Azure Monitor 활동 로그는 구독 수준 이벤트에 대한 인사이트를 제공하는 플랫폼 로그입니다. 활동 로그에는 리소스가 수정되거나 배포 오류가 발생하는 경우와 같은 정보가 포함됩니다. Azure Portal에서 활동 로그 를 보거나 PowerShell 및 Azure CLI를 사용하여 항목을 검색할 수 있습니다.
이 문서에서는 활동 로그를 보고 다른 대상으로 보내는 방법에 대한 정보를 제공합니다.
비고
- 활동 로그의 항목은 시스템에서 생성되며 변경하거나 삭제할 수 없습니다.
- 활동 로그의 항목은 가상 머신 다시 시작과 같은 컨트롤 플레인 변경 내용을 나타내며, 모든 비관계형 항목은 Azure 리소스 로그에 기록되어야 합니다.
- 활동 로그의 항목은 일반적으로 변경(만들기, 업데이트 또는 삭제 작업) 또는 시작된 작업의 결과입니다. 리소스의 세부 정보를 읽는 데 중점을 두는 작업은 일반적으로 캡처되지 않습니다.
팁 (조언)
배포 작업 오류에서 이 문서로 전달된 경우 일반적인 Azure 배포 오류 문제 해결을 참조하세요.
활동 로그 내보내기
Azure Monitor>활동 로그로 이동하여 활동 로그 내보내기를 선택합니다.
비고
단일 구독에서 최대 5개의 작업 영역으로 활동 로그를 보낼 수 있습니다.
다음 위치 중 하나 이상에 활동 로그를 보내는 진단 설정을 추가합니다.
- 더 복잡한 쿼리 및 경고를 위한 Log Analytics 작업 영역입니다.
- Azure 외부로 로그를 전달하는 Azure Event Hubs입니다.
- 더 저렴하고 장기적인 보관을 위한 Azure Storage입니다.
진단 설정을 만드는 방법에 대한 자세한 내용은 플랫폼 로그 및 메트릭을 다른 대상으로 전송하는 진단 설정 만들기를 참조하세요.
팁 (조언)
다음과 같은 이점을 위해 활동 로그 데이터를 Log Analytics 작업 영역으로 보냅니다.
- Log Analytics 작업 영역으로 로그를 보내는 작업은 기본 보존 기간 동안 무료로 제공됩니다.
- 최대 12년까지 더 오래 보존하려면 Log Analytics 작업 영역에 로그를 보냅니다.
- Log Analytics 작업 영역으로 내보낸 로그는 Power BI에서 확인할 수 있음
- Log Analytics로 내보낸 활동 로그에 대한 인사이트가 제공됩니다.
Log Analytics 작업 영역으로 보내기
활동 로그를 Log Analytics 작업 영역으로 보내 Azure Monitor 로그 기능을 사용하도록 설정하려면 다음을 수행합니다.
- 활동 로그 데이터를 Azure Monitor에서 수집한 다른 모니터링 데이터와 상호 연결합니다.
- 여러 Azure 구독 및 테넌트에서 로그 항목을 함께 분석할 수 있는 한 위치로 통합합니다.
- 로그 쿼리를 사용하여 복잡한 분석을 수행하고 활동 로그 항목에 대한 심층적인 인사이트를 얻습니다.
- 보다 복잡한 경고 논리를 위해 작업 항목과 함께 로그 검색 경고를 사용합니다.
- 활동 로그 보존 기간보다 오랫동안 활동 로그 항목을 저장합니다.
- Log Analytics 작업 영역에 저장된 활동 로그 데이터에 대한 데이터 수집 또는 보존 요금이 부과되지 않습니다.
- Log Analytics의 기본 보존 기간은 90일입니다.
Log Analytics 작업 영역의 활동 로그 데이터는 AzureActivity에서 로그 쿼리를 사용하여 검색할 수 있는 라는 테이블에 저장됩니다. 이 테이블의 구조는 로그 항목의 범주에 따라 달라집니다. 테이블 속성에 대한 설명은 Azure Monitor 데이터 참조를 참조하세요.
