Configurer Microsoft Entra ID pour l’authentification client
Avertissement
À ce stade, l’authentification du client Microsoft Entra et le service de jeton d’identité managée sont mutuellement incompatibles sur Linux.
Pour les clusters s’exécutant sur Azure, Microsoft Entra ID est recommandé de sécuriser l’accès aux points de terminaison de gestion. Cet article explique comment configurer Microsoft Entra ID de façon à authentifier les clients pour un cluster Service Fabric.
Sur Linux, vous devez suivre les étapes ci-dessous pour pouvoir créer le cluster. Sur Windows, vous avez également la possibilité de configurer l’authentification Microsoft Entra pour un cluster existant.
Dans cet article, le terme « application » fait référence aux applications Microsoft Entra, et non aux applications Service Fabric ; la distinction est faite si nécessaire. Azure AD permet aux organisation (appelées locataires) de gérer l’accès utilisateur aux applications.
Un cluster Service Fabric offre plusieurs points d’entrée pour ses fonctionnalités de gestion, notamment les outils web Service Fabric Exploreret Visual Studio. Par conséquent, vous allez créer deux applications Microsoft Entra pour contrôler l’accès au cluster : une application web et une application native. Une fois les applications créées, vous affecterez les utilisateurs aux rôles en lecture seule et administrateur.
Remarque
À ce stade, Service Fabric ne prend pas en charge l’authentification Microsoft Entra pour le stockage.
Remarque
Le fait que les applications et les nœuds sur des clusters Microsoft Entra ID Linux ne puissent pas être affichés dans le portail Azure est un problème connu.
Remarque
Azure Active Directory nécessite désormais qu’un domaine d’éditeur d’application (inscription d’application) soit vérifié ou utilise le schéma par défaut. Pour plus d’informations, consultez Configurer un domaine d’éditeur d’application et Dans les applications monolocataires, l’URI AppId nécessite l’utilisation du schéma par défaut ou des domaines vérifiés.
Remarque
L’outil Service Fabric Explorer nécessite, à partir de Service Fabric 11.0, un URI de redirection d’application monopage au lieu d’un URI de redirection web.
Prérequis
Dans cet article, nous partons du principe que vous avez déjà créé un locataire. Si ce n'est pas le cas, commencez par lire Comment obtenir un locataire Microsoft Entra. Pour simplifier certaines des étapes impliquées dans la configuration de Microsoft Entra ID avec un cluster Service Fabric, nous avons créé un ensemble de scripts Windows PowerShell. Certaines actions nécessitent un accès au niveau administratif à Microsoft Entra ID. Si le script rencontre une erreur 401 ou 403 « Authorization_RequestDenied », un administrateur doit exécuter le script.
- Authentifiez-vous à l’aide d’autorisations administratives Azure.
- Clonez le référentiel sur votre ordinateur.
- Assurez-vous d’avoir réuni toutes les conditions préalables pour les scripts installés.
Créer des applications Microsoft Entra et affecter des utilisateurs à des rôles
Nous allons utiliser les scripts pour créer deux applications Microsoft Entra pour contrôler l’accès au cluster : une application web et une application native. Une fois que vous avez créé des applications pour représenter votre cluster, vous allez créer des utilisateurs pour les rôles pris en charge par Service Fabric : lecture seule et administrateur.
SetupApplications.ps1
Exécutez SetupApplications.ps1, puis entrez les paramètres d’ID du locataire, de nom du cluster, d’URI de l’application web et d’URL de réponse de l’application web. Utilisez -remove pour supprimer les inscriptions d’applications. L’utilisation de -logFile <log file path> génère un journal de transcription. Pour plus d’informations, consultez l’aide du script (help .\setupApplications.ps1 -full). Le script crée les applications web et native pour représenter votre cluster Service Fabric. Les deux nouvelles entrées d’inscription d’application sont au format suivant :
- ClusterName_Cluster
- ClusterName_Client
Notes
Pour les clouds nationaux (notamment Azure Government, Microsoft Azure géré par 21Vianet), spécifiez également le paramètre -Location.
