HYPER-V R2 Networking – How to configure management and VM networks
Hi All :-)
I see very often confusion around the configuration of the hyper-v networking and the creation of the virtual networks (Hyper-V). Therefore I will try to give you here an short / simple overview how you can configure your Hyper-V Host networking environment in regards to best practice which ensures the reliability and availability of your virtualized workloads.
Generally there are three different types of networks available :
EXTERNAL
External networks are mainly used for "”PUBLIC” communication = provide VMs access to network where physical NIC is connected which is used for EXTERNAL network creation. NOTE: For high availability and throughput reasons NIC teaming is possible here, but must be supported from NIC manufacturer.
INTERNAL
Internal networks are dedicated on the Hyper-V host only, The difference between an PRIVATE network here is only, the virtual adapter (loopback) which will be created on host with an INTERNAL network. This loopback adapter can be used to get TCP/IP access to the INTERNAL network from the HOST only. For this you need to assign an IP address from the IP subnet which you want to access.
PRIVATE
An private network is private only = no TCP/IP communication from host to VMs possible = isolated VMs/network.
1. EXTERNAL (VM <-> PUBLIC NETWORK ACCESS)
This network type must be used when you need external “PUBLIC” connectivity for your Virtual Machines. VMs or better their virtual network adapters (vNIC) which are bound in their VM settings to this network will have logical access to the same network as the underlying physical NIC (pNIC) connected is. Hope that is so far clear ![]()
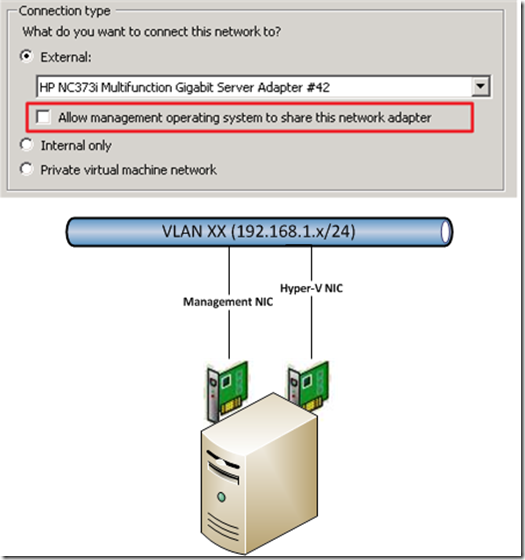
In R2 (SP1) Hyper-V systems it is possible AND best practice to have an DEDICATED pNIC for the VM networking. This is configurable trough the setting “ALLOW MANAGEMENT OPERATING SYSTEM TO SHARE THIS NETWORK ADAPTER”. If you want to give the physical network adapter (pNIC) dedicated to the VM network traffic then UNCHECK this setting!
An Best Practice Example with minimum 2 physical NIC ports where both are connected to same network/subnet. One physical NIC is used for management traffic to Hyper-V host system and 2nd physical NIC is exclusively for the VM traffic. Each VM which are connected to the Virtual Switch in Hyper-V does have network access to the underlying connected network/subnet.
The effect of “Allow management OS to share this network adapter” setting is:
Checked => Adapter is shared with OS and Hyper-V
Unchecked => Adapter is DEDICATED to Hyper-V ONLY
For lab/test environments the physical adapter can also be shared (Checked : “Allow management OS to share this network adapter”) but it is not a recommended scenario for production usage! Physical server-class NICs are also a recommendation here!
EXAMPLE:
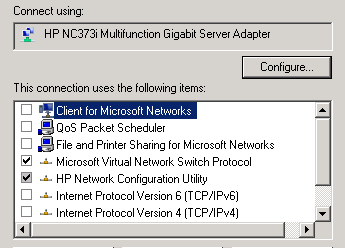
When I create here an “EXTERNAL” network which is called “PUBLIC – EXTERNAL” here and bound to my HP NC373i which is connected to VLAN1 (192.168.0.x) then each VM which are later connected to this virtual network will have access to VLAN1 – of course if their IP settings are correctly set ![]() In addition there will no Virtual Adapter (Switch) created as in RTM times as we had chosen to dedicate the pNIC for this External switch and will therefore NOT be shared ! You will monitor in the properties of your selected pNIC that Hyper-V will unbind all protocols (except 3rd Party Management Software) A.e.: In my case, the used HP NC373i adapter – Added New Protocol –> “Microsoft Virtual Network Switch Protocol” ONLY!
In addition there will no Virtual Adapter (Switch) created as in RTM times as we had chosen to dedicate the pNIC for this External switch and will therefore NOT be shared ! You will monitor in the properties of your selected pNIC that Hyper-V will unbind all protocols (except 3rd Party Management Software) A.e.: In my case, the used HP NC373i adapter – Added New Protocol –> “Microsoft Virtual Network Switch Protocol” ONLY!
NOTE : no further IP communication to host via this adapter is possible as this adapter will now be exclusive used by Hyper-V virtual machines which are connected to the belonging external VSwtich!
2. INTERNAL (HOST <-> VM)
The network type “INTERNAL” should be used when you require ONLY VM INTERNAL networking communication. The “speciality” here is, an virtual NIC (loopback) adapter will be created on the host where you then can configure an IP from the VM Network IP segment and would therefore gain network access into the VM “INTERNAL” network subnet.
