Disabling SSL 3.0 in Lync Server 2013 and Skype for Business Server 2015
If you recently tried to check on a certificate on DigiCert – SSL Certificate Checker (https://www.digicert.com/help/), you may have noticed the following warning:
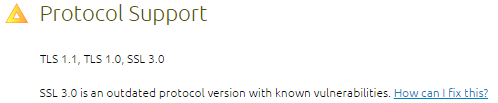
DigiCert added this verification due to a vulnerability that was discovered a few days ago. For more information about this vulnerability, check the following articles:
Vulnerability Summary for CVE-2014-3566
https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-3566
This POODLE bites: exploiting the SSL 3.0 fallback
https://googleonlinesecurity.blogspot.co.uk/2014/10/this-poodle-bites-exploiting-ssl-30.html
Microsoft also released a Security Advisory describing how to disable SSL 3.0 on the client and server side:
Microsoft Security Advisory 3009008
Vulnerability in SSL 3.0 Could Allow Information Disclosure
https://technet.microsoft.com/en-us/library/security/3009008.aspx
This Security Advisory mentions that, in order to disable it in the server, you need to add a key to the registry. To make things easier, here is the command to run on Command Prompt:
reg add "HKLM\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server" /v Enabled /t REG_DWORD /d 0 /f
After changing this, a restart to the Lync Services will be enough to apply the new configuration:
Stop-CsWindowsService
Start-CsWindowsService
Note: If you use ARR for publishing Lync External Web Services, you can also disable SSL 3.0 in those servers with the same command and restart IIS (iisreset).
Finally, you can check it again using the DigiCert – SSL Certificate Checker (https://www.digicert.com/help/):
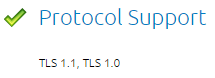
In case you need to rollback, simply remove the key and restart the Lync Services:
reg delete "HKLM\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server" /v Enabled