Windows: Protection against ransomware and possible issues
Introduction
Recently a new ransomware hit the world with its massive rate of destruction and we can say at the moment of writing this article, it is spreading and infecting more and more systems in different organizations around the world. The malware is called “WannaCry”, and it basically utilize the SMBv1 vulnerability in order to gain access on the victim system and encrypt data on the hard drive of a victim. Just like any other ransomware, you should pay a specific amount of money or the price will double up after a couple of days. In the case you refuse, the data is lost forever.
In this article, we are going to discuss the prevention against this ransomware and talk about the possible issues which might show up when you take actions against this ransomware.
Possible ways of protection
Before we discuss the methods in order to prevent this infection in your environment, we should first talk about, how this infection can spread and most importantly, in what ways a system becomes infected.
The spread can be done via the Internet, Email attachments, malicious links and other typical methods. Once the malware is transferred to the victim client, then it can abuse the SMBv1 vulnerability. The main way that a clean system becomes infected is by having a privilege escalation which utilize SMBv1 in order to gain access. This is the main part, the rest of the job is nothing but a simple encryption. Considering the SMBv1 as a gateway, it is safe to say that once you have blocked SMBv1 on your systems, there is no possibility to get abused by this malware. So we can say, here is the fixed number one: Disable SMBv1 through your network. This can be done using a variety of methods ranging from the registry, PowerShell, GPO. Secondly, if you have SMBv1 and yet have not decided to remove it from your infrastructure, you need to make sure that the “MS17-010” is applied to your system. The point to consider is, that this patch will not block SMBv1, but it resolves the vulnerability inside SMBv1, meaning your clients will be able to use SMBv1 if they wish for, but “WannaCry” will not be able to abuse that built-in vulnerability. As the time of writing this article, anti-virus should have found out the pattern of this attack. So if your anti-virus software is updated, you have much fewer worries to encounter. I am aware that the majority of anti-virus software, has included the appropriate DAT file in their database to prevent this attack.
How to disable SMBv1
Before continuing this method, it is highly recommended to update your anti-virus software and operating systems to the most recent version. If you are still worried, you can keep on removing SMBv1 through your domain. Frankly speaking, you should have disabled this SMBv1 long before this malware became into existence, but it is still a good point to disable SMBv1 for possible future vulnerabilities.
All we have to do is to apply a GPO which blocks the usage of SMBv1 in your domain through out all your systems. Since the creation of GPO in GPMC is not a complex task, we will highlight the key principal in that. Open up GMC and create a new GPO, linked to the domain. Once you open the GPO setting, navigate to Computer Configuration \ Preferences \ Registry, then add a new item using the parameters below:
- Hive: HKLM
- Path: SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
- Value Name: SMB1
- Value Type: Reg_DWORD
- Value Data: 0
The images below shows the procedure which is required to block SMBv1 using GPO:
However the setting below, AFAIK, will take care of SMB server side, but the client side is still open. So what we have to do is to disable SMBv1 client side using the commands below:
- sc.exe config lanmanworkstation depend= bowser/mrxsmb20/nsi
- sc.exe config mrxsmb10 start= disabled
It is worth mentioning again that if you have already patched your operating system, there is no necessity to disable SMBv1 because it might introduce issues to your environment which will be discussed in next section.
Possible issues after disabling
It is pretty clear that SMB is another protocol which is used in communications. Considering this fact, it is safe to say that when you SMBv1 is disabled, several communications will be interrupted. The point is, you are safe and sound to disable SMBv1 as long as it has been replaced by newer versions like SMBv1 and SMBv3. Here comes the problem: SMBv2 and SMBv3 are used in newer operating systems, which mean the older operating systems ranging from XP, 2000, 2003 will suffer from disabling SMBv1.
The rule behind this is simple. Once you disable SMBv1 on your environment, your 2012 R2 servers will continue functioning like a charm (because they no longer use SMBv1), but what happens to your windows XP clients? Surely they will fail in certain scenarios, simply because your DC’s are no longer accepting requests from SMBv1 clients and their requests are dropped. Here we will cover some of the possible issues in regard with disabling SMBv1.
Join to domain problems
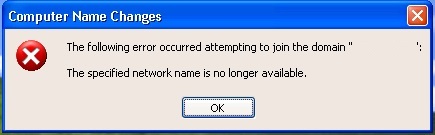
When we want to join an older client to the domain, you will receive error “The specified network name no longer available”. Basically what it says is right. If you open NetSetup.log file from debug folder of the client, you will notice that SMB connections are used in order to connect to Domain Controller to complete the process of joining to the domain. And because our domain controllers no longer listen to SMBv1, they cannot accept the request from older clients. The image below represents the error from a Windows XP client:
After we re-enable SMB, the problem is resolved.
Cross domain authentication
This one is a tricky one! You may encounter a situation where a user from domain A, cannot login to an older client (2003, XP) computer from domain B. Once the username and password is entered, an error will pop up which says “The RPC server is unavailable” during your logon. The story behind this error is related to the process where the client should connect to an originating domain in order to verify the trust and login credential of that user. Once it cannot do that, the error will be nothing but the image below:
Once this problem occurs we can actually do two things. The first approach is to just re-enable SMB on the originating domain (the domain who holds the remote user) and let them accept SMBv1. The second approach is to manipulate IgnoreRegUserConfigErrors registry key which is located at HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server with the value of “1”. If more information is needed about this registry key, take a look at the “Other Links” section.
GPO Stuff
The GPO processing is another possible issue of disabling SMBv1. Because the client should be able to collect the gpt information from a domain controller and when the mentioned protocol is blocked, no GPO will be processed.
SCDPM 2010
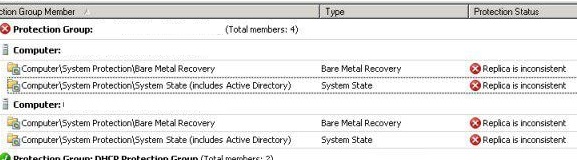
If you have already worked with SCDPM as you backup technology, you should have found out that when a backup is triggered and taken successfully, the backed up data from the client must be copied to the volume at the DPM server. This is a possible issue that when you disable SMBv1, DPM 2010 will not be able to function correctly at the backup transfer stage. Meaning that the backup will complete successfully itself, but once the copy is initiated, it will fail. The image below represents a sample of this error:
Conclusion
It is clearly visible that each day we face a different type of attacks which are based on the existing vulnerabilities of our environment. Considering the fact that old protocols are not immune to attacks, it is necessary to upgrade our infrastructure including (Operating System, Anti-Virus...) to remove these type of vulnerabilities in our environment.
Having said that, the WannaCry malware, will not be able to function if SMBv1 is no longer used in your environment. If you still have not decided to disable this vulnerable protocol, at least make sure that your operating systems are patched with “MS17-010” and your security software is up to date.