Manually hooking up DKIM signing in Office 365
Note: This content also appears on our official documentation here, Use DKIM to validate outbound email sent from your domain in Office 365.
Here’s how to enable DKIM signing for your domain if it is hosted in Office 365 (Exchange Online Protection).
What steps do I have to take to enable DKIM?
First, for each domain that needs to DKIM sign, you will need to publish two CNAMEs in DNS (not TXT records):
Host name: selector1._domainkey
Points to address or value: selector1-<domainGUID>._domainkey.<inititalDomain>
TTL: 3600
Host name: selector2._domainkey
Points to address or value: selector2-<domainGUID>._domainkey.<inititalDomain>
TTL: 3600
The <domainGUID> is the same as the <domainGUID> in the customized MX record for yourdomain that appears before mail.protection.outlook.com. For example, for a domain contoso.com:
contoso.com. 3600 IN MX 5 contoso-com.mail.protection.outlook.com.
The <domainGUID> is contoso-com.
The <initialDomain> is the same one that you signed up with for Office 365. For example, contoso.com may have signed up with contoso.onmicrosoft.com. Therefore, the two CNAMEs that contoso.com would publish are the following:
Host name: selector1._domainkey
Points to address or value: selector1-contoso-com._domainkey.contoso.onmicrosoft.com
TTL: 3600
Host name: selector2._domainkey
Points to address or value: selector2-contoso-com._domainkey.contoso.onmicrosoft.com
TTL: 3600
In the above, the host name does not contain the full FQDN of the domain you are provisioning. You could explicitly include the full thing, that is, instead of Host name selector1._domainkey, you could put selector1._domainkey.<domain>.
For each other domain you have provisioned with Exchange Online, you will need to enable DKIM signing for it.
For example, if your initial domain is contoso.onmicrosoft.com and you have provisioned contoso.com and fabrikam.com, you will need to provision 4 CNAMEs (two for each domain). The two CNAMEs are so that we can perform automatic DKIM key rotation for you.You need to do this for each domain that you use to send email. DKIM signing does not inherit DKIM settings for other domains that you have provisioned for your organization. For a company trying to DKIM-sign contoso.com and fabrikam.com, you'd have four additional DNS records that look like this:
selector1._domainkey.contoso.com IN CNAME selector1-contoso-com._domainkey.contoso.onmicrosoft.com
selector2._domainkey.contoso.com IN CNAME selector2-contoso-com._domainkey.contoso.onmicrosoft.com
selector1._domainkey.fabrikam.com IN CNAME selector1-fabrikam-com._domainkey.contoso.onmicrosoft.com
selector2._domainkey.fabrikam.com IN CNAME selector2-fabrikam-com._domainkey.contoso.onmicrosoft.com
Do not set up TXT records; if you set up TXT records and not CNAME records you have done it incorrectly!
Second , you need to enable DKIM-signing for the domain within the service. You can do this in the UX by going to protection > dkim and clicking Enable for each domain you own: 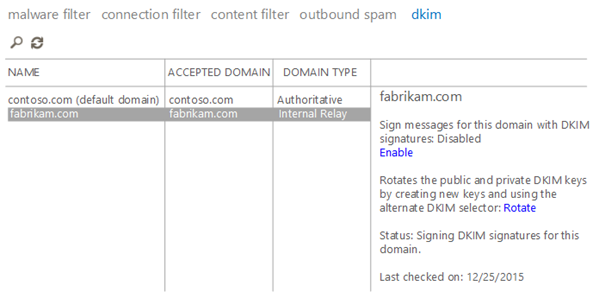
Alternatively, if you use Powershell, connect to Exchange Online using Powershell and then run the following cmdlet:
New-DkimSigningConfig –DomainName <domain> –Enabled $true
Or, let us know when done and we will enable on the backend, you can request this by opening up a support ticket telling us which domains you want DKIM-signing for. We will then create the 1024-bit DKIM public keys and the associated private keys which we store internally.
How do I know it worked?
