Implement auto-labeling policies
As we follow the global consulting firm's efforts to enhance its data security, we now explore the implementation of auto-labeling policies within Microsoft Purview Information Protection. This step is important for managing sensitive information across SharePoint Online, OneDrive, and Exchange Online, automating the sensitivity labeling process. This automation ensures consistent data protection across the firm’s digital platforms, reducing the dependence on manual labeling.
Client-side vs. service-side labeling
There are two different methods for automatically applying a sensitivity label to content in Microsoft 365:
- Client-side labeling enables users in Office apps to interactively apply or reject recommended labels.
- Service-side labeling automatically applies labels to content within SharePoint, OneDrive, and Exchange Online, without requiring user intervention and ensuring organization-wide consistency.
Configure client-side auto-labeling for Office apps
Make sure your Office apps meet the version requirements for automatic labeling. You can use the Azure Information Protection client to auto-label documents and emails based on their sensitive information types.
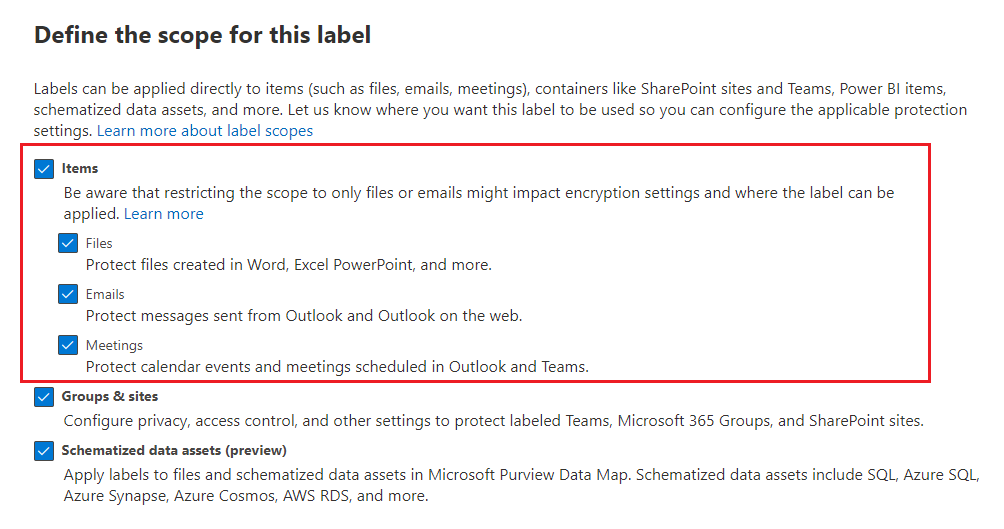
When you set up auto-labeling, select Items as the scope of your label to enable labeling for Files and Emails. This setting allows documents and emails be automatically labeled according to your sensitivity label settings.
As you move through the configuration, you see the Auto-labeling for files and emails page where you can choose from a list of sensitive info types or trainable classifiers:
When this sensitivity label is automatically applied, the user sees a notification in their Office app. For example:
You can configure sensitive information types and trainable classifiers for auto-labeling to automatically apply labels to content with personal information, like credit card numbers. When using exact data match (EDM), include at least one non-EDM sensitive information type to ensure auto-labeling remains enabled. Trainable classifiers expand detection capabilities, subject to specific Microsoft 365 Apps version requirements.
You can also configure sensitivity labels for Office apps to suggest users to apply sensitivity labels, letting them choose to accept or reject based on the content. In desktop versions of Word, users can see the sensitive content that caused the label suggestion, helping them make informed decisions. You can customize the suggestion message to further direct user actions by adding specific organizational references.
Configure service-side auto-labeling for SharePoint, OneDrive, and Exchange
To use service-side auto-labeling in Microsoft 365, you have to meet certain requirements and have an understanding of simulation mode.
Prerequisites for service-side auto-labeling
- Auditing for Microsoft 365 must be enabled.
- To view file or email contents in the source view, you must have the Data Classification Content Viewer role, which is included in the Content Explorer Content Viewer role group, or Information Protection and Information Protection Investigators role groups. Without the required role, you don't see the preview pane when you select an item from the Items to review tab. Global admins don't have this role by default.
- To auto-label files in SharePoint and OneDrive:
- Sensitivity labels must be enabled for files within these services.
- Files shouldn't be open or checked out during the auto-labeling process.
- For using sensitive information types, ensure they're set up before the policy creation and consider testing with new documents.
- Using document properties as a condition (Document property is) relies on SharePoint managed properties, similar to data loss prevention (DLP) policy setup.
- Label configuration:
- Labels used in auto-labeling can include visual markings but note that these markings don't apply to documents automatically.
- Labels that enforce encryption must follow specific settings related to permissions and content access expiration.
Understand simulation mode
Before labels can apply automatically, simulation mode is required and allows testing up to 1,000,000 files that match the policy. If this limit is surpassed, the policy needs to be modified and simulated again.
Workflow for an auto-labeling policy
Create and configure an auto-labeling policy.
Run the policy in simulation mode, which can take 12 hours to complete.
Review the results, and if necessary, fine-tune your policy.
Repeat analysis and adjustment as necessary.
Once the results from the simulation are satisfactory, proceed with policy deployment.
Simulation mode lets you refine the policy's accuracy before its full deployment. This process involves gradually expanding the policy's scope and estimating the time needed for its complete application. Regular checks of simulation outcomes against expected results are important, with adjustments made as necessary to align with any changes in content.
Creating an auto-labeling policy
- Access the Microsoft Purview compliance portal and navigate to Solutions > Information protection > Auto-labeling. If the Auto-labeling option is unavailable, it might not be supported in your region due to backend dependencies.
- Select + Create auto-labeling policy This starts the New policy configuration.

- On the Choose info you want this label applied to page, select a template (for example, Financial, Privacy) or select Custom policy if templates don't fit your needs. Select Next.
- Name your policy and optionally provide a description on the Name your auto-labeling policy page.
- If using administrative units, select them on the Assign admin units page to restrict policy scope. Otherwise, select "Full directory" to include the entire organization.
- On the Choose locations where you want to apply the label page, specify where the label applies: Exchange, SharePoint, and OneDrive. Choose specific instances to include or exclude as needed and proceed by selecting Next.

- The Set up common or advanced rules page lets you define labeling rules using conditions like sensitive information types, trainable classifiers, sharing options, and more. Choose between common rules for all locations or advanced rules for specific conditions and select Next.
- Define new rules using conditions and exceptions. Confirm all rules are active and proceed to the next step.
- Select a sensitivity label to auto-apply on the Choose a label to auto-apply page.
- For Exchange policies, configure optional settings on the Additional settings for email page, such as automatic replacement of existing labels and applying encryption to incoming emails from outside the organization.
- On the Decide on policy testing page, select Run policy in simulation mode if you're ready to run the auto-labeling policy now, in simulation mode. Then decide whether to automatically turn on the policy if it isn't edited for seven days.
 If you're not ready to run simulation, select Leave policy turned off.
If you're not ready to run simulation, select Leave policy turned off. - Review your auto-labeling policy's settings on the Summary page, make any necessary adjustments, and finalize the configuration.
Create auto-labeling policies interactive guide
Use the interactive guide for a walkthrough on creating auto-labeling policies.
Knowledge check
Select the best response to the question.