Identity & Access Management
MIIS Gets your Directories in Sync
Randy Muller
At a Glance:
- Managing diverse credential information
- Using management agents
- Becoming familiar with the MIIS metaverse
Trying to maintain security and identity information in a large, heterogeneous network can be difficult and complicated. And this can put your network at risk. Fortunately, Microsoft Identity
Integration Server (MIIS) 2003 allows you to synchronize identity information from many different directories and services into a single, organization-wide solution. This can help protect your network's security and simplify management.
Some of the major capabilities of MIIS 2003 include:
- Directory synchronization
- Account provisioning
- Certificate publishing
- Group management
- Management of Global Address Lists (GALs) for diverse e-mail systems
- Management and synchronization of passwords
There are four major components of MIIS 2003. They are the connected data sources, management agents, connector spaces, and the metaverse. I'll explain each concept briefly and describe how they all fit together.
Connected Data Sources
A connected data source is a system that provides information to or receives information from MIIS 2003. Many systems can act as a connected data source including directory services (such as Active Directory®), databases, and even individual files. The connected data sources currently supported by MIIS 2003 Service Pack 1 (SP1) are shown in Figure 1.
Management Agents
Every connected data source has a corresponding management agent. Each management agent acts to control the flow of information between its connected data source and MIIS. If you modify synchronized data in either the connected data source or within MIIS (via defined rules), the management agent will keep MIIS 2003 and the connected data sources consistent. Since there is a management agent for each supported connected data source type, the types of management agents are the same as the types of connected data sources supported by MIIS 2003. If you need to connect a data source not listed in Figure 1, MIIS also provides a generic management agent that can be configured to connect to any system that provides programmatic access to its data, called the extensible connectivity management agent. In Figure 2 an Active Directory management agent (called NewAgent) has been created.
Figure 1 Supported Sources
| Active Directory |
| Active Directory Application Mode (ADAM) |
| Active Directory Global Address List (GAL) |
| Attribute-Value Pair text file |
| Delimited text file |
| Directory Services Mark-up Language (DSML) 2.0 |
| Exchange Server 5.5 |
| Exchange Server 5.5 (bridgehead server) |
| Fixed-Width text file |
| IBM DB2 Universal Databases |
| IBM Resource Access Control Facility (RACF) |
| IBM Tivoli Directory Server |
| LDAP Data Interchange Format (LDIF) |
| Lotus Notes 4.6, 5.0, and 6.x |
| Microsoft Exchange Server 2000 (use the management agent for Active Directory) |
| Microsoft SQL Server 7.0 |
| or SQL Server 2000 |
| Netscape Directory Servers |
| Novell eDirectory 8.6.2, 8.7, and 8.7.x |
| Oracle Database 8i or 9i |
| Sun ONE Directory Server: 4.x and 5.x |
| Windows NT 4.0 |
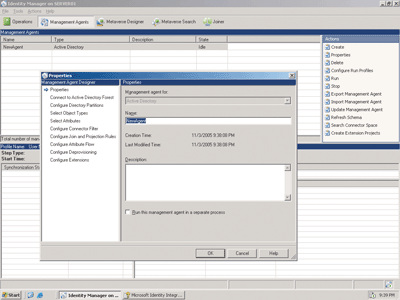
Figure 2** Creating a Management Agent **
Management agents are all very similar in their construction, with only slight variations depending on their type. All management agents perform some common tasks regardless of their type. These tasks include schema discovery, configuring the connector filter, configuring join and projection rules, configuring attribute flow, configuring deprovisioning, and configuring rules extensions.
Management agents also support password management, which will be important to know later in the article. The management agents that natively support password management in MIIS 2003 SP1 are: Active Directory, Active Directory Application Mode (ADAM), Lotus Notes, Sun and Netscape Directory Servers, Novell eDirectory, and Windows NT® 4.0. Any of the management agents can be programmatically extended to support password management.
Connector Spaces
The connector space is a staging area for information coming into or going out from a given management agent. The information that is staged in a management agent's connector space is used to synchronize with the metaverse or is exported out to its connected data source. Each connected data source has its own reserved logical area within the connector space that is used by its corresponding management agent. The connector space does not actually contain the connected data source as an object itself, but rather contains a subset of the connected data sources' attributes, as defined on the management agent. MIIS uses the connector space object instead of making direct queries to the connected data source when processing business rules. This improves synchronization speed between the metaverse and the connected data sources.
