Set branch permissions
Azure DevOps Services | Azure DevOps Server 2022 - Azure DevOps Server 2019
Set up permissions to control who can read and update the code in a branch on your Git repo. You can set permissions for individual users and groups, and inherit and override permissions as needed from your repo permissions.
Prerequisites
| Category | Requirements |
|---|---|
| Project access | Member of a project. |
| Permissions | - View code in private projects: At least Basic access. - Clone or contribute to code in private projects: Member of the Contributors security group or corresponding permissions in the project. - Set branch or repository permissions: Manage permissions permissions for the branch or repository. - Change default branch: Edit policies permissions for the repository. - Import a repository: Member of the Project Administrators security group or Git project-level Create repository permission set to Allow. For more information, see Set Git repository permissions. |
| Services | Repos enabled. |
| Tools | Optional. Use az repos commands: Azure DevOps CLI. |
Note
In public projects, users with Stakeholder access have full access to Azure Repos, including viewing, cloning, and contributing to code.
| Category | Requirements |
|---|---|
| Project access | Member of a project. |
| Permissions | - View code: At least Basic access. - Clone or contribute to code: Member of the Contributors security group or corresponding permissions in the project. |
| Services | Repos enabled. |
Use the branches view to configure security
Sign in to your project (
https://dev.azure.com/{Your_Organization}/{Your_Project}).Select Repos > Branches.
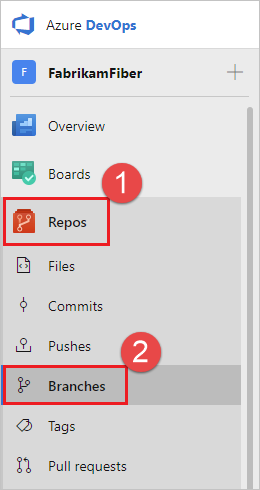
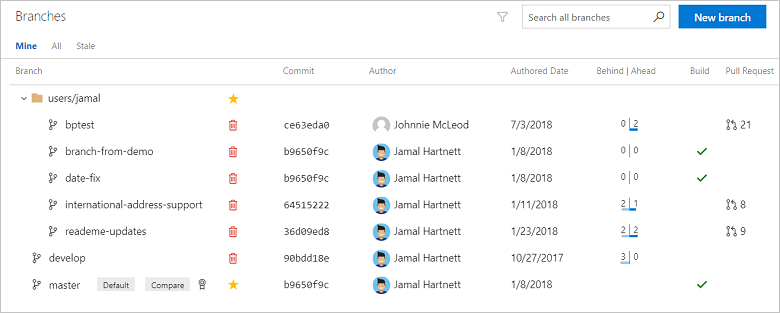
Locate your branch in the page. You can browse the list or you can search for your branch using the Search box in the upper right.
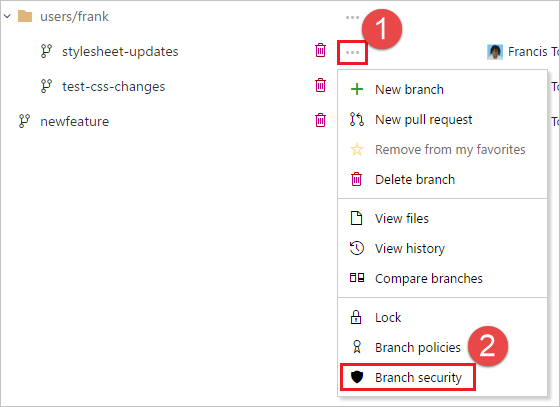
To open the context menu, select ... More actions next to the branch name. Select Branch security from the menu.
Add users or groups
Tip
You can only add permissions for users and groups already in your project. Add new users and groups to your project before you set branch permissions.
1.To add users or groups to your branch permissions, selectAdd.
2.Enter the sign-in address or group alias, then select Save.
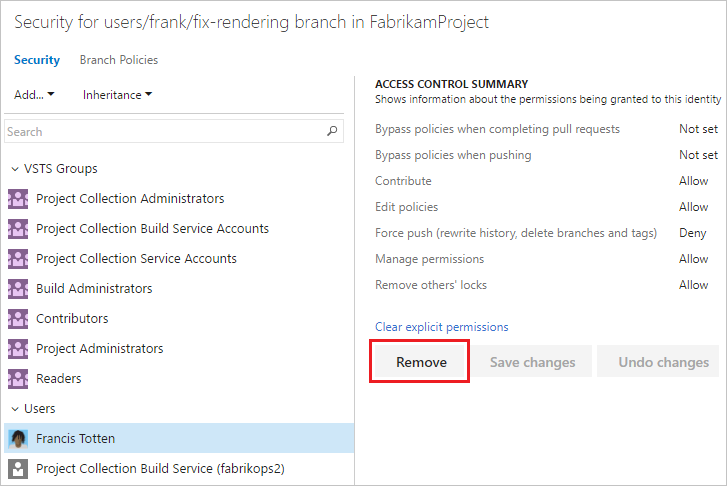
Remove users or groups
To remove permissions for a user or group, select the user or group, and then select Remove. This change doesn't affect other permissions for the user or group in your project.
Set permissions
Users and groups with permissions set at the repository level inherit those permissions by default.
Branch creators automatically receive the following permissions:
- Contribute
- Force push
- Manage permissions (when allowed through the repository setting Permissions management)
- Remove others' locks
Note
The Exempt from policy enforcement permission is replaced by the following two permissions:
- Bypass policies when completing pull requests
- Bypass policies when pushing
Users who previously had Exempt from policy enforcement enabled have these permissions enabled instead. The following table shows more details on these permissions. ::: moniker-end
| Permission | Description |
|---|---|
| Bypass policies when completing pull requests | Users with this permission are exempt from the branch policy set for the branch when completing pull requests and can opt in to override the policies by checking Override branch policies and enable merge when completing a PR. |
| Bypass policies when pushing | Users with this permission can push to a branch that has branch policies enabled. When a user with this permission makes a push that would override branch policy, the push automatically bypasses branch policy with no opt-in step or warning. |
| Contribute | Can push new commits to the branch and lock the branch. Can't rewrite existing commits on the branch. |
| Edit policies | Can edit branch policies. |
| Force push (rewrite history, delete branches and tags) | Can force push to a branch, which can rewrite history. This permission is also required to delete a branch. |
| Manage permissions | Can set permissions for the branch. |
| Remove others' locks | Can remove locks set on branches by other users. |