Vulnerability in Microsoft Word Could Allow Remote Code Execution
 |
Updates are Now Available: Find these links located on the following Office Update Blog |
As reported, Microsoft is working on a fix to address the recently reported Vulnerability with RTF files in Microsoft Word.
- Microsoft Security Advisory (2953095)
Vulnerability in Microsoft Word Could Allow Remote Code Execution
https://technet.microsoft.com/en-us/security/advisory/2953095
The following Security blog contains some good information about the vulnerability.
- Security Research and Defense Blog:
Blog: Security Advisory 2953095: recommendation to stay protected and for detections
https://blogs.technet.com/b/srd/archive/2014/03/24/security-advisory-2953095-recommendation-to-stay-protected-and-for-detections.aspx
|
Date for Office Patch Microsoft Plans to address this issue with an update on April 8th. The update provided through MS14-017 fully addresses the Microsoft Word issue first described in Security Advisory 2953095. This advisory also included a Fix it to disable opening rich-text format (RTF) files within Microsoft Word. Once the security update is applied, you should disable the Fix it to ensure RTF files will again render normally. At this time, we are still only aware of limited, targeted attacks directed at Microsoft Word 2010. The update will fully address all affected versions. |
Microsoft provides vulnerability information to major security software providers that can then use this information to provide updated protections to customers via their security software or devices, such as antivirus, network-based intrusion detection systems, or host-based intrusion prevention systems. To determine whether active protections are available from security software providers, please visit the active protections websites provided by program partners, listed in Microsoft Active Protections Program (MAPP) Partners .
Mitigation using File Block
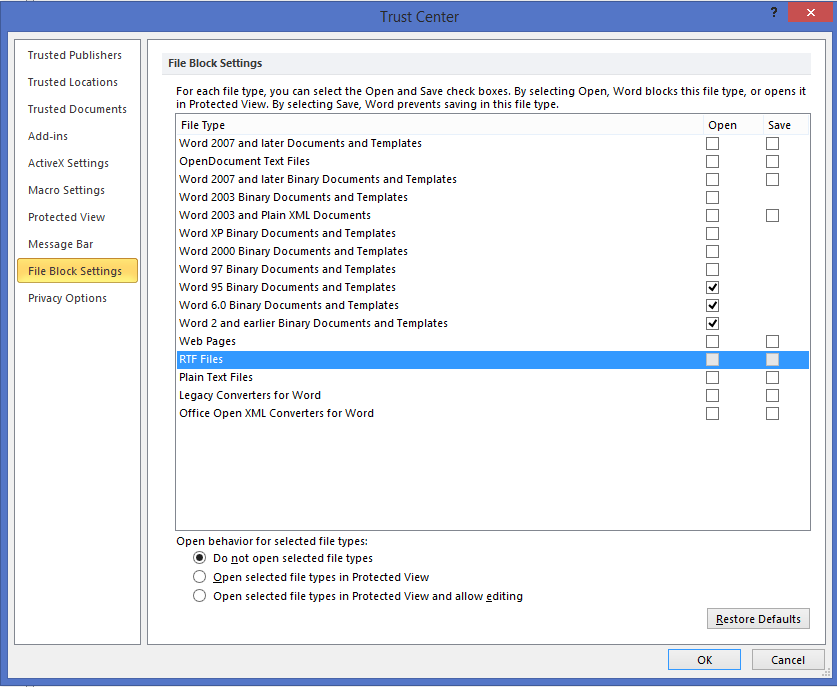
One of the points of mitigation for the Windows versions of Word is to enable the File Block options for the Rich Text Format (RTF). This option is available in the Trust Center for Word 2010 and 2013.
Figure 1: File Block Settings in the Trust Center.
Registry keys for the RTF File Block
The registry keys for 2013 and 2013 are a little different from those for 2003 / 2007. With the later versions, the key has changed to one key from a separate key for Open and Save as in 2003 / 2007.
- Word 2013
HKCU\Software\Microsoft\Office\15.0\Word\Security\FileBlock\RtfFiles
Dword value=2
- Word 2010
[HKCU\Software\Microsoft\Office\14.0\Word\Security\FileBlock\]
"RtfFiles"=dword:00000002
- Word 2007
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Office\12.0\Word\Security\FileOpenBlock]
"RtfFiles"=dword:00000001
- Word 2003
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Office\11.0\Word\Security\FileOpenBlock]
"RtfFiles"=dword:00000001
Deploying using a Group Policy
Here are some various articles around the Administrative templates for the various Office versions and deploying Office keys via a Group Policy.
Available Policy Template Downloads (contains the File Block items)
Group Policy Templates:
Group Policy Administrative Template files (ADMX, ADML) and Office Customization Tool (OCT) files for Office 2013
https://technet.microsoft.com/en-us/library/cc178992.aspxOffice 2010 : Office 2010 Administrative Template files (ADM, ADMX/ADML) and Office Customization Tool download
https://www.microsoft.com/en-us/download/details.aspx?id=18968
2007 Office system Administrative Template files (ADM, ADMX, ADML) and Office Customization Tool version 2.0
https://www.microsoft.com/en-us/download/details.aspx?id=22666
More Information:
-
- Overview of Group Policy for Office 2013
https://technet.microsoft.com/en-us/library/cc179176.aspx
- Overview of Group Policy for Office 2013
-
- Use Group Policy to enforce Office 2010 settings
https://technet.microsoft.com/en-us/library/cc179081(v=office.14).aspx
- Use Group Policy to enforce Office 2010 settings
-
- How administrators can use Office policy templates together with the Group Policy settings of Windows
https://support.microsoft.com/kb/924617
- How administrators can use Office policy templates together with the Group Policy settings of Windows
-
- Use Group Policy Software Installation to deploy the 2007 Office system
https://technet.microsoft.com/en-us/library/cc179214(v=office.12).aspx
- Use Group Policy Software Installation to deploy the 2007 Office system
Macintosh
We do not have any means to mitigate this from the Macintosh environment as we have with the File Block for RTF options that the security advisory discusses. The Macintosh versions do not have this infrastructure for blocking the various file types and instigating Protected View.