In either case above, when done, a DKIM-signed message will look like the following:
From: Example User <example@contoso.com>
DKIM-Signature: v=1; a=rsa-sha256; q=dns/txt; c=relaxed/relaxed;
s=selector1; d=contoso.com; t=1429912795;
h=From:To:Message-ID:Subject:MIME-Version:Content-Type;
bh=<body hash>;
b=<signed field>;
Or like this:
From: Example User <example@contoso.com>
DKIM-Signature: v=1; a=rsa-sha256; q=dns/txt; c=relaxed/relaxed;
s=selector2; d=contoso.com; t=1429912795;
h=From:To:Message-ID:Subject:MIME-Version:Content-Type;
bh=<body hash>;
b=<signed field>;
The DKIM-signed messages will align with DMARC (the d= domain will align with the 5322.From domain). This is even true for SMTP bounces where the MAIL FROM is <>.
To test it out, wait a few minutes for the newly enabled DKIM domains to replicate throughout the network, then send a message to another account such as your Outlook.com/Hotmail account, Yahoo account, Gmail account, or other account that you have access to. Open up the message and look at the message headers, looking for the Authentication-Results header. Each service stamps it a little differently, but it will say dkim=pass or dkim=ok or something similar.
If you send to an aol.com account, it may not work because AOL may skip the DKIM-check if the SPF-check passes and aligns with the domain in the From: address.
To test whether or not your DNS records or DKIM settings are properly configured, you can use this Powershell script to help you verify your DKIM config.
Can I set the DKIM key size?
You don’t need to set the size of the DKIM keys,
Do I have to rotate the keys?
No, you don't need to rotate the keys because we do that for you. Once you set it, you can forget it.
How do I add another domain for DKIM signing?
To DKIM sign another domain, you must go through the above steps for each of the domains you want to DKIM sign unless you want to have them signed with the default DKIM signature for your organization (see below on Disabling DKIM).
How do I troubleshoot delivery problems with DKIM?
There are some email receivers on the Internet that reject email due to a broken DKIM signature. A DKIM signature can break for multiple reasons:
a) If you have another mail server positioned after Office 365 that relays out to the Internet, it may modify the message content and cause the DKIM signature not to verify. If this occurs, you should ensure that Office 365 is the last service to relay out to the Internet, otherwise you may get some email bounces due to a broken DKIM signature.
b) Some messages get forwarded and modified in transit at the receiver side.
In cases like this, messages with failed DKIM signatures are not supposed to be bounced by the receiver, as per RFC 6376, section 6.1 and 6.2. If you continue to receive bounces, you should contact the recipient and inform them that rejecting on failed DKIM signatures is against the RFC because messages can be modified in transit, it is not malicious. In addition, you can ask them to locally allow your messages that are failing DKIM.
How do I disable DKIM signing?
To disable the DKIM signing policy, you need to use the following Powershell commands:
$p=Get-DkimSigningConfig –identity <domain>
$p[0] | set-DkimSigningConfig –enabled $false
OR
Set-DkimSigningConfig –identity $p[0].identity –enabled $false
Use $p[X] where X is the index of the policy.
However, this doesn't disable DKIM signing completely. Even if you don't enable DKIM, Office 365 will still (eventually) enable DKIM signing for your domain using the default signing configuration. Suppose that fabrikam.com was enabled by Office 365, not by the admin of the domain (so the required CNAMEs do not exist in DNS). DKIM signatures will look like the following:
From: Second Example <second.example@fabrikam.com>
DKIM-Signature: v=1; a=rsa-sha256; q=dns/txt; c=relaxed/relaxed;
s=selector1-fabrikam-com; d=contoso.onmicrosoft.com; t=1429912795;
h=From:To:Message-ID:Subject:MIME-Version:Content-Type;
bh=<body hash>;
b=<signed field>;
In the example above, the selector and d= domain contain the values where the CNAME would point to had DKIM-signing for fabrikam.com been enabled by the customer. Eventually, every single message out of Office 365 will be DKIM-signed. If you enable DKIM yourself, the d= domain will align with the domain in the From: address; if not, it will not align and instead will have your organization's initial domain.