EXAMPLE:
When I create here an INTERNAL network called “New INTERNAL Network” where I do required HOST <-> VM INTERNAL ONLY communication – IP Network 10.0.1.x - this action will automatically create an vNIC (earlier Virtual Server times = similar to loopback adapter) on my Hyper-V Host. Now I can configure an IP address of that (INTERNAL) IP segment (a.e. 10.0.1.99) and I would be able to communicate from HOST to GUEST or vice versa via network TCP/IP communication.
Now, there will be an “Virtual” NIC created on my Hyper-V Host where I can configure the TCP/IP settings of the VMs IP network range: 
3. PRIVATE (Same Host: VM <-> VM ONLY)
This network should be used when you want to create an VM ONLY networking (PRIVATE) WITHOUT host access. This is mainly used when you want to establish an totally secure and separated network environment for testing purposes (security, cloning, restore…). Here you will not be able to establish an network communication between HOST and GUEST – the only possible method here for data exchange between host and guest is the Hyper-V ISO sharing method !
At example :
When I create here an PRIVATE network called “My PRIVATE Network” there will no (vNIC) created on the Hyper-V HOST like in example with INTERNAL network. This PRIVATE Hyper-V internal virtual network switch will be later selectable in the “available” network list where you can connect your Virtual Machines virtual network adapters (vNIC) to it. This will establish an VM-VM communication if the TCP/IP settings are configured correctly.
Hope that helps a bit to an general understanding around the configuration for Hyper-V R2 networks and the usage scenarios.
Again, It is BEST PRACTICE to configure dedicated physical adapters and separate the VM and management network traffic!
Additionally here are in addition some more useful links and published documentation around Hyper-V networking :
UNDERSTANDING HYPER-V NETWORKING
USING HYPER-V AND FAILOVER CLUSTERING
HYPER-V – LIVE MIGRATION NETWORK GUIDE
If you still have any questions please let me know.
Stay tuned…. ![]()
Regards
Ramazan
Comments
- Anonymous
May 03, 2011
According to the Hyper-V documentation, you can use the internal type of network to do host > VM as well as VM > VM (if the VM's are running on the smae physical pc).- Anonymous
May 04, 2011
Hi Scott,this is correct as documented in this blog post. An internal networks creates an "kind of" loopback adapter at the host, private will not. When you then assign an IP from your "internal" network range, then you can access from host the VMs network directly. Hope that helps.RegardsRamazan
- Anonymous
- Anonymous
May 21, 2011
Fantastic to be browsing your website again, that continues to be weeks for me. - Anonymous
November 18, 2011
Hi Ramazan, I have a new server with a total of 8 NICs. One dedicated for host machine management, 6 will be setup as external NIC's with each one being dedicated to a specific VM, and the last will be setup for use by multiple different low utilizing VM's. My question is, will it be best to also setup a Private network on each of the 6 VM's with dedicated external NIC's. This way the 6 VM's can have direct access to each other without having to leave the server to hit the physical switch and come back to the server to talk with each other.Or does this create other problems???- Anonymous
September 17, 2012
Generally the idea is good but it really depends how much network traffic do you expect later? A gigabit theoretic throughput is ~120MB/s you need to think about if the physical underlying disks can handle all the I/O? Therefore I would start with single NIC and monitor network util and if required add private network. This is from routing possible only important thing is do never use more than 1 default gateway and cross check your routing tables ;))Btw, why do you not NIC team all 6? I think depends on driver but traffic could be handled locally without switch interactionJust my 2 centsRamazan Can- Anonymous
September 17, 2012
The comment has been removed- Anonymous
September 17, 2012
Yeah correct :) was really busy last year... Ohh yes, if you are currently moving to a clustered environment I would recommend to overlook 2012 RTM which hypervisor is very stable and more tight I integration into cluster. Also lot of great improvements for network and storage virtualization....great storyboard with system center ;))
- Anonymous
- Anonymous
- Anonymous
- Anonymous
July 31, 2012
Great article. We use Hyper-V Failover Cluster Manager to monitor the networks. The problem is when you uncheck the "allow mgmt os to share this network adapter" for our virtual machine external virtual network (which we have teamed) it then disappears from the FCM console and we can't monitor it from here. Is there any way of fixing this?- Anonymous
September 17, 2012
No, this is by design and correct as there is no way for OS to control the NIC anymore as dedicated for Hyper-V ;))Hope that helpsRamazan Can
- Anonymous
- Anonymous
November 14, 2012
Hi GuysI'm a bit lost still, here is what i want to do:I have a physical cable from my switch to my host (192.168.1.20(static)) I then created 2 vm servers on the host. how would i configure the Hyper-v to produce addresses for these VM? also remember on of the servers will have a DHCP running.PS this is a test lab :) Server 2012 sp1 HYPER-VKind RegardsDenzel- Anonymous
June 23, 2013
for test lab you can use a single network connection and create a New external hyper-v switch and enable the checkbox "allow host OS to share...". In production I wouldnt recommend this ;)
- Anonymous
- Anonymous
January 12, 2013
The comment has been removed- Anonymous
March 18, 2013
have a look on 2012 virtualization improvements and it's builtin and "unlimited" ;)
- Anonymous
- Anonymous
June 24, 2013
It's hard to come by experienced people about this topic, but you seem like you know what you're talking about! Thanks