예를 들어 각 범주에 대한 활동 로그 레코드 수를 보려면 다음 쿼리를 사용합니다.
AzureActivity
| summarize count() by CategoryValue
관리 범주에 있는 모든 레코드를 검색하려면 다음 쿼리를 사용합니다.
AzureActivity
| where CategoryValue == "Administrative"
중요합니다
일부 시나리오에서는 AzureActivity 필드의 값에 해당하는 값과 다른 대/소문자를 가질 수 있습니다. AzureActivity에서 데이터를 쿼리하여 문자열 비교에 대/소문자를 구분하지 않는 연산자를 사용하거나 스칼라 함수를 사용하여 비교 전에 필드를 균일한 대/소문자로 강제 적용할 때 주의해야 합니다. 예를 들어 문자열 비교를 수행할 때 필드의 tolower() 함수를 사용하여 항상 소문자 또는 =~ 연산자로 강제 적용합니다.
Azure Event Hubs로 전송
타사 SIEM 또는 다른 로그 분석 솔루션과 같은 Azure 외부의 항목을 보내려면 활동 로그를 Azure Event Hubs로 보냅니다. 이벤트 허브의 활동 로그 이벤트는 각 페이로드의 레코드가 포함된 records 요소와 함께 JSON 형식으로 사용됩니다. 스키마는 범주에 따라 다르며 Azure 활동 로그 이벤트 스키마에 설명되어 있습니다.
다음 샘플 출력 데이터는 활동 로그에 대한 이벤트 허브에서 가져온 것입니다.
{
"records": [
{
"time": "2019-01-21T22:14:26.9792776Z",
"resourceId": "/subscriptions/s1/resourceGroups/MSSupportGroup/providers/microsoft.support/supporttickets/115012112305841",
"operationName": "microsoft.support/supporttickets/write",
"category": "Write",
"resultType": "Success",
"resultSignature": "Succeeded.Created",
"durationMs": 2826,
"callerIpAddress": "111.111.111.11",
"correlationId": "aaaa0000-bb11-2222-33cc-444444dddddd",
"identity": {
"authorization": {
"scope": "/subscriptions/s1/resourceGroups/MSSupportGroup/providers/microsoft.support/supporttickets/115012112305841",
"action": "microsoft.support/supporttickets/write",
"evidence": {
"role": "Subscription Admin"
}
},
"claims": {
"aud": "https://management.core.windows.net/",
"iss": "https://sts.windows.net/72f988bf-86f1-41af-91ab-2d7cd011db47/",
"iat": "1421876371",
"nbf": "1421876371",
"exp": "1421880271",
"ver": "1.0",
"http://schemas.microsoft.com/identity/claims/tenantid": "ffffffff-eeee-dddd-cccc-bbbbbbbbbbb0",
"http://schemas.microsoft.com/claims/authnmethodsreferences": "pwd",
"http://schemas.microsoft.com/identity/claims/objectidentifier": "2468adf0-8211-44e3-95xq-85137af64708",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn": "admin@contoso.com",
"puid": "20030000801A118C",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier": "9vckmEGF7zDKk1YzIY8k0t1_EAPaXoeHyPRn6f413zM",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname": "John",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname": "Smith",
"name": "John Smith",
"groups": "cacfe77c-e058-4712-83qw-f9b08849fd60,7f71d11d-4c41-4b23-99d2-d32ce7aa621c,31522864-0578-4ea0-9gdc-e66cc564d18c",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name": " admin@contoso.com",
"appid": "00001111-aaaa-2222-bbbb-3333cccc4444",
"appidacr": "2",
"http://schemas.microsoft.com/identity/claims/scope": "user_impersonation",
"http://schemas.microsoft.com/claims/authnclassreference": "1"
}
},
"level": "Information",
"location": "global",
"properties": {
"statusCode": "Created",
"serviceRequestId": "50d5cddb-8ca0-47ad-9b80-6cde2207f97c"
}
}
]
}
Azure Storage에 보내기
감사, 정적 분석 또는 백업을 위해 로그 데이터를 90일 이상 유지하려는 경우 활동 로그를 Azure Storage 계정으로 보냅니다. 이벤트를 90일 이하로 보존해야 하는 경우 스토리지 계정에 대한 보존을 설정할 필요가 없습니다. 활동 로그 이벤트는 90일 동안 Azure 플랫폼에 보존됩니다.
