Configure Kerberos authentication (Office SharePoint Server)
In this post I would like to share basics steps for configuration of Kerberos for SharePoint. I have referred to one of my test environment as an example throughout this configuration.
What is Kerberos:- The Kerberos version 5 Authentication Protocol provided a mechanism for Authentication – and mutual authentication between a client and a Server, or between one server and another Server. The Kerberos V5 protocol assumes that initial transactions between clients and servers take place on an open network in which packets transmitted along the network can be monitored and modified at will. The assumed environment, in other words, is very much like today’s Internet, where an attacker can easily pose as either a client or a server,
Based on RFC 1510: https://www.ietf.org/rfc/rfc1510.txt?number=1510 •
Uses encrypted tickets to authenticate clients and services.
There are many reasons why Kerberos authentication should be used over the default NTLM, one reason should be because it is faster and more secure than NTLM. A question can always come to our mind as to why would one use Kerberos ....what are some of the benefits.
§ User's passwords are never sent across the network .
§ Double Hops are supported.
§ Kerberos is more secure.
§ Kerberos is entirely based on open standards.
Kerberos authentication is required for some key scenarios in SharePoint 2007 such as the RSS Viewer web part and any time user network credentials need to be delegated across multiple machine hops. This document details how to enable Kerberos delegation with Excel Services and the RSS Viewer web part.
NOTE – Successful implementation of Constrained Kerberos authentication and delegation in a SharePoint farm is dependent on the farm topology and where within the farm Excel Services has been enabled. Depending on the scenario, you may be required to change the content web application pool account used to match that of the SSP account in order to successfully implement Constrained Kerberos delegation.
Read More About Kerberos On TechNet
Now lets look at how to setup Kerberos or what are some of the basic steps we need to follow in order to configure SharePoint to run with Kerberos. • Gather Informtion for URLs and Service Accounts • Create SPN’s • Content Web Applications • SSP Web Application • SQL Server • Enable Delegation for Service Accounts • Constrained Delegation (more secure) • Unconstrained Delegation • Enable Delegation for All Servers including SQL Server • Enable Kerberos for Web Applications in Central Administration • Application Management | Authentication Providers | I will try and outline a few steps which we can follow step by step to configure Kerberos :- On this blog I have taken a test environment and a couple of service accounts. This will help understand the example and the utilities I have used in a more effective manner and will also be easier for me to explain. So let’s look at the next action .
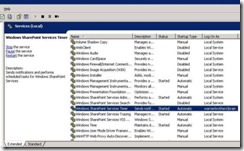
How to Find SharePoint Farm Account
Log on to one of the SharePoint server in the farm . In our case as mentioned I have a single server. From start menu click on run and type Services.msc. Locate Windows SharePoint Services Timer .Farm Account is listed in Logon On As column
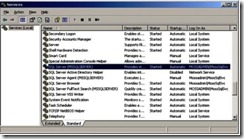
How to Find Out SQL Server Service Account
Log on to SQL Server,From start menu click on run and type Services.msc.Locate SQL Server Service & the SQL Service Account is listed in Logon On As column
Next important activity is to find out all URLS on the SharePoint farm as well as keep the service accounts we gathered handy. Ideally SharePoint administrator will be aware of each of this settings however if you are an administrator and you need to get this settings quickly below is third party utility which you can use. The utility is called SPSFarmReport. The objective of this tool is to gather environment details where Windows SharePoint Services 3.0 or Office SharePoint Server 2007 is installed.You can download the utility from the link below
Note :SPSFarmReport is a thirdparty utility and blog owner is not responsible for the supportability or the warranty of execution or any issues if faced . Please read the supportability and disclaimer if any from the download link of the utility and test out the utility on your test environment before you execute the same on your production.
Download SPSFarmReport
You can always navigate to the server hosting Central Administration and get all of these details required to configure Kerberos . However if you have tested this utility and decide to run it log on to server hosting Central Administration and run the executable . Installation is not Required and it just creates a HTML Report on the loaction you excuted the executable.