Installing the Password Change Notification Service
The actual Password Change Notification Service (PCNS) is not installed by default. The installation files are located on the installation media and can be installed by clicking the password change notification service.msi file found in the Password Synchronization folder.
When you install the PCNS a dialog box will appear telling you that the service will need to extend the schema with the command msiexec /i “D:\ENGLISH\IIS2003\ ENT_SP1\ PASSWORD SYNCHRONIZATION\PASSWORD CHANGE NOTIFICATION SERVICE.MSI” SCHEMAONLY=TRUE as shown in Figure A.
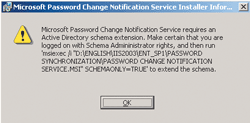
Figure A** Extend the Schema **
As you continue with the installation process, a dialog box appears confirming that you wish to extend the schema to support the PCNS. Click OK to make the changes.
Now you can go back and install the PCNS; once the service has been installed, you will have to restart the system for all of the changes to take affect.
During the installation process for the PCNS, three components are installed: pcnsflt.dll, pcnssvc.exe, and pcnscfg.exe.
Pcnsflt.dll This is the filter that is used to actually capture any changes to passwords.
Pcnssvc.exe This is the actual PCNS. It encrypts and sends the password changes to a designated MIIS 2003 server.
Pcnscfg.exe You use this command-line utility to configure the service.
Both the pcnssvc.exe and pcnscfg.exe files are located in the %Systemroot%\Program Files\Microsoft Password Change Notification Service directory. You will use these later to configure the PCNS. Once you have the PCNS installed, you will need to configure it using the pcnscfg.exe command mentioned earlier. With this command, you will specify which MIIS 2003 server will receive password changes. An example of the pcnscfg.exe command and some of the switches can be seen in Figure B.
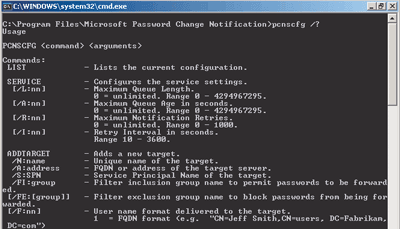
Figure B** Pcnscfg.exe and Some Switches **
The Metaverse
The metaverse is a collection of tables that contains information about connected identities from the connected data sources. These tables are stored in a SQL Server database and contain all the aggregated information about a specific entity as it exists in all of the connected data sources. Attributes and objects flow into and out of the metaverse. Updates flowing in are used to update the metaverse; updates going out are used to update the connected data sources through their respective connector space. The metaverse contains its own schema, which defines which object types and attributes the metaverse can contain. All objects in the metaverse must be of one of the types defined in the metaverse schema. The metaverse schema contains the following default objects, but can be easily extended:
- computer
- domain
- group
- locality
- organization
- organizational unit
- person
- printer
- role
Now that you have some background on the structure and components of MIIS 2003 SP1 and how they interact, let's discuss the password management functionality in more detail.
Password Management in MIIS
Passwords are one of the weakest security points in a network, but the use of secure passwords can become a source of contention between administrators and users. Users would rather have nice, easy-to-remember passwords (or truthfully, none at all), whereas administrators want to implement more restrictive password requirements. This is of even more concern on networks with disparate directories where users may have several accounts with varying levels of password requirements to access each of these directories or services. MIIS 2003 SP1 has a number of new password management and synchronization features that can help. Let's see how the use of the password management and synchronization capabilities help you control passwords and reduce administrative efforts.
- Auditing features let you track changes to or setting of passwords through the use of entries written to the Event Log.
- Developers have the ability to perform password management functions through an API.
- An administrator or a user can reset passwords through a central point or through a Web services application.
- Integrated third-party solutions can be used to extend the capabilities of MIIS 2003.
- Password policies as defined in Active Directory, for example, can be enforced across other systems.
A number of security groups are created by default when you install MIIS 2003. Two of these groups are used specifically in support of password management, MIISBrowse and MIISPasswordSet, while the others, MIISAdmins, MIISOperators, and MIISJoiners are used in support of MIIS 2003. A listing of these groups and a description of their functions is shown in Figure 3.
