effective,CN=Schema,CN=Configuration,DC=rlo,DC=local;
1> instanceType: 0x4 = ( IT_WRITE );
1> whenCreated: 11/09/2005 15:42:30 Pacific Standard Time Pacific Daylight Time;
1> whenChanged: 07/19/2007 10:50:06 Pacific Standard Time Pacific Daylight Time;
1> uSNCreated: 4162;
1> attributeID: 1.2.840.113556.1.4.914;
1> attributeSyntax: 2.5.5.2;
1> isSingleValued: FALSE;
1> uSNChanged: 4162;
1> showInAdvancedViewOnly: TRUE;
1> adminDisplayName: Allowed-Attributes-Effective;
1> adminDescription: Allowed-Attributes-Effective;
1> oMSyntax: 6;
1> searchFlags: 0;
1> lDAPDisplayName: allowedAttributesEffective;
1> name: Allowed-Attributes-Effective;
1> objectGUID: fb7fa1c4-1719-480e-a9fa-80f640985afe;
1> schemaIDGUID: 9a7ad941-ca53-11d1-bbd0-0080c76670c0;
1> attributeSecurityGUID: e48d0154-bcf8-11d1-8702-00c04fb96050;
1> systemOnly: TRUE;
1> systemFlags: 0x8000014 = ( FLAG_ATTR_IS_CONSTRUCTED | FLAG_SCHEMA_BASE_OBJECT | FLAG_DOMAIN_DISALLOW_RENAME );
1> objectCategory: CN=Attribute-Schema,CN=Schema,CN=Configuration,DC=rlo,DC=local;
CN=Allowed-Attributes-Effective,CN=Schema,CN=Configuration
This one will tell you what attributes on an object you can modify, under whatever security context you query as.
Here I am logged on as Admin – and query the Cert Publishers object to see what I can do to it.
As you can see – I can pretty much modify anything.. as admin.
***Searching...
ldap_search_s(ld, "CN=Cert Publishers,CN=Users,DC=rlo,DC=local", 2, "(objectCategory=*)", attrList, 0, &msg)
Result <0>: (null)
Matched DNs:
Getting 1 entries:
>> Dn: CN=Cert Publishers,CN=Users,DC=rlo,DC=local
92> allowedAttributesEffective: proxiedObjectName; accountNameHistory; dSCorePropagationData; otherWellKnownObjects; mS-DS-ConsistencyGuid; mS-DS-ConsistencyChildCount; uSNSource; msDS-AzLDAPQuery; msDS-NonMembers; isCriticalSystemObject; altSecurityIdentities; unixUserPassword; userSMIMECertificate; lastKnownParent; url; partialAttributeDeletionList; legacyExchangeDN; textEncodedORAddress; managedBy; userCert; showInAddressBook; partialAttributeSet; mail; wellKnownObjects; sIDHistory; secretary; labeledURI; nonSecurityMember; msSFU30Name; msSFU30NisDomain; systemFlags; fSMORoleOwner; desktopProfile; sAMAccountType; wbemPath; controlAccessRights; groupMembershipSAM; rid; groupAttributes; adminCount; revision; operatorCount; supplementalCredentials; securityIdentifier; nTGroupMembers; flags; replUpToDateVector; replPropertyMetaData; objectGUID; name; msExchLabeledURI; USNIntersite; wWWHomePage; msExchAssistantName; msSFU30PosixMember; displayNamePrintable; garbageCollPeriod; uSNDSALastObjRemoved; extensionName; adminDescription; proxyAddresses; adminDisplayName; showInAdvancedViewOnly; uSNLastObjRem; uSNChanged; gidNumber; memberUid; repsFrom; repsTo; info; objectVersion; dSASignature; isDeleted; uSNCreated; displayName; subRefs; whenChanged; whenCreated; distinguishedName; userCertificate; userPassword; member; telephoneNumber; description; objectCategory; groupType; sAMAccountName; objectSid; nTSecurityDescriptor; instanceType; cn; objectClass;
-----------
A code snip of how to use this is here - https://msdn2.microsoft.com/en-us/library/aa814512.aspx
CN=ms-DS-Repl-Value-Meta-Data,CN=Schema,CN=Configuration
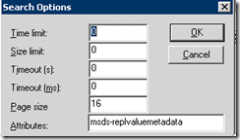
This one will dump the metadata of the object in XML:
Below is the output..
