Identity and Rights Management in CSP model
Today I will describe how identity works in CSP model, because it is not obvious for CSP Partners.
The main part of identity process in CSP is based on Azure Active Directory. There are 2 types of directories in CSP - Partner directory and Customer directory. Each CSP Partner authenticates on Partner Center portal using its Azure AD directory. For example, it can be CSPPartner.onmicrosoft.com. Every Azure AD directory name must be unique, it consists of the tenant name ("CSPPartner" in my example) and onmicrosoft.com suffix.
Partner employees logon to Partner Center portal using their Azure AD user account. It can be john@csppartner.onmicrosoft.com or just john@csppartnerdomain.com (to do so Partner should add an existing custom domain to his Azure AD directory first and change user's domain suffix).
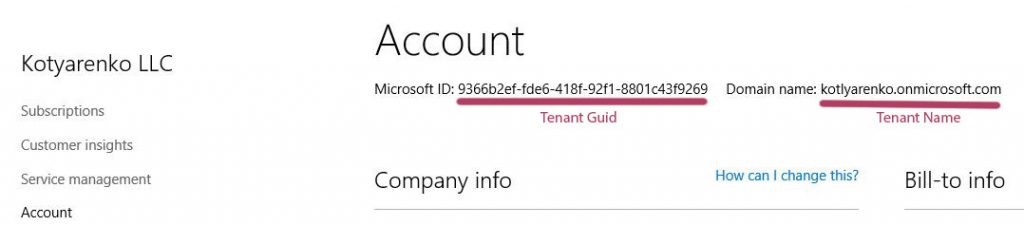
When Partner creates a new Customer on Partner Center portal, a new Office 365 tenant with a new Azure AD directory is created. Is my example it will be "CSP Customer LLC" with CSPCustomer.onmicrosoft.com domain. There are 2 important unique values for the tenant, that you will need to remember (and don't confuse them) - Tenant GUID and Tenant Name. You can check them on Account page for the specified Customer.
Also new user with a login admin@CSPCustomer.onmicrosoft.com is automatically created and being assigned Global Admin rights in this directory. Its password is shown as plain text at the moment of Customer creation, but it can be changed in the future. Also there is a way to link an existing tenant with existing Azure AD to the CSP Partner account, but I won't touch this topic in details now.
This Office 365 tenant will have a CSP partner as a Managed Partner (DPOR) assigned. One Customer can have several Managed Partners assigned.
BTW, you can add 4 types of user accounts into Azure AD:
- Clout-based user account - created directly in this Azure AD (using old Azure Management Portal or Office 365 Admin Portal)
- Synced or Federated user account - account, created in on-premise Active Directory and synchronized/federated with Azure Active Directory using ADConnect (or legacy DirSync/ADSync)
- Microsoft Account (former LiveID)
- User accounts, added from another Azure AD. E.g. you can add user from Partner Azure AD to Customer's Azure AD.
To understand this in details, I recommend you to use 70-346 course.
So, Partner employees sign in to Partner Center, Office 365 Admin Portal, Azure Portal etc. using their Azure AD credentials. Customer admins sign in to Office 365 Admin Portal, Azure Portal etc. using their Azure AD credentials.
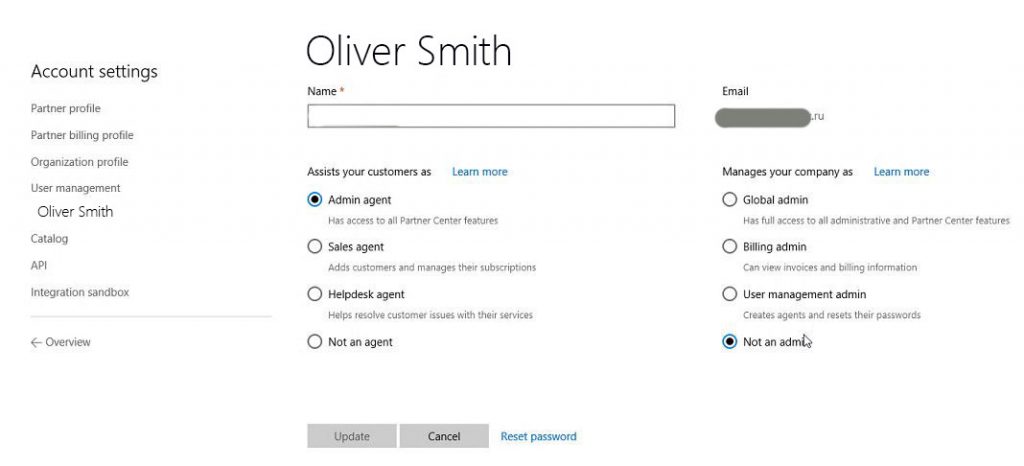
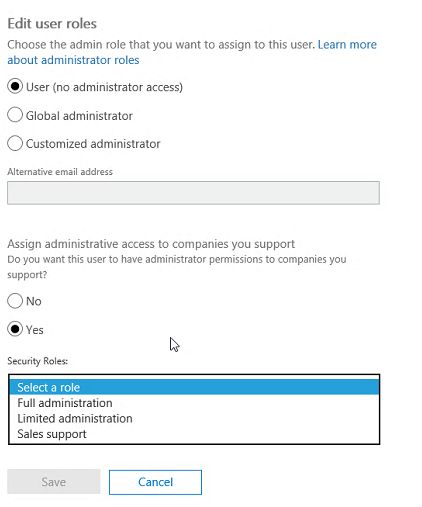
On Partner Center portal there are some capabilities to assign roles to partner users (or create new users in Partner directory with specified roles).