Paramètres
tenantId : vous pouvez trouver votre TenantId en exécutant la commande PowerShell
Get-AzureSubscription. L’exécution de cette commande permet d’afficher le TenantId de chaque abonnement.clusterName : ClusterName est utilisé pour préfixer les applications Microsoft Entra créées par le script. Il ne doit pas forcément correspondre précisément au nom du cluster. Il est destiné uniquement à faciliter le mappage des artefacts Microsoft Entra au cluster Service Fabric avec lequel ils sont utilisés.
SpaApplicationReplyUrl : SpaApplicationReplyUrl est le point de terminaison par défaut que Microsoft Entra ID retourne à vos utilisateurs une fois qu’ils se sont connectés. Définissez ce point de terminaison en tant que point de terminaison Service Fabric Explorer de votre cluster. Si vous créez des applications Microsoft Entra pour représenter un cluster existant, vérifiez que cette URL correspond au point de terminaison de votre cluster existant. Si vous créez des applications pour un nouveau cluster, planifiez le point de terminaison de votre cluster et faites attention à ne pas utiliser celui d’un cluster existant. Par défaut, le point de terminaison Service Fabric Explorer est le suivant :
https://<cluster_domain>:19080/Explorer/index.htmlwebApplicationUri : WebApplicationUri est l’URI d’un « domaine vérifié » ou un URI utilisant un format de schéma d’API API://{{ID locataire}}/{{nom cluster}}. Pour plus d’informations, consultez Dans les applications monolocataires, l’URI AppId nécessite l’utilisation du schéma par défaut ou des domaines vérifiés.
Exemple de schéma d’API : API://0e3d2646-78b3-4711-b8be-74a381d9890c/mysftestcluster
Exemple SetupApplications.ps1
# if using cloud shell
# cd clouddrive
# git clone https://github.com/Azure-Samples/service-fabric-aad-helpers
# cd service-fabric-aad-helpers
# code .
$tenantId = '0e3d2646-78b3-4711-b8be-74a381d9890c'
$clusterName = 'mysftestcluster'
$spaApplicationReplyUrl = 'https://mysftestcluster.eastus.cloudapp.azure.com:19080/Explorer/index.html' # <--- client browser redirect url
#$webApplicationUri = 'https://mysftestcluster.contoso.com' # <--- must be verified domain due to AAD changes
$webApplicationUri = "API://$tenantId/$clusterName" # <--- doesn't have to be verified domain
$configObj = .\SetupApplications.ps1 -TenantId $tenantId `
-ClusterName $clusterName `
-SpaApplicationReplyUrl $spaApplicationReplyUrl `
-AddResourceAccess `
-WebApplicationUri $webApplicationUri `
-Verbose
Le script génère une variable $configObj pour les commandes suivantes, et imprime le JSON requis par le modèle Azure Resource Manager. Copiez la sortie JSON et utilisez-la lors de la création ou de la modification d’un cluster existant créer votre cluster Microsoft Entra ID activé.
