Configure managed identities for Azure resources on a virtual machine scale set
Managed identities for Azure resources is a feature of Microsoft Entra ID. Each of the Azure services that support managed identities for Azure resources are subject to their own timeline. Make sure you review the availability status of managed identities for your resource and known issues before you begin.
Managed identities for Azure resources provide Azure services with an automatically managed identity in Microsoft Entra ID. You can use this identity to authenticate to any service that supports Microsoft Entra authentication, without having credentials in your code.
For information about Azure Policy definition and details, see Use Azure Policy to assign managed identities (preview).
In this article, using the Azure portal, you learn how to perform the following managed identities for Azure resources operations on a virtual machine scale set:
If you're unfamiliar with managed identities for Azure resources, check out the overview section.
If you don't already have an Azure account, sign up for a free account before continuing.
To perform the management operations in this article, your account needs the following Azure role assignments:
Note
No additional Microsoft Entra directory role assignments required.
- Virtual Machine Contributor to enable and remove system-assigned managed identity from a virtual machine scale set.
System-assigned managed identity
In this section, you will learn how to enable and disable the system-assigned managed identity using the Azure portal.
Enable system-assigned managed identity during creation of a virtual machine scale set
Currently, the Azure portal does not support enabling system-assigned managed identity during the creation of a virtual machine scale set. Instead, refer to the following virtual machine scale set creation Quickstart article to first create a virtual machine scale set, and then proceed to the next section for details on enabling system-assigned managed identity on a virtual machine scale set:
Enable system-assigned managed identity on an existing virtual machine scale set
Tip
Steps in this article might vary slightly based on the portal you start from.
To enable the system-assigned managed identity on a virtual machine scale set that was originally provisioned without it:
Sign in to the Azure portal using an account associated with the Azure subscription that contains the virtual machine scale set.
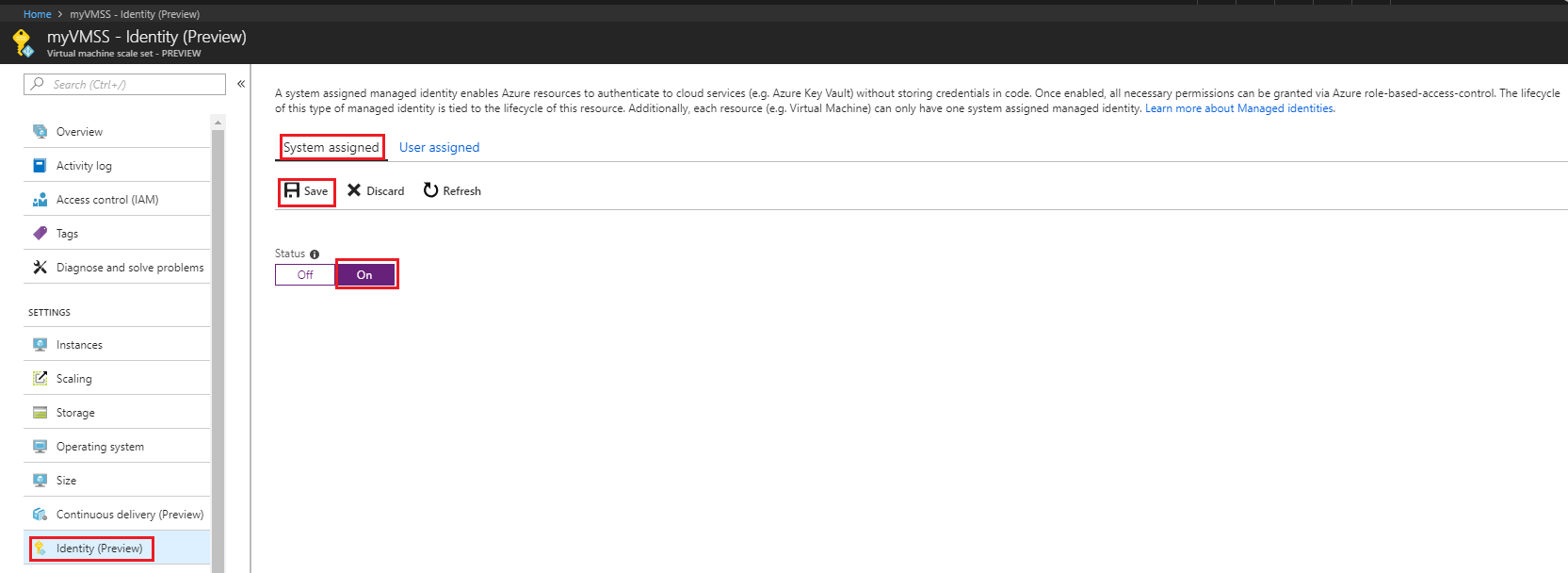
Navigate to the desired virtual machine scale set.
Under System assigned, Status, select On and then click Save:
Remove system-assigned managed identity from a virtual machine scale set
If you have a virtual machine scale set that no longer needs a system-assigned managed identity:
Sign in to the Azure portal using an account associated with the Azure subscription that contains the virtual machine scale set. Also make sure your account belongs to a role that gives you write permissions on the virtual machine scale set.
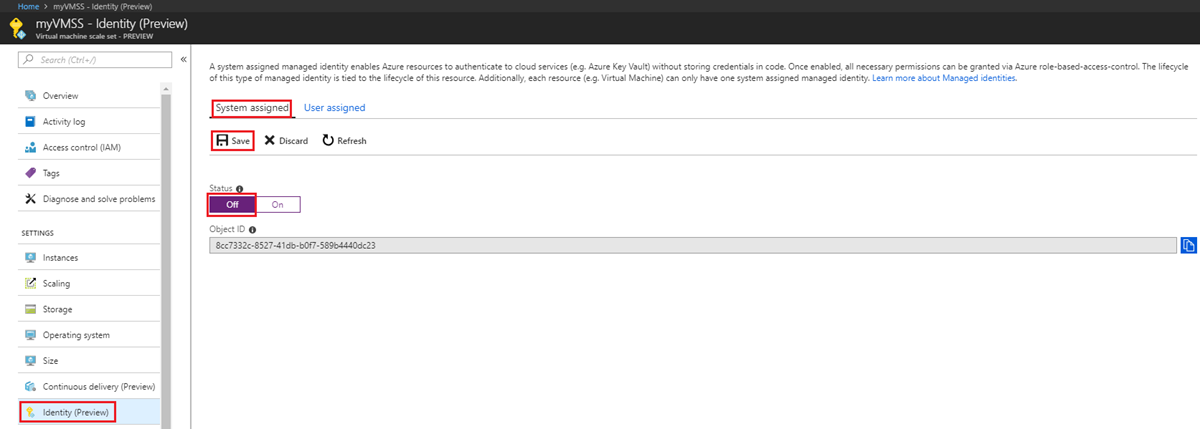
Navigate to the desired virtual machine scale set.
