4.1 S4U2self Single Realm Example
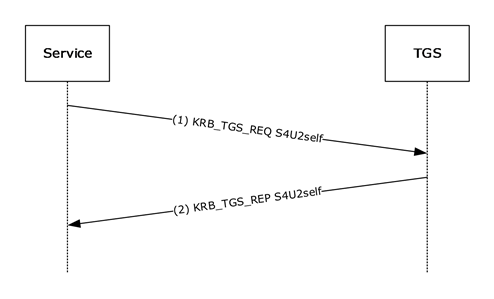
The following figure depicts the S4U2self KRB_TGS_REQ message being processed from the service to the Kerberos TGS. In this case, the user's account belongs to the same realm as the service.
Figure 4: S4U2self KRB_TGS_REQ
The precondition to the previous figure is that the service has already authenticated to the KDC and has a TGT.
In step 1, the service uses the S4U2self extension to retrieve a service ticket to itself on behalf of the user. The service fills out the PA_FOR_USER data structure and sends the KRB_TGS_REQ message to the TGS.
Assuming that the TGS supports the PA_FOR_USER extension, the TGS returns the service ticket for the user in the KRB_TGS_REP message in step 2. The privilege attribute certificate (PAC) returned in the service ticket contains the authorization data, as specified in [MS-PAC] section 3. If the service requested the forwardable option and the local policy of the TGS allows it, the TGS shall set the ticket-flag field to forwardable.