Behind Live Mesh: Authorization and encryption
Hi, I am Nikolai Smolyanskiy, a developer on the Accounts team. I work on the Account service that takes care of account management, and user/device authentication and authorization in Live Mesh.
There were many questions asked by early adopters about how their data is transmitted and stored in Live Mesh, and how access is controlled. In this post I’ll talk about the security and authorization architecture behind Live Mesh, so that you understand the amount of care we take and feel better about trusting your data to the Mesh. This post can also be found here.
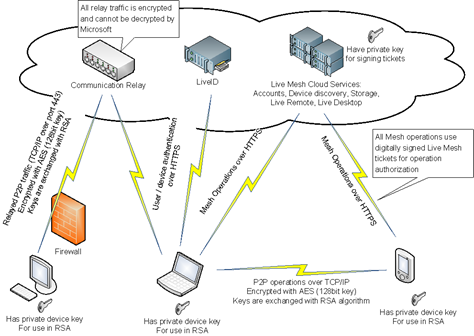
Here is the diagram that illustrates all communications between user devices and Live Mesh cloud services and encryption/security mechanisms used in these communication channels:
Live Mesh security is rooted at the authentication provider (Windows Live ID, aka Microsoft Passport is our provider today) which is used for initial user and device authentication. Once a user or a device is authenticated and a corresponding authentication token is obtained, the Live Mesh client passes this token to the Live Mesh Account service to access the root of the user’s mesh and to get the initial set of Live Mesh tickets. These tickets are used for further Mesh operations on other resources that this root is pointing to. All communications with the Live Mesh cloud services are done via HTTPS / SSL, so 3rd parties cannot intercept and read client-server communication.
All user (or device) related resources in Live Mesh are organized in a RESTful manner, i.e. they form a graph where each node is identified by a unique URL and represents a given resource. Nodes contain resource metadata and links to other resources. Mesh operations are essentially CRUD operations on the nodes of the user tree or nodes of other user trees if those users shared any data. Live Mesh cloud services check access rights in each operation by inspecting passed tickets and authorizing access only if a correct set of tickets is passed. Tickets can be obtained from the Account service or from responses to previous cloud operations.
Live Mesh authorization tickets are standard SAML tickets. They are digitally signed with the Live Mesh private key to prevent spoofing and they expire after a limited lifetime. Some tickets are used to just authenticate users or devices, other tickets contain authorization information about user/device rights. Cloud services inspect each resource request and authorize access only if it contains valid tickets (correctly signed and not expired) and these tickets specify that the requestor indeed has access to the requested resource. For example, a device X can initiate P2P data synchronization with device Y only if it presents a ticket that is correctly signed by Live Mesh and contains a record saying that both device X and Y are claimed by the same user OR if it contains a record saying that X and Y have the same Live Mesh Folder mapped on them (in the case that the devices are claimed by different users that are members of this Live Mesh Folder). Tickets are passed to the cloud services in the Authorization header using HTTPS to prevent replay attacks.
Each device in Live Mesh (computers, PDAs, mobile phones) has a unique private key that is generated during Live Mesh installation and used to authenticate the device in P2P communications with other devices. When a P2P communication is being established between two devices, they first use asymmetric encryption (RSA algorithm) to exchange encryption keys and then use symmetric encryption (AES with 128 bit key) to transfer data/files over TCP/IP. The RSA exchange guards against leaking symmetric encryption keys. AES encryption protects actual data from prying eyes. Live Mesh also uses a keyed message authentication code (HMAC) to verify the integrity of the data exchanged on a P2P channel.
If there is no direct connection between two devices (for example, if one device is behind a firewall), then the cloud communication relay located in the Microsoft data center is used to forward data packets from one device to another. All the traffic is encrypted in the same way as in the case with direct P2P link, i.e. first keys are exchanged with RSA and then traffic is encrypted with AES. The cloud relay cannot decrypt/read user data, since encryption keys are exchanged with the use of asymmetric encryption (RSA).
Live Mesh cloud services help devices find each other and establish communications. They cannot read synchronized user data/files relayed through the cloud, except for the case when user files are synchronized with the cloud storage (i.e. Live Desktop). At the moment, the limited Tech Preview of Live Mesh synchronizes your files not only between your devices, but also with your cloud storage (which you can access via Live Desktop) until you reach your storage quota (5GB as of today). So your files and metadata that describes them are stored in the Microsoft datacenter. They are protected by strong access control mechanisms, but the data is not stored in encrypted form. After the storage quota has been reached, all files are synchronized only P2P and not stored in the cloud (only metadata is stored in the datacenter). In the future, Live Mesh will allow users to selectively choose which files or Live Mesh Folders they want to synchronize with the cloud. If you choose to synchronize your data/files between your devices only, Live Mesh will not store your files in the cloud and will only store metadata that lets the service to operate.
