Protect your Amazon Web Service (AWS) containers with Defender for Containers
Defender for Containers in Microsoft Defender for Cloud is the cloud-native solution that is used to secure your containers so you can improve, monitor, and maintain the security of your clusters, containers, and their applications.
Learn more about Overview of Microsoft Defender for Containers.
You can learn more about Defender for Container's pricing on the pricing page.
Prerequisites
You need a Microsoft Azure subscription. If you don't have an Azure subscription, you can sign up for a free subscription.
You must enable Microsoft Defender for Cloud on your Azure subscription.
Verify your Kubernetes nodes can access source repositories of your package manager. For information about the requirements, see Network requirements.
Ensure the following Azure Arc-enabled Kubernetes network requirements are validated.
Enable the Defender for Containers plan on your AWS account
To protect your EKS clusters, you need to enable the Containers plan on the relevant AWS account connector.
To enable the Defender for Containers plan on your AWS account:
Sign in to the Azure portal.
Search for and select Microsoft Defender for Cloud.
In the Defender for Cloud menu, select Environment settings.
Select the relevant AWS account.

Set the toggle for the Containers plan to On.
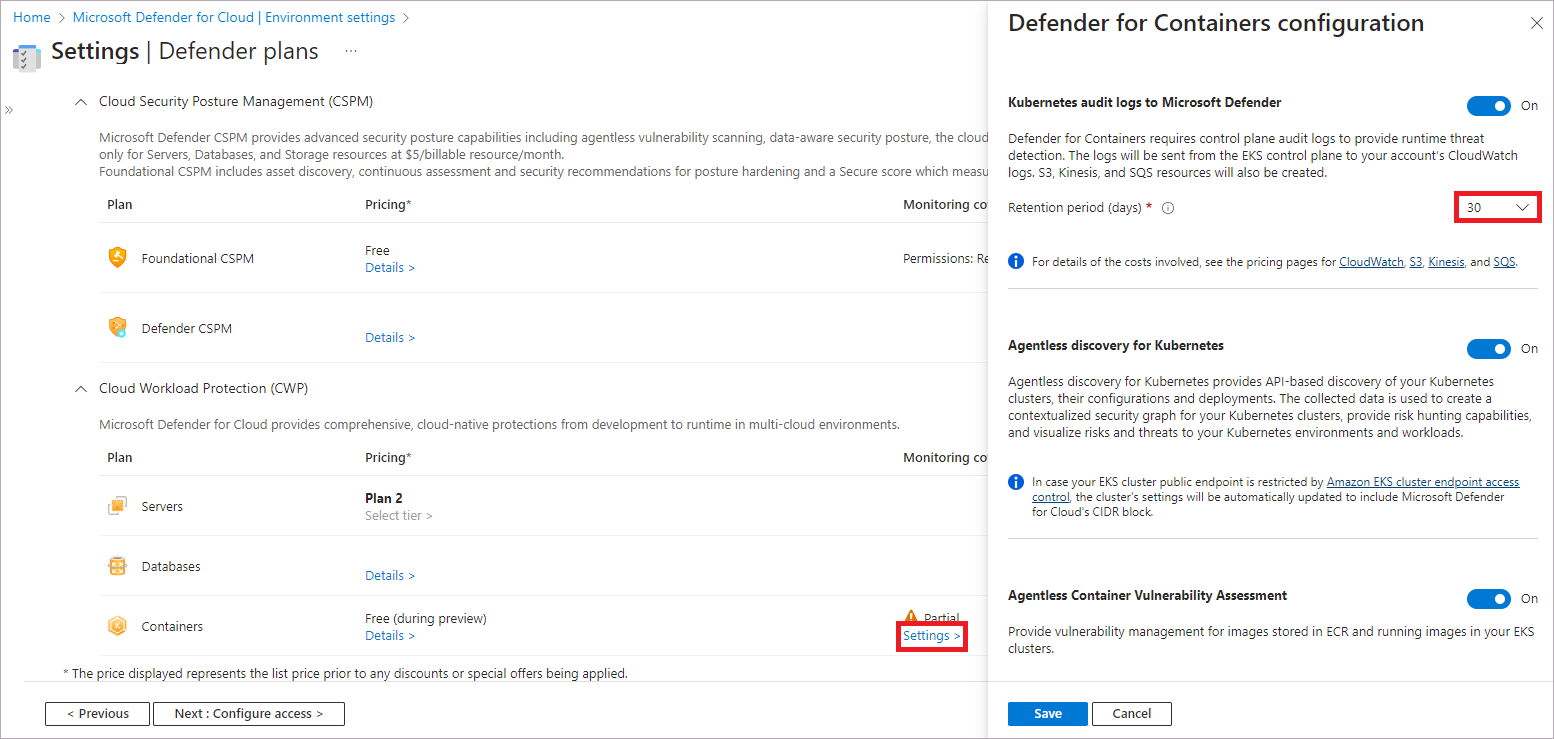
To change optional configurations for the plan, select Settings.
Defender for Containers requires control plane audit logs to provide runtime threat protection. To send Kubernetes audit logs to Microsoft Defender, toggle the setting to On. To change the retention period for your audit logs, enter the required time frame.
Note
If you disable this configuration, then the
Threat detection (control plane)feature will be disabled. Learn more about features availability.Agentless discovery for Kubernetes provides API-based discovery of your Kubernetes clusters. To enable the Agentless discovery for Kubernetes feature, toggle the setting to On.
The Agentless Container Vulnerability Assessment provides vulnerability management for images stored in ECR and running images on your EKS clusters. To enable the Agentless Container Vulnerability Assessment feature, toggle the setting to On.
Select Next: Review and generate.
Select Update.
Note
To enable or disable individual Defender for Containers capabilities, either globally or for specific resources, see How to enable Microsoft Defender for Containers components.
Deploy the Defender sensor in EKS clusters
Azure Arc-enabled Kubernetes, the Defender sensor, and Azure Policy for Kubernetes should be installed and running on your EKS clusters. There's a dedicated Defender for Cloud recommendation that can be used to install these extensions (and Azure Arc if necessary):
EKS clusters should have Microsoft Defender's extension for Azure Arc installed
To deploy the required extensions:
From Defender for Cloud's Recommendations page, search for one of the recommendations by name.
Select an unhealthy cluster.
Important
You must select the clusters one at a time.
Don't select the clusters by their hyperlinked names: select anywhere else in the relevant row.
Select Fix.
Defender for Cloud generates a script in the language of your choice:
- For Linux, select Bash.
- For Windows, select PowerShell.
Select Download remediation logic.
Run the generated script on your cluster.
Next steps
For advanced enablement features for Defender for Containers, see the Enable Microsoft Defender for Containers page.