Under System assigned, Status, select Off and then click Save:
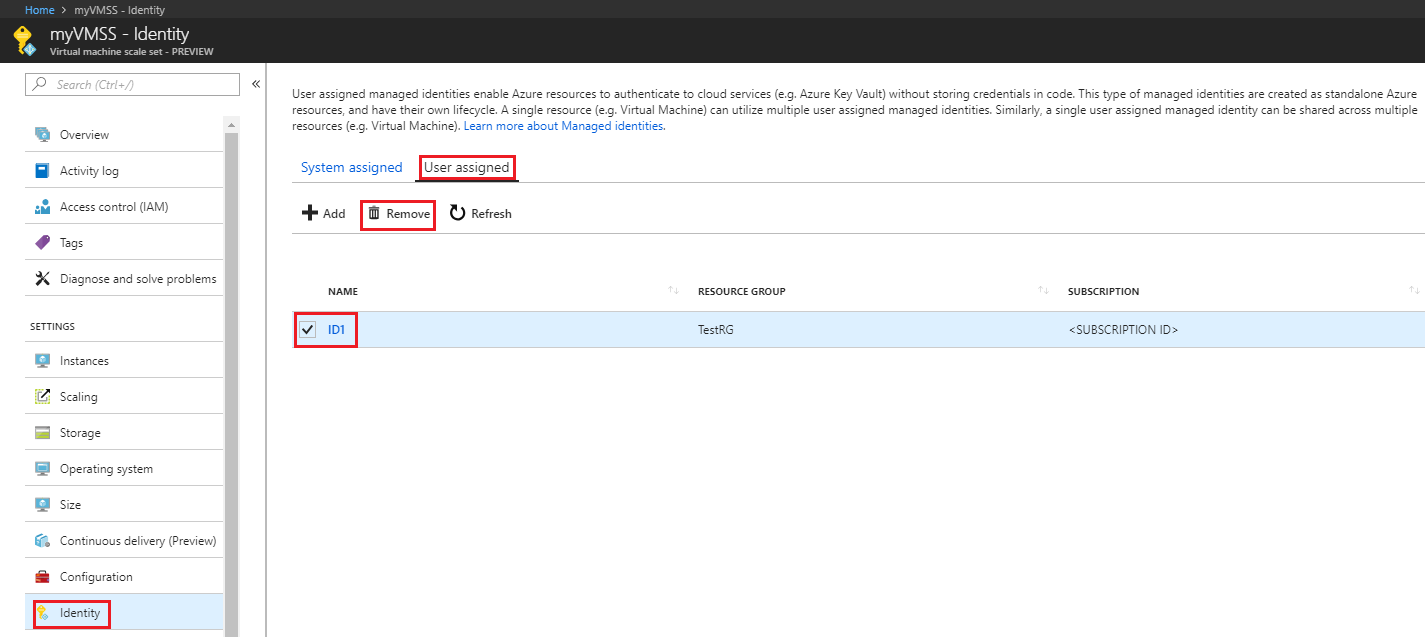
User-assigned managed identity
In this section, you learn how to add and remove a user-assigned managed identity from a virtual machine scale set using the Azure portal.
Assign a user-assigned managed identity during the creation of a virtual machine scale set
Currently, the Azure portal does not support assigning a user-assigned managed identity during the creation of a virtual machine scale set. Instead, refer to the following virtual machine scale set creation Quickstart article to first create a virtual machine scale set, and then proceed to the next section for details on assigning a user-assigned managed identity to it:
Assign a user-assigned managed identity to an existing virtual machine scale set
Sign in to the Azure portal using an account associated with the Azure subscription that contains the virtual machine scale set.
Navigate to the desired virtual machine scale set and click Identity, User assigned and then +Add.
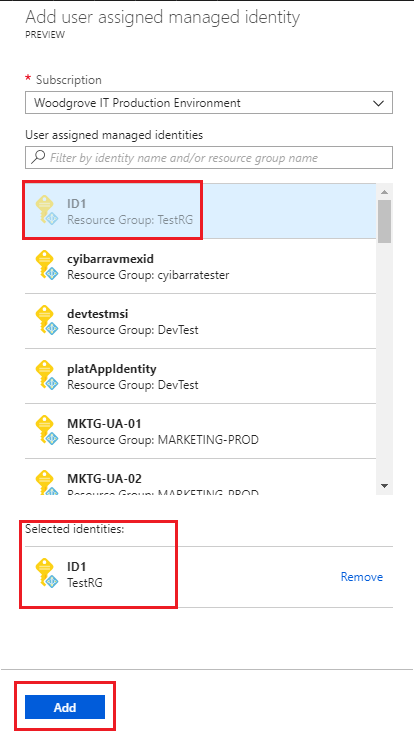
Click the user-assigned identity you want to add to the virtual machine scale set and then click Add.

Remove a user-assigned managed identity from a virtual machine scale set
Sign in to the Azure portal using an account associated with the Azure subscription that contains the VM.
Navigate to the desired virtual machine scale set and click Identity, User assigned, the name of the user-assigned managed identity you want to delete and then click Remove (click Yes in the confirmation pane).
Next steps
- Using the Azure portal, give an Azure virtual machine scale set managed identity access to another Azure resource.
In this article, you learn how to perform the following managed identities for Azure resources operations on an Azure virtual machine scale set, using the Azure CLI:
- Enable and disable the system-assigned managed identity on an Azure virtual machine scale set
- Add and remove a user-assigned managed identity on an Azure virtual machine scale set
If you don't already have an Azure account, sign up for a free account before continuing.
Prerequisites
If you're unfamiliar with managed identities for Azure resources, see What are managed identities for Azure resources?. To learn about system-assigned and user-assigned managed identity types, see Managed identity types.
To perform the management operations in this article, your account needs the following Azure role-based access control assignments:
Virtual Machine Contributor to create a virtual machine scale set and enable and remove system and/or user-assigned managed identity from a virtual machine scale set.
Managed Identity Contributor role to create a user-assigned managed identity.
Managed Identity Operator role to assign and remove a user-assigned managed identity from and to a virtual machine scale set.
Note
No additional Microsoft Entra directory role assignments required.
Use the Bash environment in Azure Cloud Shell. For more information, see Quickstart for Bash in Azure Cloud Shell.
If you prefer to run CLI reference commands locally, install the Azure CLI. If you're running on Windows or macOS, consider running Azure CLI in a Docker container. For more information, see How to run the Azure CLI in a Docker container.
If you're using a local installation, sign in to the Azure CLI by using the az login command. To finish the authentication process, follow the steps displayed in your terminal. For other sign-in options, see Sign in with the Azure CLI.
When you're prompted, install the Azure CLI extension on first use. For more information about extensions, see Use extensions with the Azure CLI.
Run az version to find the version and dependent libraries that are installed. To upgrade to the latest version, run az upgrade.
System-assigned managed identity
In this section, you learn how to enable and disable the system-assigned managed identity for an Azure virtual machine scale set using Azure CLI.
Enable system-assigned managed identity during creation of an Azure virtual machine scale set
To create a virtual machine scale set with the system-assigned managed identity enabled:
Create a resource group for containment and deployment of your virtual machine scale set and its related resources, using az group create. You can skip this step if you already have a resource group you would like to use instead:
az group create --name myResourceGroup --location westusCreate a virtual machine scale set. The following example creates a virtual machine scale set named myVMSS with a system-assigned managed identity, as requested by the
--assign-identityparameter, with the specified--roleand--scope. The--admin-usernameand--admin-passwordparameters specify the administrative user name and password account for virtual machine sign-in. Update these values as appropriate for your environment:az vmss create --resource-group myResourceGroup --name myVMSS --image win2016datacenter --upgrade-policy-mode automatic --custom-data cloud-init.txt --admin-username azureuser --admin-password myPassword12 --assign-identity --generate-ssh-keys --role contributor --scope mySubscription
Enable system-assigned managed identity on an existing Azure virtual machine scale set
If you need to Enable the system-assigned managed identity on an existing Azure virtual machine scale set:
az vmss identity assign -g myResourceGroup -n myVMSS
Disable system-assigned managed identity from an Azure virtual machine scale set
If you have a virtual machine scale set that no longer needs the system-assigned managed identity, but still needs user-assigned managed identities, use the following command:
az vmss update -n myVM -g myResourceGroup --set identity.type='UserAssigned'
If you have a virtual machine that no longer needs system-assigned managed identity and it has no user-assigned managed identities, use the following command:
Note
The value none is case sensitive. It must be lowercase.
az vmss update -n myVM -g myResourceGroup --set identity.type="none"
User-assigned managed identity
In this section, you learn how to enable and remove a user-assigned managed identity using Azure CLI.
Assign a user-assigned managed identity during the creation of a virtual machine scale set
This section walks you through creation of a virtual machine scale set and assignment of a user-assigned managed identity to the virtual machine scale set. If you already have a virtual machine scale set you want to use, skip this section and proceed to the next.
