Microsoft Entra single sign-on (SSO) integration with SignalFx
In this tutorial, you'll learn how to integrate SignalFx with Microsoft Entra ID. When you integrate SignalFx with Microsoft Entra ID, you can:
- Control from Microsoft Entra ID who has access to SignalFx.
- Enable your users to be automatically signed-in to SignalFx with their Microsoft Entra accounts.
- Manage your accounts in one location (the Azure portal).
Prerequisites
To get started, you need the following items:
- A Microsoft Entra subscription. If you don't have a subscription, you can get a free account.
- SignalFx single sign-on (SSO) enabled subscription.
Scenario description
In this tutorial, you'll configure and test Microsoft Entra SSO in a test environment.
- SignalFx supports IDP initiated SSO.
- SignalFx supports Just In Time user provisioning.
Step 1: Add the SignalFx application in Azure
Use these instructions to add the SignalFx application to your list of managed SaaS apps.
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
- Browse to Identity > Applications > Enterprise applications > New application.
- In the Add from the gallery section, type SignalFx in the search box.
- Select SignalFx from results panel and then add the app. Wait a few seconds while the app is added to your tenant.
- Leave the Microsoft Entra admin center open, and then open a new browser tab.
Step 2: Begin SignalFx SSO configuration
Use these instructions to begin the configuration process for the SignalFx SSO.
- In the newly opened tab, access and log into the SignalFx UI.
- In the top menu, click Integrations.
- In the search field, enter and select Microsoft Entra ID.
- Click Create New Integration.
- In Name, enter an easily recognizable name that your users will understand.
- Mark Show on login page.
- This feature will display a customized button in the login page that your users can click on.
- The information you entered in Name will appear on the button. As a result, enter a Name that your users will recognize.
- This option will only function if you use a custom subdomain for the SignalFx application, such as yourcompanyname.signalfx.com. To obtain a custom subdomain, contact SignalFx support.
- Copy the Integration ID. you'll need this information in a later step.
- Leave the SignalFx UI open.
Step 3: Configure Microsoft Entra SSO
Use these instructions to enable Microsoft Entra SSO.
Return to the Microsoft Entra admin center, and on the SignalFx application integration page, locate the Manage section, and then select Single sign-on.
On the Select a single sign-on method page, select SAML.
On the Set up single sign-on with SAML page, click the pencil icon for Basic SAML Configuration to edit the settings.
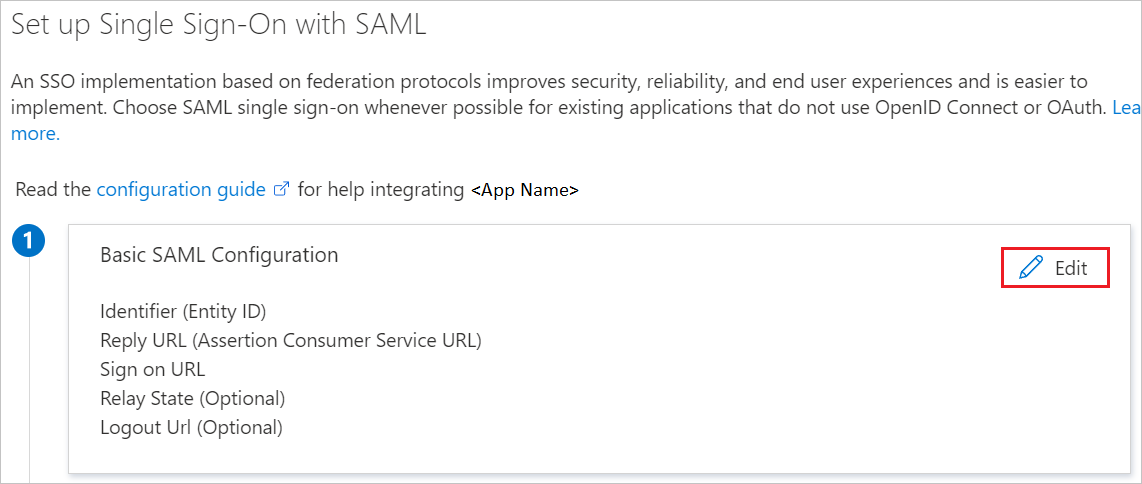
On the Set up single sign-on with SAML page, perform the following steps:
a. In Identifier, enter the following URL
https://api.<realm>.signalfx.com/v1/saml/metadataand replace<realm>with your SignalFx realm, as well as<integration ID>with the Integration ID you copied earlier from the SignalFx UI. (except realm US0, the url should behttps://api.signalfx.com/v1/saml/metadata).b. In Reply URL, enter the following URL
https://api.<realm>.signalfx.com/v1/saml/acs/<integration ID>and replace<realm>with your SignalFx realm, as well as<integration ID>with the Integration ID you copied earlier from the SignalFx UI. (except US0, the url should behttps://api.signalfx.com/v1/saml/acs/<integration ID>)SignalFx application expects the SAML assertions in a specific format, which requires you to add custom attribute mappings to your SAML token attributes configuration.
Review and verify that the following claims map to the source attributes that are populated in the Active Directory.
Name Source Attribute User.FirstName user.givenname User.email user.mail PersonImmutableID user.userprincipalname User.LastName user.surname Note
This process requires that your Active Directory is configured with at least one verified custom domain, as well as has access to the email accounts in this domain. If you are unsure or need assistance with this configuration, please contact SignalFx support.
