Update to Supersedence Behaviour for Security Only and Security Monthly Quality Rollup Updates
Further to my recent post about Changes to Software Updates on Down Level Operating Systems for ConfigMgr Admins there has been some changes to how the updates are superseded based on feedback for Windows 7, Windows 8.1, Windows Server 2008 R2, Windows Server 2012, and Windows Server 2012 R2. The official update is explained here More on Windows 7 and Windows 8.1 servicing changes.
UPDATE - there has been some misunderstanding about this post. Note that the way updates are bundled has not changed - simply the way they are superseded which affects the way they can be applied using WSUS or Configuration Manager. See More on Windows 7 and Windows 8.1 servicing changes for details of those changes.
Last month when updates were released, contrary to expectation of organisations using WSUS or Configuration Manager;
- The Security Only Quality Update for October was superseded by the November Security Monthly Quality Rollup for November
- The Security Only Quality Update for November was also superseded by the November Security Monthly Quality Rollup for November
Visually, this was the supersedence relationship for updates last month (red are superseded):
[caption id="attachment_4395" align="alignnone" width="750"]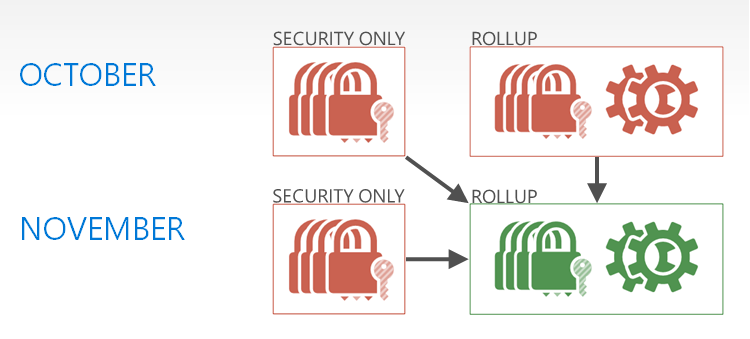 November Update Supersedence Relationships[/caption]
November Update Supersedence Relationships[/caption]
This resulted in customers using WSUS or Configuration Manager 2007 being unable to deploy Security Only Quality Updates using the built in software update mechanisms without additional workarounds.
- Configuration Manager and Simplified Windows Servicing on Down Level Operating Systems
- Deploying Superseded Down Level Windows Updates with Microsoft Configuration Manager 2007
Based on feedback, the team has updated the supersedence relationship of updates so that Security Only Quality Updates are not superseded. In addition, the logic of the updates has been modified so that if the Monthly Quality update is installed (which contains the security updates), the security update will not be applicable. This allows organisations managing updates via WSUS or Configuration Manager to:
- Selectively install Security Only Quality Updates (bundled by Month) at any time
- Periodically deploy the Security Monthly Quality Rollup and only deploy the Security Only Quality Updates since then, and;
- More easily monitor software update compliance using Configuration Manager or WSUS.
An update to previous Security Only Quality Updates will be released as meta data only for the changes to take effect which will require a Software Update (or WSUS) synchronisation.