"Assists your customer" buttons set the role for Customer management, "Manages you company" buttons set the admin role inside Partner's Azure AD. These 2 switches are independent.
In "Manages you company" switch you can choose among 4 options:
- Leave user as a regular user (no rights to manage Partner's directory, but you'll still be able to assign this user some Customer management rights).
- Assign User Management Admin role to this user in Partner's directory
- Assign Billing Admin role to this user in Partner's directory
- Assign Global Admin role to this user in Partner's directory (super user)
Detailed admin role comparison is available here. If this user needs to manage user rights on Partner Center, choose Global Admin or User Management Admin role.
In "Assists your customer" switch you can choose among 4 options:
- Not an agent - no rights to create customers and manage their subscriptions and services. But if this user will have Global Admin or User Management admin rights, he will be able to logon to Partner Center or Office 365 Admin Portal and grant himself the required rights.
- Sales agent - user will be able to manage Customer subscriptions and billing, but won't be able to manage Customer's services (Office 365, Azure etc.)
- Helpdesk agent - user won't be able to manager Customer subscriptions, but will have Office 365 Limited Administration delegated admin rights (equals to Password Admin role)
- Admin Agent - user will be able to manage Customer subscription, will have Office 365 Full Administration delegated admin rights (equals to Global Admin role) and Owner rights for Customer Azure subscriptions (super user).
You can also configure these options for Partner user account on Office 365 Admin portal, it will also switch the selection on Partner Center.
Managing Office 365 tenants
To manage Office 365 for a customer, Partners engineers can use several ways:
- Go to Customer's page on Partner Center, click Service Management -> Office 365. Office 365 Admin portal for this tenant will be opened.
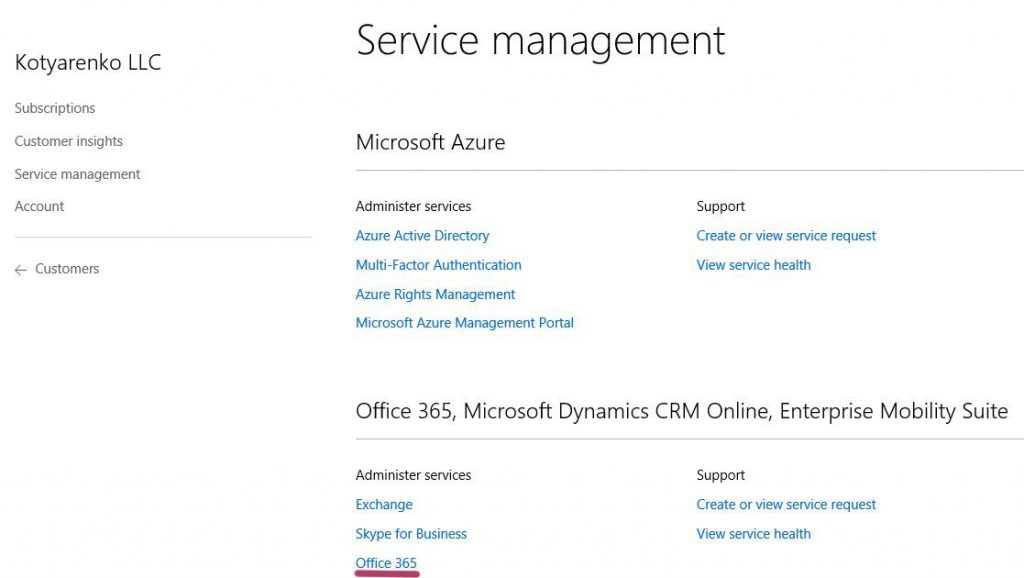
- Use Office 365 Partner Admin portal
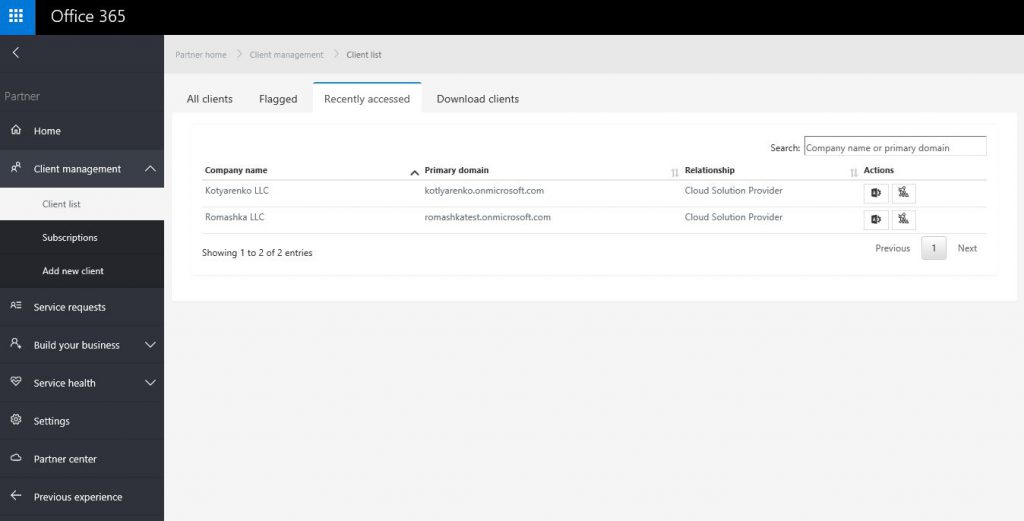
- Use URL https://portal.office.com/Partner/BeginClientSession.aspx?CTID=TENANDGUID&CSDEST=o365admincenter to open Office 365 Admin portal for that tenant directly.
