A closer look at Office 365 Advanced Security Management

In my introduction to Office 365 Advanced Security Management, I talked about the security concerns that every business leader has as companies continue their digital transformation journeys. As part of Secure Productive Enterprise, Office 365 Advanced Security Management (ASM) will make it easier for organizations to empower their employees by delivering advanced enterprise security and productivity technology. In this post, a follow up to both the introduction and the September 2016 community call, I’ll provide a closer look at the three ways ASM gives customers enhanced visibility and control into their Office 365 environment.
Introduction to Office 365 Advanced Security Management Watch the Office 365 Partner Community call about ASM on demand Security and compliance updates from Ignite 2016 (added 9/26/2016)
Threat detection
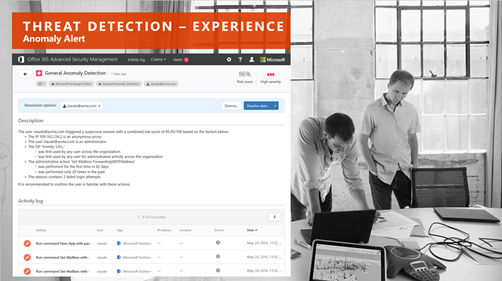
Office 365 Advanced Security Management lets you detect threats by helping you identify high-risk and abnormal usage, security incidents, and threats. In ASM, you have a robust policy and alerting engine that provides insight into potential breaches by setting up anomaly detection policies for your Office 365 environment. Anomalies are detected by scanning user activity and evaluating its risk, based on more than 70 different indicators. Risk factors include login failures, administrator activity, inactive accounts, location, impossible travel, and device and user agent.
Advanced Security Management also leverages behavioral analytics as part of anomaly detection to assess risk in what users are doing. It does this by understanding how the user interacts with Office 365 on a daily basis. After establishing a baseline, ASM can determine if a user’s activity/session is suspicious, and give it a risk score to help you determine whether to take further action.
Enhanced control
Advanced Security Management leverages granular controls and security policies to provide you with enhanced control. These policies help you shape the Office 365 environment, and let your track specific activities. Create your policies using out-of-the-box templates that help you see when someone is downloading a lot of data, has multiple failed logon attempts, or logs in from a new IP address.
It’s likely that you will want to create additional policies that are customized to your unique environment, and you can do this, too. Using activity filters, you can look for specific items like the location of the person, a user or group, the device type, IP address, if a new user is created, or if someone is granted admin rights. Based on these activities happening once or a repeated number of times in a specific timeframe, you can create an alert, or notify or someone in IT. Alerts give you the visibility into the activities that you want monitored, and ASM gives you an easy way to see all of these and start your investigation. Based on the investigation, you might deem that the behavior is risky and you want to stop the user from doing anything else by suspending the account which you can do that directly from the alert.
Discovery and insights
Using ASM, discover information and get insights into your Office 365 usage, as well as other cloud services, to help you with any shadow IT problems. The app discovery dashboard makes it easy for you to get a snapshot of pertinent information around your Office 365 usage:
- How much traffic is your Office 365 use generating?
- Who are the top Office 365 users in your organization?
- Are users utilizing other productivity cloud services?
With the ability to discover about ~1,000 applications for collaboration, cloud storage, webmail, and more, you can better determine if there is shadow IT happening in your organization. For example, perhaps a department has purchased another SaaS productivity solution with their credit card, and you see Dropbox usage after having standardized on OneDrive for Business for your organization. You may decide to take action on that insight, perhaps educating a top user or department about the benefits of OneDrive for Business. What’s great about this aspect of ASM is that there is nothing to install on the user end points to collect this data.
Try it yourself – and demo it for customers
You can try Advanced Security Management yourself, and set up a demo to show customers on the Microsoft Demos website.
- Sign in to Microsoft Demos with your MPN credentials
- Select Tenants > Create > Quick Tenant > Standard Office 365 Demo Content > Next
- In the Add Ons menu, select Advanced Security Management (ASM)
If you are a Customer Immersion Experience (CIE) partner, Advanced Security Management in the latest version of the Microsoft CIE demo. Review the “ASM with CIE Walk-through” in the resource section of the site, or download it from here.
The partner opportunity
The features and capabilities of Advanced Security Management provide you with an opportunity to address customer priorities such as trust, collaboration, mobility, and intelligence. I hope the focus on this topic in the Office 365 Partner Community helps you with the customer conversation. If you have comments about this blog post or questions about the topic, let us know in the Office 365 Partners Yammer group.
Office 365 and Voice Partner Community