You can skip this step if you already have a resource group you would like to use. Create a resource group for containment and deployment of your user-assigned managed identity, using az group create. Be sure to replace the
<RESOURCE GROUP>and<LOCATION>parameter values with your own values. :az group create --name <RESOURCE GROUP> --location <LOCATION>Create a user-assigned managed identity using az identity create. The
-gparameter specifies the resource group where the user-assigned managed identity is created, and the-nparameter specifies its name. Be sure to replace the<RESOURCE GROUP>and<USER ASSIGNED IDENTITY NAME>parameter values with your own values:Important
When you create user-assigned managed identities, the name must start with a letter or number, and may include a combination of alphanumeric characters, hyphens (-) and underscores (_). For the assignment to a virtual machine or virtual machine scale set to work properly, the name is limited to 24 characters. For more information, see FAQs and known issues.
az identity create -g <RESOURCE GROUP> -n <USER ASSIGNED IDENTITY NAME>The response contains details for the user-assigned managed identity created, similar to the following. The resource
idvalue assigned to the user-assigned managed identity is used in the following step.{ "clientId": "73444643-8088-4d70-9532-c3a0fdc190fz", "clientSecretUrl": "https://control-westcentralus.identity.azure.net/subscriptions/<SUBSCRIPTON ID>/resourcegroups/<RESOURCE GROUP>/providers/Microsoft.ManagedIdentity/userAssignedIdentities/<USER ASSIGNED IDENTITY NAME>/credentials?tid=5678&oid=9012&aid=73444643-8088-4d70-9532-c3a0fdc190fz", "id": "/subscriptions/<SUBSCRIPTON ID>/resourcegroups/<RESOURCE GROUP>/providers/Microsoft.ManagedIdentity/userAssignedIdentities/<USER ASSIGNED IDENTITY NAME>", "location": "westcentralus", "name": "<USER ASSIGNED IDENTITY NAME>", "principalId": "e5fdfdc1-ed84-4d48-8551-fe9fb9dedfll", "resourceGroup": "<RESOURCE GROUP>", "tags": {}, "tenantId": "733a8f0e-ec41-4e69-8ad8-971fc4b533bl", "type": "Microsoft.ManagedIdentity/userAssignedIdentities" }Create a virtual machine scale set. The following example creates a virtual machine scale set associated with the new user-assigned managed identity, as specified by the
--assign-identityparameter, with the specified--roleand--scope. Be sure to replace the<RESOURCE GROUP>,<VMSS NAME>,<USER NAME>,<PASSWORD>,<USER ASSIGNED IDENTITY>,<ROLE>, and<SUBSCRIPTION>parameter values with your own values.az vmss create --resource-group <RESOURCE GROUP> --name <VMSS NAME> --image <SKU Linux Image> --admin-username <USER NAME> --admin-password <PASSWORD> --assign-identity <USER ASSIGNED IDENTITY> --role <ROLE> --scope <SUBSCRIPTION>
Assign a user-assigned managed identity to an existing virtual machine scale set
Create a user-assigned managed identity using az identity create. The
-gparameter specifies the resource group where the user-assigned managed identity is created, and the-nparameter specifies its name. Be sure to replace the<RESOURCE GROUP>and<USER ASSIGNED IDENTITY NAME>parameter values with your own values:az identity create -g <RESOURCE GROUP> -n <USER ASSIGNED IDENTITY NAME>The response contains details for the user-assigned managed identity created, similar to the following.
{ "clientId": "73444643-8088-4d70-9532-c3a0fdc190fz", "clientSecretUrl": "https://control-westcentralus.identity.azure.net/subscriptions/<SUBSCRIPTON ID>/resourcegroups/<RESOURCE GROUP>/providers/Microsoft.ManagedIdentity/userAssignedIdentities/<USER ASSIGNED IDENTITY >/credentials?tid=5678&oid=9012&aid=73444643-8088-4d70-9532-c3a0fdc190fz", "id": "/subscriptions/<SUBSCRIPTON ID>/resourcegroups/<RESOURCE GROUP>/providers/Microsoft.ManagedIdentity/userAssignedIdentities/<USER ASSIGNED IDENTITY>", "location": "westcentralus", "name": "<USER ASSIGNED IDENTITY>", "principalId": "e5fdfdc1-ed84-4d48-8551-fe9fb9dedfll", "resourceGroup": "<RESOURCE GROUP>", "tags": {}, "tenantId": "733a8f0e-ec41-4e69-8ad8-971fc4b533bl", "type": "Microsoft.ManagedIdentity/userAssignedIdentities" }Assign the user-assigned managed identity to your virtual machine scale set. Be sure to replace the
<RESOURCE GROUP>and<VIRTUAL MACHINE SCALE SET NAME>parameter values with your own values. The<USER ASSIGNED IDENTITY>is the user-assigned identity's resourcenameproperty, as created in the previous step:az vmss identity assign -g <RESOURCE GROUP> -n <VIRTUAL MACHINE SCALE SET NAME> --identities <USER ASSIGNED IDENTITY>
Remove a user-assigned managed identity from an Azure virtual machine scale set
To remove a user-assigned managed identity from a virtual machine scale set use az vmss identity remove. If this is the only user-assigned managed identity assigned to the virtual machine scale set, UserAssigned is removed from the identity type value. Be sure to replace the <RESOURCE GROUP> and <VIRTUAL MACHINE SCALE SET NAME> parameter values with your own values. The <USER ASSIGNED IDENTITY> is the user-assigned managed identity's name property, which can be found in the identity section of the virtual machine scale set using az vmss identity show:
az vmss identity remove -g <RESOURCE GROUP> -n <VIRTUAL MACHINE SCALE SET NAME> --identities <USER ASSIGNED IDENTITY>
If your virtual machine scale set doesn't have a system-assigned managed identity and you want to remove all user-assigned managed identities from it, use the following command:
Note
The value none is case sensitive. It must be lowercase.
az vmss update -n myVMSS -g myResourceGroup --set identity.type="none" identity.userAssignedIdentities=null
If your virtual machine scale set has both system-assigned and user-assigned managed identities, you can remove all the user-assigned identities by switching to use only system-assigned managed identity. Use the following command:
az vmss update -n myVMSS -g myResourceGroup --set identity.type='SystemAssigned' identity.userAssignedIdentities=null
Next steps
- Managed identities for Azure resources overview
- For the full Azure virtual machine scale set creation Quickstart, see Create a Virtual Machine Scale Set with CLI
In this article, using PowerShell, you learn how to perform the managed identities for Azure resources operations on a virtual machine scale set:
- Enable and disable the system-assigned managed identity on a virtual machine scale set
- Add and remove a user-assigned managed identity on a virtual machine scale set
Note
We recommend that you use the Azure Az PowerShell module to interact with Azure. See Install Azure PowerShell to get started. To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az.
Prerequisites
If you're unfamiliar with managed identities for Azure resources, check out the overview section. Be sure to review the difference between a system-assigned and user managed assigned identity.
If you don't already have an Azure account, sign up for a free account before continuing.
To perform the management operations in this article, your account needs the following Azure role-based access control assignments:
Note
No additional Microsoft Entra directory role assignments required.
- Virtual Machine Contributor to create a virtual machine scale set and enable and remove system-assigned managed and/or user-assigned managed identity from a virtual machine scale set.
- Managed Identity Contributor role to create a user-assigned managed identity.
- Managed Identity Operator role to assign and remove a user-assigned managed identity from and to a virtual machine scale set.
To run the example scripts, you have two options:
- Use the Azure Cloud Shell, which you can open using the Try It button on the top-right corner of code blocks.
- Run scripts locally by installing the latest version of Azure PowerShell, then sign in to Azure using
Connect-AzAccount.
System-assigned managed identity
In this section, you learn how to enable and remove a system-assigned managed identity using Azure PowerShell.
