AD DS Site Awareness for AD CS and PKI Clients
Applies to
Windows®8 and Windows Server® 2012
Certificate services in Windows® 8 and Windows Server® 2012 can be configured to utilize Active Directory Domain Service (AD DS) sites to help optimize certificate services client requests. This functionality is not enabled by default the certification authority (CA).
Enabling site awareness on a CA
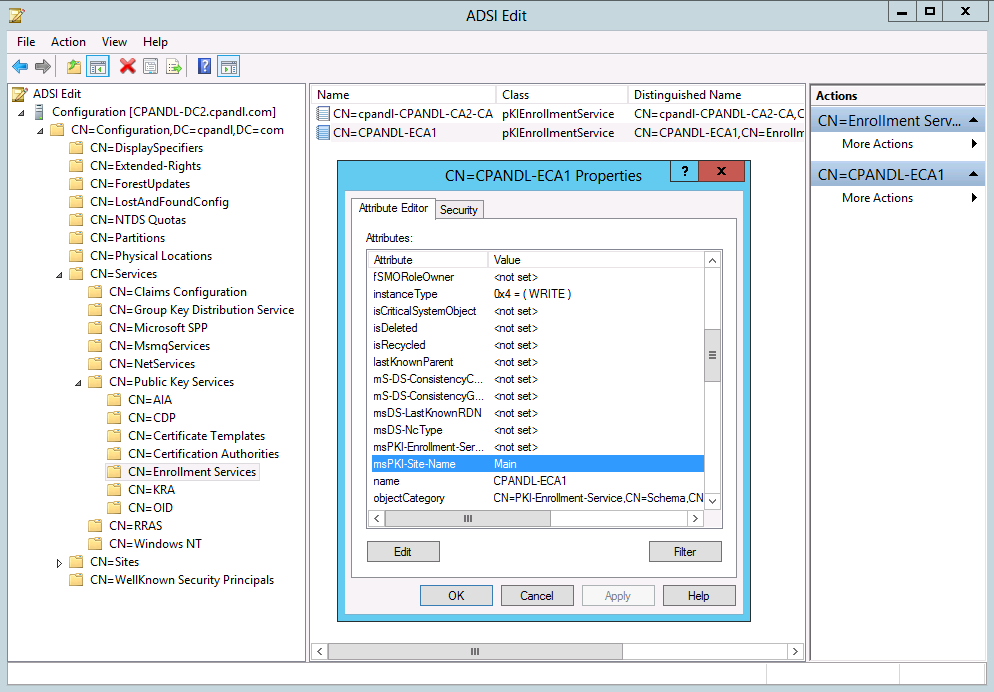
To enable certificate services site awareness, the msPKI-Site-Name attribute must be populated for the certification authority (CA) object in the Enrollment Services container of Active Directory Domain Services (AD DS). The Enrollment Services container is in the Configuration container of AD DS under CN=Public Key Services, CN=Services,CN=Configuration,DC=<domainDistinguishedNamingContext>. For example, the following figure shows a CA named CPANDL-ECA1 has an msPKI-Site-Name attribute value of Main.
To set the msPKI-Site-Name attribute value on a CA, you can run the following command:
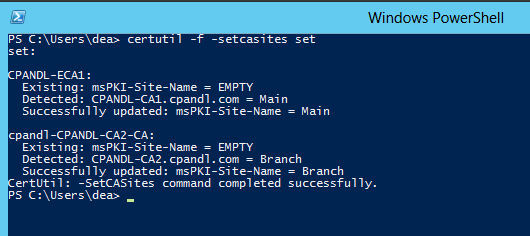
certutil -f -setcasites set
You can see the results of this command in the following figure when run on the CPANDL AD DS domain with two Enterprise certification authorities.
The command enumerates all CAs in the enterprise using directory services APIs. The CA site memberships are checked for their current site membership. Then, the CA objects in AD DS are configured for the site name that is appropriate for their network configuration.