Technorati Tags: LiveMesh
Comments
Anonymous
May 29, 2008
PingBack from http://www.straferight.com/forums/pc-hardware-software/177232-anyone-else-mesh-8.html#post2554807Anonymous
May 29, 2008
digg_url = 'http://blogs.msdn.com/stevecla01/archive/2008/05/30/authorization-and-encryption-in-live-mesh.aspx';Anonymous
June 01, 2008
The comment has been removedAnonymous
June 02, 2008
Mesh does not split files nor encrypt them on local hard drives at the moment. I think this is OK for most of people, but you are right that there are special cases where it needs to be even more secure. I guess this feature may be added in the future, based on customer feedback. So Mesh will be able to operate in the "normal" security mode and in the "hightened" security mode.Anonymous
June 03, 2008
Hi, i'm wondering why the process wlcrasvc.exe doesn't quit? When I first saw it I thought it was malware (nice job naming it) and tried pretty hard to end the task but it kept popping up. I then checked the registry and found out it was a live mesh ware...but kept running despite the fact I had quit the moe client on my pc.Anonymous
June 04, 2008
@iceanfire This is the service that supports Live Mesh Remote Desktop. It runs as a service by design, so that you’re able to use remote desktop when another user is logged in to Live Mesh (or no user is logged in.) It’s configured as an auto-start service, so killing the process means a new one just starts up in its place. If you wish to temporarily disable the service, you can do “net stop wlcrasvc” from an elevated command prompt. To prevent the service from running, open the Services control panel and set the Startup Type for “Live Mesh Remote Desktop” service to Disabled. If the service is not running, though, you will not be able to connect to the computer remotely using Live Mesh.Anonymous
June 09, 2008
The comment has been removedAnonymous
June 09, 2008
Have you heard, instead of thorough betas and public testing... Apple is just magically revealing their me.com, I geuss our me(sh).com is sneakier in name alone. A comparable product, that I hope gets dumptrucked after release and outgunned by mesh and mesh mobile :)Anonymous
June 10, 2008
In response to Erik, Hardly a comparable product, in my opinion Apples MobileMe is far superior. You get Push calendar, Push email, push contacts, and synching of photos and idisk. And they are EASY to use. MobileMe is available in July and is a complete product - ie Not in beta like all the Windows Live offerings.
- To get the same functionality on windows you have to sign into Hotmail, Live Spaces,Skydrive, sign up for Mesh tech preview, participate in the Live Calendar beta and have the Live Mobile client installed on your phone. All these windows services are not easily accessable from a single interface that is easy to use
- Live Calendar doesnt work with Windows Mobile, so theres no Push Calendaring there. Nor does Live Calendar work on the Live Mail Desktop client
- iDisk has the ability to map as a network drive in windows and mac. Skydrive does neither.
- None of the Windows Live stuff works on mac. I was a real windows fan, but im getting tired of all these Windows Live products that have no cohesion and are difficult to use together. Who is running this ship?
Anonymous
June 10, 2008
@Craig I second this. Now, granted, LiveMesh is still in beta status, but it would be great if all of these things worked together instead of these tiny little islands that they currently are. I'm still using Google for almost everything, but if all this Live stuff starts to integrate more between the different peices, I'll have a good reason to move.Anonymous
June 10, 2008
Craig, I'm sorry that our Live suite has been a disappointment to you so far. We're continually refining and improving our products and their integration, so I hope you come back occasionally to give us another look. You're right that the Live suite is more directly comparable to Mobile.Me than our mesh technology preview, which is more of an early platform demo.Anonymous
June 11, 2008
how can I try the Live mesh? I already sumit my participation throught the connect web site but no response. I have a lot of devices to sync and I wish try the live mesh :-)Anonymous
June 16, 2008
Why is Desktop.ini not synchronized between machines? is there an alternate way to customize the icon for each of my Mesh-managed folders? Michael HermanAnonymous
June 16, 2008
@Michael Herman If you haven't done so already, you might want to visit our forums, particularly our Wish List sticky thread where you can throw in your vote for different features (such as customized icons). http://forums.community.microsoft.com/en/LiveMesh/threadsAnonymous
June 17, 2008
The protocol looks very similar to SSL ,with assymetric keys used to negotiate a symmetric keys and then moving ahead from there. But you go on to add that the relay can't see the data. Few questions : Can HTTPS be used from me to relay and relay to other client? if relay can't read data, you seem to have cracked message level encryption (unlike SSL which is envelope level encryption) , can you give us more details on what you have done? I can't wait for you guys to release this into markets and let loose the hax0rs on this .Anonymous
June 18, 2008
me.com is $99 a year, I don't think Microsoft is going to charge you for it, Apple rip you off first. Let's give them time to do it right, and then we judge them.Anonymous
June 22, 2008
I think it's really brilliant to see Microsoft services becoming "Good" again. Companies which want to be a top company, will be doing new "Cloud" services. I think Live Mesh is a totally nice fresh idea which - I think should/will be in the next Windows. I hope the same for Sidebar, integrated into Windows Explorer. Keep it coming MS.Anonymous
June 24, 2008
The comment has been removedAnonymous
September 02, 2008
Hi All, Yesterday, I along with Chris ( from my team) delivered a talk onpervasive computing in a classroomAnonymous
October 08, 2008
Hey there! I’m Viraj Mody , a developer on the Live Mesh services team. I bet some of you are curious