Windows Identity Foundation (WIF) By Example Part I – How To Get Started.
This post reflects on the steps I needed to perform to create my first Windows Identity Foundation (WIF) application from zero to Hello World. It can serve as a bootstrap for starting developing Claims-Aware ASP.NET application using Windows Identity Foundation (WIF).
This post quickly goes through preparing the development environment for using Windows Identity Foundation (WIF) and it walks through creating basic simple Claims-Aware web site.
Summary of steps:
- Step 1 – Prepare Development Environment
- Step 2 – Configure IIS7 to use SSL
- Step 3 – Create Claims-Enabled Web Site
- Step 4 - Add local STS (Security Token Service)
- Step 5 – Configure IIS to load User Profile
- Step 6 – Test Your Work
Rest of the post is detailed explanation for each step followed by the resources in the end.
Step 1 – Prepare Development Environment
- Have VS2010 installed.
- Use Web Platform Installer available here to configure your dev machine. Tick all options on for Web Server and for Frameworks and Runtimes unless it completely sounds off like CGI.
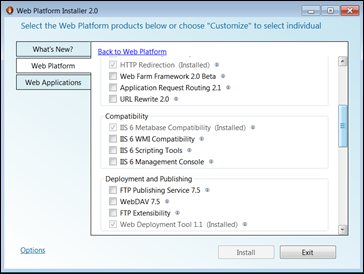
- Make sure to configure IIS 6 Metabase and IIS 6 Configuration compatibility otherwise you will hit the following error message when trying to create a web site in Visual Studio 2010 when working directly against IIS vs. File System.
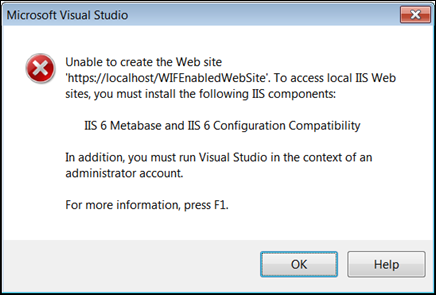
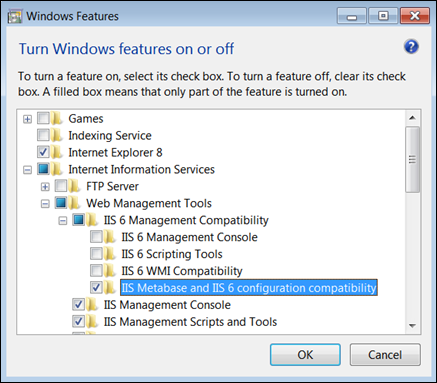
- To configure IIS 6 Metabase and IIS 6 Configuration Compatibility use either Web Platform Installer or go to Programs and Features. Expand Internet information Services and tick the option on, then press OK.
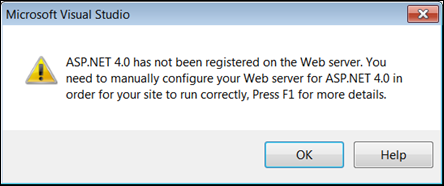
- Make sure IIS is configured to use ASP.NET 4.0 otherwise you will receive the follow error message:
ASP.NET 4.0 has not been registered on the Web server. You need to manually configure your Web server for ASP.NET 4.0 in order for your site to run correctly, Press F1 for more details.
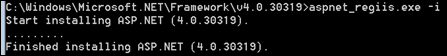
To configure IIS7 to use ASP.NET 4.0 follow these steps:
- Open command prompt under Administrative privileges.
- Navigate to this location C:\Windows\Microsoft.NET\Framework\v4.0.30319.
- Locate aspnet_regiis.exe file.
