Microsoft WSUS 3.0 SP2 - Part 2
Status update sites
Status update sites can be accessed from the WSUS console. By using filters you can find a status update on a particular station, you can find out the status of several stations in the Group of Computers X.
Status |
Description |
Installed
|
The update is installed on the system.
|
Necessary |
Making reference to the status of workstations, in the column Needed/Required is specified that the updates are compatible with work stations. A positive result indicates that updates have been approved but have not been installed on the Windows, the following may be true in the event that an update is required: -Updates have been approved for installation, but the stations have not contacted the WSUS server, as was done this change. -Updates have been downloaded and installed, but the stations have not contacted the WSUS server, as was done this change. -Updates have been downloaded and installed but requires restart working stations, before the changes to be made. -Updates have been downloaded on work stations, but have not been installed. -Updates are not downloaded or installed on workstations.
|
Installed/Not Applicable
|
With reference to the status of workstations, installing or not applicable
|
No Status
|
Workstations have not contacted the WSUS server since the last synchronization. |
Failed |
An error was detected in an installation or detection for updates on the station.
|
Last Contacted
|
The date on which the working stations have contacted the WSUS server the last time.
|
Create Reports
Reports can provide detailed information on monitoring update, Workstations and Servers downstream. Generate reports for a large number of stations or updates can provide a high consumption of resources (RAM, processor, etc.). For such reports recommend their generation to another downstream WSUS server.
Report Name
|
Function |
Software updates reports
|
View the status of updates.
|
Reports for workstations
|
View your workstations.
|
Synchronization reports
|
View the results of the last synchronization.
|
Software updates reports
Reports of security updates provides detailed information relating to them.
Can be run in 4 ways:
- Summary (Summary).
- detailed (Detailed).
- Tabular.
- Tabular for approval of updates (Tabular for approved updates).
They can also be filtered according to the classification, product, and the selected station status update. Frequency synchronization of a client with the WSUS server is made once the native 22 hours, the frequency can be changed in the WSUS console.
From the command line, you can run wuauclt /detectnow, forcing client detection by the WSUS server.
Configuration of policy GPOs to automate the installation of security updates for groups of computers in WSUS
Microsoft recommends installing all security updates in a test environment before deploying them into production environment.
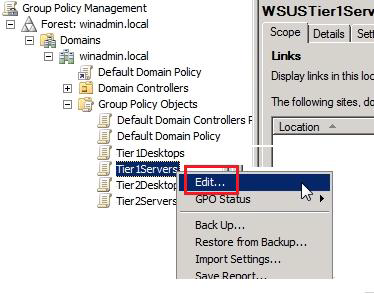
Created security policy "Tier1Desktop", group of computers "Tier1Desktop" in the WSUS console (see picture below):
"Tier1Desktop" is a group of test computers from the WSUS console, addressable test stations are assigned, they are supposed to be updated and monitored for 1 week. As a result of these monitoring stations, administrators can see if any changes to the operating system (Windows XP and Windows 7) and at the level of applications that are installed on these test stations:
If after applying the security updates on test stations there are changes to the operating system level or at the level of applications will take immediate steps to uninstall the updates that have produced these incidents and will analyse the causes that led to this behavior. In the situation where you cannot identify/resolve this problem will be to open a support case to the manufacturer (Microsoft).
