Microsoft WSUS (Part 1)
Introduction
The information in this article applies to WSUS 3.0 SP2 and later.
WSUS is a zero-cost solution, used for the distribution of updates (critical and security) in an organization. WSUS enables administrators to manage and distribute updates of operating systems and Microsoft applications. Updates are made automatically and manually.
You can specify the time and date on which updates can be installed, and applications that will make updates. According to the rules that apply updates are configured by using the WSUS management console and group policy. This solution does not distribute and 3rd party patches, it is necessary for management tools such as Microsoft System Center advanced Essentials or Microsoft System Center Configuration Manager 2007 SP2 R3.
WSUS 3.0 SP2 comes with support for Windows Server 2008 R2, Windows 7, BranchCache, auto-approval rules with deadlines and the ability to sort the target groups in alphabetical order. A single WSUS 3.0 SP2 server supports up to 25,000 clients, for 50,000 clients using 2x WSUS servers back to back with a Standard Microsoft SQL server.
Some Architecting & Implementing
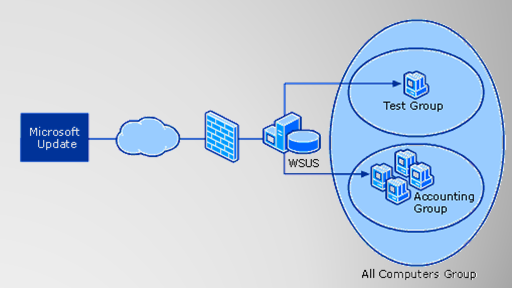
1. Simple Architecture
— Single, well-connected site
◦ WSUS Updates from Microsoft Update
◦ Clients update from WSUS
— Single server can handle 25,000 clients
2. Simple, with Groups Architecture
— Largest use case in production today
— Driving forces to move to Machine Groups:
◦ Differing patching requirements or schedules
◦ Test groups
◦ Servers vs. Workstations
◦ Politics
— Not necessarily used for load distribution
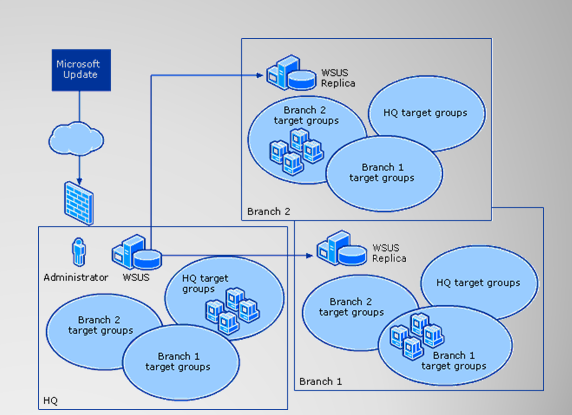
3- Centralized Architecture
— Downstream servers are replicas of primary server
— Little downstream control over servers
◦ Downstream admins drop machines into predefined groups
◦ All update approvals and schedule done at primary server
WSUS Chaining
— Chaining involves downstream servers getting updates (and sometimes Group data) from upstream servers
— Options for chaining
◦ Distributed vs. Centralized model
◦ “Autonomous Mode” vs. “Replica Mode”
— Chaining solves the problem of “MESH” or “Fully Independent” architectures
◦ Wastes resources and bandwidth
◦ Not that some situations don’t mandate “MESH” or “Fully Independent”
architectures.
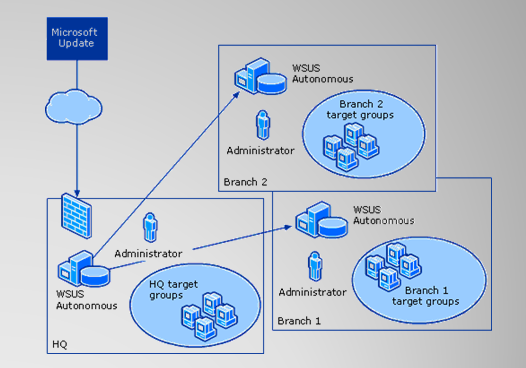
4. Distributed Architecture
— Downstream servers obtain updates from primary server, except:
◦ Update approvals do not flow down. Assigned at each site individually.
◦ Downstream admins have greater control. Can create groups and assign approvals.
— Used for distribution rather than control of updates
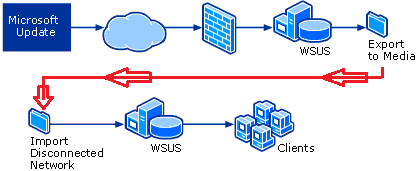
5- Disconnected Architecture
— Many environments don’t have Internet connectivity.
◦ Test/dev, government, classified, air gap environments
— Data must be imported from “the outside”
◦ Any the previous architectures will work
— Manual import process required
◦ Gives CM/QA/Security the option to review updates prior to bringing “inside”.
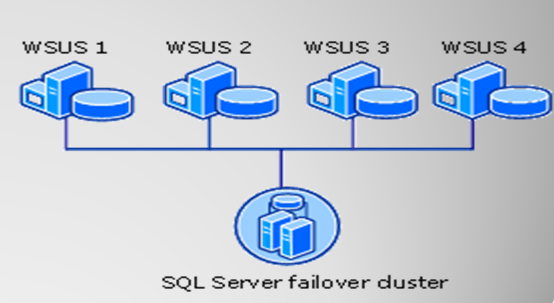
6- High Availability Architecture
— WSUS 3.0 includes native support for high availability
◦ NLB Clusters connect multiple WSUS web servers via a single cluster IP
◦ SQL Cluster manages the database
◦ No single point of failure
This design is useful for availability, but does little for performance.
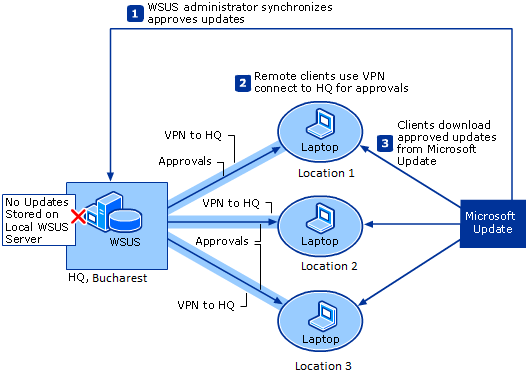
5- WSUS Update storage sites
- Store update sites can be made on other servers and remote, recommended for locations with a small number of users connected to a network limited WAN but with a stable connection to the Internet.
Overview
Approval and Installation of updates
Updates can be aprobabate initially for one or more workstations in a workgroup. Test stations in the group will contact the WSUS server in the urmtoarele 24 hours, after that period, the rate of success when you install the update, you can check the WSUS reports. If the tests associated with success, updates can be approved for the rest of the Group of computers within the organization.
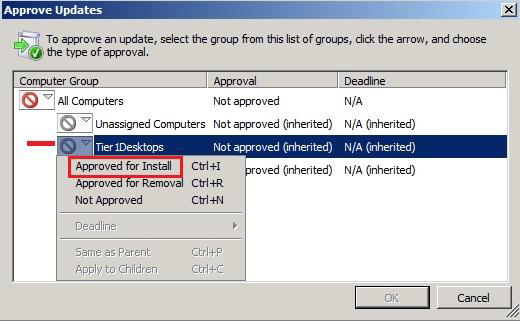
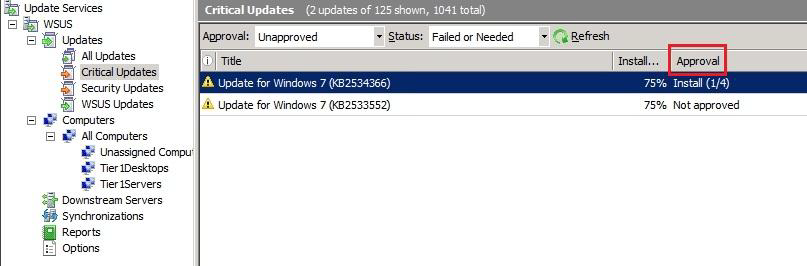
In the WSUS console, select update or updates you want, and then Approve option:
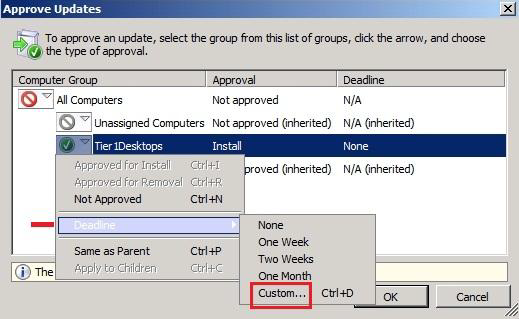
To select the desired computer group and Approved for Install:
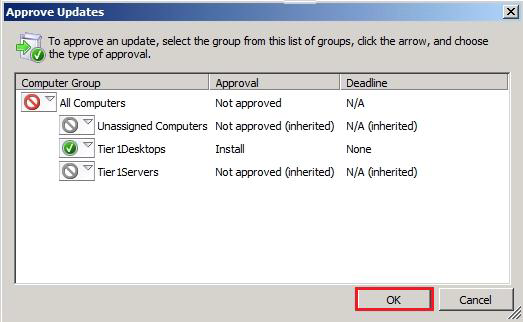
The Update has been approved for installation:
In the WSUS console, the update has been approved for one of the existing computer groups (1/4):
Quick Approval of the update sites
Select an update from the list to Approve:
Choose the desired category and Custom:
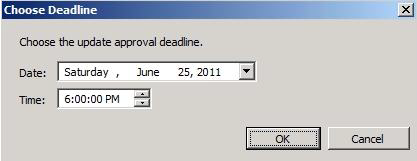
Choose a date on which the update should be installed:
The Update has been approved for installation:
Approval of Automatic Update
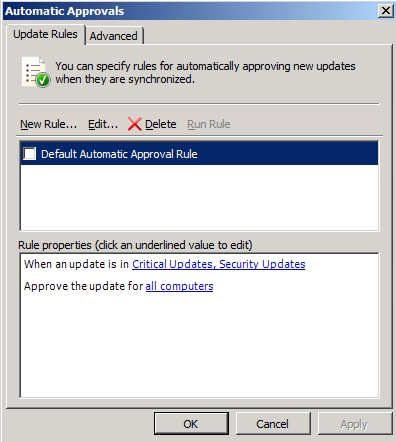
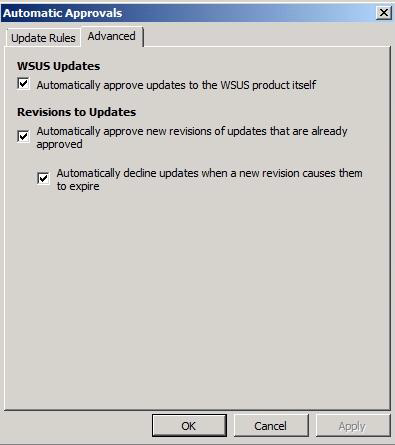
In the server management console, select the WSUS Automatic Approvals:
Natively, there is a single update policy, but new ones can be customized:
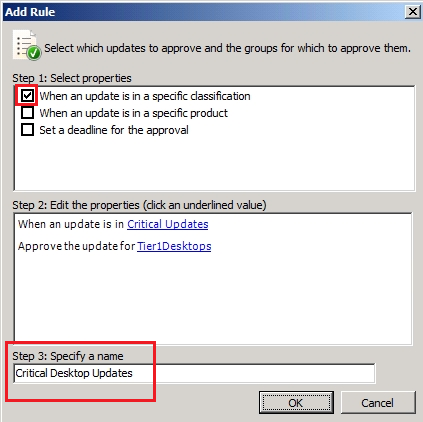
Select The New Rule:
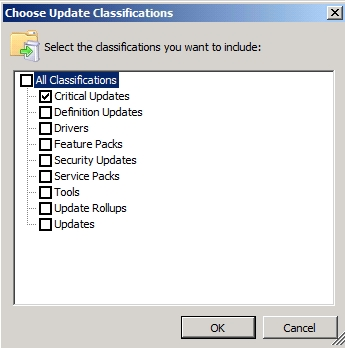
Select The Critical Updates:
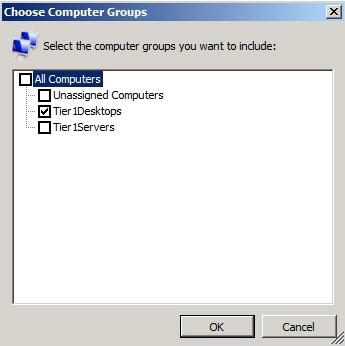
Choose the computer you want to Tier1Desktops:
Select the category and classification, we set a name, such as Critical Desktop Updates:
The new rule was created successfully, select and OK:
Bandwidth
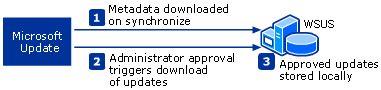
Your WSUS server allows the download-area type metadata information before downloading the update sites. Updates are downloaded immediately after the approval, which help save bandwidth and the space on your hard disk. Updates can be tested before being installed on the Windows clients.
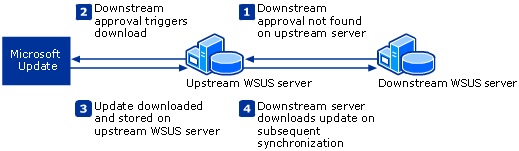
Below is presented a way to download the update sites using multiple WSUS servers (if you want such an architecture in the future):
Email notification setting
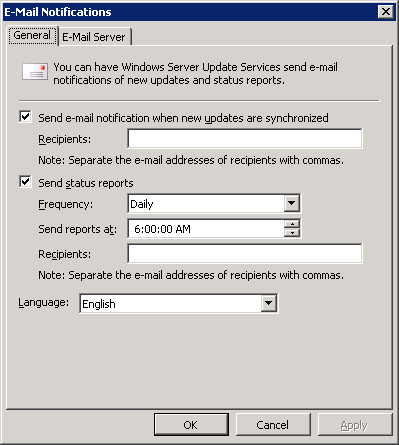
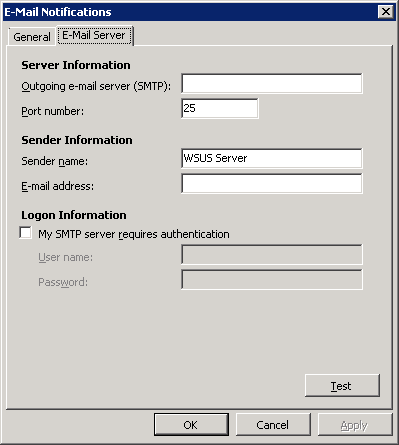
WSUS server can be configured to send notifications by e-mail of new updates occurred or daily or monthly detailed reports about the WSUS network.
Notices will be sent every time the WSUS server synchronizes its new updates. Notices shall include information on the downstream WSUS servers.
Customizing the WSUS administration console
You can configure the space on the WSUS administration console, displaying information about the status update and WSUS clients.
Update of the classification
Classification Updates
|
Description
|
Critical Updates
|
Fixes of problems specific to solutions.
|
Updated definitions
|
Updates of virus definitions.
|
Drivers |
Software components designed to support new types of hardware.
|
Feature packs (Features)
|
New product launches gathered under a future product.
|
Security updates
|
Fixes of specific solutions to security issues.
|
Service Packs (service packs)
|
Cumulative packages that contain critical fixes and security updates, and a limited number of updates at the request of clients.
|
Utilities |
Utilities or features that come in through a task or set of tasks. |
Cumulative updates
|
Cumulative packages fixes, critical updates Security and implemented together.
|
Updates |
Fixes to specific problems and solutions addressed to non-critical and non-security.
|
Managing WSUS server from the command line
Wsusutil command is used in the administration of the WSUS server and is in the WSUSInstallDir\Tools folder, the command may be rolled under credentiale. Below are listed and described the commands that can be run from the command line:
| Command | Description |
| configuressl
|
Updating the registry keys on the WSUS server after IIS configuration was changed.
|
| healthmonitoring | Configures health monitoring values in the database. If new values are not specified, the current values are displayed.
|
| export | Part of the export/import process used to synchronize a downstream WSUS without using a network connection. Exports update metadata to an export package file. You cannot use this parameter to export update files, update approvals, or server settings.
|
| import | The second part of the export/import process. Imports update metadata to a server from an export package file created on another WSUS server. This synchronizes the destination WSUS server without using a network connection.
|
| movecontent | Changes the file system location where the WSUS server stores update files, and optionally copies any update files from the old location to the new location
|
| listfrontendservers | Lists the front-end servers related to this WSUS server.
|
| deletefrontendserver | Deletes the specified front-end server from the WSUS database.
|
| checkhealth | Checks the health of the WSUS server. Results will appear in the Application Event log.
|
| reset | Checks that every update metadata row in the database has corresponding update files stored in the file system. If update files are missing or have been corrupted, downloads the update files again.
|
| listinactiveapprovals | Returns a list of update titles with approvals that are in a permanently inactive state because of a change in server language settings.
|
| removeinactiveapprovals | Removes approvals for updates that are in a permanently inactive state because of a change in WSUS server language settings.
|
| usecustomwebsite | Changes the port number used by the WSUS Web services from 80 to 8530 or vice versa.
|