Automatic Bitlocker on Windows 10 during Azure AD Join
Update June 2017 - please read my post here for a workaround on all devices.
There are a lot of myths on how to automatically trigger Bitlocker on an Azure AD Joined Windows 10 device, let’s hope this post will get you some answers.
Windows 10 will automatically encrypt the local drive when joining an InstantGo capable device to Azure Active Directory (AAD). An AAD Join can either done during the “Out Of Box Experience” (OOBE) or when Window is installed by going to the “About” screen, here you have the option to Azure AD Join the device.
As an admin you can configure Azure AD in such a way that the device is automatically registered in your Mobile Device Management solution.
Important note: You cannot use Microsoft Intune (or any other MDM) to specify a policy and force Bitlocker on a Windows 10 PC. This is done automatically during an Azure AD Join.
What does “InstantGo capable device” mean?
InstantGo (formerly known as Connected Standby) is a very low power state that some devices support. It’s very like your mobile phone, it’s almost switched off but still can receive text messages, e-mails and switch to a different power state when receiving phone calls.
A growing list of devices support InstantGo, you can manually check if your device supports this powerstate as follows:
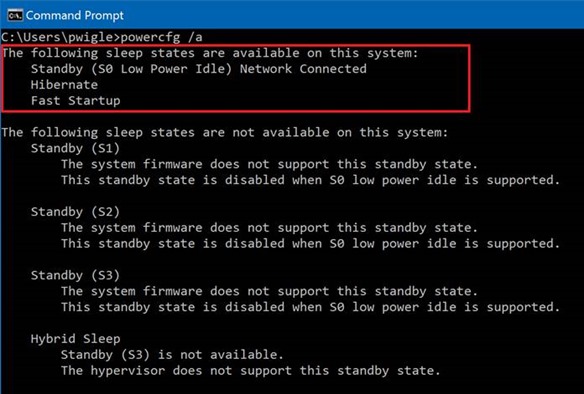
- Open a command prompt
- Type “powercfg /a”
Devices that have InstantGo support will return “Network Connected”:
If your device does not support InstantGo (and therefore: no automatic Bitlocker during Azure AD Join) you will get something similar to this: 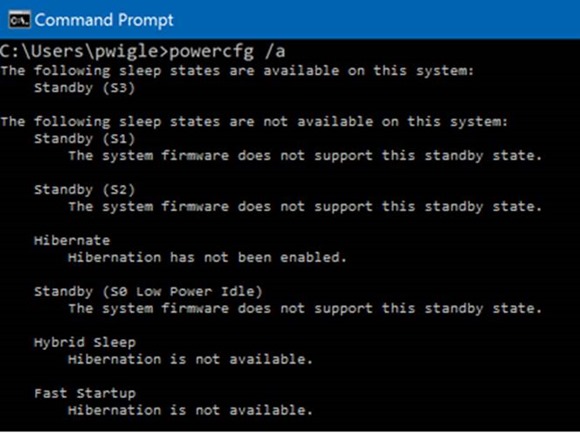
Keep in mind that this also applies to Virtual Machines. Automatic Bitlocker during Azure AD Join requires physical InstantGo Capable devices.
Where do I find the recovery key?
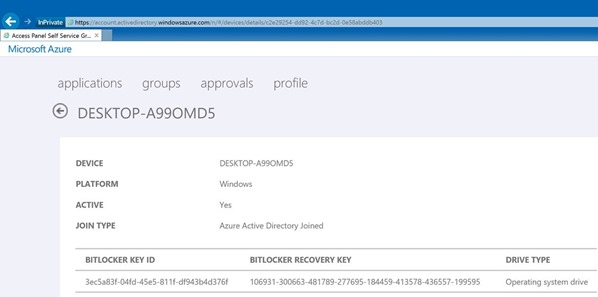
Users can retrieve their recovery key by going to https://myapps.microsoft.com, select Devices and select the device for which they would like to get the recovery key:
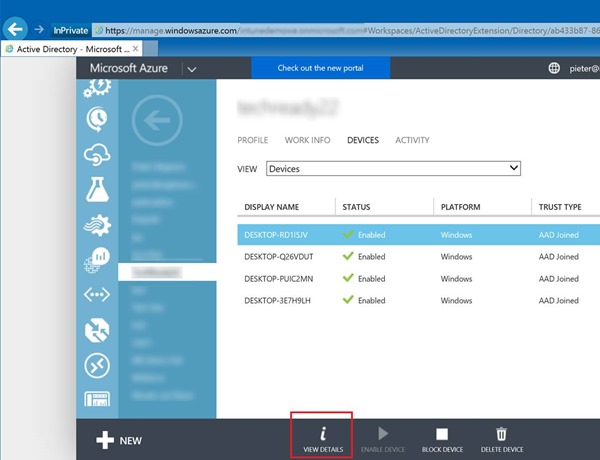
As an Azure tenant admin you can find the recovery keys for your users by going to https://manage.windowsazure.com, browse to your Active Directory, go to the Users tab and select the user who enrolled a specific device. Browse to Devices and change the dropdown list to view Devices.
