Creating Workflow Manager farm using Domain CA Certificates results in "Invalid provider type specified"
When using PowerShell to create a Workflow Manager farm using Domain CA generated certificates with Cryptography Next Generation (CNG) keys you may receive one or more of the following error messages. The error message will depend on whether you are running Add-WFHost or New-SBFarm.
- System.Security.Cryptography.CryptographicException: Invalid provider type specified. (Add-WFHost)
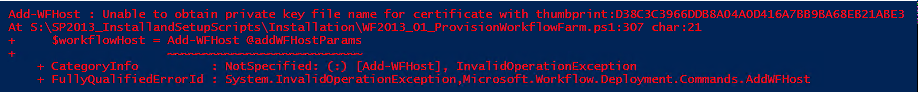
- Unable to obtain private key file name for certificate with thumbprint:<THUMBPRINT> (Add-WFHost)
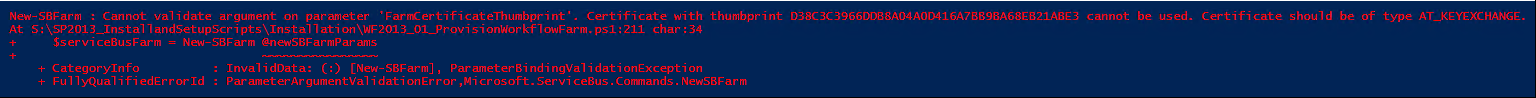
- Cannot validate argument on parameter 'FarmCertificateThumbprint'. Certificate with thumbprint <THUMBPRINT> cannot be used. Certificate should be of type AT_KEYEXCHANGE. (New-SBFarm)
Error Message #1: System.Security.Cryptography.CryptographicException: Invalid provider type specified.
When this error occurs an event with ID 702 is also logged to the Worfklow Manager admin logs in Event Manager (Applications and Services Logs > Microsoft-Workflow > Admin). This event shows the call stack of the error and we can see that it originates during cryptography operations, specifically with trying to get the certificate private key using the X509Certificate2 class.
Log Name: Microsoft-Workflow/Admin
Source: Microsoft-Workflow
Date: 4/11/2016 10:53:57 AM
Event ID: 702
Task Category: (64832)
Level: Error
Keywords:
User: Contoso\WFMSetup
Computer: SP2016WFM.Contoso.com
Description:
System.Security.Cryptography.CryptographicException: Invalid provider type specified.at System.Security.Cryptography.Utils.CreateProvHandle(CspParameters parameters, Boolean randomKeyContainer)
at System.Security.Cryptography.Utils.GetKeyPairHelper(CspAlgorithmType keyType, CspParameters parameters, Boolean randomKeyContainer, Int32 dwKeySize, SafeProvHandle& safeProvHandle, SafeKeyHandle& safeKeyHandle)
at System.Security.Cryptography.RSACryptoServiceProvider.GetKeyPair()
at System.Security.Cryptography.X509Certificates.X509Certificate2.get_PrivateKey()
at Microsoft.Workflow.Common.EncryptionHelper.DecryptStringWithCertificate(X509Certificate2 encryptionCertificate, String encryptedText)
at Microsoft.Workflow.Deployment.Commands.AddWFHost.ProcessRecordImplementation()
at Microsoft.Workflow.Deployment.Commands.WorkflowBaseCmdlet.ProcessRecord()
Error Message #2: Unable to obtain private key file name for certificate with thumbprint: This PowerShell error is a bit clearer that the error is related to certificate private key operations
Log Name: Microsoft-Workflow/Admin
Source: Microsoft-Workflow
Date: 4/11/2016 11:21:16 AM
Event ID: 702
Task Category: (64832)
Level: Error
Keywords:
User: Contoso\WFMSetup
Computer: SP2016WFM.Contoso.com
Description:
System.InvalidOperationException: Unable to obtain private key file name for certificate with thumbprint:D38C3C3966DDB8A04A0D416A7BB9BA68EB21ABE3
at Microsoft.ServiceBus.Commands.Common.Utility.GetKeyFilePath(StoreName storeName, StoreLocation storeLocation, String key)
at Microsoft.ServiceBus.Commands.Common.CertificateHelper.GrantCertificatePermission(String thumbprint, IdentityReference certUser)
at Microsoft.Workflow.Deployment.Commands.AddWFHost.ProcessRecordImplementation()
at Microsoft.Workflow.Deployment.Commands.WorkflowBaseCmdlet.ProcessRecord()
Error Message #3: Cannot validate argument on parameter 'FarmCertificateThumbprint'. Certificate with thumbprint <THUMBPRINT> cannot be used. Certificate should be of type AT_KEYEXCHANGE.