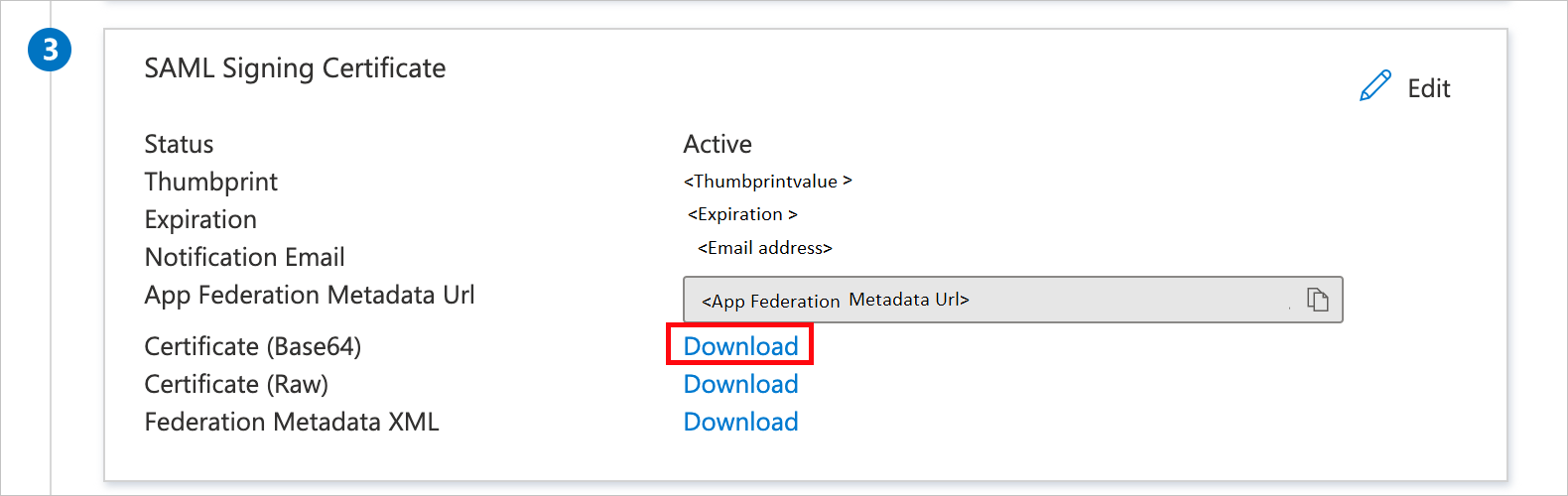
On the Set up single sign-on with SAML page, in the SAML Signing Certificate section, find Certificate (Base64), and then select Download. Download the certificate, and save it on your computer. Then, copy the App Federation Metadata Url value; you'll need this information in a later step in the SignalFx UI.
On the Set up SignalFx section, copy the Microsoft Entra Identifier value. you'll need this information in a later step in the SignalFx UI.
Step 4: Create a Microsoft Entra test user
In this section, you'll create a test user called B.Simon.
- Sign in to the Microsoft Entra admin center as at least a User Administrator.
- Browse to Identity > Users > All users.
- Select New user > Create new user, at the top of the screen.
- In the User properties, follow these steps:
- In the Display name field, enter
B.Simon. - In the User principal name field, enter the username@companydomain.extension. For example,
B.Simon@contoso.com. - Select the Show password check box, and then write down the value that's displayed in the Password box.
- Select Review + create.
- In the Display name field, enter
- Select Create.
Step 5: Assign the Microsoft Entra test user
In this section, you'll enable B.Simon to use single sign-on by granting access to SignalFx.
- Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
- Browse to Identity > Applications > Enterprise applications > SignalFx.
- In the app's overview page, select Users and groups.
- Select Add user/group, then select Users and groups in the Add Assignment dialog.
- In the Users and groups dialog, select B.Simon from the Users list, then click the Select button at the bottom of the screen.
- If you are expecting a role to be assigned to the users, you can select it from the Select a role dropdown. If no role has been set up for this app, you see "Default Access" role selected.
- In the Add Assignment dialog, click the Assign button.
Step 6: Complete the SignalFx SSO configuration
- Open the previous tab, and return to the SignalFx UI to view the current Microsoft Entra integration page.
- Next to Certificate (Base64), click Upload File, and then locate the Base64 encoded certificate file that you previously downloaded previously.
- Next to Microsoft Entra Identifier, paste the Microsoft Entra Identifier value that you copied earlier.
- Next to Federation Metadata URL, paste the App Federation Metadata Url value that you copied earlier.
- Click Save.
Step 7: Test SSO
Review the following information regarding how to test SSO, as well as expectations for logging into SignalFx for the first time.
Test logins
To test the login, you should use a private / incognito window, or you can log out. If not, cookies for the user who configured the application will interfere and prevent a successful login with the test user.
When a new test user logs in for the first time, Azure will force a password change. When this occurs, the SSO login process will not be completed; the test user will be directed to the Azure portal. To troubleshoot, the test user should change their password, and navigate to the SignalFx login page or to the MyApps and try again.
- When you click the SignalFx tile in the MyApps, you should be automatically logged into the SignalFx.
- For more information about the MyApps, see Introduction to the MyApps.
- When you click the SignalFx tile in the MyApps, you should be automatically logged into the SignalFx.
SignalFx application can be accessed from the MyApps or via a custom login page assigned to the organization. The test user should test the integration starting from either of these locations.
- The test user can use the credentials created earlier in this process for b.simon@contoso.com.
First-time logins
When a user logs into SignalFx from the SAML SSO for the first time, the user will receive a SignalFx email with a link. The user must click the link for authentication purposes. This email validation will only take place for first-time users.
SignalFx supports Just In Time user creation, which means that if a user does not exist in SignalFx, then the user's account will be created upon first login attempt.
Related content
Once you configure SignalFx you can enforce session control, which protects exfiltration and infiltration of your organization’s sensitive data in real time. Session control extends from Conditional Access. Learn how to enforce session control with Microsoft Defender for Cloud Apps.