- Use Office 365 PowerShell with Delegated Access Permissions, use Tenant GUID as TenantID.
In both ways Partner engineer must have a user account in Partner's directory with Helpdesk or Admin agent rights on Partner Center (equals to Limited or Full delegated administration rights in Partner's Office 365 tenant).
There is no granular control for different Customers, so management rights will be applied to all Customers, managed by this CSP Partner. It means that you can't assign Helpdesk/Admin agent administration rights only to some Customers - such partner person will be able to manage all Office 365 tenants, which are managed by this CSP Partner (but customer can delete this CSP Partner from the managed partner list to prohibit this).
Also there are no management capabilities based on Azure AD groups - you need to specify management roles directly for user accounts. This is a limitation of Office 365 Partner Management capabilities, not directly related to CSP. Details are here.
Customer admins can manage Office 365 by logging on Office 365 Admin portal using:
- Automatically created admin@tenantname.onmicrosoft.com user account, which has Global Admin rights
- Their Microsoft ID (former LiveID), which must be added manually to Customer's directory and assigned proper admin role.
- New user, created in Customer's directory with specified admin role. E.g. john@CSPCustomer.onmicrosoft.com with Global Admin role assigned.
Dynamics CRM and Intune in CSP use identity model similar to Office 365, so I won't dig into details here.
Managing Azure subscriptions
To manage Customer's Azure subscription, Partners engineers can use several ways:
- Go to Customer's page on Partner Center, click Service Management -> Microsoft Azure Management Portal. New Azure Portal will be opened.
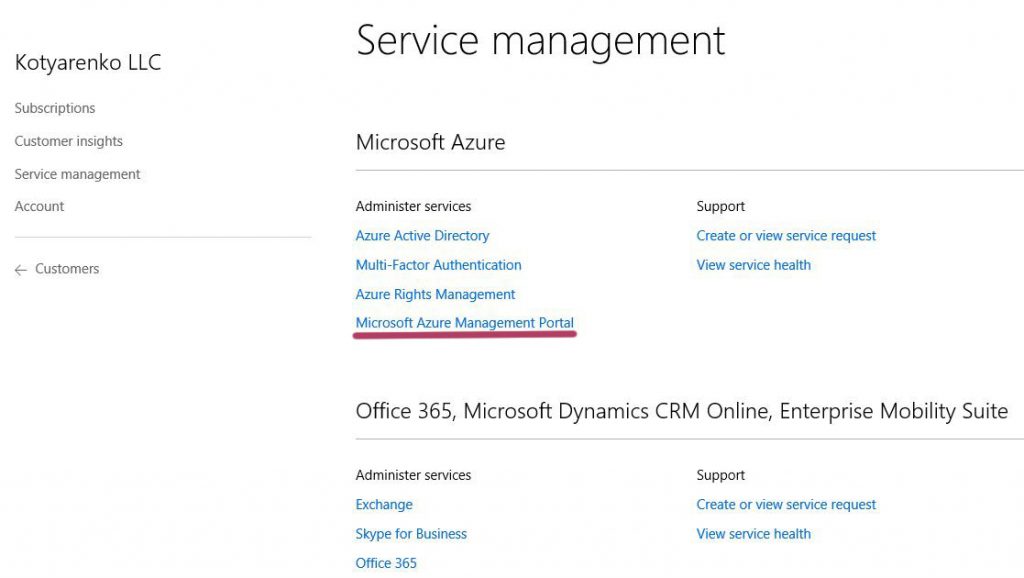
- Use URL https://portal.azure.com/TENANTNAME.onmicrosoft.com to open New Azure Portal in a context of this tenant
- Use PowerShell for Azure Resource Manager. I've showed how to use it here, use Tenant Name for $TenantID variable.
To do this, Partner engineer user account must have Admin Agent rights (Helpdesk Agent is not enough).