- Run the utility with –i switch to register ASP.NET 4.0 with IIS7
- Install WIF runtime https://www.microsoft.com/downloads/details.aspx?FamilyID=eb9c345f-e830-40b8-a5fe-ae7a864c4d76&displaylang=en
List supported OS’s – https://support.microsoft.com/?kbid=974405
Package name |
Supported operating system |
Platform |
Download file size |
Windows6.1-KB974405-x64.msu |
Windows 7 and Windows Server 2008 R2 |
x64 |
965 KB |
Windows6.1-KB974405-x86.msu |
Windows 7 |
x86 |
858 KB |
Windows6.0-KB974405-x64.msu |
Windows Vista SP2 and Windows Server 2008 SP2 |
x64 |
969 KB |
Windows6.0-KB974405-x86.msu |
Windows Vista SP2 and Windows Server 2008 SP2 |
x86 |
861 KB |
Windows5.2-KB974405-x64.exe |
Windows Server 2003 SP2 |
x64 |
1.2 MB |
Windows5.2-KB974405-x86.exe |
Windows Server 2003 SP2 |
x86 |
1.2 MB |
- Install WIF SDK https://www.microsoft.com/downloads/details.aspx?FamilyID=c148b2df-c7af-46bb-9162-2c9422208504&displaylang=en
Step 2 – Configure IIS7 to use SSL
Follow instructions on how to configure IIS7 to use SSL located here: How to Set Up SSL on IIS 7. I skipped directly to Using IIS Manager part.
Step 3 – Create Claims-Enabled Web Site
- In Visual Studio choose File->New Web Site.
- In the dialog choose Claims-Aware ASP.NET Web Site, give it a name and press OK.
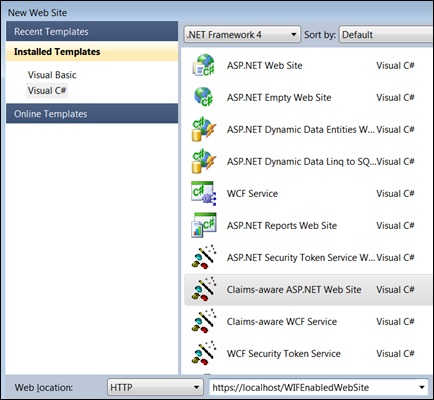
- You have created a Web Site configured to use Windows Identity Foundation. Explore web.config, you should identify several config sections related to Windows Identity Foundation.
Step 4 - Add local STS (Security Token Service)
- In Solution Explorer right click the solution and choose “Add STS reference...”
- On the Welcome to the Federation Utility wizard page click Next.
- On the Security Toke Service page choose “Create a new STS project in current solution” and click Next.
- Click Finish on Summary page.
- You should see success message – “Federation Utility completed successfully.”
- New project should be created with the same name and _STS suffix.
- Original Solution’s web.config should be updated with several more changes – explore it.
Step 5 – Configure IIS App Pool to load user profile
Make sure that the application pool is configured to load user profile. From the response to ADFS 2.0 SSO The data protection operation was unsuccessful by Claudio Sanchez:
- Open your IIS Manager
- Find out what AppPool your application is using by selecting your App, right-click on it, and Select Manage Application -> Advanced Settings.
- After that, on the top left hand side, select Applications Pools, and go ahead and select the App Pool used by your app.
- Right-click on it, and select Advanced Settings, Go to the Process Model Section and Find the "Load User Profile" Option and set it to true.
Step 6 – Test Your Work
- Navigate to the Web Site’s default.aspx page by right clicking on it and the choosing View In Browser option. In my case it is https://localhost/WIFEnabledWebSite/Default.aspx
- Notice you should be redirected for the authentication at STS web site https://localhost/WIFEnabledWebSite_STS:
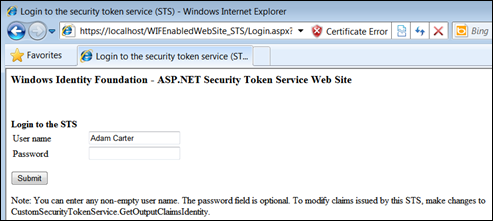
- Click Submit Button to imitate authentication process.
- You should be redirected back to the Web Site, in my case WIFEnabledWebSite:

More Info
- Identity Developer Training Kit
- A Guide to Claims-Based Identity and Access Control – Code Samples
- A Guide to Claims-Based Identity and Access Control — Book Download
Related Books
- Developing More-Secure Microsoft ASP.NET 2.0 Applications (Pro Developer)
- Ultra-Fast ASP.NET: Build Ultra-Fast and Ultra-Scalable web sites using ASP.NET and SQL Server
- Advanced .NET Debugging
- Debugging Microsoft .NET 2.0 Applications
Comments
- Anonymous
September 03, 2010
Great article Alik...it really takes out guess work and reduces setup and rampup time for WIF. - Anonymous
September 03, 2010
Thank you, Piyush!