Troubleshoot best practices assessment on SQL Server
Applies to:
SQL Server
Before you proceed, verify all the necessary prerequisites are met.
Log file locations
Extension log
The extension log file is at:
C:\ProgramData\GuestConfig\extension_logs\Microsoft.AzureData.WindowsAgent.SqlServer\
The log file name depends on the version Azure Extension for SQL Server. For the latest version of Azure Extension for SQL Server, the log file is:
unifiedagent.log
For extension version 1.1.24724.69 and earlier, the log file is:
ExtensionLog_0.log
Azure monitor agent log
The Azure monitor agent log is at:
C:\ProgramData\GuestConfig\extension_logs\Microsoft.Azure.Monitor.AzureMonitorWindowsAgent\Extension.1.log
You might encounter the following issues when you enable best practices assessment.
No Log Analytics workspace is available in the dropdown list menu
Ensure that the user configuring SQL BPA must have Log Analytics Contributor role on the resource group or subscription of the Log Analytics workspace. The list of prerequisites can be found here.
Error notifications requiring users to wait five minutes
If such a notification appears and you keep the page open, the portal automatically retries the operation after five minutes. If the page is refreshed, the portal advises you to wait for five minutes before retrying the operation. In case the same error persists after a long time, verify the state of the WindowsAgent.SqlServer extension and ensure that the extension isn't stuck in an Updating state. In case the extension is still stuck, verify the connectivity of the Arc machine.
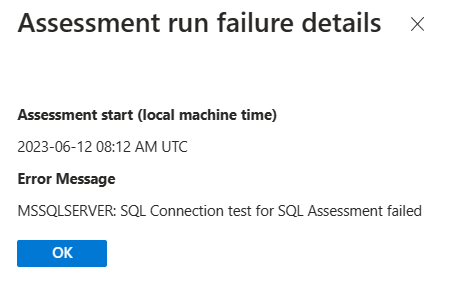
Assessment run failed
In case the assessment run fails, select the corresponding row to open a page that displays the error message.
SQL Server connection failures, general network error
Description
Connection test for SQL Assessment failed indicates that the assessment failed to connect to the instance of SQL Server. It returns:
Resolution
Follow the steps at Troubleshoot connectivity issues in SQL Server.
Server principal is not able to access model database
Description
The server principal NT Authority/SYSTEM is not able to access the database "model" under the current security context.
The server principal isn't able to access the database under the current security context returns this error in the portal.

Resolution
Ensure the SQL Server built-in login NT AUTHORITY\SYSTEM is a member of the SQL Server sysadmin server role for all the SQL Server instances running on the machine.
If this isn't allowed, you can configure a least privilege account for the Azure extension for SQL Server service on your SQL Server machine. Least privilege account is available for preview.
To configure your server, follow the steps in Operate SQL Server enabled by Azure Arc with least privilege.
Azure Monitor Agent upload failed
If the error states that the upload failed for Azure Monitor Agent (AMA), verify that the AMA is provisioned and configured correctly. The following components must be configured correctly to ensure that the agent can upload logs to the workspace:
- The linked Log Analytics workspace must have a table named
SqlAssessment_CL.- Navigate to the Tables tab under the linked Log Analytics workspace.
- The
SqlAssessment_CLtable should be present.
- Azure Monitor Agent (version >= 1.10.0) should be successfully provisioned.
- Navigate to the Extensions tab under the Arc resource.
- AMA with required version should be successfully provisioned.
- The data collection rule (DCR) and data collection endpoint (DCE) must be in the same location as the Log Analytics workspace.
- Navigate to the Overview tab of the resource group to which the Log Analytics workspace belongs.
- Under the list of resources, the DCR and the DCE can be identified by their prefixes, sqlbpa-.
- Verify that the DCR and DCE are in the same location as the Log Analytics workspace.
- The data collection Rule (DCR) should be configured correctly.
- Navigate to The Resources tab under the relevant DCR. The Arc machine name should be present on the list.
- Navigate to The Data Sources tab under the relevant DCR. Select the entry Custom Text Logs.
- Under the Data Sources tab, the table name should be
SqlAssessment_CL. - Under the Data Sources tab, the configured log collection path should be
C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft SQL Server Extension Agent\Assessment\*.csv. - Under the Destination tab, the Log Analytics workspace name should be present.
- Under the Data Sources tab, the table name should be
In case any of the components are missing, do the following:
- Disable assessment by selecting Configuration > Disable assessment.
- Confirm that you have the required permissions to enable assessment.
- Enable assessment by selecting Enable assessment.
Assessment deployment failed
- Navigate to the deployment and troubleshoot the error.
- If there are any issues with the deployment of the Azure Monitor Agent, verify that the Arc machine is connected.
- The deployment can always be retriggered with the same Log Analytics workspace by selecting the Enable assessment button.
Change the Log Analytics workspace
To change the Log Analytics workspace that is linked for the best practices assessment, follow the steps below.
Disable best practices assessment if it's currently enabled via the Azure portal.
Make a GET call to the API and get the Azure extension for SQL Server settings. For more information, review How to call Azure REST APIs with curl.
In order to complete this task, you need to obtain the bearer token in order to perform this action against the resource in Azure portal. From Azure portal:
- Navigate to the corresponding SQL Server - Azure Arc resource.
- Select Ctrl+Shift+I together, go to Network tab.
- Select Overview for the SQL Server - Azure Arc resource.
- In the name column, locate and select the entry for ArcServer name?api-version.
- On the right window, go to Request Headers.
- Copy the complete text for Authorization: Bearer to get the bearer authorization token.
GET https://edge.management.azure.com/subscriptions/ <subscription-id>/resourceGroups/<resource-group-name>/providers/Microsoft.HybridCompute/machines/<arc-resource-name>/extensions/WindowsAgent.SqlServer?api-version=2022-03-10The best practices assessment settings before the change.
"AssessmentSettings": { "Enable": true, "RunImmediately": true, "schedule": { "dayOfWeek": "Sunday", "Enable": true, "monthlyOccurrence": null, "StartDate": null, "startTime": "00:00", "WeeklyInterval": 1 }, "WorkspaceResourceId": null, "WorkspaceLocation": null, "ResourceNamePrefix": null, "settingsSaveTime": 1673278632 }Update the workspace related settings to null as follows.
"AssessmentSettings": { "Enable": false, "RunImmediately": true, "schedule": { "dayOfWeek": "Sunday", "Enable": true, "monthlyOccurrence": null, "StartDate": null, "startTime": "00:00", "WeeklyInterval": 1 }, "WorkspaceResourceId": null, "WorkspaceLocation": null, "ResourceNamePrefix": null, "SettingsSaveTime": 1673278632 }Make a
PATCHcall to the API, to update the Azure extension for SQL Server assessment settings.PATCH https://management.azure.com/subscriptions/ <subscription-id>/resourceGroups/<resource-group-name>/providers/Microsoft.HybridCompute/machines/<arc-resource-name>/extensions/WindowsAgent.SqlServer?api-version=2022-08-11-previewGo to Best Practices Assessment on your Arc-enabled SQL Server resource page in the Azure portal and re-enable best practices assessment and select a new log analytics workspace.
For more assistance, create a support ticket with Microsoft and attach the log files. Visit, Create an Azure support request

