Getting started with Microsoft Cloud App Security

The October topic for the Enterprise Mobility + Security Partner Community is Microsoft Cloud App Security. Read my introduction to the topic, and sign up for the October 27 community call. In this post, I'll provide a look at the high-level architecture of Cloud App Security and explain how to get started with deployment and usage.
Read my blog post, Introduction to Microsoft Cloud App Security Sign up for the October 27 community call
Architecture
Microsoft Cloud App Security is a component of Microsoft Enterprise Mobility + Security E5, and enables customers to discover and secure all the cloud apps in use within their organizations. Once the apps are discovered, customers can put comprehensive controls in place for management and monitoring. Microsoft Cloud App Security helps you do three things:
- Gain visibility into what cloud applications are being used in your organization today
- Implement data control over those applications
- Leverage ongoing behavioral analytics as a part of the threat protection model
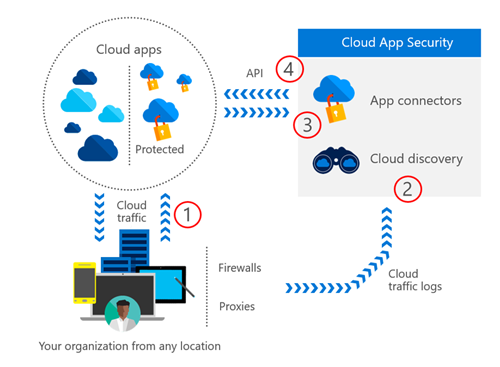
The architecture for how Cloud App Security accomplishes this is shown in the image below. In most cases, Step 1 is already being done. Users are going about their daily work and using cloud apps. Step 2 is where cloud traffic logs are analyzed by Cloud App Security to determine which apps are in use. In Step 3, an administrator reviews the apps, and either sanctions or restricts them. Finally, Step 4 leverages the APIs of the cloud apps to implement connections, controls, and ongoing monitoring for compliance and threat analysis. This process happens as a repeating cycle.
Instructions to activate and set up Cloud App Security portal
Discover
The discovery process starts with uploading the logs from your firewalls and proxies. There are two options for doing the upload: manual or automated. I recommend doing a manual upload before automating the process. This enables you to verify that your log file format is supported and working as expected.
Once you have completed and verified a manual upload, you can automate the process. Automation leverages an on-premises virtual machine to collect the logs and then upload them to Cloud App Security for analysis. Cloud App Security helps you set up a pre-configured virtual machine to deploy into Hyper-V or VMware.
Use these resources and watch the Microsoft Cloud App Security Log Upload video to learn more about the manual and automated log collection process.
Set up Cloud Discovery Completing a manual upload Automating the process Watch this video online
[embed]https://youtu.be/CcAmgQ8dXA8[/embed]
After the log files are uploaded, Cloud App Security will go to work analyzing each app and will assign the risk score based on the 60+ established evaluation criteria. You’ll be able to see those scores on the Cloud Discovery Dashboard. The dashboard gives insight into the number of apps discovered, users, IP addresses, risk levels, app categories, and more. The dashboard also allows you to drill into specific apps, view the risk score, build custom views, and customize how risk scores are calculated. The image below shows you what a list of discovered apps looks like in the portal.
How to use the Cloud Discovery Dashboard 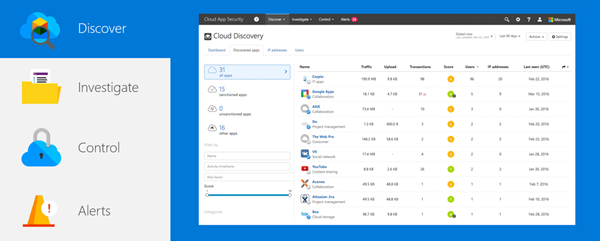
Data retention and privacy
It is important to note that when Cloud App Security performs content inspection, data privacy is enforced. Your data are not stored in the Cloud App Security data base, only the metadata of the file records and the violations that were identified.
Visit the Microsoft Trust Center Review the Microsoft Online Services Privacy Statement
Should you do a proof of concept?
I'm often asked by partners about whether they should have a customer do a proof of concept for Cloud App Security. The intent behind this question is often connected to a discussion about production data versus non-production data. In the case of Cloud App Security, because it is agentless, the recommendation is to use a manual upload of production logs to help the customer view their current list of apps, users, etc. that are being used. Just viewing this data will not impact production users. Impact will start to happen if policies are established.