Figure 3 Security Groups
| Group | Function |
| MIISBROWSE Security Group | Members of this group have permission to gather information about a user’s accounts when doing search operations with WMI queries |
| MIISPasswordSet Security Group | Members can perform account search, password set, and password change operations using the password management interfaces with WMI. |
| MIISAdmins Security Group | Members of this group have full access to everything in Identity Manager. |
| MIISOperators Security Group | Members have access to Operations in the Identity Manager only. MIISOperators can run management agents, view synchronization stats, and save the run histories. Members must also be members of the MIISBrowse group to open links in synchronization statistics. |
| MIISJoiners Security Group | Members have access to Joiner and Metaverse Search in Identity Manager. MIISJoiners can join or project disconnectors by using Joiner and they can use Metaverse Search to view object properties and disconnect objects from the metaverse. |
Configuring a Management Agent
Now that you have the PCNS installed, the next task is to configure a management agent. There are 10 steps in creating a management agent.
Start the creation process by clicking on the Management Agents tab in the Identity Integration Server screen, right-click in the Management Agents box and press create. At this point you will have to specify what type of management agent you want to create as you can see in Figure C
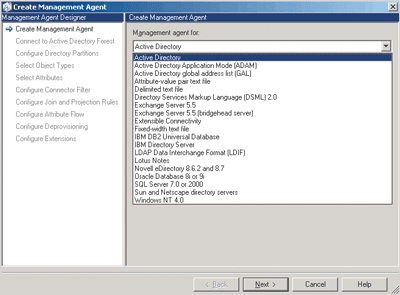
Figure C** Configure Directory Partitions **
When you have specified the management agent type, you will have to connect to a specific forest and configure directory partitions. This screen also holds the checkbox you want to ensure and check for password synchronization (by checking the Enable this partition as a password synchronization source box as you can see in Figure D.
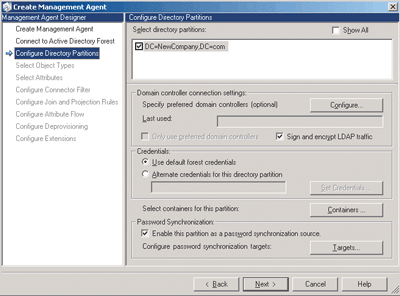
Figure D** Configure Management Agent **
Once you have done this, you will specify what object type you want, Attributes, Connector Filter, Join and Projection Rules, Attribute Flow, Deprovisioning and finally Extensions. The extensions box also holds another box you must make sure to check, Enable password management, as shown in Figure E.
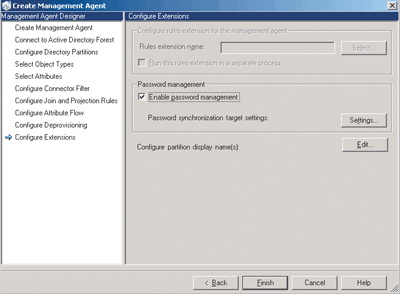
Figure E** Enable Password Management **
Password Change Notification Service
The management of passwords is a costly and time-consuming process for many administrators. Fortunately, this process has been greatly enhanced with a new feature in MIIS 2003 SP1—the Password Change Notification Service (PCNS). This new service allows for the secure updating of password resets to be sent to an MIIS 2003 server. When a password reset is initiated on a domain controller, either by a user who presses Ctrl+Alt+Del, or by an administrator, the request is intercepted. The intercepted request is encrypted and then forwarded on to the MIIS 2003 server and from there to all connected data sources (that are configured for password management) through synchronization. To see how to install the PCNS and configure a management agent, see the sidebars by the same names.
Conclusion
In this article, I have discussed the major components of MIIS 2003 and how they work together. I've also given you a brief overview of the password management and synchronization features available through the PCNS. All this should put you on the road to successful identity synchronization and password management across your organization. Now that you've been introduced to all the great features available in MIIS 2003 SP1, you'll almost certainly want to take a look at more info, which you can find at microsoft.com/windowsserversystem/miis2003/default.mspx.
Randy Muller, MCT, MCSE, MCSA, MCDST, teaches a variety of networking, security, and other computer classes. He is a former Army Signal Corp Officer and has been teaching since 2000. You can contact Randy at randy@randymuller.org.
© 2008 Microsoft Corporation and CMP Media, LLC. All rights reserved; reproduction in part or in whole without permission is prohibited.