활동 로그를 Azure로 보내면 이벤트가 발생하는 즉시 스토리지 계정에 스토리지 컨테이너가 만들어집니다. 컨테이너의 Blob은 다음과 같은 명명 규칙을 사용합니다.
insights-activity-logs/resourceId=/SUBSCRIPTIONS/{subscription ID}/y={four-digit numeric year}/m={two-digit numeric month}/d={two-digit numeric day}/h={two-digit 24-hour clock hour}/m=00/PT1H.json
예를 들어, 특정 Blob은 다음과 유사한 이름을 가질 수 있습니다.
insights-activity-logs/resourceId=/SUBSCRIPTIONS/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/y=2020/m=06/d=08/h=18/m=00/PT1H.json
각 PT1H.json Blob에는 Blob URL에 지정된 시간 동안 수신된 로그 파일의 이벤트와 함께 JSON 개체가 포함됩니다. 현재 시간 동안 이벤트는 생성된 시기에 관계없이 수신될 때 PT1H.json 파일에 추가됩니다. Blob이 시간당 기준으로 생성되므로 URL m=00의 분 값은 항상 00입니다.
각 이벤트는 다음 형식으로 PT1H.json 파일에 저장됩니다. 이 형식은 공통 최상위 스키마를 사용하지만 활동 로그 스키마에 설명된 대로 범주별로 고유합니다.
{ "time": "2020-06-12T13:07:46.766Z", "resourceId": "/SUBSCRIPTIONS/aaaa0a0a-bb1b-cc2c-dd3d-eeeeee4e4e4e/RESOURCEGROUPS/MY-RESOURCE-GROUP/PROVIDERS/MICROSOFT.COMPUTE/VIRTUALMACHINES/MV-VM-01", "correlationId": "bbbb1111-cc22-3333-44dd-555555eeeeee", "operationName": "Microsoft.Resourcehealth/healthevent/Updated/action", "level": "Information", "resultType": "Updated", "category": "ResourceHealth", "properties": {"eventCategory":"ResourceHealth","eventProperties":{"title":"This virtual machine is starting as requested by an authorized user or process. It will be online shortly.","details":"VirtualMachineStartInitiatedByControlPlane","currentHealthStatus":"Unknown","previousHealthStatus":"Unknown","type":"Downtime","cause":"UserInitiated"}}}
CSV로 내보내기
CSV로 다운로드를 선택하여 Azure Portal을 사용하여 활동 로그를 CSV 파일로 내보냅니다.
중요합니다
로그 항목이 많은 경우 내보내는 데 과도한 시간이 걸릴 수 있습니다. 성능을 향상시키려면 내보내기의 시간 범위를 줄입니다. Azure Portal에서 이 설정은 Timespan 설정으로 설정됩니다.
다음 예제와 같이 PowerShell 또는 Azure CLI를 사용하여 활동 로그를 CSV 파일로 내보낼 수도 있습니다.
az monitor activity-log list --start-time "2024-03-01T00:00:00Z" --end-time "2024-03-15T23:59:59Z" --max-items 1000 > activitylog.json
Get-AzActivityLog -StartTime 2021-12-01T10:30 -EndTime 2022-01-14T11:30 | Export-csv operations_logs.csv
다음 예제 PowerShell 스크립트는 각각 별도의 파일에 저장되는 1시간 간격으로 활동 로그를 CSV 파일로 내보냅니다.
