Enable B2B collaboration across Microsoft clouds
Applies to:  Workforce tenants
Workforce tenants  External tenants (learn more)
External tenants (learn more)
When Microsoft Entra organizations in separate Microsoft Azure clouds need to collaborate, they can use Microsoft cloud settings to enable Microsoft Entra B2B collaboration with each other. B2B collaboration is available between the following global and sovereign Microsoft Azure clouds:
- Microsoft Azure commercial cloud and Microsoft Azure Government
- Microsoft Azure commercial cloud and Microsoft Azure operated by 21Vianet
Important
Both organizations must enable collaboration with each other, as described in this article. Then each organization can optionally modify their inbound and outbound access settings, as described in Configure cross-tenant access settings for B2B collaboration.
To enable collaboration between two organizations in different Microsoft clouds, an admin in each organization completes the following steps:
Configures their Microsoft cloud settings to enable collaboration with the partner's cloud.
Uses the partner's tenant ID to find and add the partner to their organizational settings.
Configures their inbound and outbound settings for the partner organization. The admin can either apply the default settings or configure specific settings for the partner.
After each organization completes these steps, Microsoft Entra B2B collaboration between the organizations is enabled.
Note
B2B direct connect is not supported for collaboration with Microsoft Entra tenants in a different Microsoft cloud.
Before you begin
- Obtain the partner's tenant ID. To enable B2B collaboration with a partner's Microsoft Entra organization in another Microsoft Azure cloud, you need the partner's tenant ID. Using an organization's domain name for lookup isn't available in cross-cloud scenarios.
- Decide on inbound and outbound access settings for the partner. Selecting a cloud in your Microsoft cloud settings doesn't automatically enable B2B collaboration. Once you enable another Microsoft Azure cloud, all B2B collaboration is blocked by default for organizations in that cloud. You need to add the tenant you want to collaborate with to your Organizational settings. At that point, your default settings go into effect for that tenant only. You can allow the default settings to remain in effect. Or, you can modify the inbound and outbound settings for the organization.
- Obtain any required object IDs or app IDs. If you want to apply access settings to specific users, groups, or applications in the partner organization, you need to contact the organization for information before configuring your settings. Obtain their user object IDs, group object IDs, or application IDs (client app IDs or resource app IDs) so you can target your settings correctly.
Note
Users from another Microsoft cloud must be invited using their user principal name (UPN). Email as sign-in is not currently supported when collaborating with users from another Microsoft cloud.
Enable the cloud in your Microsoft cloud settings
Tip
Steps in this article might vary slightly based on the portal you start from.
In your Microsoft cloud settings, enable the Microsoft Azure cloud you want to collaborate with.
Sign in to the Microsoft Entra admin center as at least a Security Administrator.
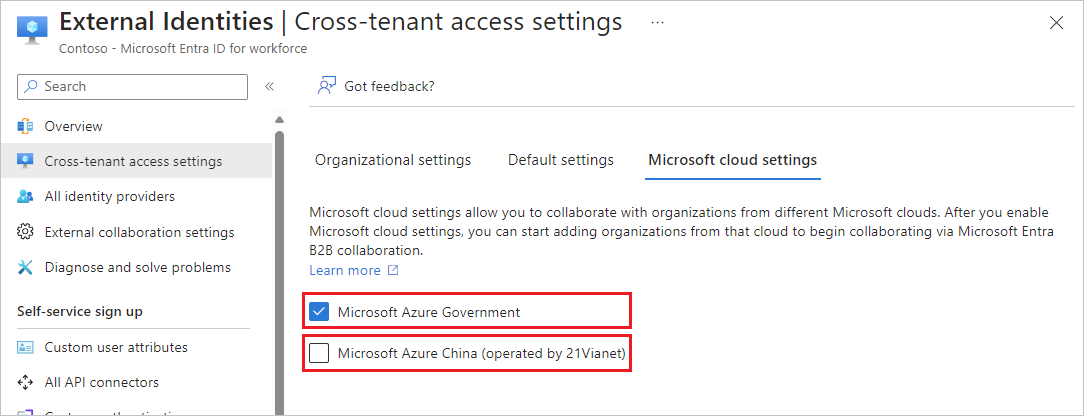
Browse to Identity > External Identities > Cross-tenant access settings, then select Microsoft cloud settings.
Select the checkboxes next to the external Microsoft Azure clouds you want to enable.
Note
Selecting a cloud doesn't automatically enable B2B collaboration with organizations in that cloud. You'll need to add the organization you want to collaborate with, as described in the next section.
Add the tenant to your organizational settings
Follow these steps to add the tenant you want to collaborate with to your Organizational settings.
Sign in to the Microsoft Entra admin center as at least a Security Administrator.
Browse to Identity > External Identities > Cross-tenant access settings, then select Organizational settings.
Select Add organization.
On the Add organization pane, type the tenant ID for the organization (cross-cloud lookup by domain name isn't currently available).
