Micorosft Azure Application With LiveID, Google, Facebook, Yahoo!, and OpenID - PaaS
Back to [[ Azure Active Directory Solutions For Developers]]
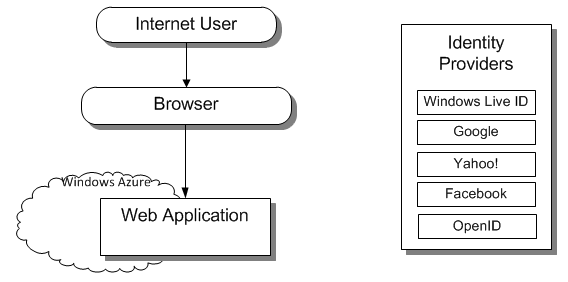
Scenario
In this scenario, you are developing a web application to be deployed to Azure. It should serve Internet users whose identities and credentials are managed by Internet identity providers such as Live ID, Facebook, Google, Yahoo!, and any Open 2.0 identity provider. The users should be provided with Single Sign-On (SSO) capability so they can use their existing Internet credentials to log on to the Azure deployed web application.
- Web Application to be deployed to Azure.
- Internet end users whose identities are managed by Internet identity providers such as Live ID, Facebook, Google, Yahoo!, and any Open 2.0 identity provider.
- Need to provide SSO so that the end users can use same credentials managed by Internet identity providers such as Live ID, Facebook, Google, Yahoo!, and any Open 2.0 identity provider when accessing the Azure deployed web application.
Solution Approach
ACS used to solve this scenario. ACS provides federation capability with Internet identity providers such as Live ID, Facebook, Google, Yahoo!, and any Open 2.0 identity provider.
- ACS used to provide federation with Internet identity providers such as Live ID, Facebook, Google, Yahoo!, and any Open 2.0 identity provider.
- Internet identity provider issues tokens upon successful authentication.
- Application uses WIF to manage trust and validate and parse incoming tokens issued by Internet identity provider and transformed by ACS.
Analysis
ACS serves as an abstraction layer between the application (relying party) and the Internet identity provider (IdP). Developers do not need to learn time and again when dealing with different IdP's - all that is needed is a simple configuration and ACS takes care of protocols heavy lifting.