Enable system-assigned managed identity during the creation of an Azure virtual machine scale set
To create a virtual machine scale set with the system-assigned managed identity enabled:
Refer to Example 1 in the New-AzVmssConfig cmdlet reference article to create a virtual machine scale set with a system-assigned managed identity. Add the parameter
-IdentityType SystemAssignedto theNew-AzVmssConfigcmdlet:$VMSS = New-AzVmssConfig -Location $Loc -SkuCapacity 2 -SkuName "Standard_A0" -UpgradePolicyMode "Automatic" -NetworkInterfaceConfiguration $NetCfg -IdentityType SystemAssigned`
Enable system-assigned managed identity on an existing Azure virtual machine scale set
If you need to enable a system-assigned managed identity on an existing Azure virtual machine scale set:
Make sure the Azure account you're using belongs to a role that gives you write permissions on the virtual machine scale set, such as "Virtual Machine Contributor".
Retrieve the virtual machine scale set properties using the
Get-AzVmsscmdlet. Then to enable a system-assigned managed identity, use the-IdentityTypeswitch on the Update-AzVmss cmdlet:Update-AzVmss -ResourceGroupName myResourceGroup -Name -myVmss -IdentityType "SystemAssigned"
Disable the system-assigned managed identity from an Azure virtual machine scale set
If you have a virtual machine scale set that no longer needs the system-assigned managed identity but still needs user-assigned managed identities, use the following cmdlet:
Make sure your account belongs to a role that gives you write permissions on the virtual machine scale set, such as "Virtual Machine Contributor".
Run the following cmdlet:
Update-AzVmss -ResourceGroupName myResourceGroup -Name myVmss -IdentityType "UserAssigned"If you have a virtual machine scale set that no longer needs system-assigned managed identity and it has no user-assigned managed identities, use the following command:
Update-AzVmss -ResourceGroupName myResourceGroup -Name myVmss -IdentityType None
User-assigned managed identity
In this section, you learn how to add and remove a user-assigned managed identity from a virtual machine scale set using Azure PowerShell.
Assign a user-assigned managed identity during creation of an Azure virtual machine scale set
Creating a new virtual machine scale set with a user-assigned managed identity isn't currently supported via PowerShell. See the next section on how to add a user-assigned managed identity to an existing virtual machine scale set. Check back for updates.
Assign a user-assigned managed identity to an existing Azure virtual machine scale set
To assign a user-assigned managed identity to an existing Azure virtual machine scale set:
Make sure your account belongs to a role that gives you write permissions on the virtual machine scale set, such as "Virtual Machine Contributor".
Retrieve the virtual machine scale set properties using the
Get-AzVMcmdlet. Then to assign a user-assigned managed identity to the virtual machine scale set, use the-IdentityTypeand-IdentityIDswitch on the Update-AzVmss cmdlet. Replace<VM NAME>,<SUBSCRIPTION ID>,<RESROURCE GROUP>,<USER ASSIGNED ID1>,USER ASSIGNED ID2with your own values.Important
When you create user-assigned managed identities, the name must start with a letter or number, and may include a combination of alphanumeric characters, hyphens (-) and underscores (_). For the assignment to a virtual machine or virtual machine scale set to work properly, the name is limited to 24 characters. For more information, see FAQs and known issues.
Update-AzVmss -ResourceGroupName <RESOURCE GROUP> -Name <VMSS NAME> -IdentityType UserAssigned -IdentityID "<USER ASSIGNED ID1>","<USER ASSIGNED ID2>"
Remove a user-assigned managed identity from an Azure virtual machine scale set
If your virtual machine scale set has multiple user-assigned managed identities, you can remove all but the last one using the following commands. Be sure to replace the <RESOURCE GROUP> and <VIRTUAL MACHINE SCALE SET NAME> parameter values with your own values. The <USER ASSIGNED IDENTITY NAME> is the user-assigned managed identity's name property, which should remain on the virtual machine scale set. This information can be found in the identity section of the virtual machine scale set using az vmss show:
Update-AzVmss -ResourceGroupName myResourceGroup -Name myVmss -IdentityType UserAssigned -IdentityID "<USER ASSIGNED IDENTITY NAME>"
If your virtual machine scale set doesn't have a system-assigned managed identity and you want to remove all user-assigned managed identities from it, use the following command:
Update-AzVmss -ResourceGroupName myResourceGroup -Name myVmss -IdentityType None
If your virtual machine scale set has both system-assigned and user-assigned managed identities, you can remove all the user-assigned managed identities by switching to use only system-assigned managed identity.
Update-AzVmss -ResourceGroupName myResourceGroup -Name myVmss -IdentityType "SystemAssigned"
Next steps
For the full Azure VM creation Quickstarts, see:
In this article, you learn how to perform the following managed identities for Azure resources operations on an Azure virtual machine scale set, using Azure Resource Manager deployment template:
- Enable and disable the system-assigned managed identity on an Azure virtual machine scale set
- Add and remove a user-assigned managed identity on an Azure virtual machine scale set
Prerequisites
If you're unfamiliar with managed identities for Azure resources, check out the overview section. Be sure to review the difference between a system-assigned and user-assigned managed identity.
If you don't already have an Azure account, sign up for a free account before continuing.
To perform the management operations in this article, your account needs the following Azure role-based access control assignments:
Note
No additional Microsoft Entra directory role assignments required.
- Virtual Machine Contributor to create a virtual machine scale set and enable and remove system and/or user-assigned managed identity from a virtual machine scale set.
- Managed Identity Contributor role to create a user-assigned managed identity.
- Managed Identity Operator role to assign and remove a user-assigned managed identity from and to a virtual machine scale set.
Azure Resource Manager templates
As with the Azure portal and scripting, Azure Resource Manager templates provide the ability to deploy new or modified resources defined by an Azure resource group. Several options are available for template editing and deployment, both local and portal-based, including:
- Using a custom template from the Azure Marketplace, which allows you to create a template from scratch, or base it on an existing common or quickstart template.
- Deriving from an existing resource group, by exporting a template from either the original deployment, or from the current state of the deployment.
- Using a local JSON editor (such as VS Code), and then uploading and deploying by using PowerShell or CLI.
- Using the Visual Studio Azure Resource Group project to both create and deploy a template.
Regardless of the option you choose, template syntax is the same during initial deployment and redeployment. Enabling managed identities for Azure resources on a new or existing VM is done in the same manner. Also, by default, Azure Resource Manager does an incremental update to deployments.
System-assigned managed identity
In this section, you will enable and disable the system-assigned managed identity using an Azure Resource Manager template.
Enable system-assigned managed identity during the creation of a virtual machines scale set or an existing virtual machine scale set
Whether you sign in to Azure locally or via the Azure portal, use an account that is associated with the Azure subscription that contains the virtual machine scale set.
To enable the system-assigned managed identity, load the template into an editor, locate the
Microsoft.Compute/virtualMachinesScaleSetsresource of interest within the resources section and add theidentityproperty at the same level as the"type": "Microsoft.Compute/virtualMachinesScaleSets"property. Use the following syntax:"identity": { "type": "SystemAssigned" }When you're done, the following sections should be added to the resource section of your template and should resemble the example shown below:
"resources": [ { //other resource provider properties... "apiVersion": "2018-06-01", "type": "Microsoft.Compute/virtualMachineScaleSets", "name": "[variables('vmssName')]", "location": "[resourceGroup().location]", "identity": { "type": "SystemAssigned", }, "properties": { //other resource provider properties... "virtualMachineProfile": { //other virtual machine profile properties... } } } ]
Disable a system-assigned managed identity from an Azure virtual machine scale set
If you have a virtual machine scale set that no longer needs a system-assigned managed identity:
Whether you sign in to Azure locally or via the Azure portal, use an account that is associated with the Azure subscription that contains the virtual machine scale set.
