Azure Multi-Factor Authentication Story
**Old Days **
We use passwords all the time, weather we are using a good authentication protocol like NTLM or a better one like Kerberos. Cryptography and digital certificates are the stronger alternatives to traditional passwords as you will have a public and private key pairs, which indeed makes things more interesting in terms of manageability and cost of implementation.
As security becomes more and more relevant to business today, people start thinking of two and three factor authentications. Smart cards were so popular because of their two factor nature and they indeed provide some sort of prestige. Smart cards are a good example of two factor authentication, because you need to have the physical card in addition to the PIN (something you have and something you know).
One of the big disadvantages of using smart cards is the cost of management. You need to enroll smart cards, replace them, retire them, update the certificates, etc. Imagine that someone forgot his smart card at home and he needs to log on. On the other hand, one time password (OTP) devices became common also. You get a hardware token with a number that keep changing every while. When you want to access a resource, just enter that number currently displayed in the device.
Moreover, some smart card providers are now offering smart cards with Biometrics. You should have the card itself (something you have), your thump (something you are) and perhaps a PIN (something you know). The addition of biometrics adds a difficult-to-clone token as they describe it.
The common thing between all the previous solutions is that you need to buy a hardware token, and maintaining it. If you look at the business model today, it is easily seen that every thing is moving fast. Security is a top priority and a must to be deployed from day one. There is no time to get a PKI specialist and educate people to carry around physical tokens all the time just to enable two factor authentication. People will forget their cards at airports, or at their home. Even worse, they will keep the smart card plugged in the smart card reader so that if the laptop get stolen, the smart card is stolen too.
**Nowadays
**
Nowadays, no one can move without carrying his mobile phone, and nothing can be a better second factor of authentication than your mobile device. There is a very small chance that you will forget your mobile device at home. Even if you do so, i am sure that you will go back and get it right away.
Your phone becomes the token, and it is by far the most cost effective solution for businesses nowadays. No extra training for people to use their mobiles, and no extra overhead for IT administrators if the token (mobile) is lost. There is no provisioning or management of tokens, since users already managing and owning their own mobiles.
We will talk about multi-factor authentication on premise just to explain my point here. To perform a multi-factor authentication for on premise applications, you need your application to redirect authentication to a service (MFA service) that will authenticate users by username and password, and by using the user’s mobile phone as a second factor authentication.
Although this seems to be a very effective solution, it introduces another problem. The IT administrators need to install and deploy the MFA service on premise, worry about how this service can contact the user’ mobile device for second factor authentication, and to make sure this service is always available.
The smart thing to do is to move the MFA service to the cloud, and use the MFA part as an offered cloud service. Your application will contact a cloud service for a second factor authentication, the cloud service will take over the task of contacting the user mobile number and getting response back, and finally the cloud service will return to your application with a response (success/failure).
Microsoft Azure MFA Offering
Microsoft Azure Multi Factor Authentication is a An Azure Identity and Access management service that prevents unauthorized access to both on-premises and cloud applications by providing an additional level of authentication.
The good news is that Azure Multi-Factor Authentication services is can be used right away if you have your applications on Azure or if you are using Office 365. Nothing can work better that using Multi-Factor authentication for your Office 365 users, since the application is already hosted in Azure.
What about on premise applications? what if you do not have any cloud presence yet and you want to use only the MFA part of Azure?
This is completely possible because of the smart design and offering of Azure MFA. Microsoft designed the solution in a completely abstracted way. It starts with your applications that require the multi-factor authentication. These applications can be your VPN server, your RDS farm, your IIS portals or any other service. The problem is that every application can offload the authentication task in a different way. Some of them (like most VPN gateways) prefer to offload the authentication using RADIUS protocol, while others may prefer LDAP.
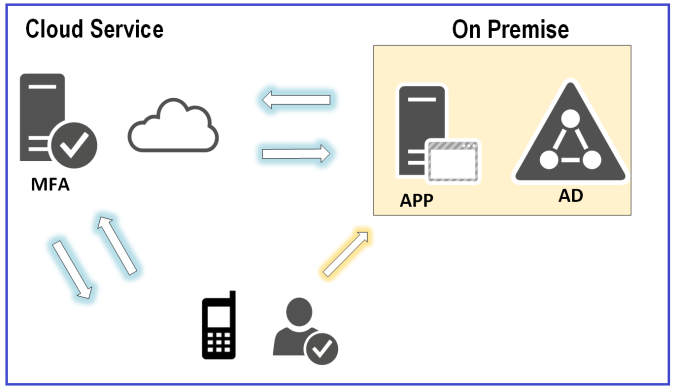
Since different applications prefer different methods of offloading the authentication, and theses applications need to contact Azure MFA services, Microsoft introduced a proxy server on premise (called the MFA server), that acts as an authentication proxy mainly. It has many listeners like RADIUS and LDAP from one side to talk to your applications, and it connects to Azure MFA services from the other side using HTTPS. This server is so easy to deploy on premise, and you just need to install the bits and do a little configuration via a wizard. No special service accounts, no extra difficult configuration to worry about, and you can rebuild it in few minutes.
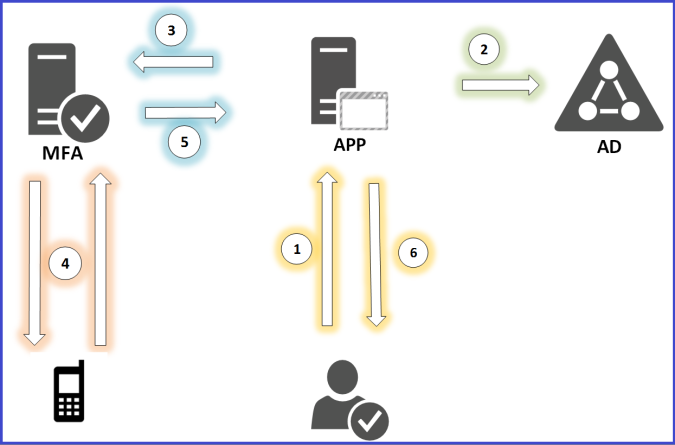
So how does this Azure MFA works? well, corporate applications that require multi-factor authentication will proxy any authentication request to the on premise MFA server. The MFA on premise server will contact your Active Directory or any LDAP directory on premise to check if the first factor authentication (username and password) is correct. If and only if the first factor authentication is successful, then the MFA on premise server will connect to Auzre services asking it to do the second factor authentication via the user’s mobile phone. This can be a phone call, an SMS message, or a push notification using Azure MFA mobile App.
What I really like about the Azure MFA is the level of abstraction that it provides. Your applications will do the first factor authentication using username or password perhaps, and then offload the second factor authentication to Azure MFA services. So what you are buying is really the second factor authentication here, which can be a mobile call, SMS or even a mobile app. You can configure each user with his preferable second factor authentication method. One use can choose a phone call as his second factor authentication where another may choose the mobile app.
Because Azure MFA can integrate with your applications using RADIUS also, you can easily enable multi factor authentication to your VPN clients in no time. The speed of deployment for such multi factor authentication solution in addition to simplicity and cost is something you cannot find easily elsewhere.
Why to do with Azure Multi-Factor Authentication?