* * * * * * * * * * * * * * *
And that’s it. As I say at the top of this post, this is only a short term solution and eventually it will all be self serve (that is, asking us to enable it for you will no longer be required, you still need to set up the CNAMEs).
Happy DKIM signing!
Comments
Anonymous
October 09, 2015
Good news but the helpdesk does not seem to be up to date with the manual activation process. Below is the response I received. "According to the provided details on the case, I have discussed with my Technical Advisor on the Exchange Online Protection technology and he has informed me that this features hasn't been implemented yet ; in theory there have been some activations made, followed by occurring issues - it is still in production phase ; after deployment you should be able to activate it manually, or within the Office 365 portal; at the moment we do not have an exact time when this will be implemented."Anonymous
October 09, 2015
Just tell them to create a support ticket and have it routed to the Antispam team.Anonymous
October 21, 2015
Terry -- thanks for the help in getting this set up and the clear presentation above. Now that I have fixed my own typos in my CNAMEs, I'm looking forward to putting this new feature to work.Anonymous
October 24, 2015
If we run the PowerShell cmdlet do we also need to open a support ticket?Anonymous
October 26, 2015
The comment has been removedAnonymous
October 28, 2015
The comment has been removedAnonymous
October 29, 2015
@Phillip -- it sounds like Terry's team already set up your signing config, based on your request. Is your signing working?Anonymous
October 30, 2015
To delete (or re-enable an existing) DKIM policy, you have to get creative with Powershell: $p=Get-DkimSigningConfig-Organization <domain> $p[0] | set-DkimSigningConfig –enabled $true OR Set-DkimSigningConfig –identity $p[0].identity –enabled $true Use $p[X] where X is the index of the policy.Anonymous
November 01, 2015
What's wrong when >I get the error that New-DkimSigningConfig is not a valid object or cmdlet? Does that mean that this Feature is not rolled out to my Account yet? Or am I making a mistake?Anonymous
November 02, 2015
If the cmdlet is generating an error, open up a support ticket. It may be that your domain's forest is not enabled.Anonymous
November 04, 2015
The comment has been removed- Anonymous
November 07, 2017
The comment has been removed- Anonymous
December 01, 2017
I have the same issue. Did anybody found a solution?
- Anonymous
- Anonymous
Anonymous
November 11, 2015
I had issues running the cmdlet, however support gave me another script to run than the normal connect to O365 one I have been using: $LiveCred = Get-Credential $Session=New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri ps.outlook.com/powershell -Credential $LiveCred -Authentication Basic –AllowRedirection Import-PSSession $Session Seemed to get the job done. Took a bit to import everything.Anonymous
November 17, 2015
Where do I get DKIM keys for "domainkey"?Anonymous
November 18, 2015
The comment has been removedAnonymous
November 20, 2015
Based on this implementation of DKIM, I assume there is no way to have a third-party send DKIM signed messages on our behalf correct?Anonymous
November 20, 2015
The comment has been removedAnonymous
November 23, 2015
Following these directions, "-Organization" is not a valid parameter for Get-DkimSigningConfig. I have to use "-Identity" instead, and it works fine. Just me, or has the cmdlet been modified?Anonymous
November 25, 2015
The comment has been removedAnonymous
November 25, 2015
To the comment above this one - I have updated the cmdlet. I mixed it up because what you as a customer types in is different than what I as a developer have to type when I try to debug someone's account.Anonymous
November 25, 2015
Is this considered production ready? I've implemented this about a week ago and today enabled DMARC records with p=none. I'm getting reports back from facebook and hotmail that some of Office 365's servers are not signing messages.Anonymous
November 25, 2015
Thanks! Managed to set up DKIM signing, but Automatic Replies and Non-Delivery Receipts aren't signed with DKIM, and fails DMARC. Will those be signed with DKIM in future?Anonymous