Load the template into an editor and locate the
Microsoft.Compute/virtualMachineScaleSetsresource of interest within theresourcessection. If you have a VM that only has system-assigned managed identity, you can disable it by changing the identity type toNone.Microsoft.Compute/virtualMachineScaleSets API version 2018-06-01
If your apiVersion is
2018-06-01and your VM has both system and user-assigned managed identities, removeSystemAssignedfrom the identity type and keepUserAssignedalong with the userAssignedIdentities dictionary values.Microsoft.Compute/virtualMachineScaleSets API version 2018-06-01
If your apiVersion is
2017-12-01and your virtual machine scale set has both system and user-assigned managed identities, removeSystemAssignedfrom the identity type and keepUserAssignedalong with theidentityIdsarray of the user-assigned managed identities.The following example shows you how to remove a system-assigned managed identity from a virtual machine scale set with no user-assigned managed identities:
{ "name": "[variables('vmssName')]", "apiVersion": "2018-06-01", "location": "[parameters(Location')]", "identity": { "type": "None" } }
User-assigned managed identity
In this section, you assign a user-assigned managed identity to a virtual machine scale set using Azure Resource Manager template.
Note
To create a user-assigned managed identity using an Azure Resource Manager Template, see Create a user-assigned managed identity.
Assign a user-assigned managed identity to a virtual machine scale set
Under the
resourceselement, add the following entry to assign a user-assigned managed identity to your virtual machine scale set. Be sure to replace<USERASSIGNEDIDENTITY>with the name of the user-assigned managed identity you created.Microsoft.Compute/virtualMachineScaleSets API version 2018-06-01
If your apiVersion is
2018-06-01, your user-assigned managed identities are stored in theuserAssignedIdentitiesdictionary format and the<USERASSIGNEDIDENTITYNAME>value must be stored in a variable defined in thevariablessection of your template.{ "name": "[variables('vmssName')]", "apiVersion": "2018-06-01", "location": "[parameters(Location')]", "identity": { "type": "userAssigned", "userAssignedIdentities": { "[resourceID('Microsoft.ManagedIdentity/userAssignedIdentities/',variables('<USERASSIGNEDIDENTITYNAME>'))]": {} } } }Microsoft.Compute/virtualMachineScaleSets API version 2017-12-01
If your
apiVersionis2017-12-01or earlier, your user-assigned managed identities are stored in theidentityIdsarray and the<USERASSIGNEDIDENTITYNAME>value must be stored in a variable defined in the variables section of your template.{ "name": "[variables('vmssName')]", "apiVersion": "2017-03-30", "location": "[parameters(Location')]", "identity": { "type": "userAssigned", "identityIds": [ "[resourceID('Microsoft.ManagedIdentity/userAssignedIdentities/',variables('<USERASSIGNEDIDENTITY>'))]" ] } }When you are done, your template should look similar to the following:
Microsoft.Compute/virtualMachineScaleSets API version 2018-06-01
"resources": [ { //other resource provider properties... "apiVersion": "2018-06-01", "type": "Microsoft.Compute/virtualMachineScaleSets", "name": "[variables('vmssName')]", "location": "[resourceGroup().location]", "identity": { "type": "UserAssigned", "userAssignedIdentities": { "[resourceID('Microsoft.ManagedIdentity/userAssignedIdentities/',variables('<USERASSIGNEDIDENTITYNAME>'))]": {} } }, "properties": { //other virtual machine properties... "virtualMachineProfile": { //other virtual machine profile properties... } } } ]Microsoft.Compute/virtualMachines API version 2017-12-01
"resources": [ { //other resource provider properties... "apiVersion": "2017-12-01", "type": "Microsoft.Compute/virtualMachineScaleSets", "name": "[variables('vmssName')]", "location": "[resourceGroup().location]", "identity": { "type": "UserAssigned", "identityIds": [ "[resourceID('Microsoft.ManagedIdentity/userAssignedIdentities/',variables('<USERASSIGNEDIDENTITYNAME>'))]" ] }, "properties": { //other virtual machine properties... "virtualMachineProfile": { //other virtual machine profile properties... } } } ]
Remove user-assigned managed identity from an Azure virtual machine scale set
If you have a virtual machine scale set that no longer needs a user-assigned managed identity:
Whether you sign in to Azure locally or via the Azure portal, use an account that is associated with the Azure subscription that contains the virtual machine scale set.
Load the template into an editor and locate the
Microsoft.Compute/virtualMachineScaleSetsresource of interest within theresourcessection. If you have a virtual machine scale set that only has user-assigned managed identity, you can disable it by changing the identity type toNone.The following example shows you how to remove all user-assigned managed identities from a VM with no system-assigned managed identities:
{ "name": "[variables('vmssName')]", "apiVersion": "2018-06-01", "location": "[parameters(Location')]", "identity": { "type": "None" } }Microsoft.Compute/virtualMachineScaleSets API version 2018-06-01
To remove a single user-assigned managed identity from a virtual machine scale set, remove it from the
userAssignedIdentitiesdictionary.If you have a system-assigned identity, keep it in the
typevalue under theidentityvalue.Microsoft.Compute/virtualMachineScaleSets API version 2017-12-01
To remove a single user-assigned managed identity from a virtual machine scale set, remove it from the
identityIdsarray.If you have a system-assigned managed identity, keep it in the
typevalue under theidentityvalue.
Next steps
In this article, using CURL to make calls to the Azure Resource Manager REST endpoint, you learn how to perform the following managed identities for Azure resources operations on a virtual machine scale set:
- Enable and disable the system-assigned managed identity on an Azure virtual machine scale set
- Add and remove a user-assigned managed identity on an Azure virtual machine scale set
If you don't already have an Azure account, sign up for a free account before continuing.
Prerequisites
If you're unfamiliar with managed identities for Azure resources, see What are managed identities for Azure resources?. To learn about system-assigned and user-assigned managed identity types, see Managed identity types.
To perform the management operations in this article, your account needs the following Azure role assignments:
Virtual Machine Contributor to create a virtual machine scale set and enable and remove system and/or user-assigned managed identity from a virtual machine scale set.
Managed Identity Contributor role to create a user-assigned managed identity.
Managed Identity Operator role to assign and remove a user-assigned identity from and to a virtual machine scale set.
Note
No additional Microsoft Entra directory role assignments required.
Use the Bash environment in Azure Cloud Shell. For more information, see Quickstart for Bash in Azure Cloud Shell.
If you prefer to run CLI reference commands locally, install the Azure CLI. If you're running on Windows or macOS, consider running Azure CLI in a Docker container. For more information, see How to run the Azure CLI in a Docker container.
If you're using a local installation, sign in to the Azure CLI by using the az login command. To finish the authentication process, follow the steps displayed in your terminal. For other sign-in options, see Sign in with the Azure CLI.
When you're prompted, install the Azure CLI extension on first use. For more information about extensions, see Use extensions with the Azure CLI.
Run az version to find the version and dependent libraries that are installed. To upgrade to the latest version, run az upgrade.
System-assigned managed identity
In this section, you learn how to enable and disable system-assigned managed identity on a virtual machine scale set using CURL to make calls to the Azure Resource Manager REST endpoint.
Enable system-assigned managed identity during creation of a virtual machine scale set
To create a virtual machine scale set with system-assigned managed identity enabled, you need to create a virtual machine scale set and retrieve an access token to use CURL to call the Resource Manager endpoint with the system-assigned managed identity type value.
