Report: Debugged Processes
A debugged process is a process that is under direct control of a separate process (the "debugging" process). All the memory and execution primitives of a debugged process are visible to the debugging process.
Report Detail: Debugged Processes
Following are the debugged processes at the time the memory snapshot was taken of the ubuntu 14.04 with ptrace image from the samples gallery (requires authentication).
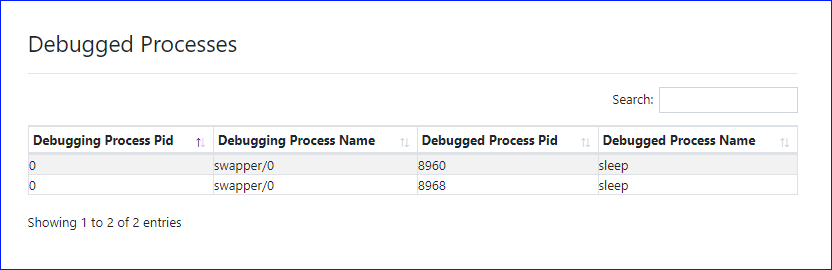
The following table describes each column of the reported data.
| Column | Description | Notes |
|---|---|---|
| Debugging Process Pid | PID of the debugging process | |
| Debugging Process Name | Name of the debugging process | Ensure this process is authorized to debug |
| Debugged Process Pid | PID of the debugged process | |
| Debugged Process Name | Name of the debugged process | Ensure this process is authorized to be debugged |
Forensic Hints
A debugged processes's memory is fully accessible to the debugging process, including any passwords or cryptographic keys. While debugging is a normal occurrence during software development, any unexpected debugging on a production system might be evidence of intrustion. Especially worrisome would be finding that a process that accepts untrusted data (e.g., httpd or named) is debugging or any process that stores sensitive data (e.g., systemd) is being debugged. Note, however, that some processes do normally use tools like ptrace to track performance ofther processes.
This data cannot be obtained from a running Linux system, so an internal-external comparison is not possible.