To set the the msPKI-Site-Name attribute on a single CA object in AD DS to a specific name, you can run the following command:
certutil -setcasites -f -config "<CAConfigName>" <SiteName>
You can see the configuration of a CA by running the following command:
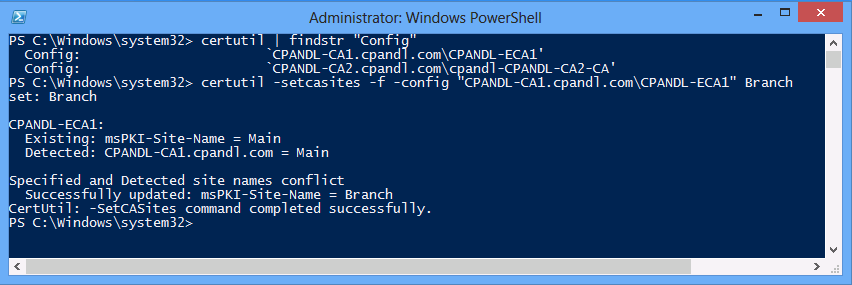
certutil | findstr "Config"
The following figure illustrates the configuration of CPANDL-CA1.cpandl.com\CPANDL-ECA1 with the site name Branch, even though the detected name is Main.
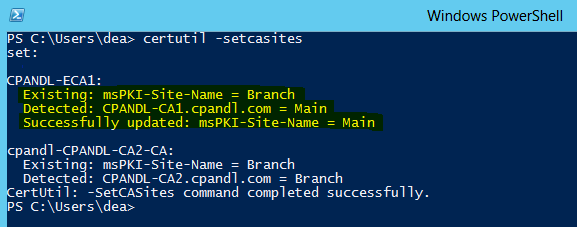
Running the certutil -setcasites command displays and also corrects the name conflict, as shown in the following figure.
Client selection of a CA
When enrolling for a template-based certificate, the client queries AD DS for the template and the CA objects. The client then uses a DsGetSiteName function call to get its own site name. For CAs with the msPKI-Site-Name attribute already set, the certificate services client determine the AD DS site link cost from the client site to each target CA site. A DsQuerySitesByCost function call is used to make this determination. The certificate services client uses the returned site costs to prioritize the CAs that allow the client the Enroll permission and support the relevant certificate template. The higher cost CAs are tried to be contacted last (only if former CAs are unavailable).
Note: A CA may return no site cost if the msPKI-Site-Name attribute is not set on the CA. If no site cost is available for an individual CA, then the highest possible cost is assigned to that CA.
The following statements apply to the way that a certificate services client contacts the appropriate CA:
- Each set of CAs that have identical costs will be ordered randomly within that set, to evenly distribute the load.
- Enrollment is attempted through the lowest cost CAs (smallest numeric site cost value).
- If contacting that CA fails, the next the higher cost CAs are tried.
- If none of the CAs (that allow Enroll permission and publish the relevant template) are accessible or responding, the enrollment request fails.
Notes:
- Since all Enterprise CAs expect DCOM calls and utilize Kerberos credentials, the type of credentials required by the CA do not affect the CA ordering.
- None of the client site cost processing and CA ordering operations results in contacting any of the CAs; only AD DS queries and an AD DS site cost query calls are made.
- If site cost collection is not enabled on the client, the CAs will be ordered randomly.
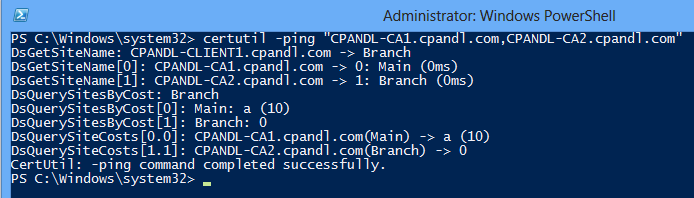
When the clients and certification authorities are both configured for AD DS site awareness, you can use the certutil -ping command to verify the site costs. For example, the certutil command shown in the following figure is: certutil -ping "CPANDL-CA1.cpandl.com,CPANDL-CA2.cpandl.com"
As for support for this feature (site awareness provided by specifying msPKI-Site-Name value on pKIEnrollmentService objects) from client side, in fact it's enabled by default on all clients running Windows 8+ and you don't need to do anything additionally.
There has been some confusion. Some articles indicated that the following command must be run to set the EnrollFlags=0x2 to support this, which is not accurate.
certutil -setreg Enroll\EnrollFlags 2
In fact this only applies to Windows 7/Windows Vista clients. In addition, this flag enables the following behavior on these clients:
1. Get the list of enterprise CA servers by querying for all pKIEnrollmentService objects in CN=Enrollment Services,CN=Public Key Services,CN=Services,CN=Configuration,...
2. For each of CA server in the list, query its dNSHostName
3. By calling dsgetsitename (with dNSHostName being the input syntax), the client works out the site name for each CA server.
4. Clients then figure out which CA server to send out requests to based on the costs.
Obviously this behavior does not rely on msPKI-Site-Name and is a different mechanism compared with what we see on Windows 8+ clients.