Limit Access to Office 365 via ADFS with Threat Management Gateway
I recently had a partner ask how to limit who can use Office 365 from defined locations. Their customer requirement was to not allow hourly employees access to Office 365 (Exchange Online) from non-corporate / store locations. They still wanted to provide non hourly employees full access.
For corporate employees, they were using the Office 365 E plans which allow for OWA and full Outlook connectivity. For hourly employees, they were using Office 365 K plans, which do not allow full Outlook connectivity (and they further disabled IMAP and POP3, meaning OWA only).
To solve this we discussed a few options:
- Changing the ADFS login page to include additional logic for user type and location determination.
- Publishing ADFS with ISA / TMG, use TMG forms authentication and modify the configuration of TMG to disable certain users from accessing ADFS.
Obviously the first option had much more customization capabilities, but the second option was supported out of the box. It was determined to use the second option.
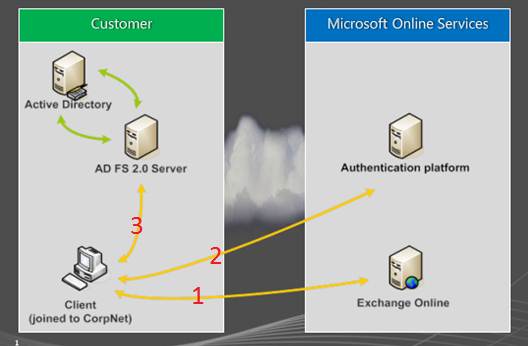
How do Office 365 and ADFS work together? Borrowing and image from: http://maso.dk/2011/06/01/how-does-adfs-work-with-office-365/, we see that the in step 3, the client workstation needs to access ADFS for authentication. In most cases ADFS is published to the internet and this is where we chose to put Microsoft Forefront Threat Management Gateway 2010 (TMG).
How to setup TMG to restrict access to ADFS for Active Directory (AD) Groups of users:
Requirements before setup:
- ADFS must be using integrated or basic authentication (no forms).
- TMG will need a cert with the ADFS public name (or a wildcard cert)
- TMG must answer as the same name as the ADFS cert and the "public" name of the ADFS server.
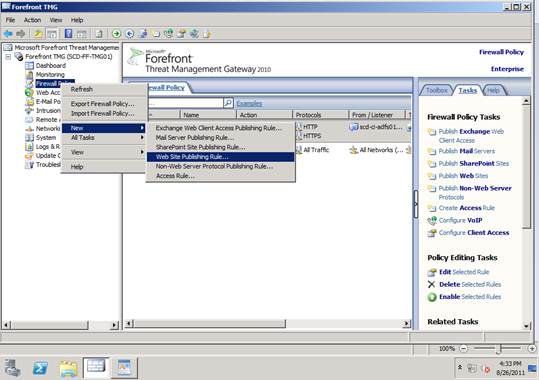
Step 1. In TMG, in the Firewall Node, click New --> Publish Web Site.
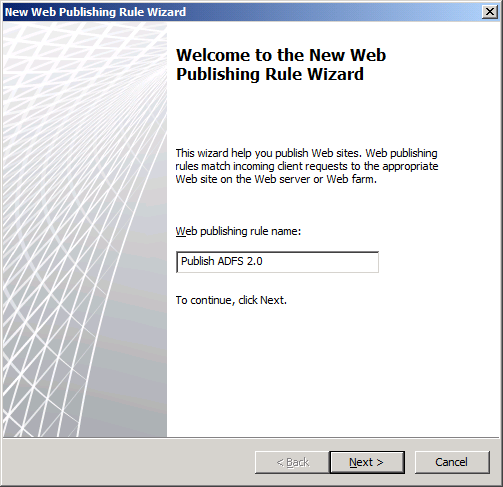
Step 2. Name the rule.
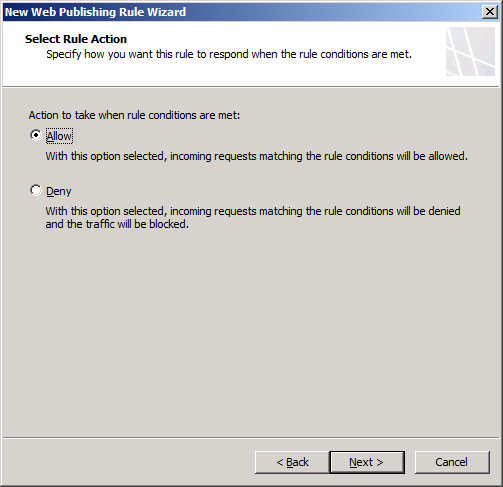
Step 3. Set the action to Allow.