November 25, 2015
Sorry double checked, and NDRs are already signed properly. Automatic Replies are not signed, so automatic replies to external senders will fail DMARC.Anonymous
November 26, 2015
@Zyonix: We're looking into how to ensure signing of automatic replies.Anonymous
December 07, 2015
I was so happy to see this and make us 100% DMARC compliant. Still dissappointed though... Powershell keeps giving errors on our domain. We can only activate for ourdomain.onmicrosoft.com, which fails DKIM aligment for DMARC...Anonymous
December 08, 2015
Though I left it out of my prior post (re DKIM signing not occurring), my approach was to allow time for things to "bake in." Sure enough, signing is now functioning as expected.Anonymous
December 10, 2015
Thanks for the easy to follow instructions. Worked on the first try. I've been waiting for this feature for quite some time :-)Anonymous
December 11, 2015
The comment has been removedAnonymous
December 20, 2015
Awesome! Great to see Office365 promoting DKIM - this way it becomes easily available also for small and medium businesses! We are currently trying DKIM, DMARC and SPF for our Domains on office365! I used your PowerShell instructions to set up DKIM, without any problem doing so... However, using dmarcian.com as a tool to observe DMARC results, I see that only about 50% of our outgoing mails are DKIM signed (SPF pass 100%) - those are messages originating from *.outbound.protection.outlook.com Servers... Is this intentional behavior so before rolling it out officially? Or is this an unknown issue limited to our domains? Anybody else observing this ?Anonymous
December 22, 2015
The comment has been removedAnonymous
December 22, 2015
The comment has been removedAnonymous
December 23, 2015
After DKIM Outbound Signing is enabled and now I want my MFP device to send email to an Internal or External using Client Submission relay then what are the steps to make sure that it will not cause false positive.Anonymous
December 28, 2015
I need to look into why this behavior is the way it is. I provisioned a new subdomain under my own tenant, but I don't have the option to enable DKIM for it in the UX. It could be a propagation time thing. Stay tuned.Anonymous
December 29, 2015
@tzink How do I publish the CNAME? Error: "CNAME record does not exist for this config. Please publish a CNAME record first."Anonymous
December 29, 2015
@jc: I have to open a bug on that, I don't know why it is saying that.Anonymous
December 29, 2015
@tzink Thanks - keep me posted!Anonymous
December 29, 2015
The comment has been removedAnonymous
December 29, 2015
The comment has been removedAnonymous
December 29, 2015
There are some spelling errors in my last post: all should be "contoso" instead of "consoto"Anonymous
December 30, 2015
@jc: Please contact me via the "Contact me" link with your tenant domain and I will take a look. blogs.msdn.com/.../contact.aspxAnonymous
January 06, 2016
Hi Terry, I tried to follow instructions in this blog post, but in the UX (for all domains in protection -> dkim) the status is "No DKIM keys saved for this domain". Should I contact the support or is there anything I should do first? I tried to verify if selector1-<our domain-com>._domainkey.<initial domain>.onmicrosoft.com has a TXT record, but it doesn't exist (selector2 also doesn't exist). Thanks, AndrzejAnonymous
January 07, 2016
The comment has been removedAnonymous
January 11, 2016
The comment has been removedAnonymous
January 11, 2016
The comment has been removedAnonymous
January 11, 2016
I don't even have a "DKIM" in the UX on my EOP account, does that mean I cannot use it?Anonymous
January 13, 2016
The comment has been removedAnonymous
January 16, 2016
$p=Get-DkimSigningConfig –identity <domain> $p[0] | set-DkimSigningConfig –enabled $true --> Shouldn't this be $false?Anonymous
January 17, 2016
My tenant is already configured, the UI shows "Enable", but the e-mails never get signed. Already have a support open (SRX616011194468149ID) since 01/10/16, but until now, nothing got signed.Anonymous
January 17, 2016
Sorry it shows "Enabled" And thicket: SRX616011194468149IDAnonymous
January 23, 2016