Visually, this is the new supersedence relationship as of December (red are superseded):
[caption id="attachment_4405" align="alignnone" width="749"]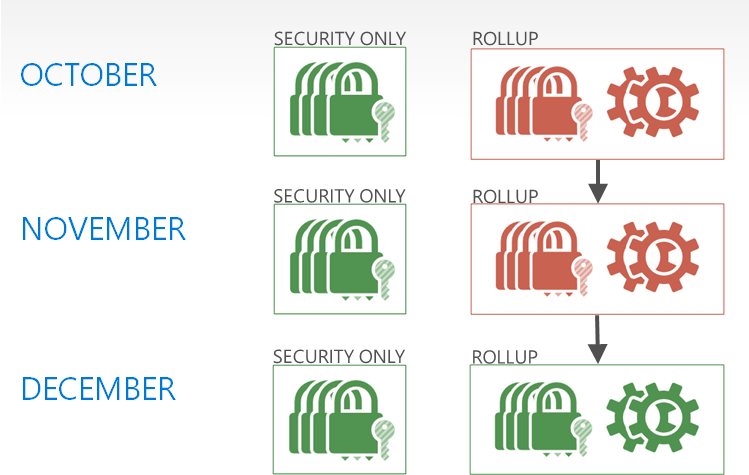 December Update Supersedence Relationships[/caption]
December Update Supersedence Relationships[/caption]
Comments
- Anonymous
December 07, 2016
What is Microsoft's policy about how non-security issues caused by security-only updates will be fixed? That is, will they be fixed in a reissue of the problematic security-only update, in a future security-only update, or not in security-only updates at all?- Anonymous
December 07, 2016
Hi Brian, If any issues are encountered, we recommend stopping or pausing deployment of the update and contacting Microsoft Support as soon as possible. Based on our analysis of the issue, we may recommend different courses of action, such as:Rolling back the update on affected machines while the issue is being investigated.Installation of other updates known to resolve the issue observed.Working with the publisher (ISV) for an affected application.The specific action is determined on a case-by-case basis, and could be different for each customer based on the specific impact to the organisation. Regardless of the action, be assured that any issues with an update are considered top priority and that we will work hard to resolve these as quickly as possible.Your organisation may also be interested in validating updates before they are publicly released, by participating in the Security Update Validation Program (SUVP). This program enables organizations to establish an additional early validation ring within the organization, while also providing a direct channel back to Microsoft for any issues encountered. For more information on SUVP, see https://msdn.microsoft.com/en-us/gg309155.aspx; contact your Technical Account Manager or Microsoft account team to discuss this further.- Anonymous
December 07, 2016
If a problem with the update itself is identified and not a known issue, a revision of the update might be released which resolves the problem. As I said, case-by-case.- Anonymous
December 07, 2016
The comment has been removed- Anonymous
December 07, 2016
The comment has been removed
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous
December 08, 2016
Thanks for the information, Scott! Do we know if this will be retroactively applied so that we can actually report correctly for October and November in SCCM reports?- Anonymous
December 08, 2016
Hi David, the updates will be revised but I admit I'm not 100% sure how this will work with Configuration Manager. I'll be testing as soon as I can after they are released - I'll report back once I know for sure!- Anonymous
December 09, 2016
Thanks, Scott!- Anonymous
December 13, 2016
I've tested Windows Server 2012 R2 and it seems to have updated reporting as expected!- Anonymous
January 11, 2017
Hi, Scott:"An update to previous Security Only Quality Updates will be released as meta data only for the changes to take effect which will require a Software Update (or WSUS) synchronisation."Is this confirmed? one of our client on SCCM2012 R2 SP1, and always only deploy security-only patches. now following two are marked as expired.October, 2016 Security Only Quality Update for Windows 7 for x64-based Systems (KB3192391)November, 2016 Security Only Quality Update for Windows 7 for x64-based Systems (KB3197867)and Dec one KB320539 are showing superseded. However I do see it's fine to server updates in other environment. Thanks, Cliff- Anonymous
January 11, 2017
As far as I know they aren’t supposed to be superseded! I'll let you know what I find out (if anything).- Anonymous
January 11, 2017
Looks like it's resolved. Synchronise your ConfigMgr / WSUS to see the changes :)
- Anonymous
- Anonymous
- Anonymous
January 12, 2017
Thanks a lot for the update, Scott. I think I found the cause of why those two update are expired. Both of them were revised at Dec 13, and I confirmed that the revised version show in WSUS, however it's not reflected in SCCM console, both two still show the original release date in SCCM. Suspected this might be SUP/WSUS sync issue or even database, but haven't figure out how to fix, any suggestion? :-)Thanks again and regards, Cklilff
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous
December 10, 2016
The comment has been removed - Anonymous
December 12, 2016
The comment has been removed- Anonymous
January 11, 2017
If you only wanted security updates and not the rollup - yes. However you could just install the most recent rollup and then you wouldn't need to install all the previous security only updates.
- Anonymous
- Anonymous
December 13, 2016
Does this mean that Security Only Updates will not be superseded as before at all, in the life time of the support of the product?- Anonymous
January 11, 2017
That is the intention at the moment, yes. Security only updates shouldn't be superseded.
