System Management
Set High Standards: Powerful Tools for Configuration Management
Jeremy Chapman
At a Glance:
- Configuration management basics
- Best Practices Analyzers
- SMS 2003 Desired Configuration Monitoring
- Configuration monitoring in practice
Almost half of all unplanned service outages happen because of system configuration mistakes or oversights. With that in mind, several useful tools are available from Microsoft to help you keep
configuration issues under control in environments of all sizes and levels of complexity. These tools provide both the technology and the guidance you'll need to get started managing configuration.
First, it's important to understand the concept of configuration management. Within IT organizations, configuration management is the process of identifying, defining, and documenting the environment, its components, and the relationships between components. Ultimately, you are trying to define a known, standard system state and to maintain that standard state across your environment. Part of this process entails discovering and updating configuration items (CIs) for your systems, as well as tracking and documenting these CIs as they change.
If, for example, you have a known state for a workstation and define the CIs that represent that state within your environment, adding a patch represents a deviation from your defined state. Now imagine there's a tool that informs you of any such deviations. Each patch you install will trigger a number of alerts, telling you those patched workstations are not complying with the previously defined state. These alerts let you document any changes to the defined state, and future checks will therefore reflect the revised state you have documented.
On one hand, this sounds like a lot of additional work just to accommodate planned updates. But there's another benefit: you'll also be warned if a rogue element changes one of your defined CIs. The consequence of not being informed of an unplanned state deviation can result in amounts of work much greater than the effort invested in defining and maintaining CIs. Managing and updating your CIs puts you in control to make sure that only undesirable CIs trigger alerts.
So what goes into a CI? CIs generally consist of configuration attributes such as description, version number, component, relationships, location, and status. In an ideal state, that patch you just authorized and installed would be populated in a CI and all of the CIs would reside in a relational configuration management database.
Most people aren't willing to check configuration items against a spreadsheet or database, despite taking the time and care to define them. Likewise, automating the compliance checking and alerting process has been difficult. Let's say you have 100 configuration attributes per computer, and a skilled tester can check 50 configuration attributes manually in an hour. Now think about a company that has 1,000 servers and 20,000 desktops and imagine the workload required to maintain a desired state and check all these computers on a regular basis. Even if all computers were in the desired state at deployment, there's no practical way to maintain a standard across all 21,000 computers—or even 100 computers—without automation.
How do you define the configuration items and attributes so that a tool can automatically perform a configuration health check and tell you if your environment complies with the predefined standard? A first step was made to help automate configuration monitoring for Windows®-based systems with the release of the first Best Practice Analyzer (BPA). Microsoft published a set of CIs inside the tool to check for compliance against a known installation benchmark. Since then, Microsoft has provided tools to analyze and define CIs for a variety of applications and even customized for specific computing environments.
This article introduces a number of Microsoft tools that help automate parts of the configuration management process. It's a fact that defining CIs can be difficult and time-consuming, yet the reward is having a controlled and auditable state where any unplanned changes in configuration automatically trigger alerts, often before those changes cause a service disruption or create a security risk.
Best Practices Analyzer Tools
In September 2004, Microsoft introduced the first tools to help automate configuration monitoring for Windows-based systems with the release of the Exchange Server BPA tool, which looks at an Exchange Server deployment, compares it to a regularly updated repository of Microsoft configuration best practices, then reports its findings. To use the Exchange Server BPA, download the app, install it, and make sure that .NET Framework 1.1 is installed on the target servers. With proper network access, Exchange Server BPA can even diagnose problems with Active Directory® services. The analyzer works with Microsoft® Exchange Server 2000 and 2003 and will work with mixed-node topologies of Exchange Server 5.5 along with later versions. See the TechNet Magazine article "Tune Up Exchange Server with the Best Practices Analyzer" for more information.
Additional BPA tools are available for Internet Security and Acceleration (ISA) Server 2004 and SQL Server™ 2000. The ISA Server BPA checks configuration data from the ISA Server hierarchy of administration COM objects, Windows Management Instrumentation (WMI) classes, the system registry, files on disk, and DNS settings. The SQL Server BPA helps manage databases by allowing you to verify best practices are in place, specifically with the usage and administration of SQL Server databases and making sure that servers are properly managed and operated.