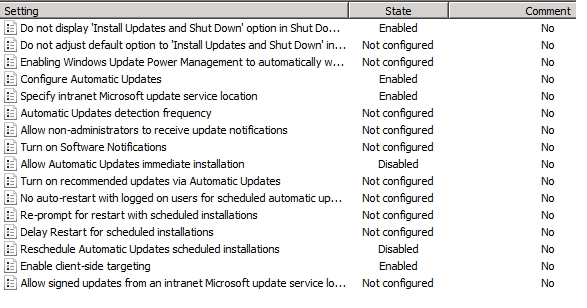
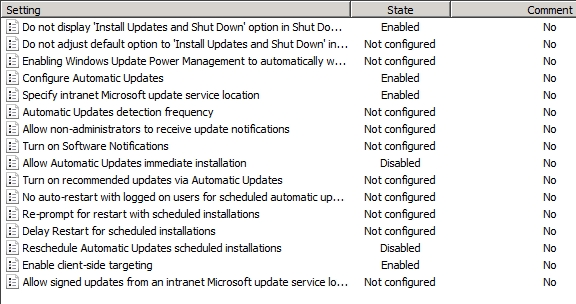
"Tier1Desktop" policy for test stations, were approved with the following security policy:
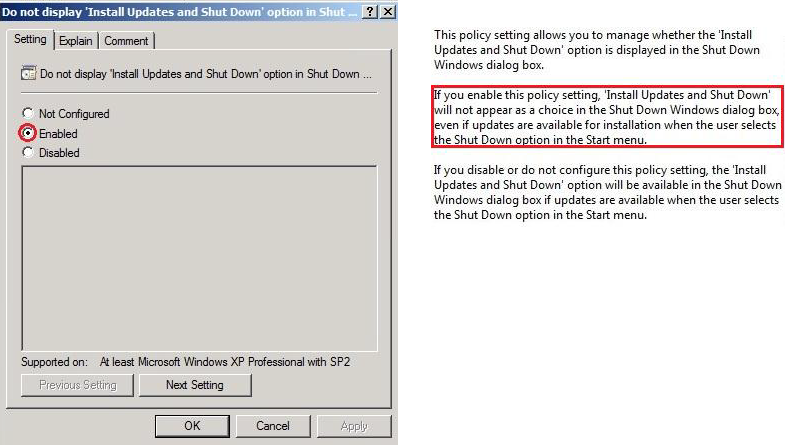
Do not display ‘Install Updates and Shut Down’ option in Shut Down Windows dialog box
This policy has been chosen for a strict control on update, administrators with the ability to install*
Configure Automatic Updates:
To download the update, the example was chosen Monday at 1: 00 AM, offering time/test to make updates and to report the correct in the WSUS console:
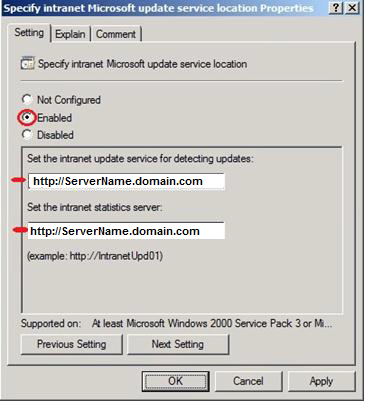
Specify intranet Microsoft update service location:
Specify the location where the internal stations will download latest updates http://servername.domain.com/
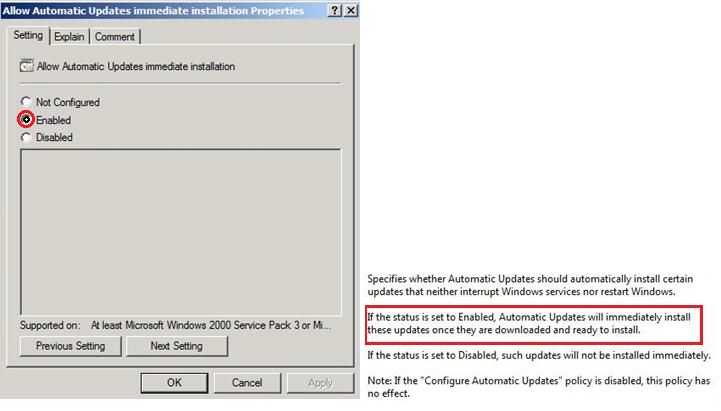
Allow Automatic Updates immediate installation:
An optional setting that offers control over downloading the update, which is automatically installed.
