Azure Multi-Factor Authentication “MFA” – Mobile App
Azure MFA works by providing the second factor authentication part as a cloud service. Azure MFA services will authenticate using one of the below methods:
- Mobile App
- Phone Call
- SMS
What is interesting here is that in your environment you can use the three methods at the same time. For example, the end user can choose that he wants the phone call option for the second factor, but as he is traveling next month, he can switch to the mobile app option. The end user can choose between these methods at any time by logging to the MFA user portal and choose his method.
Mobile App
It is an application published by Microsoft and available in all mobile stores. During the second factor authentication, you will receive a notification in the mobile app prompting you to verify that you want to complete the second authentication.
This application can be used for two things:
- As a software Token
In case you do not have good internet connection, and receiving a notification message to verify the authentication is hard, then the mobile app will generate offline one time password that keep changing every short period of time. Say for example you are building a web page, and you require people to submit a form with user name and password, you can add in the form an option to enter the one time password, then you can configure your application to contact the MFA server and verify if this one time password is working or not)
- As a push notification
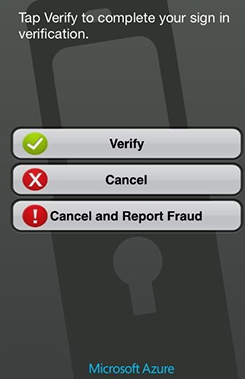
In this mode, you will get a push notification as seen in the figure below to complete the second factor authentication. Clicking Verify will complete the whole multi factor authentication cycle, while clicking cancel will cause it to fail.
There is an option (Cancel and Report Fraud), which is very interesting. Suppose you are at home watching TV, and out of no where, you receive such verification message on your Azure MFA mobile app. This means that someone is trying to authentication on your behalf. Since MFA server will not try the second authentication method until it verifies the username and password, this means that someone else has successfully logged on using his credentials and he reached phase two of the multi factor authentication process. By clicking report fraud, not only the request will be denied, but also puts a block in his user in the cloud service, so that the cloud service will not continue send push notification for coming fraud requests. You can also as an administrator, enable SMTP notification to notify a group of people for fraud reporting cases.
The interesting thing and confusing at the same time, is to locate the flow of data when using the Azure MFA mobile app during on premise implementation of the MFA server. It starts with your application calling the on premise MFA server, the MFA server will send a request to Azure to send you the verification message, then when you verify the request, your mobile will connect to the published web service located on the on premise MFA server.
Mobile App Activation
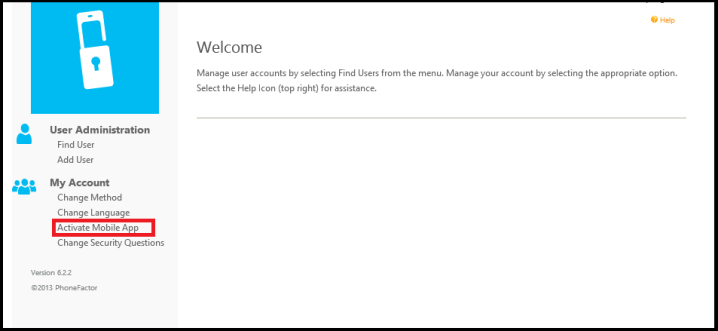
After the user is configured in the MFA with a mobile app second authentication preference, the user should download the mobile app from one of the phone stores, and then he should log on to the MFA user self service portal and choose to activate his mobile app, so that the MFA server recognize his mobile and associate the user with a mobile device. This is required in order to deliver the push notification to the correct device.