Desired Configuration Monitoring
Building on the success of the BPA tools, the Systems Management Server (SMS) 2003 Desired Configuration Monitoring (DCM) tool lets you store your identified configuration attributes into a file, which can then be consumed by an application to automate configuration checks and define how non-compliance is reported. In the BPA tools, CIs are predefined and not customizable. Even though this is easier than manually combing through your registries and providers, it can fire off alerts regarding configuration items you actually want, and it won't fire off alerts for any custom attributes your environment may have and want to monitor.
SMS 2003 DCM uses the same logic as the BPA tools, but allows you to uncover the XML configuration files and edit, add, or delete rules using the included authoring tool. (The overall process is shown in Figure 1.) Even though this sounds pretty straightforward, anyone who has taken a look at all the CIs and attributes that contribute to a healthy system will know that this is not a quick task. For that reason, Microsoft created baseline CIs for Exchange, ISA, and Windows servers.
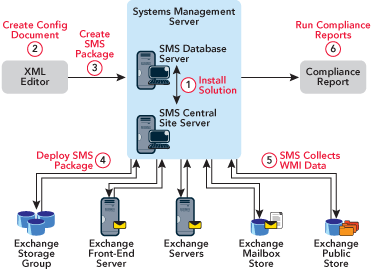
Figure 1** Desired Configuration Monitoring Process **
Let's walk through a scenario where monitoring configuration is critical and can be accomplished using the DCM solution. Imagine you have an online business that relies on custom applications and services. Any problem in the configuration of these apps could cause a service disruption and effectively stop all transactions.
Three weeks ago you went through a patch cycle on your servers and during this cycle, the credit card authentication service, which is normally set to start automatically, was set to a manual start and simply left running. This server ran fine for three weeks. Then, during an overnight scheduled maintenance window, an update to a custom application required a reboot. On startup, the credit card authentication service did not start automatically (because of the new manual setting) and credit card transactions weren't able to be processed. How long will it take your IT staff to identify and fix the problem? Depending on the size of the business, hours—or even minutes—of service disruption could account for a huge sum of lost revenue.
With the DCM solution, you would define the credit card authentication service autostart as a configuration attribute (see Figure 2). DCM would have alerted the IT department when the autostart setting was set to manual.
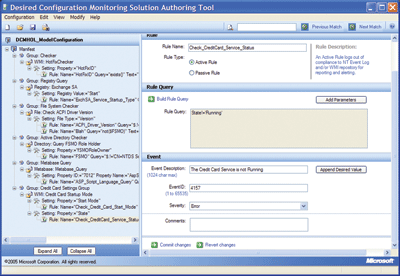
Figure 2** DCM Solution Authoring Tool **
Your Next Steps
The ISA Server baseline configuration available in the DCM Beta Configuration Manifest Program includes several thousand settings. So along with the DCM solution, I recommend that you examine your organization's current configuration management procedures to get the maximum benefit of the tools. Microsoft has a library of content on Configuration Management in its Microsoft Operations Framework (MOF) guidance. The DCM solution automates just part of these configuration management best practices.
As I'm writing this article, the SMS 2003 DCM solution is in the process of being updated to include new key functionality. The update will include desktop configuration monitoring capability and SQL Server functionality. Plans are to include CIs for both desktops and SQL Server, along with releasing the current DCM beta configuration items for Windows Server®, Exchange Server, and ISA Server.
The update will also include a reduced set of predefined SMS 2003 reports for use without SQL Server Reporting Services. Finally, the user interface will add many new features to ease the creation of configuration items. The new user interface will provide a wizard-based experience for definition of simple rules, rule templates for key configuration attributes, and a table view of simple rules. The sum of these changes promises an improved user experience and reduced time to get up and running with the solution.
For further information about change and configuration management and configuration monitoring, you should look into all the resources highlighted in the "Online Resources" sidebar.
Online Resources
If your company is interested in improving the configuration management process, these resources can help you implement a process suited to your needs.
- SMS 2003 Desired Configuration Monitoring
- Microsoft Operations Framework: Changing Quadrant
- Exchange Server Best Practices Analyzer Tool
- Best Practices Analyzer Tool for Microsoft SQL Server 2000 1.0
- ISA Server 2004 Best Practices Analyzer Tool
- BizTalk Server Best Practices Analyzer
Jeremy Chapman is a Senior Product Manager in the Microsoft Core Infrastructure Solutions team, responsible for Solution Accelerators, Reference Architecture, and Microsoft Operations Framework (MOF) guidance. He has worked as a project and operations consultant spanning the past eight years equally in Europe, Asia, and North America.
© 2008 Microsoft Corporation and CMP Media, LLC. All rights reserved; reproduction in part or in whole without permission is prohibited.