# Parameters
$subscriptionId = "Subscription ID here" # Replace with your subscription ID
$startTime = [datetime]"2025-05-08T00:00:00" # Adjust as needed
$endTime = [datetime]"2025-05-08T12:00:00" # Adjust as needed
$outputFolder = "\Logs" # Change path as needed
# Ensure output folder exists
if (-not (Test-Path $outputFolder)) {
New-Item -Path $outputFolder -ItemType Directory
}
# Set subscription context
Set-AzContext -SubscriptionId $subscriptionId
# Loop through 1-hour intervals
$currentStart = $startTime
while ($currentStart -lt $endTime) {
$currentEnd = $currentStart.AddHours(1)
$timestamp = $currentStart.ToString("yyyyMMdd-HHmm")
$csvFile = Join-Path $outputFolder "ActivityLog_$timestamp.csv"
Write-Host "Fetching logs from $currentStart to $currentEnd..."
Get-AzActivityLog -StartTime $currentStart -EndTime $currentEnd |
Export-Csv -Path $csvFile -NoTypeInformation
$currentStart = $currentEnd
}
Write-Host "Export completed. Files saved to $outputFolder."
활동 로그 이벤트를 검색하는 다른 방법
다음 방법을 사용하여 활동 로그 이벤트에 액세스할 수도 있습니다.
- Get-AzLog cmdlet을 사용하여 PowerShell에서 활동 로그를 검색합니다. Azure Monitor PowerShell 샘플을 참조하세요.