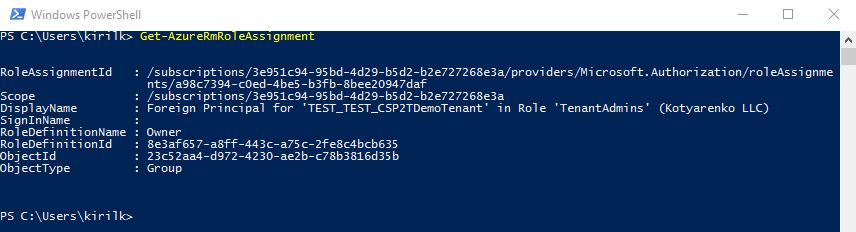
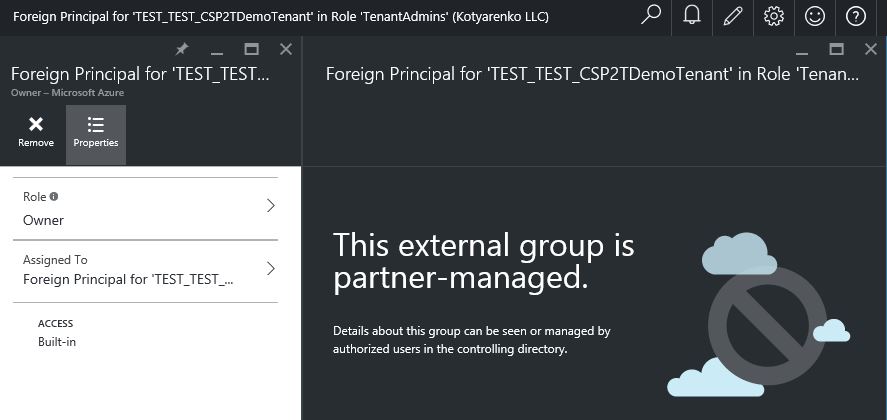
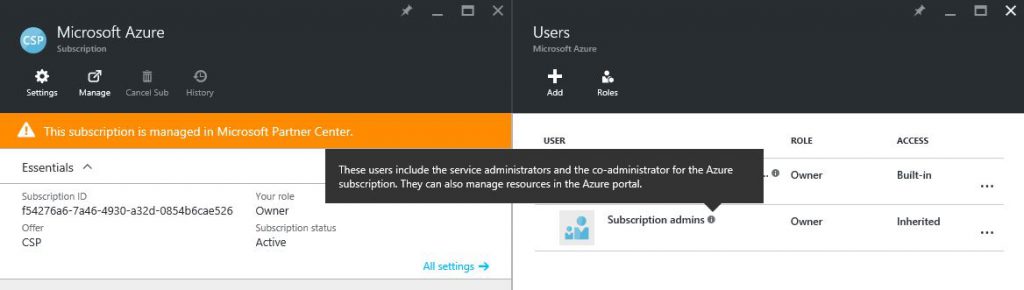
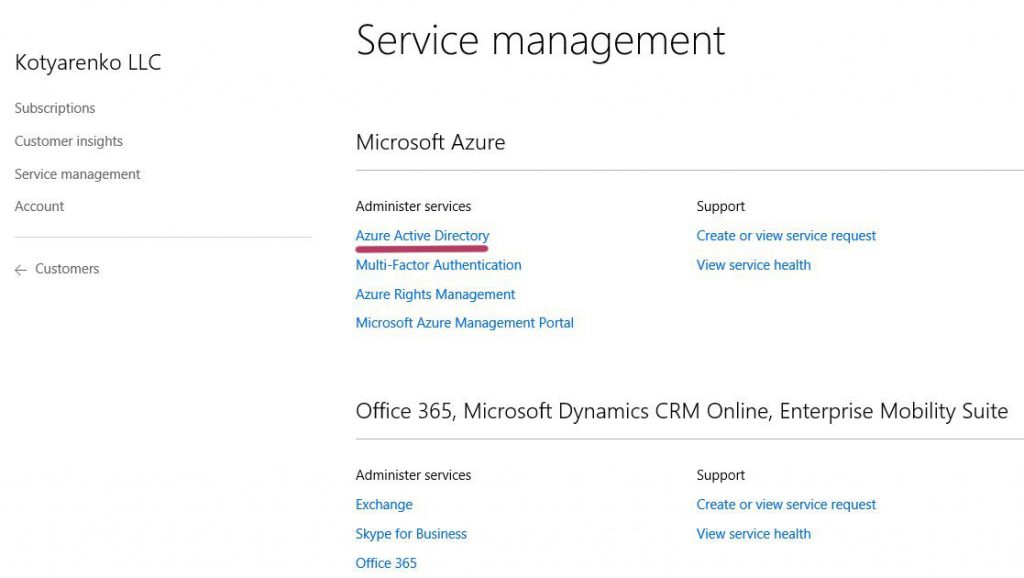
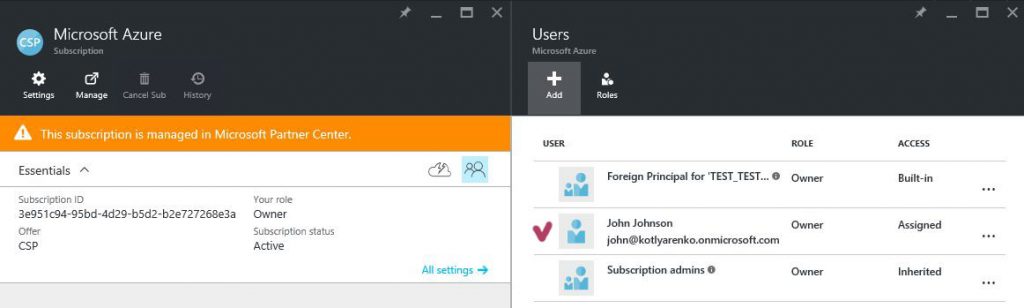
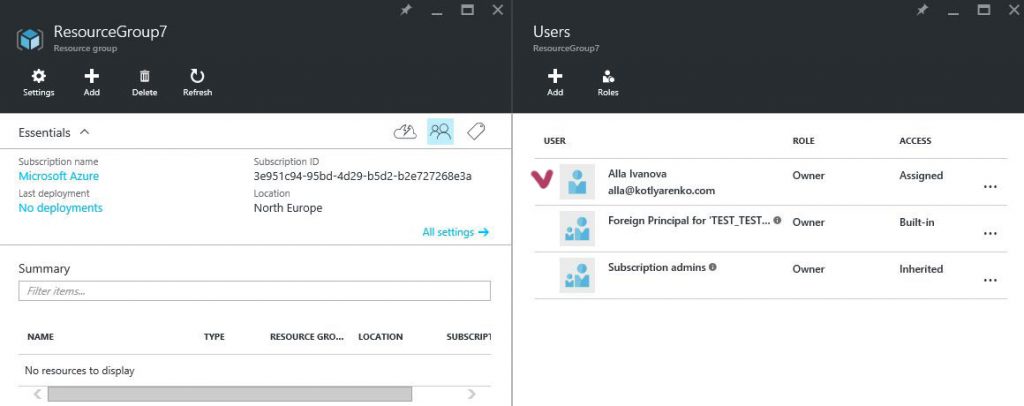
That's how it works… After assigning this role, such user will have Owner rights for all Azure subscriptions of all Customers. This is hardcoded in Azure CSP model - every Azure subscription in CSP has only 1 owner by default. This owner is a group called "Foreign Principal for 'CSPPartnerName' in role 'TenantAdmins' (CSPCustomer Directory)" (first screenshot - list of default customer's Azure Subscription owners), and this group has a role assigned - AdminAgents role in Partner's directory (second screenshot - list of available Roles in Partner's directory).
So every Partner's employee, that has Admin Agent rights assigned on Partner Center portal, will be added to AdminAgent Azure AD group in Partner's directory, which is added to a group "Foreign Principal for 'CSPPartnerName' in role 'TenantAdmins' (CSPCustomer Directory)" in Customer's directory, that has Owner rights for all Azure subscriptions of this Customer.
BTW - this group (Foreign Principal for 'CSPPartnerName' in role 'TenantAdmins' (CSPCustomer Directory) ) is not visible in Customer's Azure AD, so you won't see it if you'll get a list of all existing group in CustoSmer's directory. But you can see it if you'll open Azure Subscription rights blade. And this is the unique case when a group in Azure AD has a group in another Azure AD directory as a member.
Also you will see a group "Subscription Admins" on the portal, which also has Owner permissions for the subscription. But this is a legacy artifact, inherited from ASM - all Admins and Co-admins in ASM have Owner rights in ARM. It doesn't make sense for CSP, because there is no ASM here. If you'll try to manage this group, you'll see "Failed to get the list of users" error message. So just ignore this group.
By default, Azure subscriptions can be managed only by Partner's employees with Admin Agents rights. So even customer's admin account, that has Global Admin rights in Customer's Office 365 tenant (admin@tenantname.onmicrosoft.com), won't be able to manage Azure subscriptions by default. This is done because of the idea, that CSP Partner can manage customer's Azure subscription instead of a customer. CSP Partner can create VMs, configure Backup or ASR for the customer, and customer don't even need to access Azure Management portal in this case.
But I face customer-managed Azure subscriptions more frequently among my partners. In this case Customer admin want to access New Azure Portal to manage their Azure subscriptions. You can do it in several ways:
- Logon as Partner Admin Agent to New Azure Portal and assign another user Owner rights to the Azure Subscription.
- Logon as Partner Admin Agent to New Azure Portal, create a Resource Group and assign another user Owner rights to this Resource Group. In this case such user will me limited inside a Resource Group, but will be able to create any Azure resources inside this Resource Group (you can limit this by applying Resource Manager Policies).
After that Customer's admin will be to access New Azure Portal or use Azure Resource Manager PowerShell.
You can use other Roles instead of Owner for Customer's admins. You can use Contributor role if you don't want to allow any access management inside the Subscription, or you can use Reader role if you want to allow Customer admins to view Azure resources, but not to change them. Details about built-in roles in Azure Resource Manager are available here.
In Azure Resource Manager model you can assign rights only to users and groups, that exist in Customer's directory. You can add external users (Microsoft IDs, Azure AD users from other directories etc. - I've described it before) to Customer's directory and assign access to them. Or you can create a group in Customer's directory and add users to this group (internal or external), and that assign some access to this group. But you can't assign access to external group or you can't add external group to the group in Customer's directory.
Managing Customer's Azure AD
Azure AD management can be done through Old Azure Portal, through Office 365 Admin portal or using Azure AD PowerShell cmdlets (don't confuse them with Azure Resource Manager PowerShell cmdlets).
Office 365 Admin Portal capabilities regarding Azure AD management will be enough for the most customers - creating users and groups, managing membership of the groups, configure On-Premise AD integration etc. But some customers require additional configuration capabilities, which are available only on Old Azure Portal. There are 2 ways to allow customer to manage their Azure AD using Old Azure Portal:
- Customer creates a trial Azure account or register MSDN Azure account, after that customer adds an existing Azure AD to this Azure subscription. I've described it here.
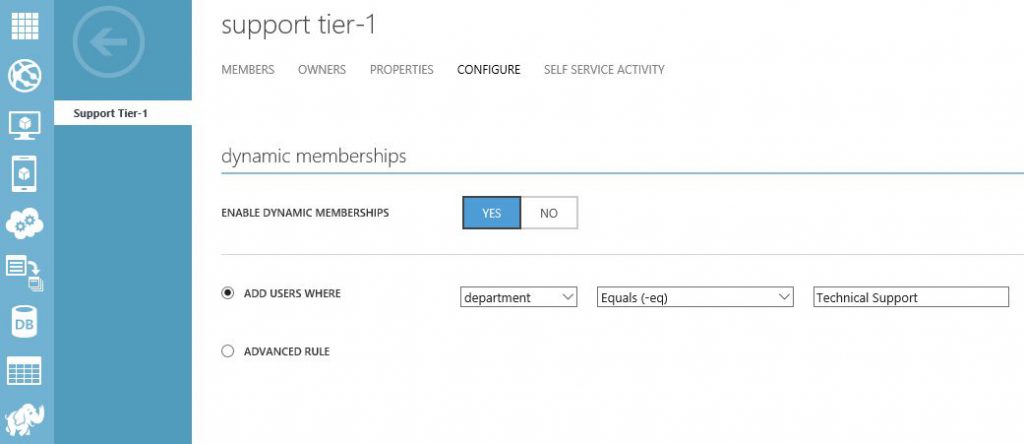
- Partners creates a license-based Subscription to any service, that includes Azure AD: Azure AD Basic, Azure AD Premium or EMS. It won't be free, but 1 license of Azure AD Basic is ~$1/month, so it's not a big deal. After that Customer will be able to access Old Azure Portal and manage his Azure AD using a special link on the Partner Center portal.
For example, Customer will be able to configure dynamic membership for Azure AD Groups:
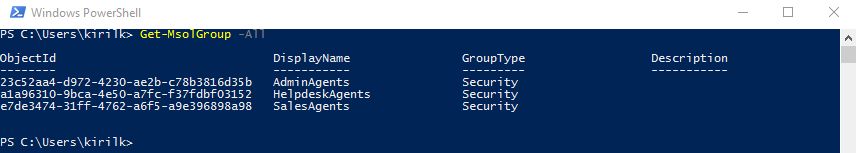
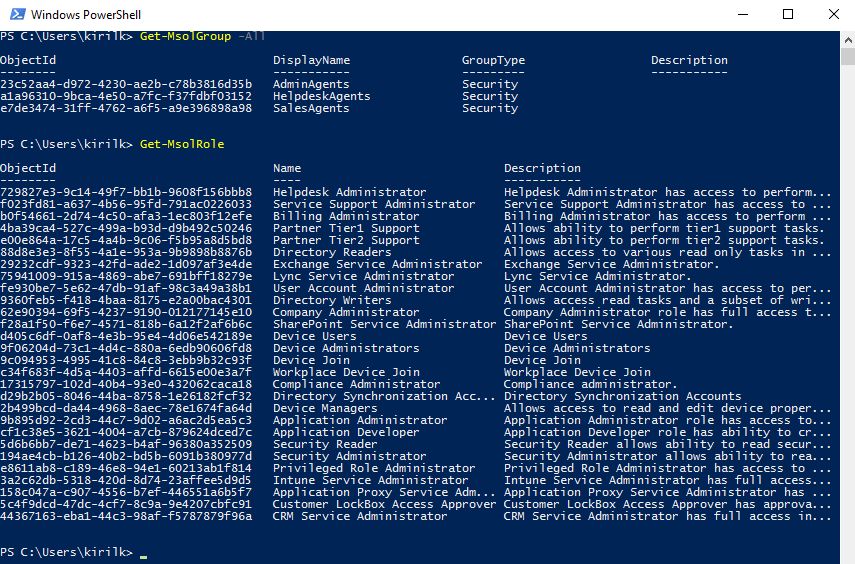
Partner can manage his Azure AD directory using Azure AD PowerShell and automate routine identity tasks. BTW - here is the list of groups and roles, created in Partner's directory after joining CSP Direct:
For example, to assign Admin Agent rights to a user, just assign him AdminAgents role in Partner's directory using PowerShell.
Granular access to different Customers
Some partners which to separate their engineers, which manage Office 365 subscriptions, and those who manager Azure subscriptions. Or they want one group to manage SMB customers, and another group to manage Enterprise customers, and users from SMB team must not have an access to EPG customers subscriptions.
This is not an easy task, but it can be done in some way.
So, Partner has a technical support engineer called James with a user account james@csppartner.onmicrosoft.com. Here are some cases:
- If you want James to manage Office 365 customer subscriptions only, and don't allow any Azure subscription management or Partner directory management, just assign "Helpdesk agent" role to this user on Partner Center (or Limited Administration delegated rights on Partner's Office 365 Admin Portal)
- If you want James to manage Office 365 for specific customers only, then add his user account as external user to each Customer's directory and assign Global Admin role, or use even more granular access.
- If you want James to manage Azure for specific customers only, add his user account as external user to each Customer's directory and assign Owner rights to every Azure subscription that is being created
- If you want James and his colleagues to manage Office 365 for a specific Enterprise customer, add all their user accounts to Customer's directory and assign each of them corresponding administration rights in Customer's directory individually (admin roles can't be assigned to Azure AD groups)
- If you want James and his colleagues to manage Azure for a specific Enterprise customer, add all their user accounts to Customer's directory, create Azure AD group (static or dynamic) and assign Owner rights for Azure Subscriptions to this group (you can't assign rights to foreign group).
If CSP Partner has a lot of customers with Office 365, Azure, EMS and Dynamics CRM subscriptions, if he has different units which need to manage and support different CSP subscriptions - then I recommend to use something that will leverage "Just In Time Administration" and "Just Enough Administration" ideas. This is not implemented in Partner Center portal, but partners can do that by themselves:
- Partner creates a special portal with Azure AD authentication.
- Partner engineer logon to this portal, choose a customer from the list, choose a service (e.g. Office 365 or Azure - or even more granular) and requests administration permissions
- Portal generates an e-mail message with a ApproveDecline request and sends it to Customer's main point of contact
- Customer's main contact person clicks "Approve" button in the e-mail, and Portal launches a PowerShell script (or triggers REST API) to grant the requested administration rights to that engineer.
- In 2 hours the admin access is automatically revoked.
I want to clarify - this is only my idea, that is not implemented by Microsoft right now, but it can be implemented by partner's in-house developers or using 3rd party admin panel. So keep this idea in mind.
That's all for today. I hope that topic of Identity and Security in CSP became more clear for you.
UPD1: Thx a lot to my colleague K.P. for this nice diagram about identity processes in CSP Indirect model:
UPD2: Thx to my colleague Bart for the great example how to work with Partner Center and assign permissions in PowerShell.
UPD3: Part 2 of this article is available here.
Comments
- Anonymous
June 08, 2016
Thanks Kirill. Appreciate you putting this together as it cleared up some things for me. - Anonymous
January 17, 2017
The comment has been removed- Anonymous
January 17, 2017
Customer can remove your partner account from Managing Partners list, so you won't be able to manage Office 365 on behalf of the customer. But you will be able to create subscriptions and manage Azure subscriptions for the customer.- Anonymous
January 18, 2017
Hi Kirill,I have a screenshot here from my partner portal... For the customer that removed us from the delegated admins in O365, it states under Administer services: You don't have delegated administrative permissions for this customer. So the link to the Azure Management Portal is also gone (as all other links) I can only click: Ask for support permissions. In that case we will be added as Managing Parner again, but that's not what we want in this case. To have us removed as O365 admin I let the customer follow this post: https://blogs.technet.microsoft.com/uspartner_ts2team/2016/04/30/removing-the-csp-as-delegated-admin-in-office-365-customer-tenants/You say we can still manage their Azure subscriptions... how would we be able to do this?- Anonymous
January 18, 2017
The comment has been removed- Anonymous
January 18, 2017
Hi Niek!That's interesting. Give me some time, I'll check this in my Partner Center account.But you are describing the scenario, that should work. Real life example: Customer has Office 365 in EA, and LAR manages it (delegated admin). Customer purchases Azure services from another partner through CSP. CSP Partner doesn't have any rights to manage Office 365, but he needs to be able to manage Azure subscription.I will check that. - Anonymous
January 18, 2017
Thanks a lot Kirill!I'm really struggeling with this, as for a lot of customer it is a dealbreaker right now, and I don't have a fitting answer for them.- Anonymous
January 19, 2017
In my case it worked. What I did:1) Logged in to Partner Center under a partner user account with Admin Agent rights.2) Created a new Customer with a new tenant.3) Logged on to Office 365 admin portal under admin@tenantname.onmicrosoft.com and removed a partner record from Managing Parners list.4) I've checked that partner user account don't have any access to manage Office 365 and don't see users in the tenant.5) While I couldn't open Azure Management console in Partner Center using Service Management menu (it showed "Ask for support permissions" action instead), I was able to log on to https://portal.azure.com/tenantname.onmicrosoft.com using partner user account. I had Owner rights for that subscription.This demonstrated a case when partner can't manage Azure AD or Office 365, but can manage Azure subscription. The only thing that don't work is IAM. I couldn't manage resource permissions using partner user account on Azure portal because that user wasn't able to get the list of users in tenant's directory.In CSP model Azure subscription is owned by CSP partner and customer can't remove that rights. Customer don't have any rights for the CSP subscription, rights need to be granted by the partner first. This is right because partner is always responsible for the bill and need to have control of all Usage-based resources.
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous
January 31, 2017
Hi Kirill,Interesting article!Is there a powershell or api to add external users from one AAD account to another? Say I want to add external user/group from one tenant under CSP to another tenant's subscription.- Anonymous
January 31, 2017
You can use Azure AD B2B COllaboration for that, but capabilities are limited and I'm not sure that it can be done via PowerShell. Check here: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-b2b-collaboration-overview
- Anonymous
- Anonymous
March 15, 2017
Hello, I have a partner account and my user has Admin Agents permissions. I created a customer and assigned an azure subscription. The problem is that on entering https://resources.azure.com I can not see the subscriptions of my customers. Help me and thanks- Anonymous
March 16, 2017
Looks like Azure Resource Explorer doesn't support tenant switch. Since your partner user account and customer Azure subscriptions live in different tenants, you won't see them.- Anonymous
March 16, 2017
Hi, thanks for your response.I am developing a partner application and I need to manage my clients' azure resources through that application.Here are the scenarios:1.- I enter the site https://partnercenter.microsoft.com with my partner user, then I go to the clients section and select a client. Finally I go to their subscriptions and there is the subscription of azure. By clicking on "All resources (Azure portal)" I enter the azure portal with my partner user but within the directory of my client. By going to the subscriptions section, I actually see your subscription and I own it because of Foreign Principal. I can fully manage subscription resources.2. I enter portal.azure.com with my partner user. When I enter the subscriptions section, I do not see any subscriptions even though I own my clients' subscriptions through scenario 1.Can scenario 1 be replicated through an application? Thank you- Anonymous
March 16, 2017
This is a limitation of Azure Resource Explorer portal, not a limitation of ARM. In your case just use PowerShell, X-CLI or REST to work with Azure Resources.Login-AzureRmAccount$TenantID="testtestest.onmicrosoft.com"$SubscriptionID="64E8EB57-ABAB-4488-6BD2-15CE6B1A25D1"Select-AzureRmSubscription -SubscriptionID $SubscriptionID -TenantId $TenantIDGet-AzureRmResourceGroup - Anonymous
March 16, 2017
If you are logging in with Partner Center admin, you need to specify a customer tenant name. For example, to manage Azure CSP subscription of a customer customer.onmicrosoft.com with Partner Center Admin credentials, use such link:http://portal.azure.com/tenantname.onmicrosoft.comThen you will see all Azure CSP subscriptions in that tenant (=directory).- Anonymous
March 16, 2017
The comment has been removed
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous
March 22, 2017
Kirill great article. Quick question, our application currently (for Azure Pay As You Go accounts) needs to authenticate to Azure AD, we create a Contributor user and then read ARM metrics via REST. But for CSP partners, who have multiple subscriptions, this means that they need to authenticate our app to each subscription individually (and create a user in each subscription) which causes a lot of new work for our CSP customers. What is the best way, using REST, to allow our app to authenticate to all of associated CSP subscriptions for a specific Partner?- Anonymous
March 22, 2017
I suppose that granting that app Admin Rights in the Partner Center is the only possible option here.- Anonymous
March 24, 2017
Well, we are looking to grant rights to CSP Admin's sub-accounts in Azure.
- Anonymous
- Anonymous
- Anonymous
March 27, 2017
Hello,I still can not see the subscriptions of my clients.I have a CSP account and activate sandbox mode. Then I create clients and assign each one an Azure subscription.Then using my sanbox global administrator account at resources.azure.com or powershell using the Get-AzureRmResource command, I can not see the list of subscriptions for my clients, despite having the privilege of managing their subscriptions as owner of these Through the admin account in the CSP program.Help and thanks. - Anonymous
May 03, 2017
The comment has been removed - Anonymous
July 10, 2017
Hi Kirill,thank you for this great article. We are trying to get the granular access running.I've tried to assign the "helpdesk agent" in the CSP and additional "global admin" in the tenant.In effect the user has the "helpdesk agent" permissions.When I only assign the "global admin" role at the tenant to the external (csp) user I'm getting a runtime error when opening the direct link to the tenants admin portal (this style: https://portal.office.com/Partner/BeginClientSession.aspx?CTID=TENANDGUID&CSDEST=o365admincenter) What am I doing wrong?- Anonymous
October 26, 2017
Hi Christopher,I have tried to do the same confirguration but I am getting a runtime error as well. Did you manage to resolve your issue?
- Anonymous