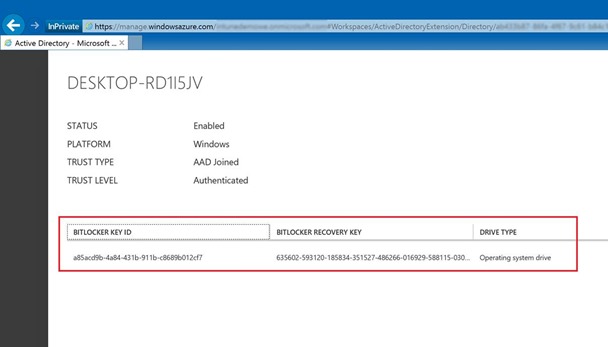
Find the device for which you would like to have the recovery key and hit Details.
“I have InstantGo capable devices but Bitlocker is not enabled automatically during an Azure AD Join”
If you are sure your device is InstantGo capable (e.g. Surface Pro 3 or Surface Pro 4) it could be that the image you are using has Automatic Bitlocker during AAD Join disabled – this is controlled by a registry key.
Update October 2016: The surface recovery image has been updated to fix this issue. Recently we have seen this issue with the Surface Pro 4 Recovery Images. Until the Recovery images are updated you can work around this by either:
Use a vanilla Windows 10 (1511) ISO or media, install Windows 10, perform the AAD Join. Either inject the Surface Pro drivers into the image in advance or install the drivers manually afterwards.
OR
During the Out Of Box Experience (OOBE) hit SHIFT-F10 on your keyboard, this will bring up a command prompt. Fire up REGEDIT and browse to
HKLM\System\CurrentControlSet\Control\Bitlocker\
Make sure that “PreventDeviceEncryption” is set to “0” 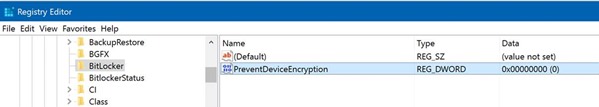
If you liked this post - please consider leaving a reply.
Comments
- Anonymous
March 14, 2016
Nice post, thank you very much. - Anonymous
March 19, 2016
It is a very cool post - do you know if it will change in the feature that is only devices with InstantGo support that are bitlocker encrypted?? - Anonymous
March 22, 2016
So devices that don't support InstantGo, can you still manually encrypt? I haven't gone through it (yet) but there is an option to manually enable bitlocker and get an option to backup key to the Cloud. If so, is there a way to run a script to encrypt after the AAD join? - Anonymous
March 22, 2016
Per Larsen: I can't disclose anything on that unfortunately.
William: Yes, you can still manually enable Bitlocker and save the recovery key to AAD. I haven't seen any script to do this and I'm not sure if it's possible at all to automate this yourself. Intune executes MSI's in the SYSTEM context so that adds another layer of complexity from a impersonation perspective. - Anonymous
March 22, 2016
Thanks Pieter. I have some automation that comes down via Intune as System, reboots the machine and starts the true automation at the next logon of the user so getting it scripted for the user isn't an issue. Hoping for a future update that allows for a scripted process. - Anonymous
March 23, 2016
The comment has been removed - Anonymous
March 24, 2016
Pieter: I have done some work on this and was going to create the MSI package. The process was to create a batch file that would do the following: -
Pre-Requisites: -
Create a OneDrive account for the admins to control
- MSI Container deployed through InTune
- Run a VBScript to open up internet explorer and login to the OneDrive with the account that holds the share
This is required to get the authentication setup for the OneDrive area
- Run a Net Use command against the HTTPS link and map the OneDrive Business to a local drive
- Run the Manage-bde to run Bitlocker and place the key onto the OneDrive Business drive that is mapped
- Run Net /Delete to close the mapping
- Run a VBScript to shutdown internet explorer
- Run commands to remove the VB Script files from the device
- Shutdown the script
- MSI Container requests a forced reboot of the machine
The whole process would save a BEX file to the One Drive that the admins could use to recover the machine.
