Setting up your first ADFS POC
Here are the steps for setting up a POC for ADFS:
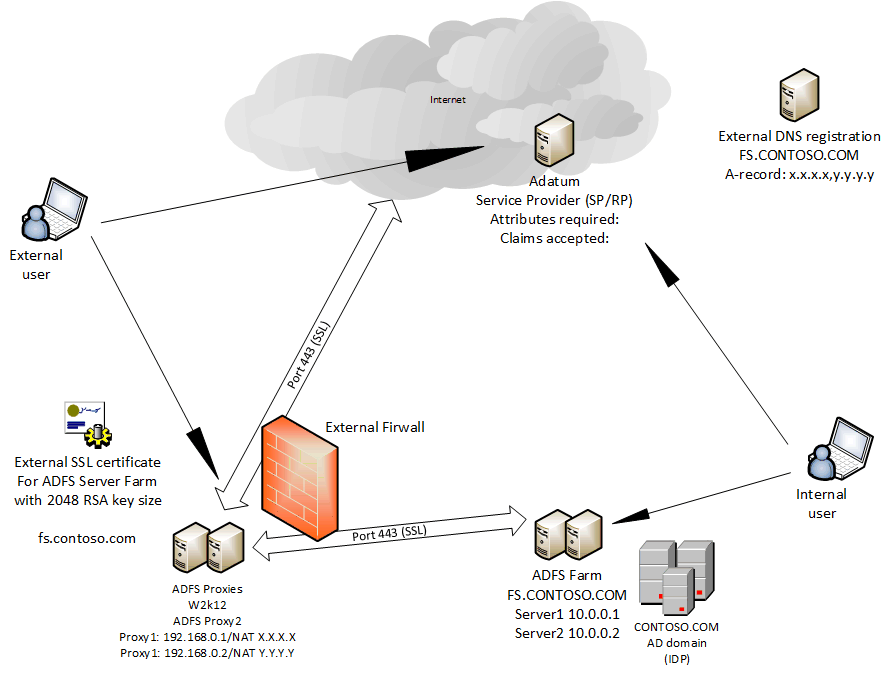
First of all, you need to decide on what your federation server farm will be called on the Internet.
In the drawing below I've chosen the name fs.contoso.com - this will be registered in DNS as follows:
- in external DNS to point to the external IP addresses assigned to the ADFS proxies *
- in internal DNS to point to the internal IP addresses assigned to the ADFS servers
Secondly, you need to make some design decisions:
Design input:
- Virtual Hardware or physical Machines for the ADFS servers and proxies?
- Operating system: We currently recommend Windows Server 2012 with the built-in ADFS 2.1 role (do not add the ADFS 1.1 role on W2k8 R2 - use the ADFS RTW download instead and make sure you patch it with the latest ADFS 2.0 Roll-up update on http://support.microsoft.com/kb/2790338)
- ADFS should preferably be installed as an ADFS Farm, even if you're only installing one server in the farm (it's simpler to scale out as a farm)
- The DNS name of the ADFS server should be registered in external DNS for the public IP that NAT's to the ADFS Proxy and the private IP's of your internal ADFS server(s) on your internal DNS servers
- Obtain a public SSL certificate that matches your chosen DNS name for the federation service (fs.contoso.com in my case). ADFS 2.1 doesn't really like wildcard certificates so try to avoid these.
- For simplicity you should choose WID as your database location (i.e. the Windows Internal Database which is a server feature in W2k8R2/W2k12)
To work on with your federation partner (SP or Service Provider) :
- Verify that the federation partner isn't using SAML Artifact Resolution (this requires SQL on the ADFS and direct connectivity between the ADFS server and external SP)
- Verify if your partner support SHA-256 (if not then your security settings for the Relying Partner trust with that SP will need to be lowered to SHA-1)
- Confirm the partner is able to federate using SAML 2.0 IdP Lite (which is what ADFS 2.1 supports)
- Send the partner the link http://download.microsoft.com/documents/France/Interop/2010/Using_ADFS2_0_For_Interoperable_SAML_2_0-Based_Federated_SSO.docx
- Agree on a unique identifier the Service Provider will use to identify you as an IDP in their systems (for my case I used CONTOSO)
- Obtain their Metadata and send them your Metadata and optionally the public key of your token signing cert.
- Agree upon which types of claims and attributes shall be used in the federation trust. Specific requirements for the SP such as transient NameID or similar will need to be manually added as claims on the ADFS trust with the SP.
- Decide whether the initial Communication will be initiated by the IDP (Your ADFS server) or the SP (by going to their web page that redirects back to your ADFS servers)
* Host files are typically used on the ADFS proxy servers to point them to the internal IP of the DNS name of the federation server farm.
Further details:
ADFS Wiki
http://social.technet.microsoft.com/wiki/contents/articles/current-adfs-resources.aspx
AD FS 2.0: Guidance for Selecting and Utilizing a Federation Service Name
http://social.technet.microsoft.com/wiki/contents/articles/4177.ad-fs-2-0-guidance-for-selecting-and-utilizing-a-federation-service-name.aspx
Interoperability with Non-Microsoft Products
http://social.technet.microsoft.com/wiki/contents/articles/2735.ad-fs-2-0-content-map.aspx#Interoperability_with_Non-Microsoft_Products
Comments
- Anonymous
February 15, 2013
great article. we are about to set up a POC so this was helpfull