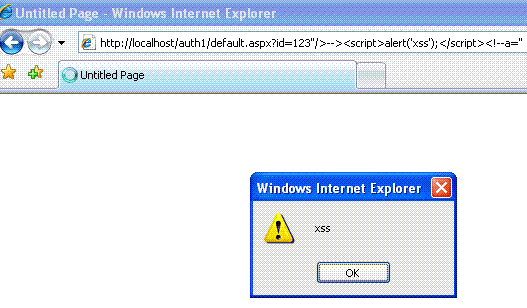
Catch the security flaw #1 (Flaw and its countermeasure)
It is time to discuss the flawed code that I posted a couple of weeks back. The comments posted were good and in essence summarize the flaw.
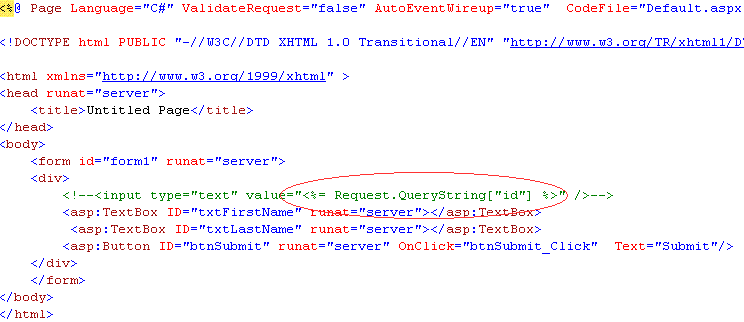
The circled part is an example of an embedded code block. The query string parameter “id” will be inserted inside the <% %> block, creating HTML at the client that looks something like this:-
<!--<input type="text" value="123" />--> for a query string value id=123.
This can lead to Cross Site Scripting (XSS).
The countermeasure is simple. Treat user controlled input which is put inside an embedded code block with caution, even if there are comments around the HTML element. If you do not need the element, remove the embedded code block. If you need it, validate the input and encode the output.
Setting ValidateRequest to true (which is by default) would have prevented this bug from getting exploited. But would ValidateRequest prevent this from being exploited?
Comments
- Anonymous
February 19, 2008
<input type"text" value="<%= Server.HtmlEncode(Request.QueryString["id"]) %>" Old problems, old solutions.