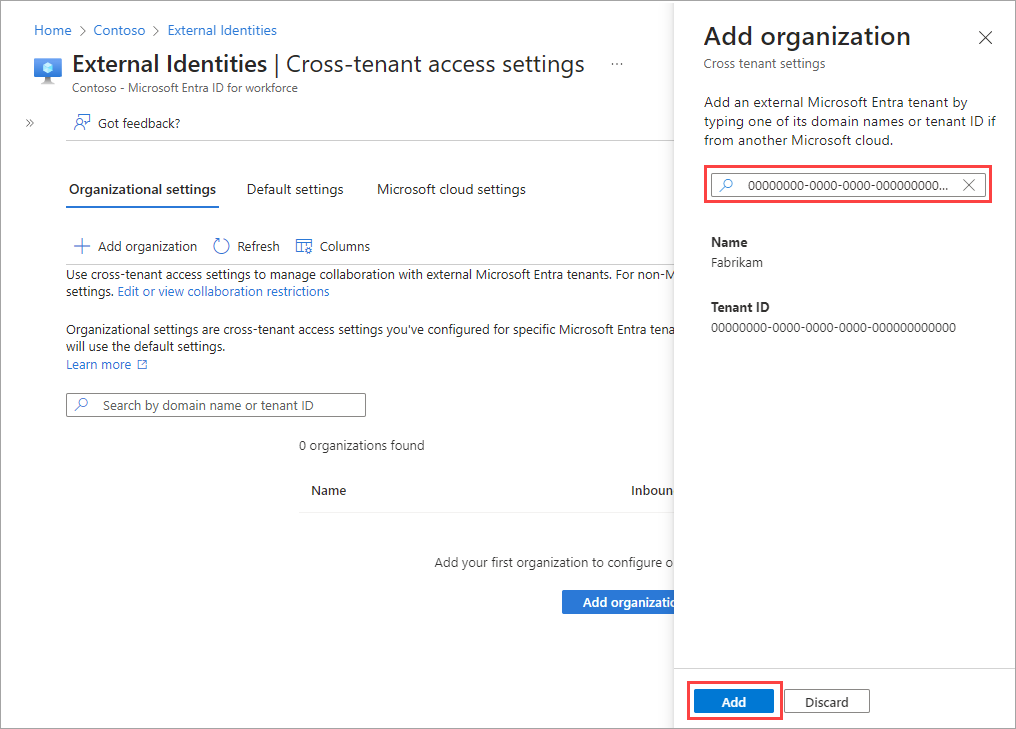
Select the organization in the search results, and then select Add.
The organization appears in the Organizational settings list. At this point, all access settings for this organization are inherited from your default settings.
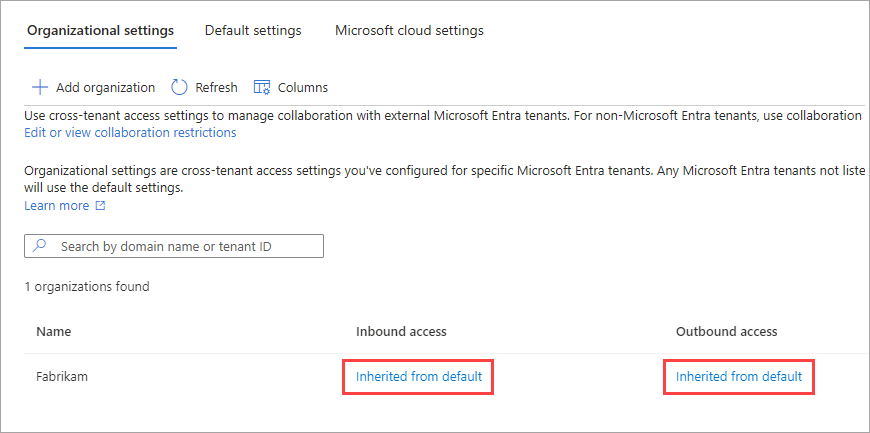
If you want to change the cross-tenant access settings for this organization, select the Inherited from default link under the Inbound access or Outbound access column. Then follow the detailed steps in these sections:
Sign-in endpoints
After you enable collaboration with an organization from a different Microsoft cloud, cross-cloud Microsoft Entra guest users can now sign in to your multitenant or Microsoft first-party apps by using a common endpoint (in other words, a general app URL that doesn't include your tenant context). During the sign-in process, the guest user chooses Sign-in options, and then selects Sign in to an organization. The user then types the name of your organization and continues signing in using their Microsoft Entra credentials.
Cross-cloud Microsoft Entra guest users can also use application endpoints that include your tenant information, for example:
https://myapps.microsoft.com/?tenantid=<your tenant ID>https://myapps.microsoft.com/<your verified domain>.onmicrosoft.comhttps://contoso.sharepoint.com/sites/testsite
You can also give cross-cloud Microsoft Entra guest users a direct link to an application or resource by including your tenant information, for example https://myapps.microsoft.com/signin/X/<application ID?tenantId=<your tenant ID>.
Supported scenarios with cross-cloud Microsoft Entra guest users
The following scenarios are supported when collaborating with an organization from a different Microsoft cloud:
- Use B2B collaboration to invite a user in the partner tenant to access resources in your organization, including web line-of-business apps, SaaS apps, and SharePoint Online sites, documents, and files.
- Use B2B collaboration to share Power BI content to a user in the partner tenant.
- Apply Conditional Access policies to the B2B collaboration user and opt to trust multifactor authentication or device claims (compliant claims and Microsoft Entra hybrid joined claims) from the user’s home tenant.
Note
Enabling the SharePoint and OneDrive integration with Microsoft Entra B2B will provide the best experience for inviting users from another Microsoft cloud within SharePoint and OneDrive.
Next steps
See Configure external collaboration settings for B2B collaboration with non Microsoft Entra identities, social identities, and non-IT managed external accounts.