Problems faced was only to do with the inconsistency of the drive mapping. It would work sometimes, but it was to erratic. The rest of the script works fine.
There are applications that will allow the mounting of the OneDrive Business more consistent, but requires licensing and installation.
The process I was going to use was going to be limited to a test group and I do not recommend for a large workforce.
I am not sure if that was what you were thinking of, but if it could just be a little more consistent in regards to the mapping of the drive that would have made it an alternative for non-S0 state devices.
The batch file runs at user level. - Anonymous
March 24, 2016
The comment has been removed- Anonymous
September 19, 2016
hmm, I am seriously considering writing up a script wrapped in an MSI that enables-bitlocker and then saves it to a secure sharepoint list or such....a simple workflow would suffice, and most who run into this lack of functionality in manage-bde or backup-bitlocker* will have Sharepoint Online... - Anonymous
September 28, 2016
Pieter Wigleven, any news regarding a workaround for backing up keys to Azure AD with script/feature/woarkaround?- Anonymous
October 18, 2016
No news yet, I will share info asap.- Anonymous
June 30, 2017
Available in windows 10 - 1703. Write directly to Azure and you can manage keys in Azure AD: # http://blog.coretech.dk/mas/how-to-manage-bitlocker-on-a-azure-ad-joined-windows-10-device-managed-by-intune/Enable-BitLocker -MountPoint "C:" -EncryptionMethod XtsAes256 -SkipHardwareTest -RecoveryPasswordProtector$BLV = Get-BitLockerVolume -MountPoint "C:" | select *BackupToAAD-BitLockerKeyProtector -MountPoint "C:" -KeyProtectorId $BLV.KeyProtector[1].KeyProtectorId
- Anonymous
- Anonymous
- Anonymous
- Anonymous
March 25, 2016
That is correct for the Manage-dbe is that we have to have a drive mapped and it has to be an alternative drive from the drive being encrypted.
The reason behind the OneDrive Business is that we wanted to keep to the nature of InTune by allowing the registration and activation of the machine to be done off-prem.
I like the idea about the ramdisk and using that to then upload the file to say an SFTP location.
I have access to an SFTP service and I can check my script and see if I can modify it to move the file from the Ramdrive on the SFTP service.
The only concern I have is that any script, service or applciaiton we have deployed from the MSI container needs to be removed, stopped and cleared so that we maintain security on the device.
I like the idea of capturing the content and look at placing this into the AD if possible. There will be some steps between the file and the AD.
I am not very clued up on that part of the process. I am interested in looking into this. I would have to place this into a private project as workload has now pulled me into another direction. - Anonymous
March 30, 2016
In testing we have done .... manually running Bitlocker from the control panel will allow a non-InstantGo device to store the recovery key to Azure AD.