Sortie de l’exemple SetupApplications.ps1
Name Value
---- -----
WebAppId f263fd84-ec9e-44c0-a419-673b1b9fd345
TenantId 0e3d2646-78b3-4711-b8be-74a381d9890c
ServicePrincipalId 3d10f55b-1876-4a62-87db-189bfc54a9f2
NativeClientAppId b22cc0e2-7c4e-480c-89f5-25f768ecb439
-----ARM template-----
"azureActiveDirectory": {
"tenantId":"0e3d2646-78b3-4711-b8be-74a381d9890c",
"clusterApplication":"f263fd84-ec9e-44c0-a419-673b1b9fd345",
"clientApplication":"b22cc0e2-7c4e-480c-89f5-25f768ecb439"
},
JSON d’objet paramètres azureActiveDirectory
"azureActiveDirectory": {
"tenantId":"<guid>",
"clusterApplication":"<guid>",
"clientApplication":"<guid>"
},
SetupUser.ps1
SetupUser.ps1 est utilisé pour ajouter des comptes d’utilisateur à l’inscription d’application nouvellement créée en utilisant la variable de sortie $configObj obtenue ci-dessus. Spécifiez le nom d’utilisateur pour le compte d’utilisateur à configurer avec l’inscription d’application, et spécifiez « isAdmin » pour les autorisations administratives. Si le compte d’utilisateur est nouveau, fournissez également le mot de passe temporaire pour le nouvel utilisateur. Le mot de passe doit être modifié lors de la première ouverture de session. Si vous utilisez « -remove », vous supprimerez le compte d’utilisateur, pas seulement l’inscription de l’application.
Exemple SetupUser.ps1 user (read)
.\SetupUser.ps1 -ConfigObj $configobj `
-UserName 'TestUser' `
-Password 'P@ssword!123' `
-Verbose
Exemple SetupUser.ps1 admin (read/write)
.\SetupUser.ps1 -ConfigObj $configobj `
-UserName 'TestAdmin' `
-Password 'P@ssword!123' `
-IsAdmin `
-Verbose
SetupClusterResource.ps1
SetupClusterResource.ps1 peut éventuellement être utilisé pour exporter un modèle ARM de ressource de cluster existant, ajouter ou modifier une configuration « azureActiveDirectory », et redéployer le modèle. Utilisez « -Whatif » pour simplement exporter et modifier le modèle sans redéployer le changement de configuration. Ce script nécessite le module Azure « Az » et le nom du groupe de ressources pour le cluster.
Exemple SetupClusterResource.ps1 -whatIf
# requires azure module 'az'
# install-module az
$resourceGroupName = 'mysftestcluster'
.\SetupClusterResource.ps1 -configObj $configObj `
-resourceGroupName $resourceGroupName `
-WhatIf
Une fois le modèle vérifié et prêt pour traitement, réexécutez le script sans « -WhatIf », ou utilisez la cmdlet PowerShell « New-AzResourceGroupDeployment » pour déployer le modèle.
Exemple SetupClusterResource.ps1
$resourceGroupName = 'mysftestcluster'
.\SetupClusterResource.ps1 -configObj $configObj `
-resourceGroupName $resourceGroupName
Remarque
Mettez à jour les modèles ARM d’approvisionnement de cluster ou les scripts avec de nouvelles modifications de configuration Microsoft Entra de la ressource de cluster.
Octroi du consentement administrateur
Il peut être nécessaire d’« accorder un consentement d’administrateur » pour les « autorisations d’API » configurées. Accédez au panneau Inscriptions d’applications Azure, puis ajoutez le nom du cluster au filtre. Pour les deux inscriptions, ouvrez « Autorisations d’API », puis sélectionnez « Accorder un consentement administrateur pour » si disponible.
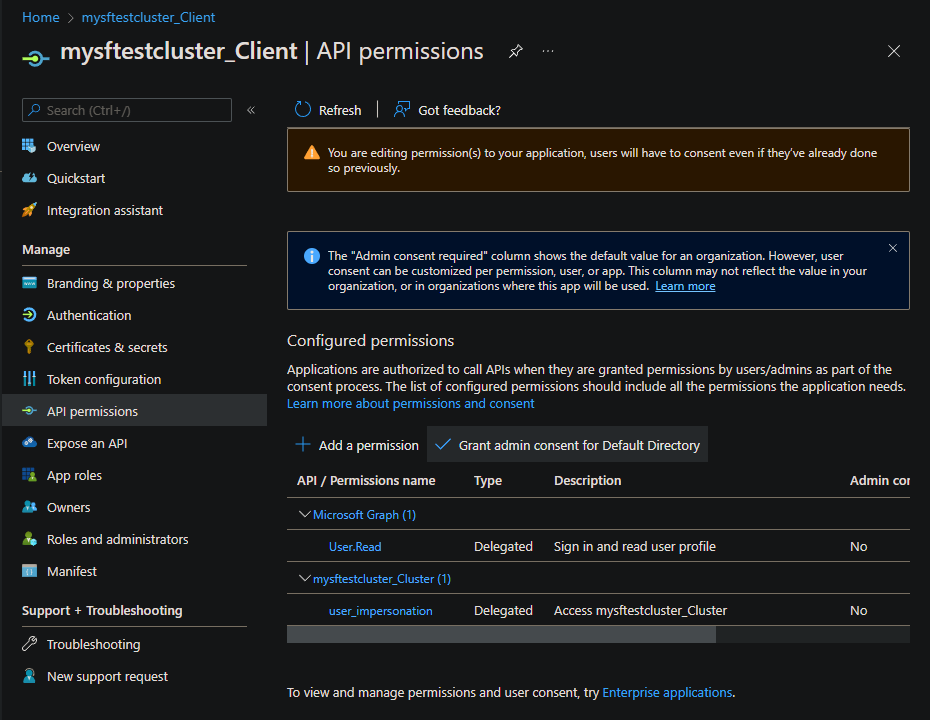
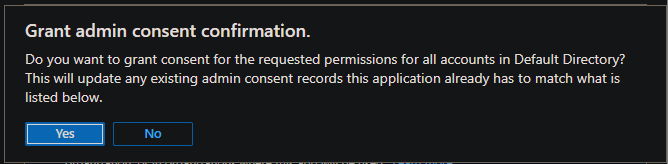
Vérification de la configuration de Microsoft Entra
Accédez à l’URL de Service Fabric Explorer (SFX). Il doit être identique au paramètre spaApplicationReplyUrl. Une boîte de dialogue d’authentification Azure devrait s’afficher. Connectez-vous avec un compte configuré avec la nouvelle configuration De Microsoft Entra. Vérifiez que le compte d’administrateur dispose d’un accès en lecture/écriture et que l’utilisateur dispose d’un accès en lecture. Toute modification apportée au cluster, par exemple, en effectuant une action, est une action administrative.
Résolution des problèmes liés à la configuration de Microsoft Entra ID
La configuration et l’utilisation d’Azure AD peuvent être difficiles, voici donc quelques conseils sur ce que vous pouvez faire pour résoudre le problème. La journalisation de transcription PowerShell peut être activée à l’aide de l’argument « -logFile » sur les scripts « SetupApplications.ps1 » et « SetupUser.ps1 » pour examiner la sortie.
Notes
Avec la migration des plateformes d’identités (ADAL vers MSAL), la dépréciation d’AzureRM en faveur d’Azure AZ, et la prise en charge de plusieurs versions de PowerShell, il se peut que les dépendances ne soient pas toujours correctes ou à jour, provoquant des erreurs dans l’exécution du script. L’exécution de commandes et de scripts PowerShell à partir d’Azure Cloud Shell réduit le risque d’erreurs avec l’authentification automatique de session et l’identité managée.
Request_BadRequest
Problème
Mise à jour de référence non valide. Code d’état HTTP : 400.
VERBOSE: POST with 157-byte payload
VERBOSE: received -byte response of content type application/json
>> TerminatingError(Invoke-WebRequest): "{"error":{"code":"Request_BadRequest","message":"Not a valid reference update.","innerError":{"date":"2022-09-11T22:17:16","request-id":"61fadb2a-478b-4483-8f23-d17e13732104","client-request-id":"61fadb2a-478b-4483-8f23-d17e13732104"}}}"
confirm-graphApiRetry returning:True
VERBOSE: invoke-graphApiCall status: 400
exception:
Response status code doesn't indicate success: 400 (Bad Request).
Invoke-WebRequest: /home/<user>/clouddrive/service-fabric-aad-helpers/Common.ps1:239
Line |
239 | … $result = Invoke-WebRequest $uri -Method $method -Headers $headers …
| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
| {"error":{"code":"Request_BadRequest","message":"Not a valid reference update.","innerError":{"date":"2022-09-11T22:17:16","request-id":"61fadb2a-478b-4483-8f23-d17e13732104","client-request-id":"61fadb2a-478b-4483-8f23-d17e13732104"}}}
at invoke-graphApiCall, /home/<user>/clouddrive/service-fabric-aad-helpers/Common.ps1: line 239
at invoke-graphApi, /home/<user>/clouddrive/service-fabric-aad-helpers/Common.ps1: line 275
at add-roleAssignment, /home/<user>/clouddrive/service-fabric-aad-helpers/SetupUser.ps1: line 193
at add-user, /home/<user>/clouddrive/service-fabric-aad-helpers/SetupUser.ps1: line 244
at enable-AADUser, /home/<user>/clouddrive/service-fabric-aad-helpers/SetupUser.ps1: line 178
at main, /home/<user>/clouddrive/service-fabric-aad-helpers/SetupUser.ps1: line 136
at <ScriptBlock>, /home/<user>/clouddrive/service-fabric-aad-helpers/SetupUser.ps1: line 378
at <ScriptBlock>, /home/<user>/clouddrive/aad-test.ps1: line 43
at <ScriptBlock>, <No file>: line 1
WARNING: invoke-graphApiCall response status: 400
invoke-graphApi count:0 statuscode:400 -uri https://graph.microsoft.com/v1.0/0e3d2646-78b3-4711-b8be-74a381d9890c/servicePrincipals/3d10f55b-1876-4a62-87db-189bfc54a9f2/appRoleAssignedTo -headers System.Collections.Hashtable -body System.Collections.Hashtable -method post
confirm-graphApiRetry returning:True
Motif
Les changements de configuration n’ont pas été propagés. Les scripts effectuent une nouvelle tentative sur certaines requêtes avec les codes d’état HTTP 400 et 404.
Solution
Les scripts effectuent une nouvelle tentative sur certaines requêtes avec les codes d’état HTTP 400 et 404 jusqu’au « -timeoutMin » fourni qui est par défaut de cinq minutes. Le script peut être réexécuté si nécessaire.
Service Fabric Explorer vous demande de sélectionner un certificat
Problème
Une fois que vous vous êtes connecté à Microsoft Entra ID dans Service Fabric Explorer, le navigateur revient à la page d’accueil, mais un message vous invite à sélectionner un certificat.
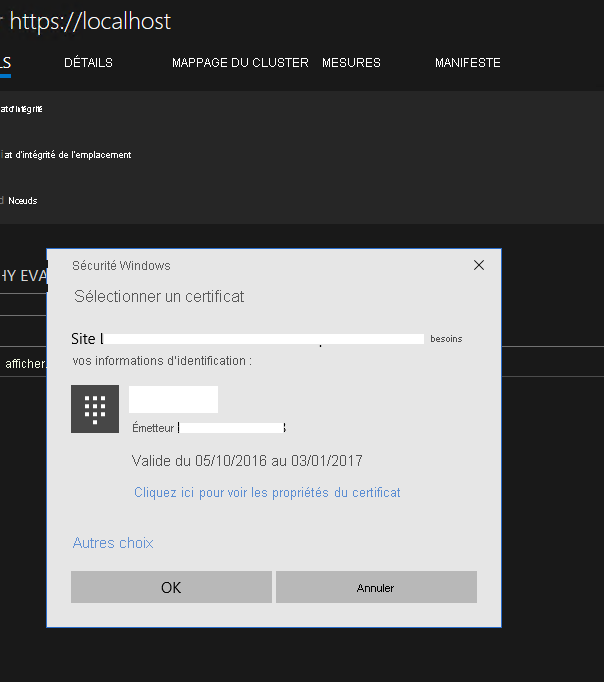
Motif
L’utilisateur n’est pas affecté à un rôle dans l’application de cluster Microsoft Entra ID. Par conséquent, l’authentification Microsoft Entra échoue sur le cluster Service Fabric. Service Fabric Explorer revient à l’authentification par certificat.
Solution
Suivez les instructions de configuration de Microsoft Entra ID et affectez des rôles utilisateur. Nous vous recommandons également d’activer l’option « Affectation de l’utilisateur requise pour accéder à l’application », comme le fait SetupApplications.ps1.
La connexion avec PowerShell échoue avec un message d’erreur : « Les informations d’identification spécifiées ne sont pas valides »
Problème
Lorsque vous utilisez PowerShell pour vous connecter au cluster à l’aide du mode de sécurité « AzureActiveDirectory », une fois que vous vous êtes connecté avec succès à Microsoft Entra ID, la connexion échoue avec une erreur : « Les informations d’identification spécifiées ne sont pas valides. »
Solution
La solution est la même que pour le problème précédent.
Lorsque vous vous connectez, Service Fabric Explorer renvoie un message d’échec : « AADSTS50011 »
Problème
Lorsque vous essayez de vous connecter à Microsoft Entra ID dans Service Fabric Explorer, la page retourne un échec : « AADSTS50011 : L’adresse de réponse <url> ne correspond pas aux adresses de réponse configurées pour l’application : <guid>. »

Motif
L’application de cluster (web) qui représente Service Fabric Explorer tente de s’authentifier auprès de Microsoft Entra ID et, dans le cadre de la requête, elle fournit l’URL de retour de redirection. Mais l’URL n’est pas répertoriée dans la liste URL DE RÉPONSE de l’application Microsoft Entra.
Solution
Dans la page d’inscription de l’application Microsoft Entra pour votre cluster, sélectionnez Authentification, puis, sous la section URI de redirection , ajoutez l’URL de Service Fabric Explorer à la liste. Enregistrez vos modifications.
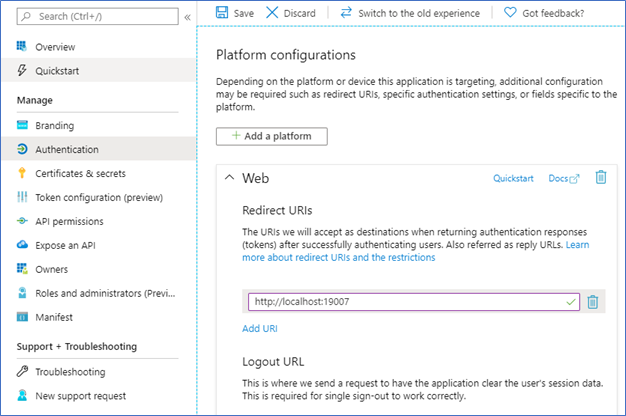
Connexion au cluster à l’aide de l’authentification Microsoft Entra via PowerShell génère une erreur lorsque vous vous connectez : « AADSTS50011 »
Problème
Lorsque vous essayez de vous connecter à un cluster Service Fabric à l’aide de Microsoft Entra ID via PowerShell, la page de connexion retourne un échec : « AADSTS50011 : L’URL de réponse spécifiée dans la requête ne correspond pas aux URL de réponse configurées pour l’application : <guid>. »
Motif
Comme pour le problème précédent, PowerShell tente de s’authentifier auprès de Microsoft Entra ID, qui fournit une URL de redirection qui n’est pas répertoriée dans l’application Microsoft Entra URL de réponse liste.
Solution
Utilisez le même processus que dans le problème précédent, mais l’URL doit être définie sur urn:ietf:wg:oauth:2.0:oob, une redirection spéciale pour l’authentification de la ligne de commande.
L’exécution du script entraîne une erreur d’autorisation
Problème
Le script PowerShell peut ne pas exécuter toutes les commandes REST requises pour terminer la configuration de Microsoft Entra avec l’erreur « Authorization_RequestDenied », « Privilèges insuffisants pour terminer l’opération ». Exemple d’erreur :
Invoke-WebRequest: /home/<user>/clouddrive/service-fabric-aad-helpers/Common.ps1:239
Line |
239 | … $result = Invoke-WebRequest $uri -Method $method -Headers $headers …
| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
| {"error":{"code":"Authorization_RequestDenied","message":"Insufficient privileges to complete the
| operation.","innerError":{"date":"2022-08-29T14:46:37","request-id":"c4fd3acc-1558-4950-8028-68bb058f7bf0","client-request-id":"c4fd3acc-1558-4950-8028-68bb058f7bf0"}}}
...
invoke-graphApi count:0 statuscode:403 -uri https://graph.microsoft.com/v1.0/72f988bf-86f1-41af-91ab-2d7cd011db47/oauth2PermissionGrants -headers System.Collections.Hashtable -body System.Collections.Hashtable -method post
Write-Error: /home/<user>/clouddrive/service-fabric-aad-helpers/SetupApplications.ps1:364
Line |
364 | assert-notNull $result "aad app service principal oauth permissio …
| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
| aad app service principal oauth permissions User.Read configuration failed
Write-Error: /home/<user>/clouddrive/service-fabric-aad-helpers/SetupApplications.ps1:656
Line |
656 | main
| ~~~~
| exception: exception: assertion failure: object: message:aad app service principal oauth permissions User.Read configuration failed Exception:
| /home/<user>/clouddrive/service-fabric-aad-helpers/Common.ps1:22 Line | 22 | throw "assertion failure: object:$obj message:$msg" |
| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ | assertion failure: object: message:aad app service principal oauth permissions User.Read configuration failed
...
Motif
Cette erreur est retournée lorsque le compte d’utilisateur qui exécute le script ne dispose pas des autorisations nécessaires pour effectuer l’appel REST. Cela peut se produire si l’utilisateur ne dispose pas d’autorisations d’administration, de gestion ou d’écriture pour les objets créés ou modifiés.
Solution
Collaborez avec un administrateur de locataire Azure ou Microsoft Entra ID pour effectuer toutes les actions restantes. Les scripts fournis étant idempotents, il est possible de les réexécuter pour terminer le processus.
Connecter le cluster à l’aide de l’authentification Microsoft Entra via PowerShell
Pour connecter le cluster Service Fabric, utilisez l’exemple de commande PowerShell suivant :
Connect-ServiceFabricCluster -ConnectionEndpoint <endpoint> -KeepAliveIntervalInSec 10 -AzureActiveDirectory -ServerCertThumbprint <thumbprint>
Pour plus d’informations, consultez l’applet de commande Connect-ServiceFabricCluster.
Puis-je réutiliser le même locataire Microsoft Entra dans plusieurs clusters ?
Oui. Cependant, n’oubliez pas d’ajouter l’URL de Service Fabric Explorer à votre application en cluster (web). Si vous ne le faites pas, Service Fabric Explorer ne fonctionnera pas.
Pourquoi ai-je toujours besoin d’un certificat de serveur alors que Microsoft Entra ID est activé ?
FabricClient et FabricGateway effectuent une authentification mutuelle. Pendant l’authentification Microsoft Entra, l’intégration de Microsoft Entra fournit une identité cliente au serveur et le certificat de serveur est utilisé par le client pour vérifier l’identité du serveur. Pour plus d’informations sur les certificats Service Fabric, consultez Certificats X.509 et Service Fabric.
Étapes suivantes
Après avoir configuré des applications Microsoft Entra et des rôles de définition pour les utilisateurs, configurer et déployer un cluster.