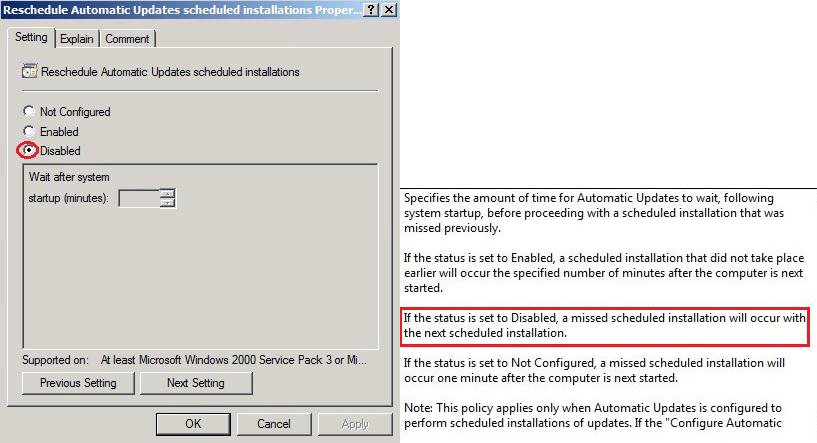
Reschedule Automatic Updates scheduled installations:
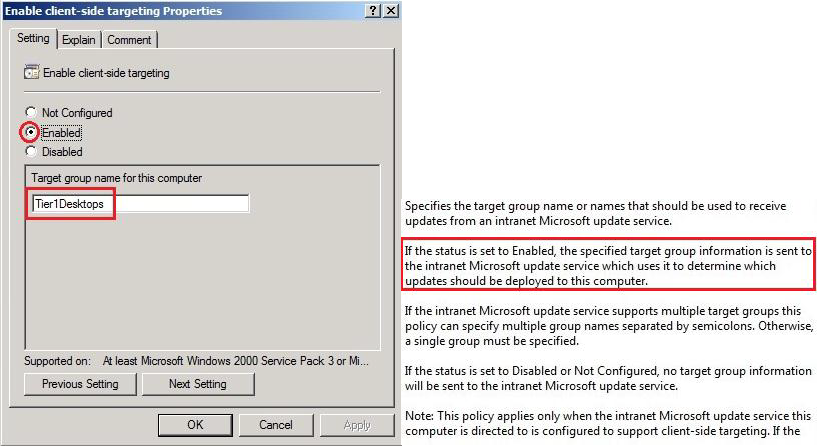
Enable client-side targeting:
This feature allows you to select direct Tier1Desktops group in WSUS console, updates are supposed to be installed only on test stations in the group.
Below are exemplified group policies chosen for Tier1Desktops test stations:
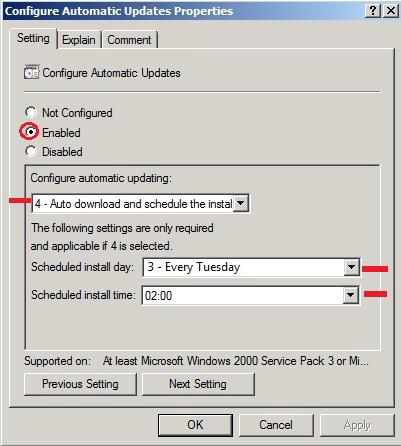
"Tier1Servers" policy for test servers, the following were approved: security policies
Do not display ‘Install Updates and Shut Down’ option in Shut Down Windows dialog box:
This policy has been chosen for strict control over update, thus having administrators can manually install updates:
Configure Automatic Updates
To download the update, the example was chosen on Tuesday at 2:00 AM, giving you time to test servers to make updates and to report correct in the WSUS console:
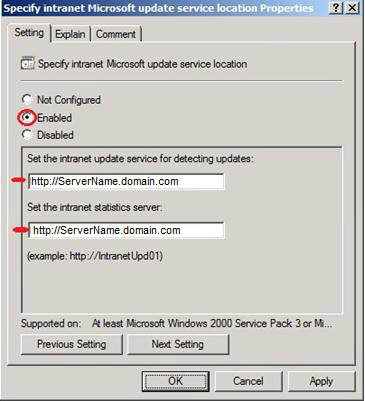
Specify intranet Microsoft update service location:
Specify the location where the internal servers will download latest updates http://servername.domain.com/
Allow Automatic Updates immediate installation:
An optional setting that offers control over downloading update sites on servers, which are manually installed by WSUS administrators:
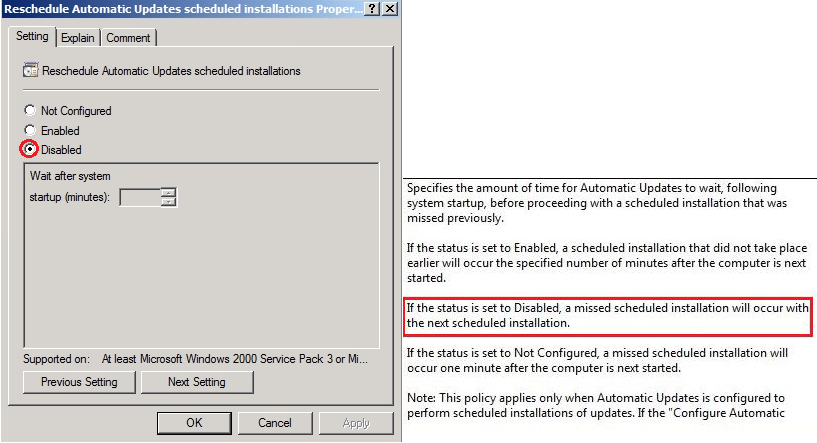
Reschedule Automatic Updates schedule installations:
This option offers to resume downloading update's on the test servers, if the maintenance was outdated:
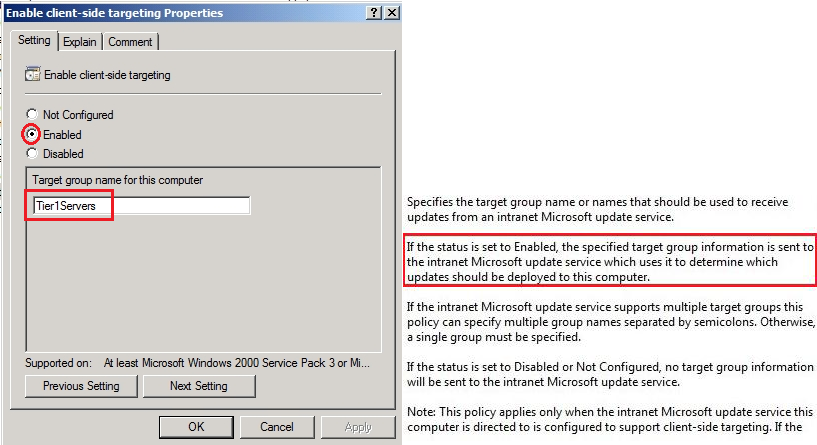
Enable Client-side targeting:
This feature allows you to select direct Tier1Servers group in WSUS console, updates are supposed to be installed only on test servers in the group.
Detailed above are selected for group policies – Tier1Servers: test servers
"Tier2Desktop" policy for the production environment, the following security policies were approved:
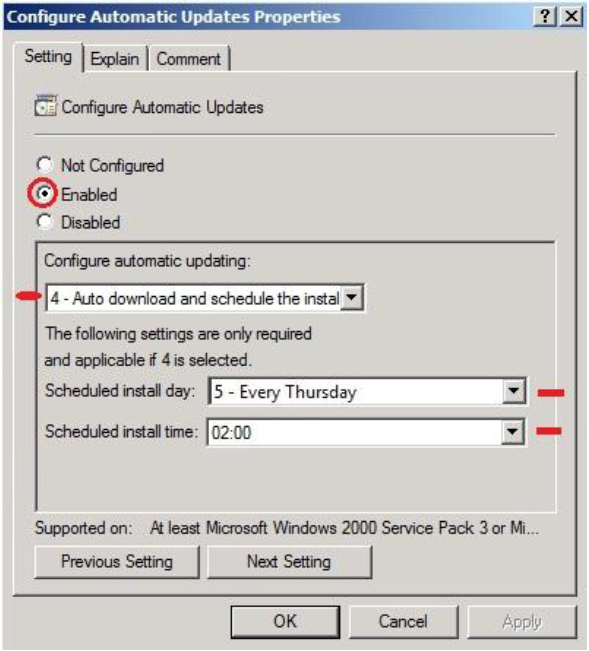
Configure Automatic Updates
To download the update, for example, was selected Thursday at 2: 00 AM, providing for the production stations and install updates.
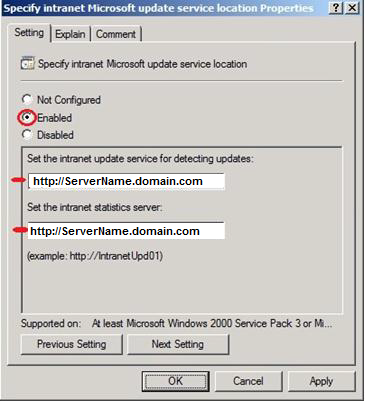
Specify intranet Microsoft update service location:
Specify the location where the internal stations will download latest updates http://ServerName.domain.com
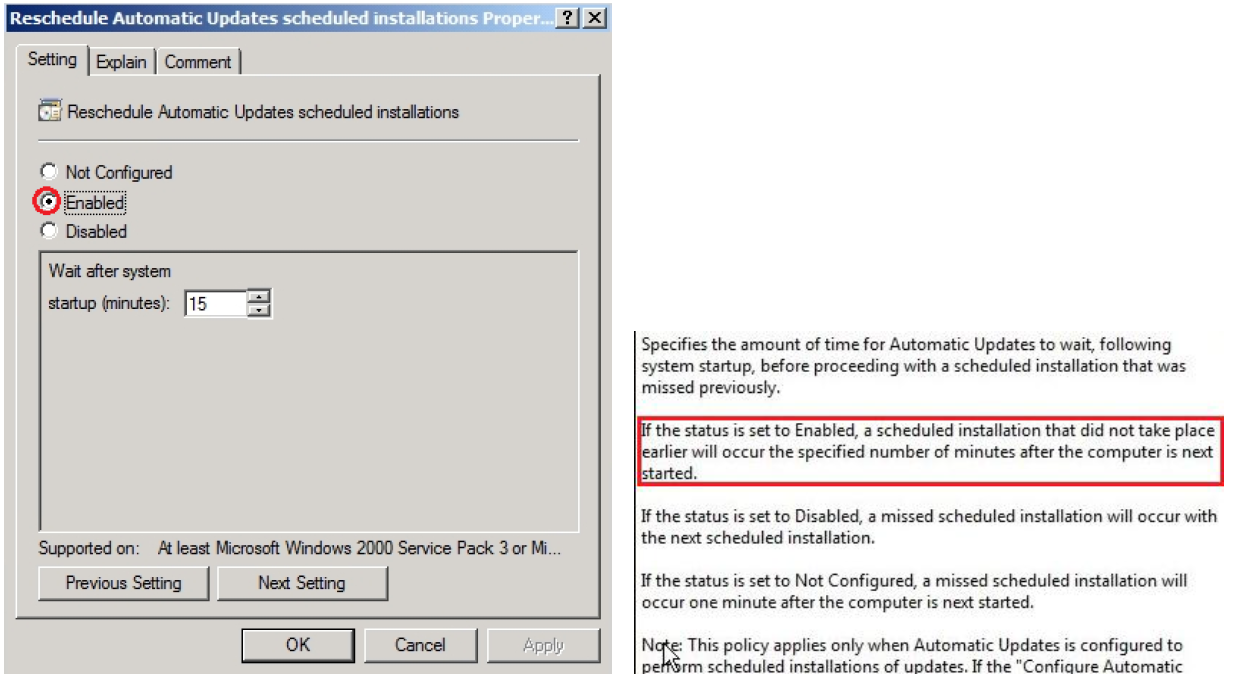
Reschedule Automatic Updates
This option offers downloading resumption check and update sites, the stations of the production, once in 15 minutes:
Microsoft WSUS 3.0 SP2 - Part 1
Microsoft WSUS 3.0 SP2 - Part 3