would certainly be nice if Microsoft provided a flag to manage-bde or to the bitlocker powershell cmdlet to store the key to Azure AD so this can be automated. - Anonymous
April 02, 2016
The comment has been removed - Anonymous
May 18, 2016
Is there a way to export bitlocker recovery key for Azure AD joined clients via powershell? Do we have any module available? - Anonymous
June 21, 2016
The comment has been removed - Anonymous
July 11, 2016
It would be really nice if we can store the encryption key with powershell or manage-bde in AzureAD so we can easily automate it... - Anonymous
August 16, 2016
Any details about how to Encrypt a Boot Camp partition on a 2015 Macbook Pro Retina would be greatly appreciated - Anonymous
September 13, 2016
Hi. I have been looking into this with the latest Windows 10 build and a reset Surface Pro 4, it seems there now is a now key available here. "PreventDeviceEncryptionForAzureADJoinedDevices" which is set to "0" by default. Maybe this is the fix for this and that updated Windows 10 Aniversary Surface Pro 4 devices will actually auto enable Bitlocker now. - Anonymous
September 19, 2016
Thanks a lot for your post, especially for last part about recovert images, you spare me a lot of time! - Anonymous
September 28, 2016
Is there ANY ways to automate storing Bitlocker keys to Azure AD on a Windows 10 device , after adding it to AZURE AD (native)Any script, registry etc than can make this easier than let the endusers encrypt the device and when asket to store keys, then choos Azure AD?- Anonymous
December 15, 2016
The comment has been removed- Anonymous
January 11, 2017
Agreed. All we need is a Policy CSP for MDM.. :) :)
- Anonymous
- Anonymous
January 12, 2017
Herman, I have found a post that might help.Please check the powershell gallery https://www.powershellgallery.com/packages/Enable-AADBitlocker/0.0.0.2/Content/Enable-AADBitlocker.ps1This might help. To deploy it with Intune, make an EXE => http://126kr.com/article/90t7z4t57b6
- Anonymous
- Anonymous
December 20, 2016
I have created a script that does the encryption and AAD key storage. Haven't tested it yet through Intune. Link: http://www.jvm-net.com/2016/12/20/store-bitlocker-recovery-keys-in-aad/ - Anonymous
January 11, 2017
Just wanted to put it out there that I love your posts and they are by far the best on MDM with Intune/EMS/AzureAD/Windows10. Very practical and easy to follow. Thank you! - Anonymous
January 25, 2017
Hi guys,Need some help here as I'm trying to enable automatically Bitlocker after Azure AD Join, and is not going at all. All the prerequisites are in place like:- win 10 (1607 EN);- TPM 2.0;- InstantGo (Standby Connected);- Microsoft Account (Azure subscription);- no prevention is set;- manually works fine;And I searched in the last two days all the info on the Internet related to Bitlocker and Azure AD Join, nothing helped.Thanks in advance. Any idea would be appreciated.NB- Anonymous
January 27, 2017
Hello,Has anyone activated this automatically when Azure AD join subscription was added? I have a DELL 7275 and I'm not sure if PIN is required in this case (when machine was added in Azure AD), doing manually activation for Bitlocker seems to work fine (no PIN though is requested). So when I tried manually to set also a PIN is giving me that this PC DELL 7275 has no option for keyboard in PRE-BOOT phase where you need to add the PIN code. Thanks,NB
- Anonymous
- Anonymous
January 27, 2017
Device is "InstantGo Capable" and "powercfg /a" returns "Standby (S0 Low Power Idle) Network Connected". Also "PreventDeviceEncryption" registry key is set to “0”. I can manually right-click on C drive and turn on BitLocker and store keys in AADP and it works fine, but this supposed to happen automatically, right? - Anonymous
April 04, 2017
You say "you can find the recovery keys for your users by going to https://manage.windowsazure.com, browse to your Active Directory, go to the Users tab and select the user who enrolled a specific device"If we are automatically enrolling devices in AAD as per GPO instructions here:https://docs.microsoft.com/en-us/azure/active-directory/active-directory-conditional-access-automatic-device-registration-setupAnd then enabling bitlocker via script under an admin context (non-InstantGo devices)eg https://www.powershellgallery.com/packages/Enable-AADBitlocker/0.0.0.2/DisplayScriptThen a "user" hasn't done any of this? I am worried that the device won't shows in the portal, hence we can't get the key?Further, the FAQ from the link aboveWindows 10 devices that are domain-joined with automatic device registration do not show up under the USER info. You need to use PowerShell to see all deviceshttps://docs.microsoft.com/en-us/azure/active-directory/active-directory-device-registration-faqSo the question is under Auto-enrollment and manual/scripted Bitlocker enablement, how do we see the bitllocker keys in AAD GUI?In my scenario I need to perform this on behalf of the users and I don't know their creds.- Anonymous
June 03, 2017
very interesting scenario. I second a lot of your questions since one scenario is that the computer is locked and the user don't have knowledge or possibility to recover the key and therefor a must for support to be able to access bitlocker key. furthermore, it would be very practical to be able to search for the bitlocker key, as you can do with both MBAM and regular AD joined bitlocker scenarios.Must say it is chocking to se the lack of understanding for AAD scenarios. where the enduser is supposed to know that much about the settings in the background.
- Anonymous