Set up user roles and access management
You can assign roles and access management in Microsoft Sustainability Manager based on individual user needs. To provide these enhanced security and privacy capabilities, Microsoft Sustainability Manager uses the role-based security model in Dataverse.
Business units define a security boundary in Dataverse. They segment your users and data across the organization. You can align your structure in Microsoft Sustainability Manager to Dataverse's business units to accomplish your required role-based access.
For more information about role-based security and business units in Dataverse, go to Security concepts in Microsoft Dataverse.
For best practices around deploying Cloud for Sustainability, go to Well-Architected for Microsoft Cloud for Sustainability.
Important
The security roles in Dataverse don't impact Power BI views, so the insights and dashboard in Microsoft Sustainability Manager have the following limitations:
- The dashboard and insights are only governed by organization scope role access.
- The business unit reporting role only impacts report generation access and data. It doesn't apply to dashboard and insights views.
Microsoft Sustainability Manager provides some sample roles that you can copy and apply to your business units to create your security segmentation. The roles control access to data and user interface (menus, grid views, and forms) across the application.
| Security role | Usage purpose | Security scope |
|---|---|---|
| Sustainability all – full access | RW access for all areas and data | Organization |
| Sustainability all – read only | RO access for all areas and data | Organization |
| Sustainability all – ingest – full access role | Access for ingestion actions | Organization |
| Sustainability all – reports – full access role | Access to view and edit reports | Organization |
| Sustainability BusinessUnit – full access role | RW access for all areas - Data view is restricted to business unit scope | Business unit |
| Sustainability BusinessUnit – ingest – full access role | Access for ingestion actions only - Data view is restricted to business unit scope | Business unit |
| Sustainability BusinessUnit – read only role | RO access for all areas - Data view is restricted to business unit scope | Business unit |
