Use portal to create private link for managing Azure resources
This article explains how you can use Azure Private Link to restrict access for managing resources in your subscriptions. It shows using the Azure portal for setting up management of resources through private access.
Private links enable you to access Azure services over a private endpoint in your virtual network. When you combine private links with Azure Resource Manager's operations, you block users who aren't at the specific endpoint from managing resources. If a malicious user gets credentials to an account in your subscription, that user can't manage the resources without being at the specific endpoint.
Private link provides the following security benefits:
- Private Access - users can manage resources from a private network via a private endpoint.
Note
Azure Kubernetes Service (AKS) currently doesn't support the ARM private endpoint implementation.
Azure Bastion doesn't support private links. It is recommended to use a private DNS zone for your resource management private link private endpoint configuration, but due to the overlap with the management.azure.com name, your Bastion instance will stop working. For more information, view Azure Bastion FAQ.
Understand architecture
Important
For this release, you can only apply private link management access at the level of the root management group. This limitation means private link access is applied across your tenant.
There are two resource types you'll use when implementing management through a private link.
- Resource management private link (Microsoft.Authorization/resourceManagementPrivateLinks)
- Private link association (Microsoft.Authorization/privateLinkAssociations)
The following image shows how to construct a solution that restricts access for managing resources.

The private link association extends the root management group. The private link association and the private endpoints reference the resource management private link.
Important
Multi-tenant accounts aren't currently supported for managing resources through a private link. You can't connect private link associations on different tenants to a single resource management private link.
If your account accesses more than one tenant, define a private link for only one of them.
Workflow
To set up a private link for resources, use the following steps. The steps are described in greater detail later in this article.
- Create the resource management private link.
- Create a private link association. The private link association extends the root management group. It also references the resource ID for the resource management private link.
- Add a private endpoint that references the resource management private link.
After completing those steps, you can manage Azure resources that are within the hierarchy of the scope. You use a private endpoint that is connected to the subnet.
You can monitor access to the private link. For more information, see Logging and monitoring.
Required permissions
Important
For this release, you can only apply private link management access at the level of the root management group. This limitation means private link access is applied across your tenant.
To set up the private link for resource management, you need the following access:
- Owner on the subscription. This access is needed to create resource management private link resource.
- Owner or Contributor at the root management group. This access is needed to create the private link association resource.
- The Global Administrator for the Microsoft Entra ID doesn't automatically have permission to assign roles at the root management group. To enable creating resource management private links, the Global Administrator must have permission to read root management group and elevate access to have User Access Administrator permission on all subscriptions and management groups in the tenant. After you get the User Access Administrator permission, the Global Administrator must grant Owner or Contributor permission at the root management group to the user creating the private link association.
Create resource management private link
When you create a resource management private link, the private link association is automatically created for you.
In the portal, search for Resource management private links and select it from the available options.

If your subscription doesn't already have resource management private links, you'll see a blank page. Select Create resource management private link.

Provide values for the new resource management private link. The root management group for the directory you selected is used for the new resource. Select Review + create.

After validation passes, select Create.
Create private endpoint
Now, create a private endpoint that references the resource management private link.
Navigate to the Private Link Center. Select Create private endpoint.

In the Basics tab, provide values for your private endpoint.

In the Resource tab, select Connect to an Azure resource in my directory. For resource type, select Microsoft.Authorization/resourceManagementPrivateLinks. For target subresource, select ResourceManagement.
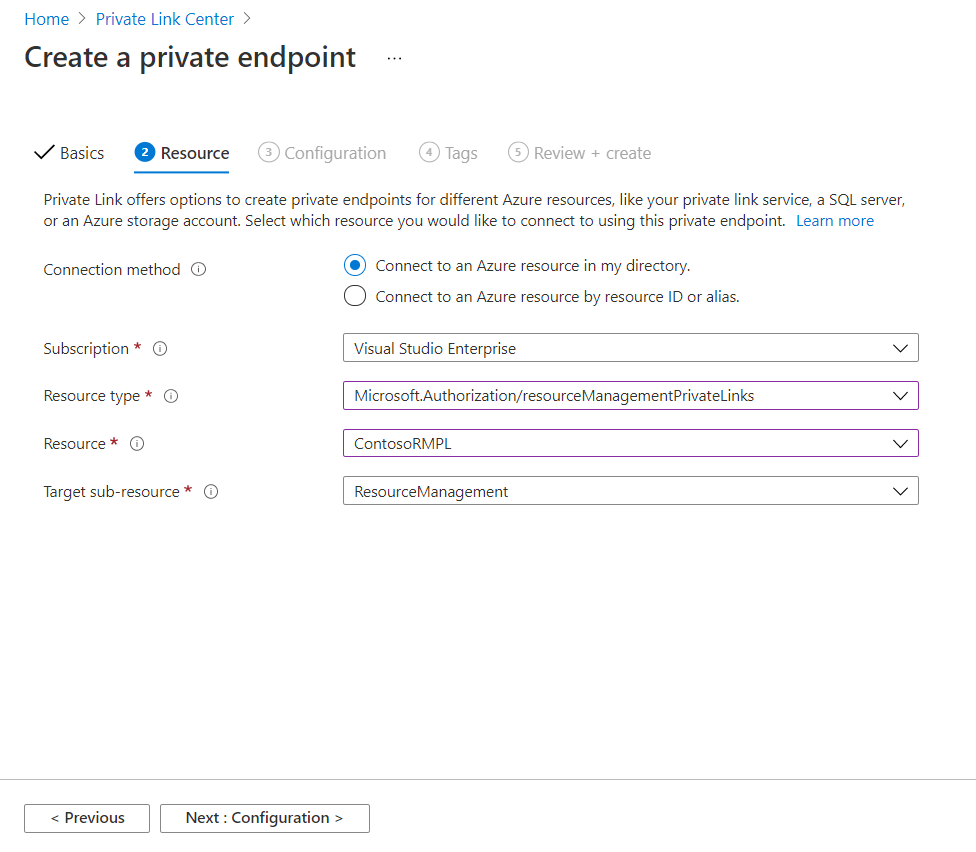
In the Configuration tab, select your virtual network. We recommend integrating with a private DNS zone. Select Review + create.
After validation passes, select Create.
Verify private DNS zone
To make sure your environment is properly configured, check the local IP address for the DNS zone.
In the resource group where you deployed the private endpoint, select the private DNS zone resource named privatelink.azure.com.
Verify that the record set named management has a valid local IP address.

Next steps
To learn more about private links, see Azure Private Link.