- Anonymous
- Anonymous
December 13, 2016
FYI, I tested the supersedence on Servers 2012I just installed the Quality Rollup update for December 2016 (KB3205409) and it appears the Security-Only Update (KB3205408) is still applicable for Server 2012. I was expecting this to not be applicable.What am I missing?- Anonymous
December 13, 2016
Hi Chad, how did you install the updates? WSUS/Configuration Manager? Where did you see that it was still applicable? I haven't tested with Windows Server 2012, but I did test applying them through Configuration Manager with Windows Server 2012 R2 and it seemed to work for me.- Anonymous
December 14, 2016
Hey Scott,I downloaded the updates manually from MSFT catalog and installed them first to test. I installed KB3205409 first, then rebooted. Then I installed KB3205408 successfully. I havent tried 2008 R2 or 2012 R2. Let me give that a try.
- Anonymous
- Anonymous
- Anonymous
December 14, 2016
The comment has been removed- Anonymous
January 11, 2017
I guess you can only provide feedback. I'm a Field Engineer (support) so all I can do is support the products as they are :)
- Anonymous
- Anonymous
December 15, 2016
The comment has been removed- Anonymous
December 20, 2016
@ abbodi86 I was afraid you were going to say that :-/Our company uses a 3rd party product for patching with leverages shavlik engine for scanning updates. I was hoping the manual install would honor the supersedance as well. Thanks for the info tho!- Anonymous
January 10, 2017
The comment has been removed
- Anonymous
- Anonymous
- Anonymous
December 16, 2016
- Being one of those having complained about the supersedence relationship mess since Oct 2016, I was really excited seeing your December 7, 2016 announcement and I fully verified this; now WSUS and even offline scans using wsussn2.cab against security-only OS updates work as expected. Thank you so much for having this fixed in December!2. However, I am quite shocked to see - using latest SUSDB data - that while the promised change was implemented for OS updates properly, the same is unfortunately NOT true for the DotNet related streams of updates. From SUSDB we see:- "October, 2016 Security Only Update for .NET Framework 3.5 on Windows Server 2012 for x64 (KB3188731)" is still superseded by "December, 2016 Security and Quality Rollup for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2 on Windows Server 2012 for x64 (KB3205403)"- "October, 2016 Security Only Update for .NET Framework 3.5 on Windows 8.1 and Windows Server 2012 R2 for x64 (KB3188732)" is still superseded by "December, 2016 Security and Quality Rollup for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2 on Windows 8.1 and Windows Server 2012 R2 for x64 (KB3205404)"This clear violation of what you explained so nicely above again kills us (SCCM 2007/WSUS context as well as offline context)!@Scott: Question: Is this merely because the DotNet group did not read your article ;-)? Or are there any good or bad reasons for DotNet updates not to follow the abovementioned scheme? Could you please shed some light on this?
- Anonymous
January 11, 2017
I was only providing information based on what I'd been told. I haven't looked into the .NET patch situation. If I come across any information I'll pass it on!
- Anonymous
- Anonymous
December 19, 2016
The comment has been removed - Anonymous
January 10, 2017
The comment has been removed- Anonymous
January 11, 2017
It does seem to have changed. I'll let you know what I find out (if anything).- Anonymous
January 11, 2017
Looks like it's resolved. Synchronise your ConfigMgr / WSUS to see the changes :)- Anonymous
January 12, 2017
Thanks, all working again :)
- Anonymous
- Anonymous
- Anonymous
- Anonymous
January 10, 2017
The comment has been removed- Anonymous
January 11, 2017
It does seem to have changed. I'll let you know what I find out (if anything). As far as I know they aren't supposed to be superseded!- Anonymous
January 11, 2017
Looks like it's resolved. Synchronise your ConfigMgr / WSUS to see the changes :)
- Anonymous
- Anonymous
- Anonymous
January 11, 2017
The comment has been removed- Anonymous
January 11, 2017
As far as I know they aren't supposed to be superseded! I'll let you know what I find out (if anything).- Anonymous
January 11, 2017
Looks like it's resolved. Synchronise your ConfigMgr / WSUS to see the changes :)- Anonymous
January 12, 2017
Thanks!
- Anonymous
- Anonymous
- Anonymous
- Anonymous
January 15, 2017
The comment has been removed - Anonymous
January 16, 2017
The comment has been removed