Create a resource group for containment and deployment of your virtual machine scale set and its related resources, using az group create. You can skip this step if you already have resource group you would like to use instead:
az group create --name myResourceGroup --location westusCreate a network interface for your virtual machine scale set:
az network nic create -g myResourceGroup --vnet-name myVnet --subnet mySubnet -n myNicRetrieve a Bearer access token, which you will use in the next step in the Authorization header to create your virtual machine scale set with a system-assigned managed identity.
az account get-access-tokenUsing Azure Cloud Shell, create a virtual machine scale set using CURL to call the Azure Resource Manager REST endpoint. The following example creates a virtual machine scale set named myVMSS in the myResourceGroup with a system-assigned managed identity, as identified in the request body by the value
"identity":{"type":"SystemAssigned"}. Replace<ACCESS TOKEN>with the value you received in the previous step when you requested a Bearer access token and the<SUBSCRIPTION ID>value as appropriate for your environment.curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01' -X PUT -d '{"sku":{"tier":"Standard","capacity":3,"name":"Standard_D1_v2"},"location":"eastus","identity":{"type":"SystemAssigned"},"properties":{"overprovision":true,"virtualMachineProfile":{"storageProfile":{"imageReference":{"sku":"2016-Datacenter","publisher":"MicrosoftWindowsServer","version":"latest","offer":"WindowsServer"},"osDisk":{"caching":"ReadWrite","managedDisk":{"storageAccountType":"StandardSSD_LRS"},"createOption":"FromImage"}},"osProfile":{"computerNamePrefix":"myVMSS","adminUsername":"azureuser","adminPassword":"myPassword12"},"networkProfile":{"networkInterfaceConfigurations":[{"name":"myVMSS","properties":{"primary":true,"enableIPForwarding":true,"ipConfigurations":[{"name":"myVMSS","properties":{"subnet":{"id":"/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Network/virtualNetworks/myVnet/subnets/mySubnet"}}}]}}]}},"upgradePolicy":{"mode":"Manual"}}}' -H "Content-Type: application/json" -H "Authorization: Bearer <ACCESS TOKEN>"PUT https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01 HTTP/1.1Request headers
Request header Description Content-Type Required. Set to application/json.Authorization Required. Set to a valid Beareraccess token.Request body
{ "sku":{ "tier":"Standard", "capacity":3, "name":"Standard_D1_v2" }, "location":"eastus", "identity":{ "type":"SystemAssigned" }, "properties":{ "overprovision":true, "virtualMachineProfile":{ "storageProfile":{ "imageReference":{ "sku":"2016-Datacenter", "publisher":"MicrosoftWindowsServer", "version":"latest", "offer":"WindowsServer" }, "osDisk":{ "caching":"ReadWrite", "managedDisk":{ "storageAccountType":"StandardSSD_LRS" }, "createOption":"FromImage" } }, "osProfile":{ "computerNamePrefix":"myVMSS", "adminUsername":"azureuser", "adminPassword":"myPassword12" }, "networkProfile":{ "networkInterfaceConfigurations":[ { "name":"myVMSS", "properties":{ "primary":true, "enableIPForwarding":true, "ipConfigurations":[ { "name":"myVMSS", "properties":{ "subnet":{ "id":"/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Network/virtualNetworks/myVnet/subnets/mySubnet" } } } ] } } ] } }, "upgradePolicy":{ "mode":"Manual" } } }
Enable system-assigned managed identity on an existing virtual machine scale set
To enable system-assigned managed identity on an existing virtual machine scale set, you need to acquire an access token and then use CURL to call the Resource Manager REST endpoint to update the identity type.
Retrieve a Bearer access token, which you will use in the next step in the Authorization header to create your virtual machine scale set with a system-assigned managed identity.
az account get-access-tokenUse the following CURL command to call the Azure Resource Manager REST endpoint to enable system-assigned managed identity on your virtual machine scale set as identified in the request body by the value
{"identity":{"type":"SystemAssigned"}for a virtual machine scale set named myVMSS. Replace<ACCESS TOKEN>with the value you received in the previous step when you requested a Bearer access token and the<SUBSCRIPTION ID>value as appropriate for your environment.Important
To ensure you don't delete any existing user-assigned managed identities that are assigned to the virtual machine scale set, you need to list the user-assigned managed identities by using this CURL command:
curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/<RESOURCE GROUP>/providers/Microsoft.Compute/virtualMachineScaleSets/<VMSS NAME>?api-version=2018-06-01' -H "Authorization: Bearer <ACCESS TOKEN>". If you have any user-assigned managed identities assigned to the virtual machine scale set as identified in theidentityvalue in the response, skip to step 3 that shows you how to retain user-assigned managed identities while enabling system-assigned managed identity on your virtual machine scale set.curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01' -X PATCH -d '{"identity":{"type":"SystemAssigned"}}' -H "Content-Type: application/json" -H Authorization:"Bearer <ACCESS TOKEN>"PATCH https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01 HTTP/1.1Request headers
Request header Description Content-Type Required. Set to application/json.Authorization Required. Set to a valid Beareraccess token.Request body
{ "identity":{ "type":"SystemAssigned" } }To enable system-assigned managed identity on a virtual machine scale set with existing user-assigned managed identities, you need to add
SystemAssignedto thetypevalue.For example, if your virtual machine scale set has the user-assigned managed identities
ID1andID2assigned to it, and you would like to add system-assigned managed identity to the virtual machine scale set, use the following CURL call. Replace<ACCESS TOKEN>and<SUBSCRIPTION ID>with values appropriate to your environment.API version
2018-06-01stores user-assigned managed identities in theuserAssignedIdentitiesvalue in a dictionary format as opposed to theidentityIdsvalue in an array format used in API version2017-12-01.API VERSION 2018-06-01
curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01' -X PATCH -d '{"identity":{"type":"SystemAssigned,UserAssigned", "userAssignedIdentities":{"/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1":{},"/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID2":{}}}}' -H "Content-Type: application/json" -H Authorization:"Bearer <ACCESS TOKEN>"PATCH https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01 HTTP/1.1Request headers
Request header Description Content-Type Required. Set to application/json.Authorization Required. Set to a valid Beareraccess token.Request body
{ "identity":{ "type":"SystemAssigned,UserAssigned", "userAssignedIdentities":{ "/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1":{ }, "/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID2":{ } } } }API VERSION 2017-12-01
curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2017-12-01' -X PATCH -d '{"identity":{"type":"SystemAssigned,UserAssigned", "identityIds":["/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1","/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID2"]}}' -H "Content-Type: application/json" -H Authorization:"Bearer <ACCESS TOKEN>"PATCH https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2017-12-01 HTTP/1.1Request headers
Request header Description Content-Type Required. Set to application/json.Authorization Required. Set to a valid Beareraccess token.Request body
{ "identity":{ "type":"SystemAssigned,UserAssigned", "identityIds":[ "/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1", "/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID2" ] } }
Disable system-assigned managed identity from a virtual machine scale set
To disable a system-assigned identity on an existing virtual machine scale set, you need to acquire an access token and then use CURL to call the Resource Manager REST endpoint to update the identity type to None.
Retrieve a Bearer access token, which you will use in the next step in the Authorization header to create your virtual machine scale set with a system-assigned managed identity.
az account get-access-tokenUpdate the virtual machine scale set using CURL to call the Azure Resource Manager REST endpoint to disable system-assigned managed identity. The following example disables system-assigned managed identity as identified in the request body by the value
{"identity":{"type":"None"}}from a virtual machine scale set named myVMSS. Replace<ACCESS TOKEN>with the value you received in the previous step when you requested a Bearer access token and the<SUBSCRIPTION ID>value as appropriate for your environment.Important
To ensure you don't delete any existing user-assigned managed identities that are assigned to the virtual machine scale set, you need to list the user-assigned managed identities by using this CURL command:
curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/<RESOURCE GROUP>/providers/Microsoft.Compute/virtualMachineScaleSets/<VMSS NAME>?api-version=2018-06-01' -H "Authorization: Bearer <ACCESS TOKEN>". If you have any user-assigned managed identity assigned to the virtual machine scale set, skip to step 3 that shows you how retain the user-assigned managed identities while removing the system-assigned managed identity from your virtual machine scale set.curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01' -X PATCH -d '{"identity":{"type":"None"}}' -H "Content-Type: application/json" -H Authorization:"Bearer <ACCESS TOKEN>"PATCH https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01 HTTP/1.1Request headers
Request header Description Content-Type Required. Set to application/json.Authorization Required. Set to a valid Beareraccess token.Request body
{ "identity":{ "type":"None" } }To remove system-assigned managed identity from a virtual machine scale set that has user-assigned managed identities, remove
SystemAssignedfrom the{"identity":{"type:" "}}value while keeping theUserAssignedvalue and theuserAssignedIdentitiesdictionary values if you are using API version 2018-06-01. If you are using API version 2017-12-01 or earlier, keep theidentityIdsarray.