Plesk is not accepting this solution with cname. What to do?Anonymous
January 25, 2016
I enabled DKIM on one of my domains (Office 365 Enterprise Plan). Using DKIM checkers and gmail, DKIM showed as pass, but on yahoo mail the received mail message header showed dkim=temperror (key retrieval failed). Another domain I controlled (Office 365 Business Premium) did not have such a problem. The message header showed dkim=pass (ok) Why would this be the case? In addition, I thought maybe if I rotated the keys, it might pass Yahoo's check. I tried to rotate DKIM keys on the Exchange admin interface and it was not able to do soAnonymous
February 05, 2016
Terry, this record syntax works great on the primary tenant domain, but it's not working on the subtenant domains (which we own). How do you create the record for the subtenant domains? Thanks!Anonymous
February 06, 2016
Terry, I can confirm what Jose, Ace, and Carol have described above (I too have a support ticket open and the engineers have no idea what is going on). There is something on the back-end of Office 365 that is not working correctly, as the messages come across as not signed. DeanAnonymous
February 14, 2016
In our case, our tenant was not enabled for DKIM. After scaling it to the enginners, they manged to enable it manually. This took +/- 25 days, so insist on the Service Request. Now it is working 100%.Anonymous
February 22, 2016
The comment has been removedAnonymous
February 24, 2016
@Michelle As I explain in this blog post, you don't generate a signature. We do that for you, all you need to do is (a) create the CNAME, and (b) enable DKIM signing in the Office 365 Admin portal.Anonymous
March 09, 2016
The comment has been removedAnonymous
March 10, 2016
In the example you provided, Fabrikam’s CNAME record discloses its relationship to Contoso (because the initial domain for the tenant was contoso.onmicrosoft.com). Is there a way to avoid revealing that a domain is provisioned on the same Office365 tenant as another domain?Anonymous
March 18, 2016
So, say, I have a handful of hmail servers.And I want to use the same signing key with those and 365.And, maybe, want to actually have control over my own dkim record.Is there a way to import/export a particular key?- Anonymous
March 18, 2016
@Rex: No, there's no way to bring your own key into Office 365, or export your private key. It isn't necessary, you can always generate a new public/private keypair and publish them at a different selector.
- Anonymous
Anonymous
April 06, 2016
The comment has been removedAnonymous
April 19, 2016
The comment has been removed- Anonymous
May 10, 2016
The comment has been removed - Anonymous
May 18, 2016
The comment has been removed
- Anonymous
Anonymous
May 18, 2016
The comment has been removed- Anonymous
May 18, 2016
The comment has been removed- Anonymous
May 19, 2016
The comment has been removed
- Anonymous
- Anonymous
Anonymous
June 13, 2016
How long does it take for the Enable/Disable option to show up after adding this domain to my tenant? so far it's not there after 1hour.Anonymous
August 22, 2016
Use this link please:https://gallery.technet.microsoft.com/DKIM-works-better-than-SPF-ad6bd13eAnonymous
September 11, 2016
Can you confirm that domains with a dash in between are supported to enable DKIM in office 365?my current customer has a my-domain.com and we're having issues adding the records in godaddy.- Anonymous
September 28, 2016
Yes, domains with a dash can use DKIM. The dash is replaced with some letter/number characters similar to the way it is in the MX record.
- Anonymous
Anonymous
September 15, 2016
I am trying to enable DKIM for my domain with Office 365. I have set the C name records on the host. When I try to enable DKIM under Protection tab, it just displays 'No DKIM keys saved for this domain'.- Anonymous
September 28, 2016
Karthikeyan, try connecting to your tenant using Powershell and use the "Get-DkimSigningConfig | fl CNAME" cmdlet associated with the domain you are trying to enable. Make sure that you don't have any typos.
- Anonymous
Anonymous
December 04, 2017
Are Microsoft not already signing emails with .onmicrosoft.com?- Anonymous
December 04, 2017
Yes, those *.onmicrosoft.com domains get DKIM-signed.
- Anonymous