The third error message provides even more specific information and actually tells us what kind of certificate we need to use for Service Bus (and Workflow Manger). This requirement is documented on the Workflow Manager System Requirements page under “General Certificate Requirements”
What is KeySPec and AT_KeyExchange?
The KeySpec property specifies or retrieves a value that identifies whether a private key can be used for signing, or encryption, or both (source). AT_KeyExchange is one of the KeySpecs available and indicates that the key can be used for encryption or key exchange. The KeySpec property AT_KeyExchange is only available when using Legacy Cryptographic Service Providers
A certificate template may be configured to use the Legacy Cryptography Service Providers that are available by default, or it may be configured to use the Cryptography API: Next Generation (CNG) Key storage Provider (KSP). The latter CNG option is not supported for Workflow Manager or Service Bus.
[caption id="attachment_65" align="alignnone" width="419"]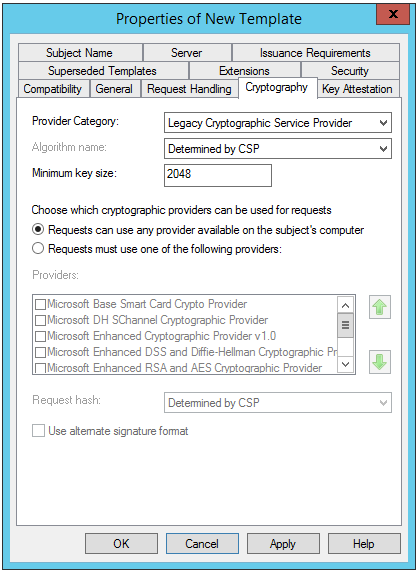 Certificate template using legacy CSP[/caption]
Certificate template using legacy CSP[/caption]
[caption id="attachment_55" align="alignnone" width="422"]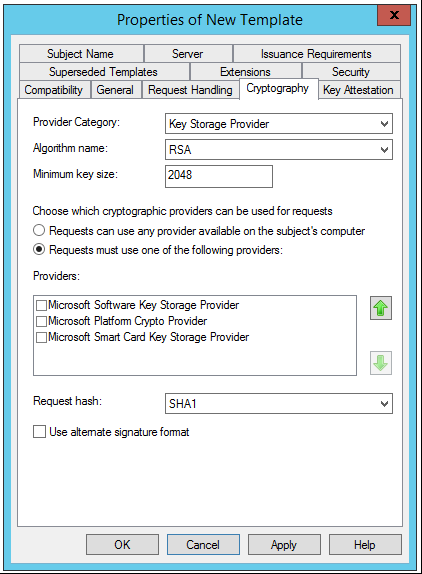 Certificate Template using CNG Key Storage Provider[/caption]
Certificate Template using CNG Key Storage Provider[/caption]
Recommendation
If using Domain CA generated certificates for Workflow Manager and Service Bus ensure they align with the certificate requirements documented here:
If you select an existing certificate, you must make sure that the following conditions are met.
- The certificate must have a subject name, a subject alternative name, and both the private and public key.
- The certificate is also installed in the personal store of all computers in the farm or any computer that intends to join the farm.
- The certificate must be valid with respect to:
- The start date.
- The end date.
- The trust chain.
- The certificate must have AT_KeyExchange set.
- The certificate can be used as a server certificate.
- The corresponding CRL list for the signing authority must be present.
https://msdn.microsoft.com/en-us/library/jj193451(v=azure.10).aspx
Additional Resources
Migrating a Certification Authority Key from a Cryptographic Service Provider (CSP) to a Key Storage Provider (KSP)
https://technet.microsoft.com/en-us/library/dn771627.aspx
CNG Key Storage Providers
https://msdn.microsoft.com/en-us/library/windows/desktop/bb931355(v=vs.85).aspx
CNG Cryptographic Algorithm Providers
https://msdn.microsoft.com/en-us/library/windows/desktop/bb931354(v=vs.85).aspx
CryptoAPI Cryptographic Service Providers
https://msdn.microsoft.com/en-us/library/windows/desktop/bb931357(v=vs.85).aspx
"Invalid provider type specified" error when accessing X509Certificate2.PrivateKey on CNG certificates
https://blogs.msdn.microsoft.com/alejacma/2009/12/22/invalid-provider-type-specified-error-when-accessing-x509certificate2-privatekey-on-cng-certificates/
IX509PrivateKey::KeySpec property
https://msdn.microsoft.com/en-us/library/windows/desktop/aa379020(v=vs.85).aspx
Verifying the Key Specification of a Given Certificate
https://social.technet.microsoft.com/wiki/contents/articles/11483.credential-roaming.aspx#Verifying_the_Key_Specification_of_a_Given_Certificate
Comments
- Anonymous
November 04, 2016
The comment has been removed