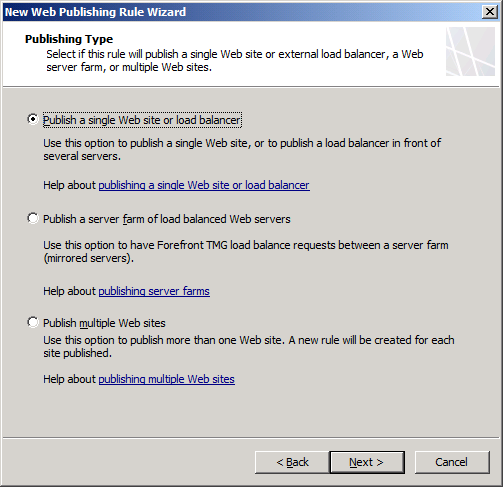
Step 4. Select Publish a single web site or load balancer.
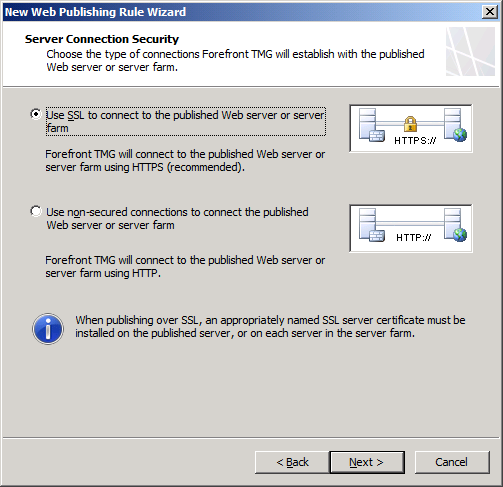
Step 5. Select SSL.
Step 6. Use the correct internal name and you will need to put in the IP address of the internal server or use it’s computer name.
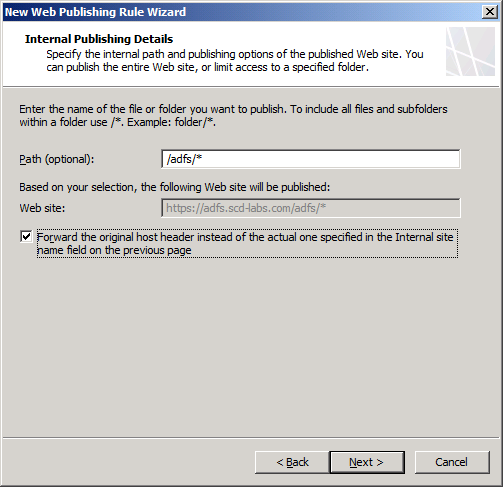
Step 7. For security reasons, type the path of /adfs/*
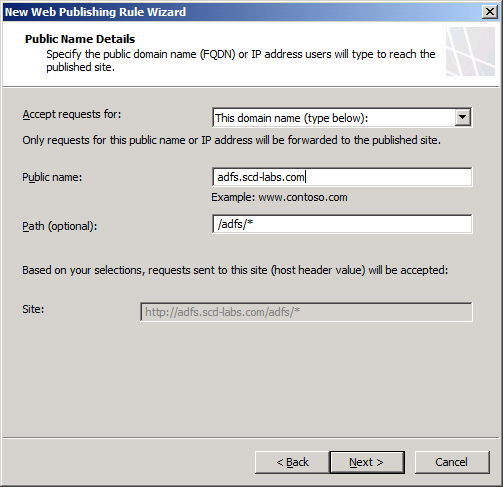
Step 8. Type the correct public name and the path /adfs/*
Step 9. Create a listener, if one does not exist that uses forms based authentication listens on port 443 and uses the SSL certificate that matches the name.
Step 10. Select NTLM authentication for the ADFS server that TMG is publishing.
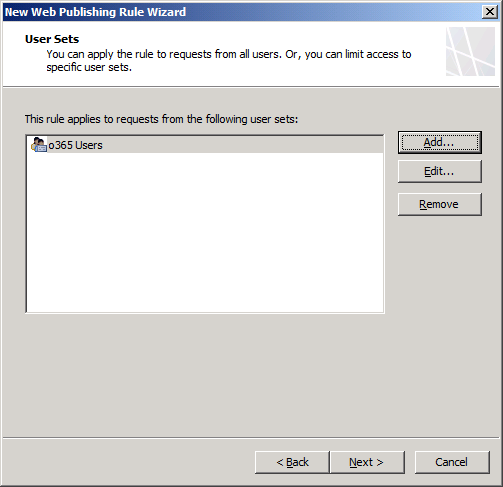
Step 11. Select only the user groups that you want to allow authentication externally (exclude the hourly workers).
Step 12. Complete the wizard.
Step 13. Configure the HTTP protocol properties on the rule you just created.
Step 14. Unchecked Verify normalization and Block high bit characters.
Step 15. Click OK on the Configure HTTP policy rule dialog.
Step 16. Modify the properties of the rule you just created.
Step 17. Uncheck Apply link translation to this rule.
Step 18. Click OK, apply the TMG changes and test after the changes have taken effect.
Authors:
Kevin Saye, Security TSP – Microsoft
Timothy Knight, Consultant – Slalom Consulting