Azure: Providing Admin Consent to Registered Application
Background
The requirement was about adding a new Task in Planner, which is part of Office 365. Now for any adding Task, we have to traverse through Groups, then Bucket and then inside any defined Bucket we can create a Task.
In order to perform all these, authentication and token generation part have to be in place because using JWT tokens only we are going to interact with our application, which is registered via App Registrations under the Azure portal.
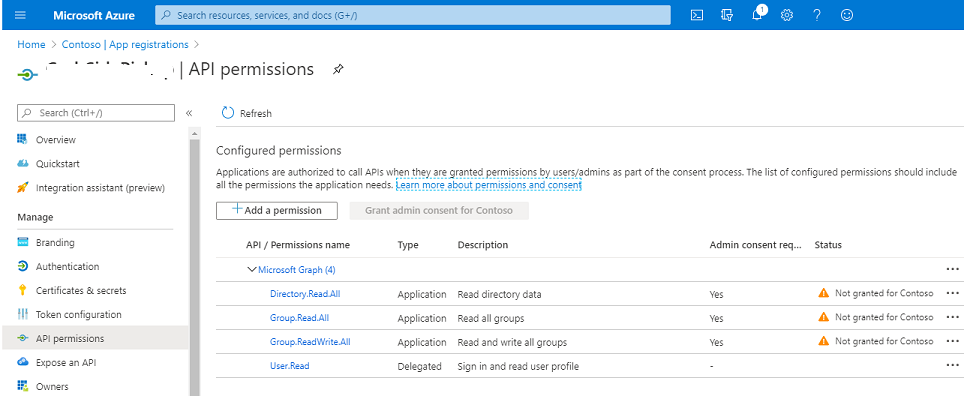
Here is the snapshot of how API permissions look like after registration of app:
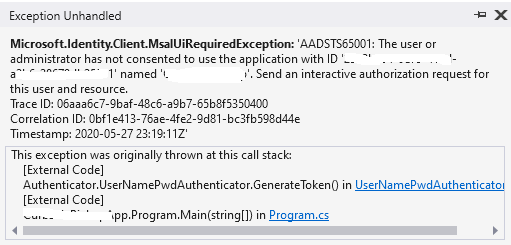
Now with everything in place, when I tried to launch my application from Visual Studio, I got the below error:
Which means that in order to access the registered application, few consents are required. Now how to provide this consent and what this consent is required for?
Analysis
If you will closely see the first screenshot having API permissions, you will notice that for performing the Read and WriteAll operations under Microsoft Graph, Admin consent is required but it is not granted [Just to brief on these Read/WriteAll, these are required in order to perform any operations under Planner].
So, how to provide this consent and who will provide this?
Solution
Well, this consent would be provided by the admin of the application by simply hitting an URL in his browser. This URL would contain TenantId as well as ClientId as follows:
https://login.microsoftonline.com/\<TenantId>/adminconsent?client_id=<ClientId>
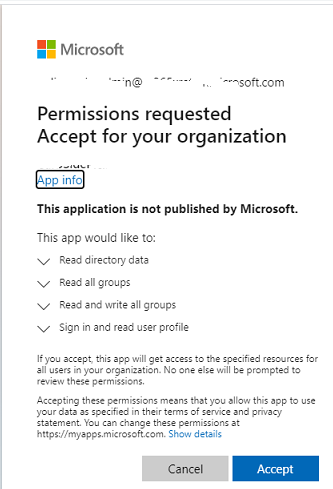
So, as soon as proper URL is entered into the browser, below dialog will pop up:
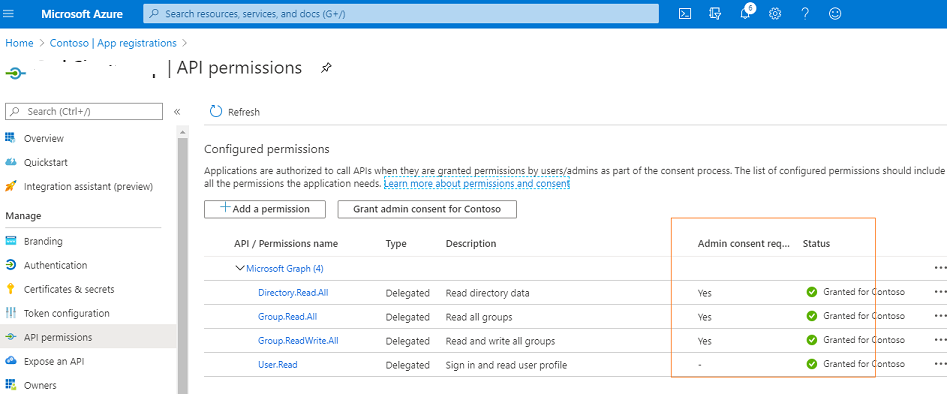
As soon as Admin clicks on Accept button, all the consents would be granted and this can be verified by going back to API permissions page on the Azure portal as shown below:
Happy learning!