- az monitor activity-log를 사용하여 CLI에서 활동 로그를 검색합니다. Azure Monitor CLI 샘플을 참조하세요.
- Azure Monitor REST API를 사용하여 REST 클라이언트에서 활동 로그를 검색합니다.
레거시 수집 방법
비고
Azure 활동 로그 솔루션은 활동 로그를 Log Analytics로 전달하는 데 사용되었습니다. 이 솔루션은 2026년 9월 15일에 사용 중지되며 자동으로 진단 설정으로 변환됩니다.
레거시 수집 방법을 사용하여 활동 로그를 수집하는 경우 다음과 같이 활동 로그를 Log Analytics 작업 영역으로 내보내고데이터 원본 - 삭제 API를 사용하여 레거시 수집을 사용하지 않도록 설정하는 것이 좋습니다.
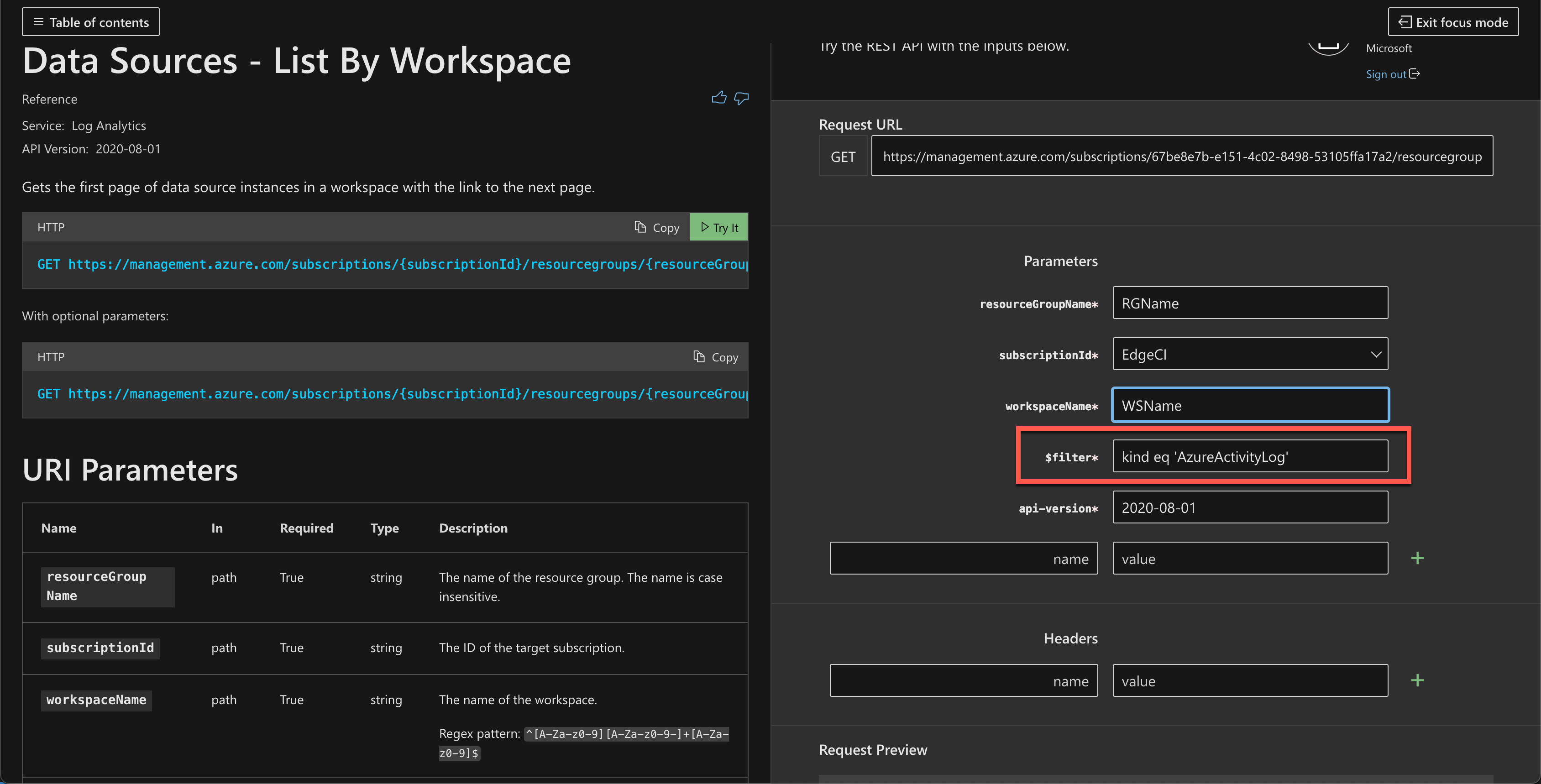
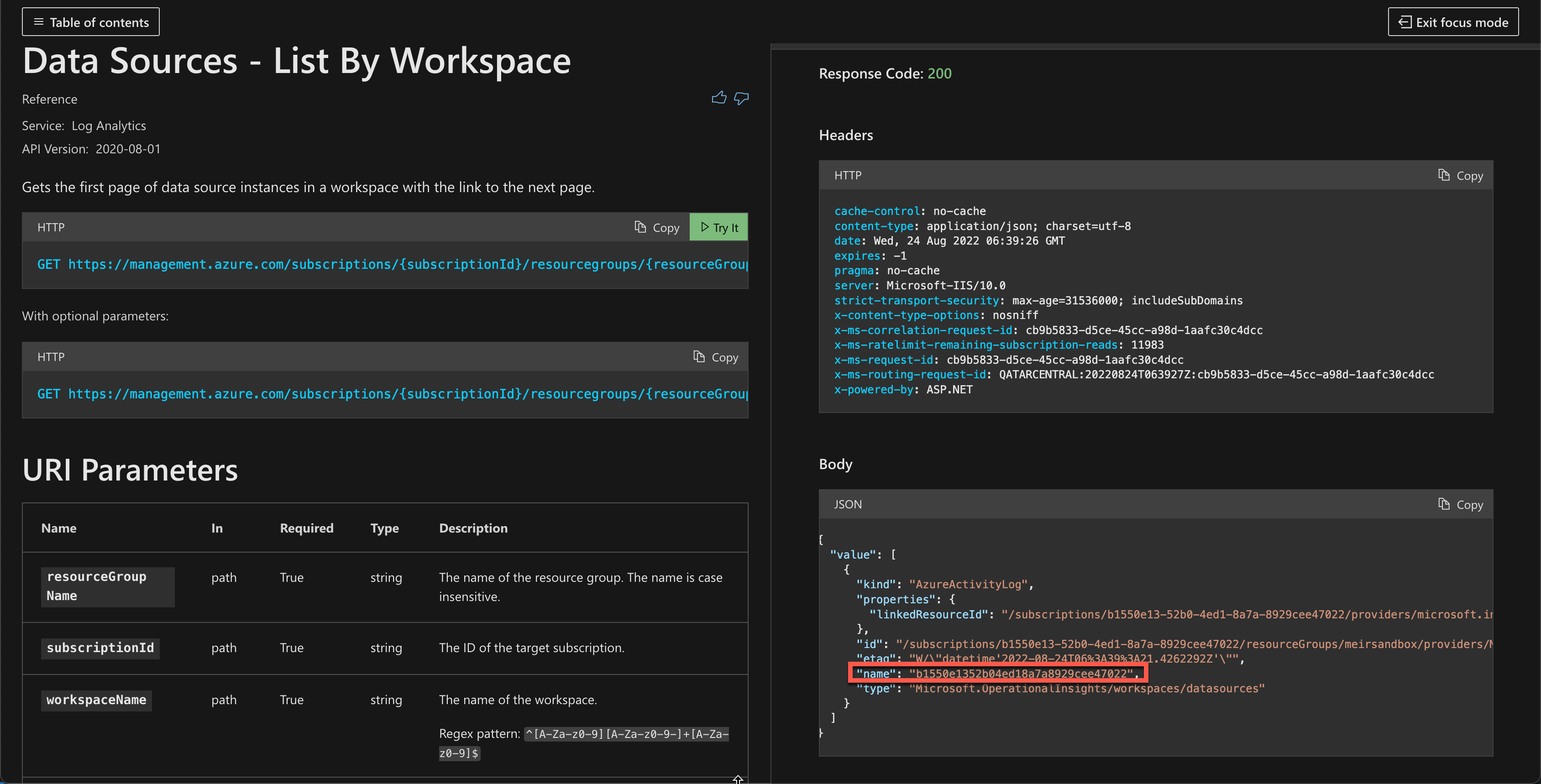
데이터 원본 - 작업 영역별 나열 API를 사용하여 작업 영역에 연결된 모든 데이터 원본을 나열하고,
