Azure Log Analytics: Queries, Has the Hostname been changed?
The question was asked, how do you find a Computer using Log Analytics that has had its name changed?
Normally you would find an EventID that contains this by doing a web search or by looking in Eventvwr after trying a name change yourself on a test server. Both methods said that EventID 6011 should be the one, and in my testing that was the case. I could see the name change in Eventvwr.
Event id 6011 is correct: The Netbios name and the DNS name of this machine have been changed from <old name> to <new name>
However when I tried the computer name change myself, Log Analytics didn’t pick this up before or after the machine re-started. I suspect this will be unreliable as the MMA agent isn’t able to send the data before the reboot happens (unless there is an extended period you wait after making the change and re-booting – which I’ve not tested).
However you can see the name change with Heartbeat
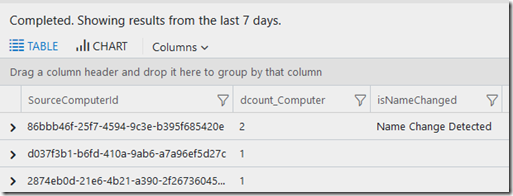
You have to know that every MMA installed creates a SourceComputerId value which is unique to the agent rather than the computer, so if the computer name changes the Id doesn't. We can then look for those, in the Heartbeat records. The easiest way was the summarize the data and use dcount (you can look those up in the help). I then for testing put in some code to limit the results to 1day and to only look for a certain set of named computers (these are commented out in the code below – now that I’m happy the syntax works).
I then used iif to add a column so it was easy to spot the records that matched, and I sorted the data so that any matches were on the top.
Here is the code and a screenshot of the results:
//
// Has the computer name been changed, look for more than one Computer against the SourceComputerID record
//
Heartbeat
//| where TimeGenerated > ago(1d)
//| where Computer startswith "cw"
| summarize dcount(Computer) by SourceComputerId
| extend isNameChanged = iff(dcount_Computer >= 2 , "Name Change Detected","")
| sort by isNameChanged desc
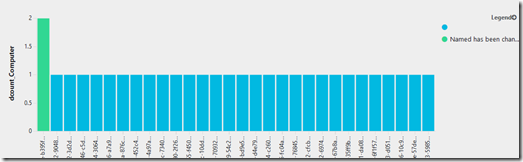
You can also add this line
| render barchart kind=stacked
…as the final line to the code example above, which will graph of the results – if you prefer?
--------------------------------------------------------------------------------------------------
To make this useful and turn this into an Alert (metric alert); please first read https://cloudadministrator.wordpress.com/2018/03/16/using-custom-log-search-alerts-based-on-metric-measurement-for-event-based-logs/
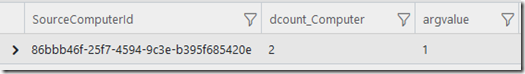
Here is the amended code and screenshot, essentially I used the where operator rather than iif to only show the entries that have 2 or more computer names per SourceComputerId – which is neater than the original code:
Heartbeat
| summarize dcount(Computer) by SourceComputerId
| where dcount_Computer >= 2
| extend argvalue = 1