Investigate
Now that you’ve successfully uploaded data and viewed the dashboard, you can investigate specific apps, how they are being used, and what data may be residing in them. There are several dashboards within the Investigate section of the Cloud App Security portal, such as insights, third-party apps, and files.
To enable deeper investigation of apps you’ll want to connect an app. App connectors leverage the APIs of app providers to enable greater visibility and control by Cloud App Security over the apps you connect to. For a list of apps, you can connect to and connection instructions, visit this site.
Learn more about the Investigate dashboards in this tutorial Learn more about App Connectors for visibility and control 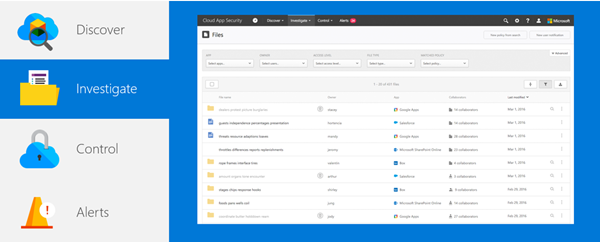
Control
Control is where you implement policies that define the way users and data can function in the cloud. Through the Policy center, seen in the image below, you can detect risky behavior, violations, or suspicious data points and activities in your cloud environment, and if required, to integrate remediation work flows to achieve complete risk mitigation.
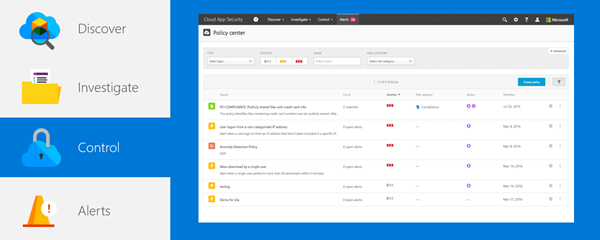
There are multiple types of policies that correlate to the different types of information you want to gather about your cloud environment and the types of remediation actions you may want to take. For example, if there is a data violation threat that you want to quarantine, you will need a different type of policy in place than if you want to block a risky cloud app from being used by your organization. Control also gives you the option to apply governance actions, remediation, and even migrate users to a new app.
Learn more about implementing Control policies Learn more about governance actions and remediation
You can create the following policy types:
| Policy type | Use |
| Activity policy | Activity policies allow you to enforce a wide range of automated processes that utilize the app provider’s APIs. You are able to monitor specific activities carried out by various users, or follow unexpectedly high rates of a certain type of activity. |
| Anomaly detection policy | Anomaly detection policies enable you to look for unusual activities on your cloud based on the risk factors you set here to alert you when something happens that is different from either the baseline of your organization or from the user's regular activity. |
| Cloud Discovery anomaly detection policy | Cloud Discovery anomaly detection policies look at the logs you use for discovering cloud apps and search for unusual occurrences.Examples:
|
| App discovery policy | App discovery policies enable you to set alerts that notify you when new apps are detected within your organization. |
| File policy | File policies enable you to scan your cloud apps for specified files or file types (shared, shared with external domains), data (proprietary information, PII, credit card information, etc.) and apply governance actions to the files (governance actions are cloud-app specific). |
Protect
Once you have everything set up, Cloud App Security enables you to monitor user behavior, policy compliance and enforcement, and more. You’ll find this information under the Alerts tab in the portal.
Get a list of built-in and custom alerts 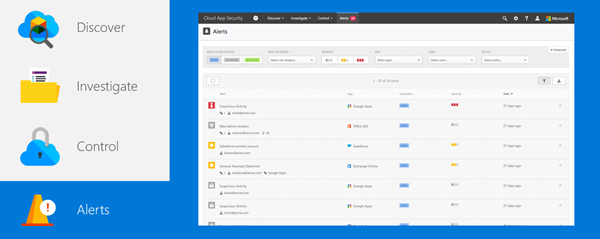
Learn more
[embed]https://youtu.be/RxW0bpXJd9A[/embed]
| Level 100 | Level 200 | Level 300 |
|
Enterprise Mobility + Security (EMS) Partner Community
- Sign up for the October 27 community call
- Blog series
- Community call schedule
- Yammer group
- Training and enablement
Comments about this blog post, or questions about the topic? Let us know in the Enterprise Mobility + Security Partners Yammer group.
Comments
- Anonymous
October 22, 2016
Great article !