User-assigned managed identity
In this section, you learn how to add and remove user-assigned managed identity on a virtual machine scale set using CURL to make calls to the Azure Resource Manager REST endpoint.
Assign a user-assigned managed identity during the creation of a virtual machine scale set
Retrieve a Bearer access token, which you will use in the next step in the Authorization header to create your virtual machine scale set with a system-assigned managed identity.
az account get-access-tokenCreate a network interface for your virtual machine scale set:
az network nic create -g myResourceGroup --vnet-name myVnet --subnet mySubnet -n myNicRetrieve a Bearer access token, which you will use in the next step in the Authorization header to create your virtual machine scale set with a system-assigned managed identity.
az account get-access-tokenCreate a user-assigned managed identity using the instructions found here: Create a user-assigned managed identity.
Create a virtual machine scale set using CURL to call the Azure Resource Manager REST endpoint. The following example creates a virtual machine scale set named myVMSS in the resource group myResourceGroup with a user-assigned managed identity
ID1, as identified in the request body by the value"identity":{"type":"UserAssigned"}. Replace<ACCESS TOKEN>with the value you received in the previous step when you requested a Bearer access token and the<SUBSCRIPTION ID>value as appropriate for your environment.API VERSION 2018-06-01
curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01' -X PUT -d '{"sku":{"tier":"Standard","capacity":3,"name":"Standard_D1_v2"},"location":"eastus","identity":{"type":"UserAssigned","userAssignedIdentities":{"/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1":{}}},"properties":{"overprovision":true,"virtualMachineProfile":{"storageProfile":{"imageReference":{"sku":"2016-Datacenter","publisher":"MicrosoftWindowsServer","version":"latest","offer":"WindowsServer"},"osDisk":{"caching":"ReadWrite","managedDisk":{"storageAccountType":"StandardSSD_LRS"},"createOption":"FromImage"}},"osProfile":{"computerNamePrefix":"myVMSS","adminUsername":"azureuser","adminPassword":"myPassword12"},"networkProfile":{"networkInterfaceConfigurations":[{"name":"myVMSS","properties":{"primary":true,"enableIPForwarding":true,"ipConfigurations":[{"name":"myVMSS","properties":{"subnet":{"id":"/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Network/virtualNetworks/myVnet/subnets/mySubnet"}}}]}}]}},"upgradePolicy":{"mode":"Manual"}}}' -H "Content-Type: application/json" -H "Authorization: Bearer <ACCESS TOKEN>"PUT https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01 HTTP/1.1Request headers
Request header Description Content-Type Required. Set to application/json.Authorization Required. Set to a valid Beareraccess token.Request body
{ "sku":{ "tier":"Standard", "capacity":3, "name":"Standard_D1_v2" }, "location":"eastus", "identity":{ "type":"UserAssigned", "userAssignedIdentities":{ "/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1":{ } } }, "properties":{ "overprovision":true, "virtualMachineProfile":{ "storageProfile":{ "imageReference":{ "sku":"2016-Datacenter", "publisher":"MicrosoftWindowsServer", "version":"latest", "offer":"WindowsServer" }, "osDisk":{ "caching":"ReadWrite", "managedDisk":{ "storageAccountType":"StandardSSD_LRS" }, "createOption":"FromImage" } }, "osProfile":{ "computerNamePrefix":"myVMSS", "adminUsername":"azureuser", "adminPassword":"myPassword12" }, "networkProfile":{ "networkInterfaceConfigurations":[ { "name":"myVMSS", "properties":{ "primary":true, "enableIPForwarding":true, "ipConfigurations":[ { "name":"myVMSS", "properties":{ "subnet":{ "id":"/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Network/virtualNetworks/myVnet/subnets/mySubnet" } } } ] } } ] } }, "upgradePolicy":{ "mode":"Manual" } } }API VERSION 2017-12-01
curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2017-12-01' -X PUT -d '{"sku":{"tier":"Standard","capacity":3,"name":"Standard_D1_v2"},"location":"eastus","identity":{"type":"UserAssigned","identityIds":["/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1"]},"properties":{"overprovision":true,"virtualMachineProfile":{"storageProfile":{"imageReference":{"sku":"2016-Datacenter","publisher":"MicrosoftWindowsServer","version":"latest","offer":"WindowsServer"},"osDisk":{"caching":"ReadWrite","managedDisk":{"storageAccountType":"StandardSSD_LRS"},"createOption":"FromImage"}},"osProfile":{"computerNamePrefix":"myVMSS","adminUsername":"azureuser","adminPassword":"myPassword12"},"networkProfile":{"networkInterfaceConfigurations":[{"name":"myVMSS","properties":{"primary":true,"enableIPForwarding":true,"ipConfigurations":[{"name":"myVMSS","properties":{"subnet":{"id":"/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Network/virtualNetworks/myVnet/subnets/mySubnet"}}}]}}]}},"upgradePolicy":{"mode":"Manual"}}}' -H "Content-Type: application/json" -H "Authorization: Bearer <ACCESS TOKEN>"PUT https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2017-12-01 HTTP/1.1Request headers
Request header Description Content-Type Required. Set to application/json.Authorization Required. Set to a valid Beareraccess token.Request body
{ "sku":{ "tier":"Standard", "capacity":3, "name":"Standard_D1_v2" }, "location":"eastus", "identity":{ "type":"UserAssigned", "identityIds":[ "/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1" ] }, "properties":{ "overprovision":true, "virtualMachineProfile":{ "storageProfile":{ "imageReference":{ "sku":"2016-Datacenter", "publisher":"MicrosoftWindowsServer", "version":"latest", "offer":"WindowsServer" }, "osDisk":{ "caching":"ReadWrite", "managedDisk":{ "storageAccountType":"StandardSSD_LRS" }, "createOption":"FromImage" } }, "osProfile":{ "computerNamePrefix":"myVMSS", "adminUsername":"azureuser", "adminPassword":"myPassword12" }, "networkProfile":{ "networkInterfaceConfigurations":[ { "name":"myVMSS", "properties":{ "primary":true, "enableIPForwarding":true, "ipConfigurations":[ { "name":"myVMSS", "properties":{ "subnet":{ "id":"/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Network/virtualNetworks/myVnet/subnets/mySubnet" } } } ] } } ] } }, "upgradePolicy":{ "mode":"Manual" } } }
Assign a user-assigned managed identity to an existing Azure virtual machine scale set
Retrieve a Bearer access token, which you will use in the next step in the Authorization header to create your virtual machine scale set with a system-assigned managed identity.
az account get-access-tokenCreate a user-assigned managed identity using the instructions found here, Create a user-assigned managed identity.
To ensure you don't delete existing user or system-assigned managed identities that are assigned to the virtual machine scale set, you need to list the identity types assigned to the virtual machine scale set by using the following CURL command. If you have managed identities assigned to the virtual machine scale set, they are listed in the
identityvalue.curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/<RESOURCE GROUP>/providers/Microsoft.Compute/virtualMachineScaleSets/<VMSS NAME>?api-version=2018-06-01' -H "Authorization: Bearer <ACCESS TOKEN>"GET https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/<RESOURCE GROUP>/providers/Microsoft.Compute/virtualMachineScaleSets/<VMSS NAME>?api-version=2018-06-01 HTTP/1.1Request headers
Request header Description Authorization Required. Set to a valid Beareraccess token.If you don't have any user or system-assigned managed identities assigned to your virtual machine scale set, use the following CURL command to call the Azure Resource Manager REST endpoint to assign the first user-assigned managed identity to the virtual machine scale set. If you have a user or system-assigned managed identity(s) assigned to the virtual machine scale set, skip to step 5 that shows you how to add multiple user-assigned managed identities to a virtual machine scale set while also maintaining the system-assigned managed identity.