kind eq 'AzureActivityLog'를 설정하여 활동 로그를 필터링합니다.API 응답에서 사용하지 않도록 설정하려는 연결의 이름을 복사합니다.
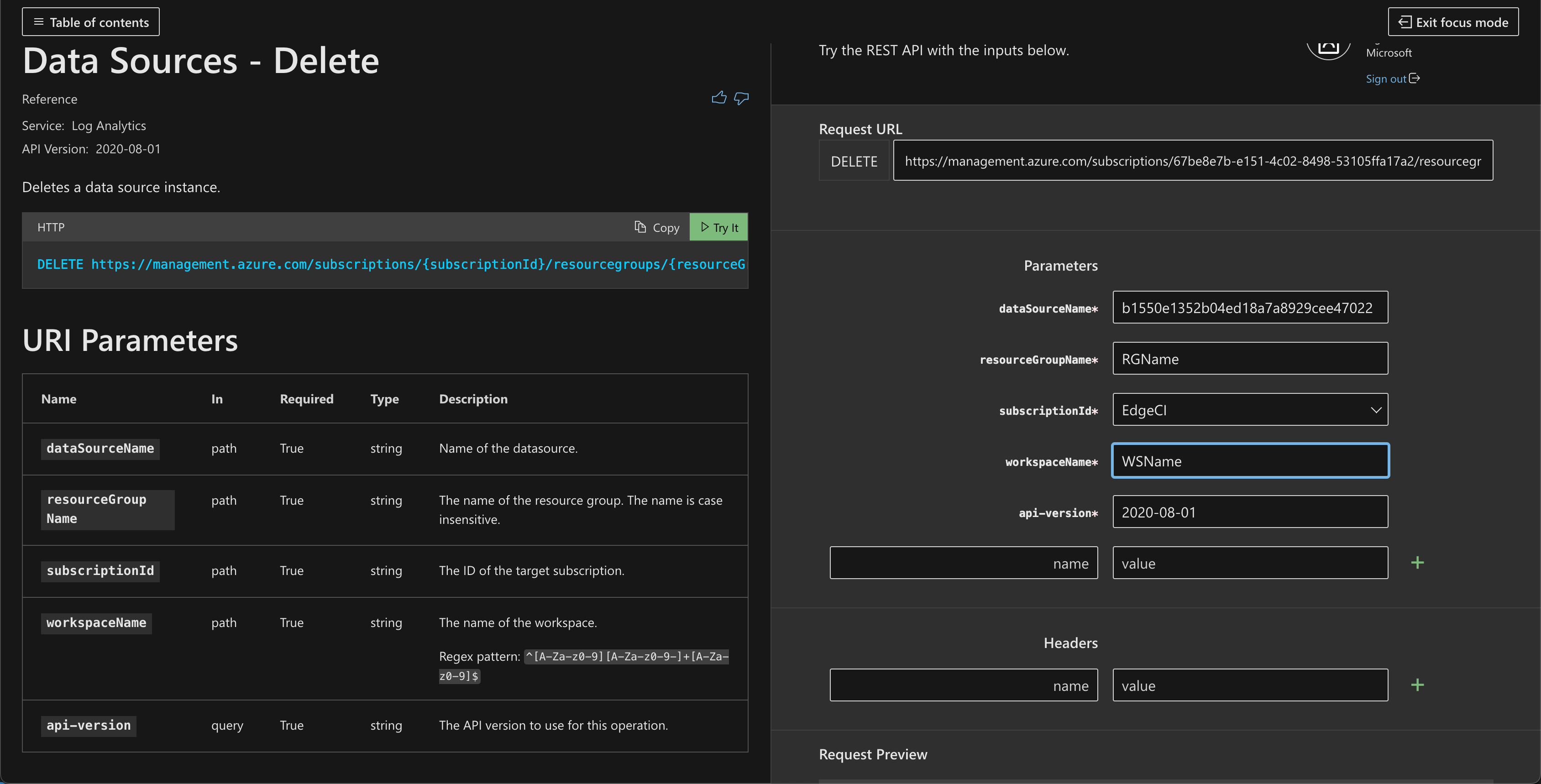
데이터 원본 - 삭제 API를 사용하여 특정 리소스에 대한 활동 로그 수집을 중지합니다.
레거시 로그 프로필 관리(사용 중지)
비고
- 로그 프로필은 활동 로그를 스토리지 계정 및 Event Hubs로 전달하는 데 사용되었습니다. 이 방법은 2026년 9월 15일에 사용 중지됩니다.
- 이 방법을 사용하는 경우 새 로그 프로필 만들기 허용을 중지할 때 2025년 9월 15일 이전에 진단 설정으로 전환합니다.
로그 프로필은 활동 로그를 스토리지 또는 이벤트 허브로 보내는 레거시 방법입니다. 이 방법을 사용하는 경우 더 나은 기능과 리소스 로그의 일관성을 제공하는 진단 설정으로 전환합니다.
로그 프로필이 이미 있는 경우 먼저 기존 로그 프로필을 제거한 다음, 새 로그 프로필을 만들어야 합니다.