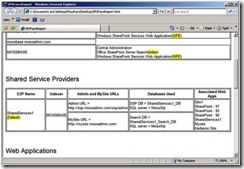
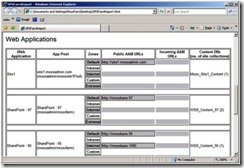
Below are some sample output of the executable that I ran on my environemnt for this sample configuration
Sample Output Shared Services Settings
Sample Output Web Application URL
Now that you have gathered all the data we have the next important task of registering the SPN
Register SPNs (Only on Domain Controller)
Log on to Domain Controller with Domain Administrator Rights:
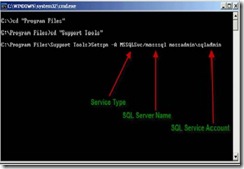
Register SPN for SQL Server (NetBIOS and FQDN)
Setspn -A MOSSLSvc/mosssql mossadmin\sqladmin
Setspn -A MOSSLSvc/mosssql.mossadmin.com mossadmin\sqladmin
Register SPN for URLs . Below are the ones I registered. Please refer back to the SPSfarm report for all of these URLS.
Register SPNs as follows:
Setspn -A HTTP/ca mossadmin\MossFarm
Setspn -A HTTP/ca.mossadmin.com mossadmin\MossFarm
Setspn -A HTTP/ssp.mossadmin.com mossadmin\MossSSPService
Setspn -A HTTP/ssp mossadmin\MossSSPService
Setspn -A HTTP/mysite.mossadmin.com mossadmin\MossMysitePool
Setspn -A HTTP/mysite mossadmin\MossMysitePool
Setspn -A HTTP/kerb.mossadmin.com mossadmin\MossKerbPool
Setspn -A HTTP/kerb mossadmin\MossKerbPool
Register SPNs for Shared Services Provider
Setspn -A MSSP/mossbase:56737/SharedServices1 mossadmin\MossSSPservice
Setspn -A MSSP/mossbase:56738/SharedServices1 mossadmin\MossSSPservice
Setspn -A MSSP/mossbasewfe1:56737/SharedServices1 mossadmin\MossSSPservice
Setspn -A MSSP/mossbasewfe1:56738/SharedServices1 mossadmin\MossSSPservice
Next important task for configuration is to Enable Delegation.
Delegation Types
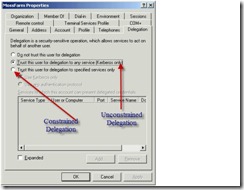
1. Non-Constrained Delegation This implementation allows the Kerberos ticket to be passed to any Service Principle Name (SPN) that is requested. If the service that is being requested is not “locked down” the potential of a user being delegated to access sensitive processes is still present. However, if all services are properly configured and “locked down” with appropriate rights this implementation is significantly easier to setup. There is no additional knowledge of the services to be delegated to needed
2. Constrained Delegation This implementation allows the Kerberos ticket to be passed to only services that have been setup as allowed delegation services. Note: This type of delegation can be setup in both the Windows 2000 and 2003 domains. This method requires that administrators to know the services present in the domain and have those services setup with appropriate rights to limit the access of users not intended to have access.
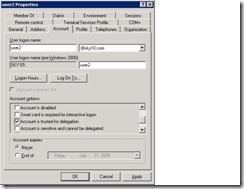
I would not talk about Domain functional level but the images below are what you would see depending on if your domain functional level is Native or not .