The following example assigns a user-assigned managed identity,
ID1to a virtual machine scale set named myVMSS in the resource group myResourceGroup. Replace<ACCESS TOKEN>with the value you received in the previous step when you requested a Bearer access token and the<SUBSCRIPTION ID>value as appropriate for your environment.API VERSION 2018-06-01
curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-12-01' -X PATCH -d '{"identity":{"type":"userAssigned", "userAssignedIdentities":{"/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1":{}}}}' -H "Content-Type: application/json" -H Authorization:"Bearer <ACCESS TOKEN>"PATCH https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-12-01 HTTP/1.1Request headers
Request header Description Content-Type Required. Set to application/json.Authorization Required. Set to a valid Beareraccess token.Request body
{ "identity":{ "type":"userAssigned", "userAssignedIdentities":{ "/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1":{ } } } }API VERSION 2017-12-01
curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2017-12-01' -X PATCH -d '{"identity":{"type":"userAssigned", "identityIds":["/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1"]}}' -H "Content-Type: application/json" -H Authorization:"Bearer <ACCESS TOKEN>"PATCH https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2017-12-01 HTTP/1.1Request headers
Request header Description Content-Type Required. Set to application/json.Authorization Required. Set to a valid Beareraccess token.Request body
{ "identity":{ "type":"userAssigned", "identityIds":[ "/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1" ] } }If you have an existing user-assigned or system-assigned managed identity assigned to your virtual machine scale set:
API VERSION 2018-06-01
Add the user-assigned managed identity to the
userAssignedIdentitiesdictionary value.For example, if you have system-assigned managed identity and the user-assigned managed identity
ID1currently assigned to your virtual machine scale and would like to add the user-assigned managed identityID2to it:curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01' -X PATCH -d '{"identity":{"type":"SystemAssigned, UserAssigned", "userAssignedIdentities":{"/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1":{},"/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID2":{}}}}' -H "Content-Type: application/json" -H Authorization:"Bearer <ACCESS TOKEN>"PATCH https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01 HTTP/1.1Request headers
Request header Description Content-Type Required. Set to application/json.Authorization Required. Set to a valid Beareraccess token.Request body
{ "identity":{ "type":"SystemAssigned, UserAssigned", "userAssignedIdentities":{ "/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1":{ }, "/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID2":{ } } } }API VERSION 2017-12-01
Retain the user-assigned managed identities you would like to keep in the
identityIdsarray value while adding the new user-assigned managed identity.For example, if you have system-assigned identity and the user-assigned managed identity
ID1currently assigned to your virtual machine scale set and would like to add the user-assigned managed identityID2to it:curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2017-12-01' -X PATCH -d '{"identity":{"type":"SystemAssigned, UserAssigned", "identityIds":["/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1","/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID2"]}}' -H "Content-Type: application/json" -H Authorization:"Bearer <ACCESS TOKEN>"PATCH https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2017-12-01 HTTP/1.1Request headers
Request header Description Content-Type Required. Set to application/json.Authorization Required. Set to a valid Beareraccess token.Request body
{ "identity":{ "type":"SystemAssigned, UserAssigned", "identityIds":[ "/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1", "/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID2" ] } }
Remove a user-assigned managed identity from a virtual machine scale set
Retrieve a Bearer access token, which you will use in the next step in the Authorization header to create your virtual machine scale set with a system-assigned managed identity.
az account get-access-tokenTo ensure you don't delete any existing user-assigned managed identities that you would like to keep assigned to the virtual machine scale set or remove the system-assigned managed identity, you need to list the managed identities by using the following CURL command:
curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/<RESOURCE GROUP>/providers/Microsoft.Compute/virtualMachineScaleSets/<VMSS NAME>?api-version=2018-06-01' -H "Authorization: Bearer <ACCESS TOKEN>"GET https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/<RESOURCE GROUP>/providers/Microsoft.Compute/virtualMachineScaleSets/<VMSS NAME>?api-version=2018-06-01 HTTP/1.1Request headers
Request header Description Authorization Required. Set to a valid Beareraccess token.If you have managed identities assigned to the VM, they are listed in the response in the
identityvalue.For example, if you have user-assigned managed identities
ID1andID2assigned to your virtual machine scale set, and you only want to keepID1assigned and retain the system-assigned managed identity:API VERSION 2018-06-01
Add
nullto the user-assigned managed identity you would like to remove:curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01' -X PATCH -d '{"identity":{"type":"SystemAssigned, UserAssigned", "userAssignedIdentities":{"/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID2":null}}}' -H "Content-Type: application/json" -H Authorization:"Bearer <ACCESS TOKEN>"PATCH https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01 HTTP/1.1Request headers
Request header Description Content-Type Required. Set to application/json.Authorization Required. Set to a valid Beareraccess token.Request body
{ "identity":{ "type":"SystemAssigned, UserAssigned", "userAssignedIdentities":{ "/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID2":null } } }API VERSION 2017-12-01
Retain only the user-assigned managed identity(s) you would like to keep in the
identityIdsarray:curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2017-12-01' -X PATCH -d '{"identity":{"type":"SystemAssigned,UserAssigned", "identityIds":["/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1"]}}' -H "Content-Type: application/json" -H Authorization:"Bearer <ACCESS TOKEN>"PATCH https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2017-12-01 HTTP/1.1Request headers
Request header Description Content-Type Required. Set to application/json.Authorization Required. Set to a valid Beareraccess token.Request body
{ "identity":{ "type":"SystemAssigned,UserAssigned", "identityIds":[ "/subscriptions/<SUBSCRIPTION ID>/resourcegroups/myResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/ID1" ] } }
If your virtual machine scale set has both system-assigned and user-assigned managed identities, you can remove all the user-assigned managed identities by switching to use only system-assigned using the following command:
curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01' -X PATCH -d '{"identity":{"type":"SystemAssigned"}}' -H "Content-Type: application/json" -H Authorization:"Bearer <ACCESS TOKEN>"
PATCH https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01 HTTP/1.1
Request headers
| Request header | Description |
|---|---|
| Content-Type | Required. Set to application/json. |
| Authorization | Required. Set to a valid Bearer access token. |
Request body
{
"identity":{
"type":"SystemAssigned"
}
}
If your virtual machine scale set has only user-assigned managed identities and you would like to remove them all, use the following command:
curl 'https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01' -X PATCH -d '{"identity":{"type":"None"}}' -H "Content-Type: application/json" -H Authorization:"Bearer <ACCESS TOKEN>"
PATCH https://management.azure.com/subscriptions/<SUBSCRIPTION ID>/resourceGroups/myResourceGroup/providers/Microsoft.Compute/virtualMachineScaleSets/myVMSS?api-version=2018-06-01 HTTP/1.1
Request headers
| Request header | Description |
|---|---|
| Content-Type | Required. Set to application/json. |
| Authorization | Required. Set to a valid Bearer access token. |
Request body
{
"identity":{
"type":"None"
}
}
Next steps
For information on how to create, list, or delete user-assigned managed identities using REST see:
Aiseolas
Ag teacht go luath: Le linn 2024 beimid ag cur deireadh de réir a chéile le fadhbanna GitHub mar mheicníocht aiseolais d’inneachar agus córas aiseolais nua a chur ina áit. Chun tuilleadh faisnéise a fháil féach ar :https://aka.ms/ContentUserFeedback.
Cuir isteach agus féach ar aiseolas le haghaidh