Get-AzLogProfile를 사용하여 로그 프로필이 있는지 확인합니다. 로그 프로필이 있으면Name속성을 기록해 두세요.Remove-AzLogProfile을 사용하여Name속성의 값을 사용하여 로그 프로필을 제거합니다.# For example, if the log profile name is 'default' Remove-AzLogProfile -Name "default"Add-AzLogProfile를 사용하여 새 로그 프로필을 만듭니다.Add-AzLogProfile -Name my_log_profile -StorageAccountId /subscriptions/s1/resourceGroups/myrg1/providers/Microsoft.Storage/storageAccounts/my_storage -serviceBusRuleId /subscriptions/s1/resourceGroups/Default-ServiceBus-EastUS/providers/Microsoft.ServiceBus/namespaces/mytestSB/authorizationrules/RootManageSharedAccessKey -Location global,westus,eastus -RetentionInDays 90 -Category Write,Delete,Action재산 필수 설명 이름 예 로그 프로필의 이름입니다. StorageAccountId (스토리지 계정 ID) 아니오 활동 로그를 저장할 스토리지 계정의 리소스 ID입니다. 서비스버스규칙ID 아니오 이벤트 허브를 생성하고자 하는 Service Bus 네임스페이스의 Service Bus 규칙 ID입니다. 이 문자열의 형식은 {service bus resource ID}/authorizationrules/{key name}입니다.위치 예 활동 로그 이벤트를 수집하려는 지역의 쉼표로 구분된 목록입니다. 일일 유지 기간 예 이벤트를 스토리지 계정에 보관해야 하는 일 수(1~365)입니다. 0 값은 로그를 무기한 저장합니다. 카테고리 아니오 수집할 이벤트 범주의 쉼표로 구분된 목록입니다. 가능한 값은 쓰기, 삭제 및 작업입니다.
예제 스크립트
이 샘플 PowerShell 스크립트는 스토리지 계정과 이벤트 허브 모두에 활동 로그를 기록하는 로그 프로필을 만듭니다.
# Settings needed for the new log profile
$logProfileName = "default"
$locations = (Get-AzLocation).Location
$locations += "global"
$subscriptionId = "<your Azure subscription Id>"
$resourceGroupName = "<resource group name your Event Hub belongs to>"
$eventHubNamespace = "<Event Hub namespace>"
$storageAccountName = "<Storage Account name>"
# Build the service bus rule Id from the settings above
$serviceBusRuleId = "/subscriptions/$subscriptionId/resourceGroups/$resourceGroupName/providers/Microsoft.EventHub/namespaces/$eventHubNamespace/authorizationrules/RootManageSharedAccessKey"
# Build the Storage Account Id from the settings above
$storageAccountId = "/subscriptions/$subscriptionId/resourceGroups/$resourceGroupName/providers/Microsoft.Storage/storageAccounts/$storageAccountName"
Add-AzLogProfile -Name $logProfileName -Location $locations -StorageAccountId $storageAccountId -ServiceBusRuleId $serviceBusRuleId
데이터 구조 변경
활동 로그 내보내기 환경은 AzureActivity 테이블의 구조를 일부 변경하여 활동 로그를 보내는 데 사용된 레거시 방법과 동일한 데이터를 보냅니다.
다음 표의 열은 업데이트된 스키마에서 더 이상 사용되지 않습니다. AzureActivity에 여전히 존재하지만 데이터가 없습니다. 이러한 열에 대한 대체는 새로운 것은 아니지만 사용되지 않는 열과 동일한 데이터를 포함합니다. 형식이 다르므로 이를 사용하는 로그 쿼리를 수정해야 할 수 있습니다.
| 활동 로그 JSON | 이전 Log Analytics 열 이름 (사용되지 않음) |
새 Log Analytics 열 이름 | 비고 |
|---|---|---|---|
| 카테고리 | 카테고리 | 카테고리 값 | |
| 상태 값은 success, start, acceptfailure |
활동 상태 JSON과 동일한 값 |
활동 상태 값 값이 succeeded, started, accepted, failed로 변경됩니다. |
유효한 값은 다음과 같이 변경됩니다. |
| 하위 상태 | 활동하위상태 | 활동 하위 상태 값 | |
| 작업이름 | 작전이름 | 작업이름값 | REST API는 작업 이름 값을 지역화합니다. Log Analytics UI는 항상 영어를 표시합니다. |
| 리소스 제공자 이름 | 리소스 제공자 | 자원제공자값 |
중요합니다
경우에 따라 이러한 열의 값이 모두 대문자일 수 있습니다. 이러한 열이 포함된 쿼리가 있는 경우 =~ 연산자를 사용하여 대/소문자를 구분하지 않고 비교합니다.
다음 열이 업데이트된 스키마의 AzureActivity에 추가되었습니다.
Authorization_dClaims_dProperties_d
다음 단계
자세히 알아보기: