Tip of the Day: The Conditional Access Framework and Device Compliance for VPN
Today’s Tip…
The removal of NAP in Windows 10 left no viable Device Compliance mechanism for remote access clients. The Conditional Access Framework, a cloud-based policy engine built into Azure AD, includes a collection of services that fill this gap. The Conditional Access Framework and its companion services are ideal for assuring health of devices requesting VPN access to corporate networks, as well as other online services such as SharePoint and Exchange Online.
What exactly is Conditional Access?
Because the use of mobile devices to access corporate information continues to rise, some way to evaluate device security or health is required. An efficient end-to-end security approach should be able to evaluate device health and use the current security state to make a real-time decision about whether to grant access to a high-value asset.
How Conditional Access Works
When access to a managed resource (VPN, for example) is requested, the device authenticates the user through a connection to an identity provider, such as Azure Active Directory, in the cloud. If the managed resource contains highly confidential information, the conditional access engine of the identity provider may elect to verify the security compliance of the mobile device before access is granted.
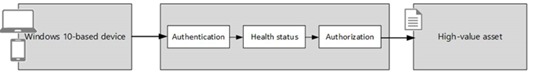
A simple conceptual flow is as follows:
Figure 1
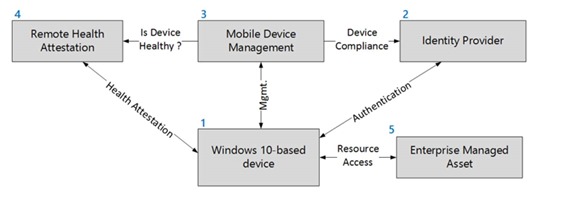
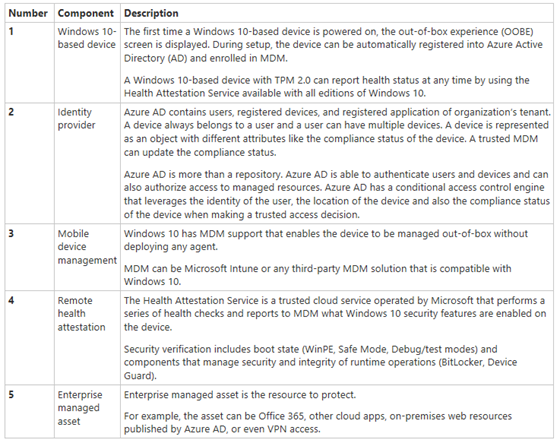
The combination of Windows 10-based devices, identity provider, MDM, and remote health attestation creates a robust end-to-end-solution that provides validation of health and compliance of devices that access high-value assets.
Figure 2
In summary, Azure Active Directory includes the ability to control access to resources (that use the AAD ID) based on many types of rules of which Device Compliance is one.