***Searching...
ldap_search_s(ld, "CN=Cert Publishers,CN=Users,DC=rlo,DC=local", 2, "(objectCategory=*)", attrList, 0, &msg)
Result <0>: (null)
Matched DNs:
Getting 1 entries:
>> Dn: CN=Cert Publishers,CN=Users,DC=rlo,DC=local
1> msDS-ReplValueMetaData: <DS_REPL_VALUE_META_DATA>
<pszAttributeName>member</pszAttributeName>
<pszObjectDn>CN=SAMME342B,OU=Domain Controllers,DC=rlo,DC=local</pszObjectDn>
<cbData>0</cbData>
<pbData></pbData>
<ftimeDeleted>1601-01-01T00:00:00Z</ftimeDeleted>
<ftimeCreated>2007-07-19T17:46:02Z</ftimeCreated>
<dwVersion>0</dwVersion>
<ftimeLastOriginatingChange>1601-01-01T00:00:00Z</ftimeLastOriginatingChange>
<uuidLastOriginatingDsaInvocationID>00000000-0000-0000-0000-000000000000</uuidLastOriginatingDsaInvocationID>
<usnOriginatingChange>0</usnOriginatingChange>
<usnLocalChange>0</usnLocalChange>
<pszLastOriginatingDsaDN></pszLastOriginatingDsaDN>
</DS_REPL_VALUE_META_DATA>
;
-----------
CN=Token-Groups,CN=Schema,CN=Configuration
This one will tell you what groups a user belongs to, including nested groups.
**Searching...
ldap_search_s(ld, "CN=Administrator,CN=Users,DC=rlo,DC=local", 0, "(objectCategory=*)", attrList, 0, &msg)
Result <0>: (null)
Matched DNs:
Getting 1 entries:
>> Dn: CN=Administrator,CN=Users,DC=rlo,DC=local
9> tokenGroups: S-1-5-32-545; S-1-5-32-544;
S-1-5-21-140114927-3003004965-4151461519-1616;
S-1-5-21-140114927-3003004965-4151461519-518;
S-1-5-21-140114927-3003004965-4151461519-519;
S-1-5-21-140114927-3003004965-4151461519-1112;
S-1-5-21-140114927-3003004965-4151461519-513;
S-1-5-21-140114927-3003004965-4151461519-512;
S-1-5-21-140114927-3003004965-4151461519-520;
-----------
This is demonstrated here - https://support.microsoft.com/kb/301916
TokenGroupsGlobalAndUniversal is another:
PS C:\Users\Administrator> get-aduser -filter "*" -SearchBase "CN=Administrator,CN=Users,DC=Contoso,DC=com" -SearchScope Base -Properties TokenGroupsGlobalAndUniversal
DistinguishedName : CN=Administrator,CN=Users,DC=EXADV-0895dom,DC=extest,DC=microsoft,DC=com
Enabled : True
GivenName :
Name : Administrator
ObjectClass : user
ObjectGUID : d84e4582-817d-4662-badd-b38eaebe109a
SamAccountName : Administrator
SID : S-1-5-21-4111566290-1971504540-1066735773-500
Surname :
TokenGroupsGlobalAndUniversal : {S-1-5-21-4111566290-1971504540-1066735773-518, S-1-5-21-4111566290-1971504540-1066735773-1109,
S-1-5-21-4111566290-1971504540-1066735773-519, S-1-5-21-4111566290-1971504540-1066735773-520...}
UserPrincipalName : Administrator@contoso.com
Comments
- Anonymous
May 07, 2008
So James has responded back to me on ADAM.