Below are some links which gives more information on Domain functional levels
What Are Active Directory Functional Levels? https://technet.microsoft.com/en-us/library/cc787290(WS.10).aspx
Raise the domain functional level https://technet.microsoft.com/en-us/library/cc776703(WS.10).aspx
How to raise domain and forest functional levels in Windows Server 2003 https://support.microsoft.com/kb/322692
Delegation for Service Accounts
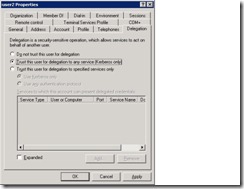
Next comes the important task of delegation of service account. Navigate to Domain Controller or else if you have the snap in installed on any member server bring up Active Directory Users and Computers | Properties of Service Account | Delegation Tab | Select Trust this user for Delegation to any service (Kerberos only)
Enable Kerberos for SSP
Perform this action on SharePoint Server where Central Administration is hosted.
Navigate to %Program Files%\Common Files\Microsoft Shared\Web Server Extensions\12\Bin\
Run following command:
stsadm –o setsharedwebserviceauthn –negotiate
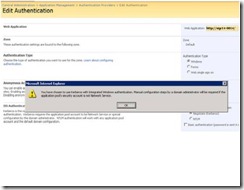
Now Enable Kerberos for All Web Applications. Browse to Central Adminstration and Application management tab
Central Admin | Application Management |Authentication Provider | Select Web App | Select Negotiate (Kerberos)
This brings us to an end of Kerberos configuartion for your SharePoint environemnt. Considering we have gathered all information for service account and executed the commands correctly the farm should be running properly with Kerberos .
Now lets talk about a couple of tools we would use in case we are troubleshooting an existing Kerberos issue
Run following command on Domain Controller to list any duplicate SPN
ldifde -f c:\spn_out.txt -d "DC=mossadmin,DC=com" -l serviceprincipalname -r "(serviceprincipalname=HTTP/mossbase*)" -p subtree
Command to List SPNs for specific Service Account:
setspn -Ldomain\serviceaccount
Troubleshooting Tools
DelegConfig
Brian Booth, Support Escalation Engineer with IIS team at Microsoft created an ASP.NET Application that runs some key checks on the client, server, to identify issues with Kerberos delegation.
Download link
https://www.iis.net/downloads/default.aspx?tabid=34&g=6&i=1434.
Below is a link to Bret Bentzinger's which has steps on how to set it up. I personally love the way it has steps to set up DelegConfig.
https://blogs.iis.net/bretb/archive/2008/03/27/How-to-Use-DelegConfig.aspx .
Now that we have setup the same lets look at some sample output from our test environment.
Sample Output:
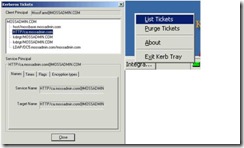
KerbTray
The Kerberos Tray tool lists all cached Kerberos tickets and allows you to view the tickets' properties as well as to purge tickets. This information may help in resolving problems with authentication and access to network resources.
KerbTray is included in Windows 2000 Resource Kit Tool: Kerbtray.exe
Event Viewer & Netmon Trace.
Definitely we can check event viewer and look at our favorite Netmon to look for some very specific error messages .
NOTE – Successful implementation of Constrained Kerberos authentication and delegation in a SharePoint farm is dependent on the farm topology and where within the farm Excel Services has been enabled. Depending on the scenario, you may be required to change the content web application pool account used to match that of the SSP account in order to successfully implement Constrained Kerberos delegation.
WARNING – Configuring Kerberos on the Default zone of a SharePoint web application may prevent Search from being able to index the site.Seehttps://technet2.microsoft.com/Office/en-us/library/40117fda-70a0-4e3d-8cd3-0def768da16c1033.mspx?mfr=truefor more information. You may need to change the account under which Search runs or make other modifications for successful Search indexing, etc.
ASSUMPTION – It is assumed that SharePoint is the only product installed in the farm. These procedures have not been tried in environments that host non-SharePoint web applications. It is also assumed that the SharePoint farm has a single Shared Service Provider. These procedures have not been tried in farms that have multiple SSPs, etc. Its recommended that you test this on your test environment before implementing on your production. Please read disclaimer section of this blog for more info.
Disclaimer : This posting is provided "AS IS" with no warranties, and confers no rights.