| Sustainability BusinessUnit – reports – full access role | Access to view and edit reports - Data view is restricted to business unit scope | Business unit |
Note
When you add users, be sure they're assigned the Basic user role. This role is required for data ingestion.
Segment access by role or department
To segment your organization access by role or department, perform the following steps:
Create business units in Dataverse aligned to your organization structure. For instructions on creating business units in Dataverse, go to Create a new business unit.
Copy the roles in the table above to each business unit (or use default roles).
Assign the roles to users or groups according to required privileges.
For example, an administrator might provision roles within business units and assign users accordingly to segment access to data and user interface based on user responsibilities or sub-organization internal boundaries.
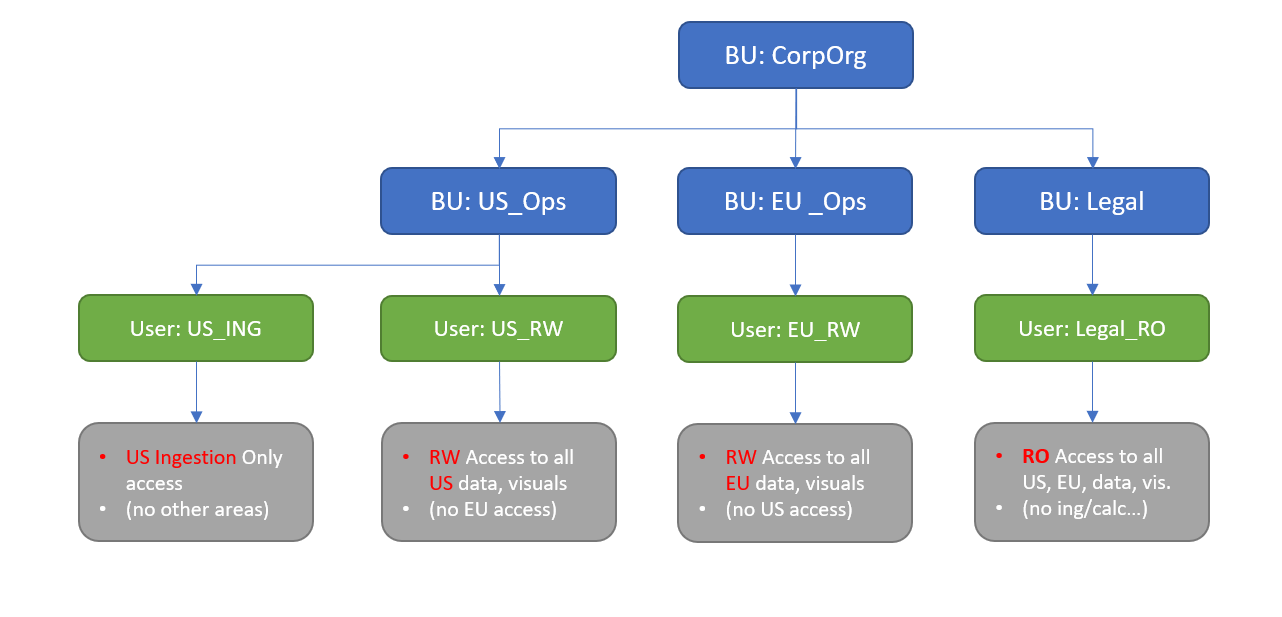
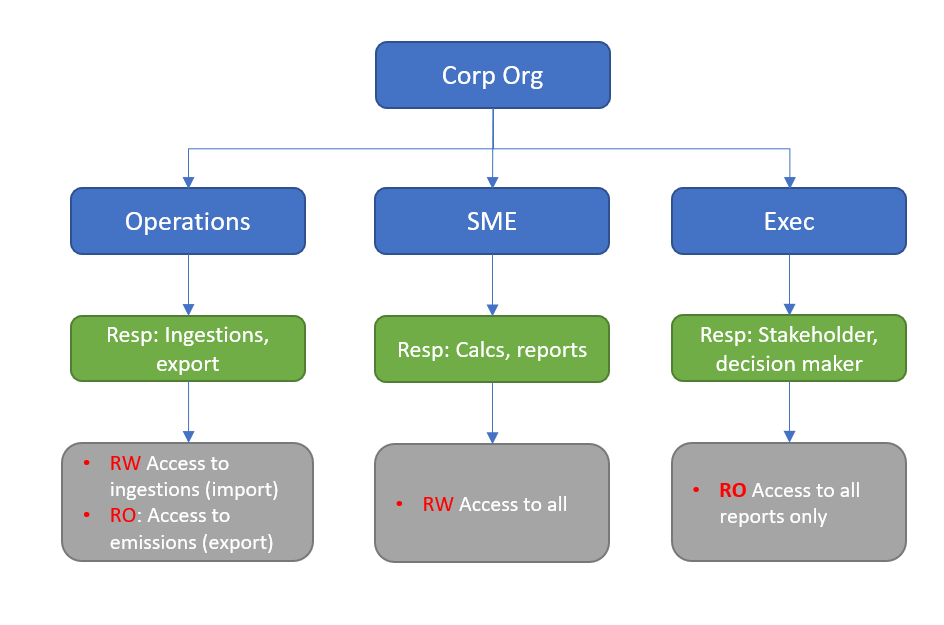
Fine tune segmentation
Important
Default business unit roles only apply to activities and emissions. Specifically, reference data is scoped at the organizational level by default. Most reference data is applicable across business unit boundaries, such as factor libraries, transport mode, or fuel type. If they're precluded from a sibling business unit, calculations would be unavailable or fail.
Some organizations require stricter segmentation, such that for example, facilities or organizational units aren't visible across business units. In this case, you can perform the following procedure to copy and edit the default roles so you can fine tune role-based user access according to your needs.
Important
Non-default roles that you create can potentially cause backend support to fail due to privilege issues. Use the following procedure with caution.
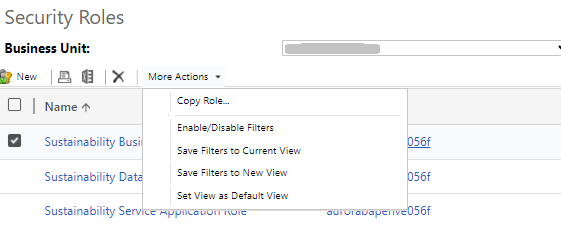
Navigate to Advanced settings > Security > Security Roles
Select the role you want to base your new role on.
Select More Actions > Copy Role.
Enter the New Role Name, and then select OK.
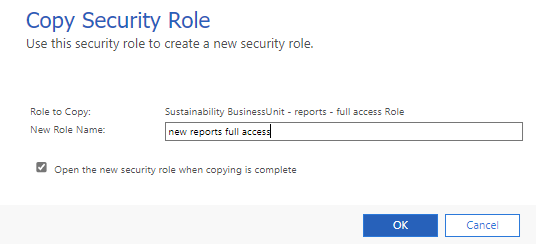
After the copy completes, open your new role, go to the Custom Entities tab, and then edit as needed.