Add or remove users or groups, manage security groups
TFS 2017 | TFS 2015 | TFS 2013
The recommended method for managing permissions and access is to assign users to a security group. You can assign users to a default security group or create a custom group to grant or restrict permissions. You can add users and groups to more than one security group. For example, you add most developers to the Contributors group. When that same user is added as a member to a team, then they are added to the team's system-generated security group.
This article shows how to perform the following tasks:
- Create a custom security group at the project or collection level
- Add or remove users or groups to a security group
- Change a group name, image, or description
- Delete a custom security group
For information on the following related tasks, see the corresponding articles:
- Add AD/Azure AD users or groups to a built-in security group
- Add users & manage access
- Add users or groups to a team or project
- Remove user accounts
- Grant or restrict access using permissions
- Change project-level permissions
- Change project collection-level permissions
Note
Users inherit permissions from the group(s) that they belong to. If a permission is set to Allow for one group and Deny for another group to which the user belongs, then their effective permission assignment is Deny. To learn more about permission inheritance, see Get started with permissions, access, and security groups, Permission inheritance and security groups.
How Azure DevOps uses security groups
Azure DevOps uses security groups for the following purposes:
- Determine permissions allocated to a group or user
- Determine access level allocated to a group or user
- Filter work item queries based on membership within a group
- Use @mention of a project-level group to send email notifications to members of that group
- Send team notifications to members of a team group
- Add a group to a role-based permission
- Set object-level permissions to a security group
Note
All security groups are collection-level entities, even those groups that only have permissions to a specific project. From the web portal, visibility of some security groups may be limited based on user permissions. However, you can discover the names of all groups in an organization using the REST APIs. To learn more, see Add and manage security groups.
Prerequisites
- To manage permissions or groups at the project level, you must be a member of the Project Administrators Group. If you created the project, you are automatically added as a member of this group.
- To manage permissions or groups at the collection or instance level, you must be a member of the Project Collection Administrators Group. If you created the organization or collection, you are automatically added as a member of this group.
Create a custom security group
You create a custom security group from the Project settings>Permissions or Organization settings>Permissions pages. Choose to create a project-level group when you want to manage permissions at the project or object-level for a project. Create a collection-level group when you want to manage permissions at the collection level. To learn more about setting permissions for these areas, see Change project-level permissions and Change project collection-level permissions.
Open the web portal and choose the project where you want to add users or groups. To choose another project, see Switch project, repository, team.
Choose the
 gear icon to open the administrative context.
gear icon to open the administrative context.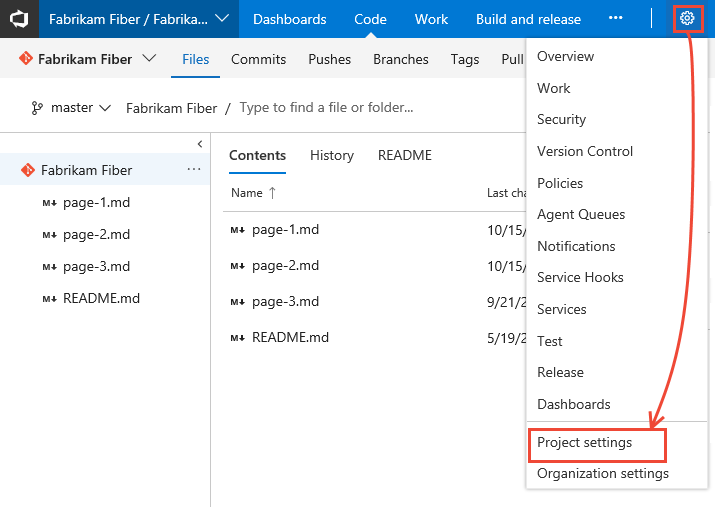
Choose Security and under Groups, choose one of the following options:
- Readers: To add users who require read-only access to the project, choose.
- Contributors: To add users who contribute fully to this project or who have been granted Stakeholder access.
- Project Administrators: To add users who need to administrate the project. To learn more, see Change project-level permissions.
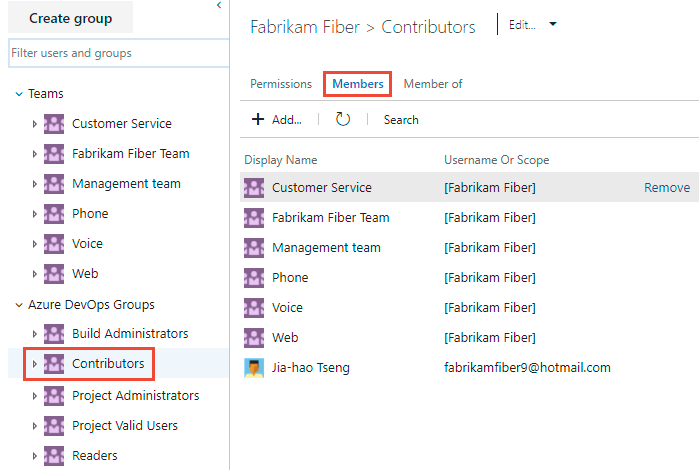
Next, choose the Members tab.
Here we choose the Contributors group.
Tip
Managing users is much easier using groups, not individual users.
By default, the default team group and any other teams you add to the project, are included as members of the Contributors group. Add a new user as a member of a team instead, and the user automatically inherits Contributor permissions.
Choose
 Add to add a user or a user group.
Add to add a user or a user group.Enter the name of the user account into the text box. You can enter several identities into the text box, separated by commas. The system automatically searches for matches.
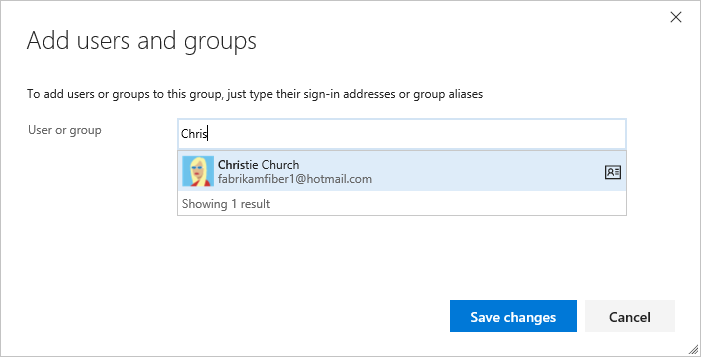
Note
The first time you add a user or group to Azure DevOps, you can't browse to it or check the friendly name. After the identity has been added, you can just enter the friendly name.
(Optional) You can customize user permissions for other functionality within the project, such as areas and iterations or shared queries.
Note
Users that have limited access, such as Stakeholders, won't be able to access select features even if granted permissions to those features. To learn more, see Permissions and access.
Add users or groups to a security group
As roles and responsibilities change, you might need to change the permission levels for individual members of a project. The easiest way to do that is to add the user or a group of users to either a default or custom security group. If roles change, you can then remove the user from a group.
Here we show how to add a user to the built-in Project Administrators group. The method is similar no matter what group you are adding. If your organization is connected to Azure Active Directory or Active Directory, then you can add security groups defined in those directories to Azure DevOps security groups. To learn more, see Add AD/Azure AD users or groups to a built-in security group.
Open the Permissions page for either the project-level or organization-level as described in the previous section, Create a custom security group.
Choose the security group whose members you want to manage, then choose the Members tab, and then choose Add.
For example, here we choose the Project Administrators group, Members, and then Add.
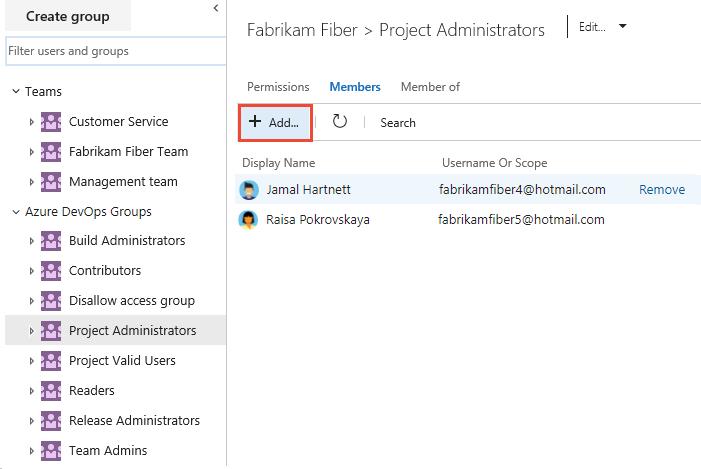
Enter the name of the user account into the text box. You can enter several identities into the text box, separated by commas. The system automatically searches for matches. Choose the match(es) that meets your choice.

Note
Users that have limited access, such as Stakeholders, won't be able to access select features even if granted permissions to those features. To learn more, see Permissions and access.
Choose Save changes. Choose the
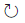 refresh icon to see the additions.
refresh icon to see the additions.
Change permissions for a user or group
To change the permissions for a user or group, you need to open the security dialog for the user or group. Because permissions are defined at different levels, review the following articles to open the dialog for the permissions you want to change:
Remove users or groups from a security group
You add or remove users from a group from the Members tab of a selected group.
To remove a user from a group, choose Remove next to the user's name that you want to remove.
Manage group settings
You can change a group name, description, add a group image, or delete a group.
From the Project > Settings > Security or Organization > Settings > Security page, choose the group you want to manage
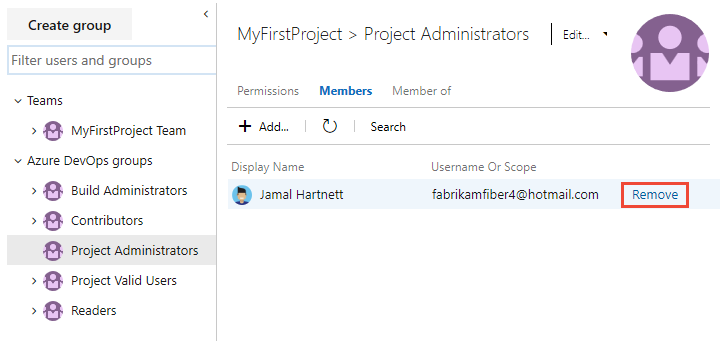
Choose from the Edit menu to either Edit profile or Delete.
For example, here we open the Edit profile for the Stakeholder Access group.
. . . and change the description. Note that you can change the name of the group as well.
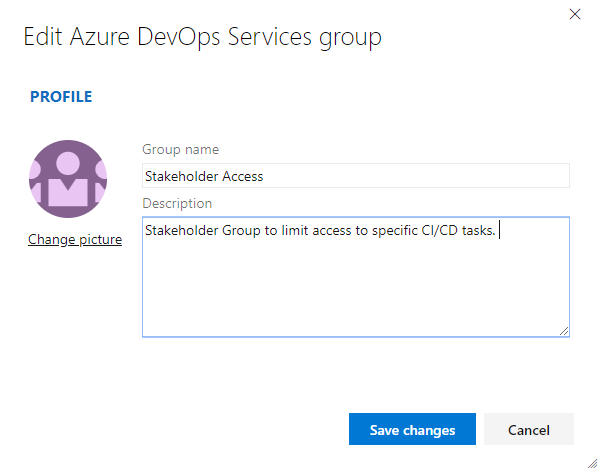
Choose Save to save your changes.
On-premises deployments
For on-premises deployments, see these additional articles:
If your on-premises deployment is integrated with a SharePoint product or SQL Server Reports, you'll need to manage membership for those products separately from their websites.