Jamf Mobile Threat Defense connector with Intune
Control mobile device access to corporate resources using conditional access based on risk assessment conducted by Jamf. Jamf is a Mobile Threat Defense (MTD) solution that integrates with Microsoft Intune. Risk is assessed based on telemetry collected from devices by the Jamf service, including:
- Operating system vulnerabilities
- Malicious apps installed
- Malicious network profiles
- Cryptojacking
You can configure conditional access policies that are based on Jamf's risk assessment, enabled through Intune device compliance policies. Risk assessment policy can allow or block noncompliant devices from accessing corporate resources based on detected threats.
Note
In July of 2021, Jamf completed acquisition of Wandera, and more recently began rebranding and updates to move Wandera to the Jamf portfolio. Work to update the Intune admin center to reflect the new branding remains in progress. This content will reflect the new branding Jamf where possible, but continue to reflect the Wandera branding when necessary to retain accuracy to the current user interface in the admin center.
How do Intune and Jamf Mobile Threat Defense help protect your company resources?
Jamf's mobile app seamlessly installs using Microsoft Intune. This app captures file system, network stack, and device and application telemetry (where available). This information synchronizes to the Jamf cloud service to assess the device's risk for mobile threats. These risk level classifications are configurable to suit your needs in the Jamf administrator console.
The compliance policy in Intune includes a rule for MTD based on Jamf's risk assessment. When this rule is enabled, Intune evaluates device compliance with the policy that you enabled.
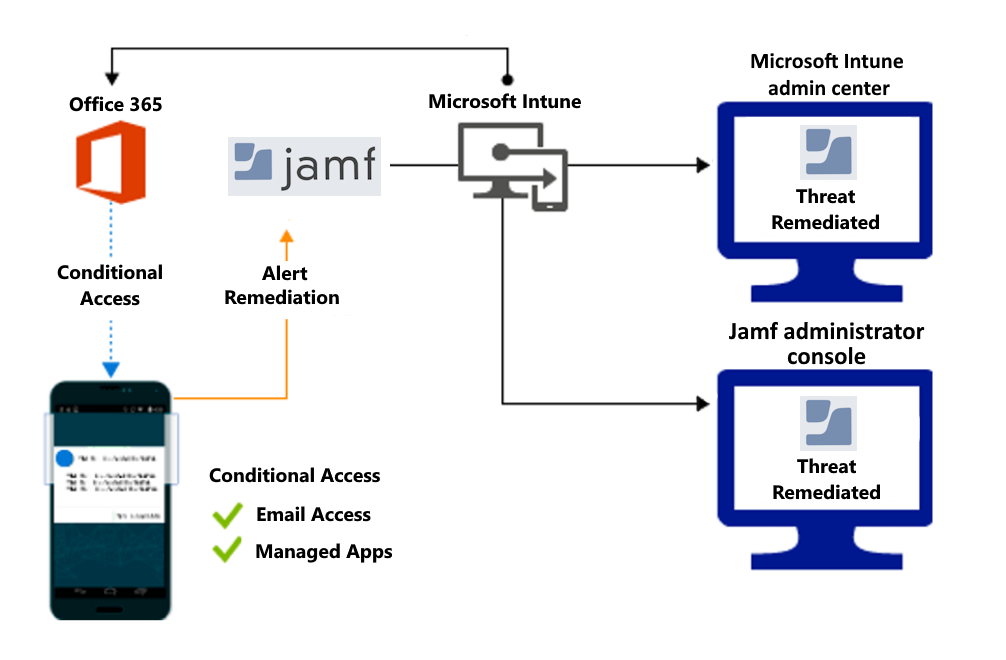
For devices that are noncompliant, access to resources like Microsoft 365 can be blocked. Users on blocked devices receive guidance from the Jamf app to resolve the issue and regain access.
Jamf updates Intune with each device’s latest threat level (Secure, Low, Medium, or High) whenever it changes. This threat level is continuously recalculated by the Jamf Security Cloud and is based upon device state, network activity, and numerous mobile threat intelligence feeds across various threat categories.
These categories and their associated threat levels are configurable in Jamf Security Cloud portal such that the total calculated threat level for each device is customizable per your organization’s security requirements. With threat level in hand, there are two Intune policy types that make use of this information to manage access to corporate data:
Using Device Compliance Policies with Conditional Access, administrators set policies to automatically mark a managed device as “out of compliance” based upon the Jamf-reported threat level. This compliance flag subsequently drives Conditional Access Policies to allow or deny access to applications that utilize modern authentication. See Create Mobile Threat Defense (MTD) device compliance policy with Intune for configuration details.
Using App Protection Policies with Conditional Launch, administrators can set policies that are enforced at the native app level (for example, Android and iOS/iPad OS apps like Outlook, OneDrive, etc.) based upon the Jamf-reported threat level. These policies can also be used for unenrolled devices with MAM managed applications to provide uniform policy across all device platforms and ownership modes. See Create Mobile Threat Defense app protection policy with Intune for configuration details.
Supported platforms
The following platforms are supported for Jamf when enrolled in Intune:
- Android 9.0 and later
- iOS 13.7 and later
For more information about platform and device, see the Jamf website.
Prerequisites
- Microsoft Intune Plan 1 subscription
- Microsoft Entra ID
- Jamf Mobile Threat Defense
For more information, see Jamf Mobile Security.
Sample scenarios
Here are the common scenarios when using Jamf MTD with Intune.
Control access based on threats from malicious apps
When malicious apps such as malware are detected on devices, you can block devices from common tools until you can resolve the threat. Common blocks include:
- Connecting to corporate e-mail
- Syncing corporate files with the OneDrive for Work app
- Accessing company apps
Block when malicious apps are detected:
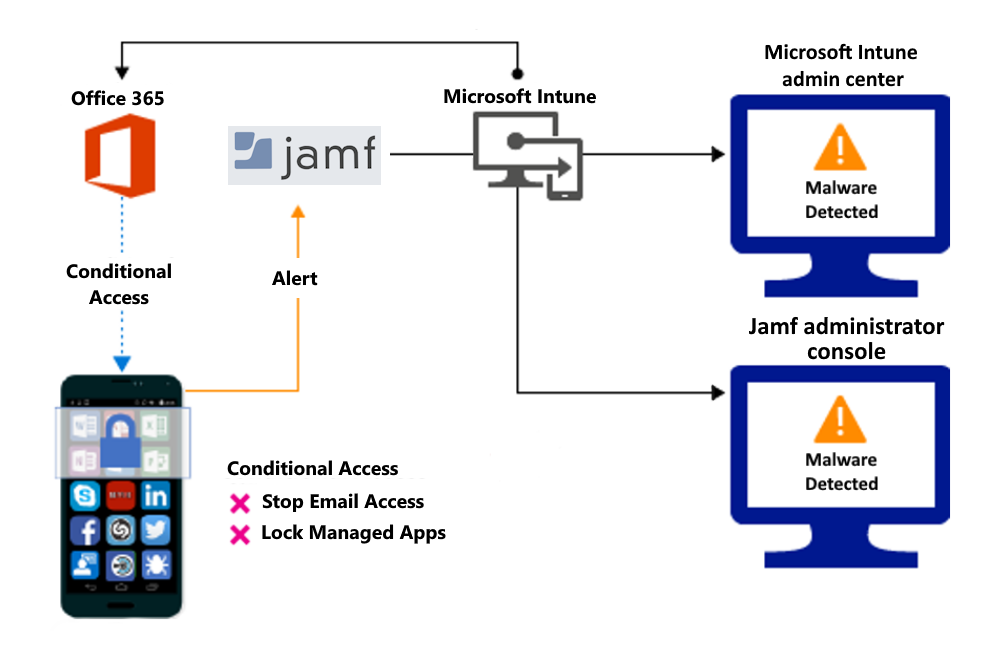
Access granted on remediation:
Control access based on threat to network
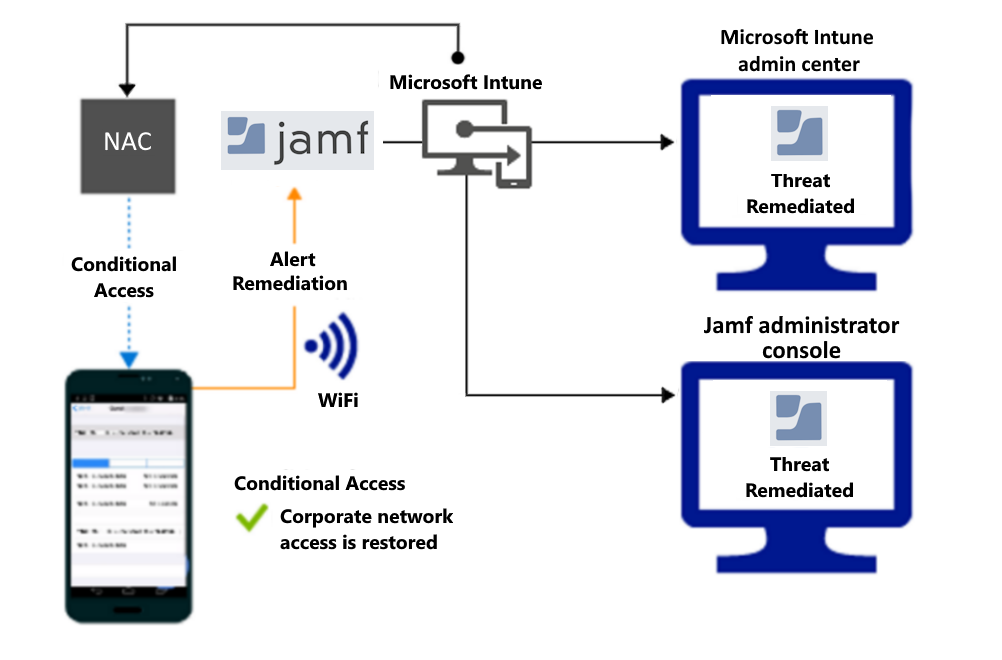
Detect threats to your network such as man-in-the-middle attacks and protect access to Wi-Fi networks based on the device risk.
Block network access through Wi-Fi:
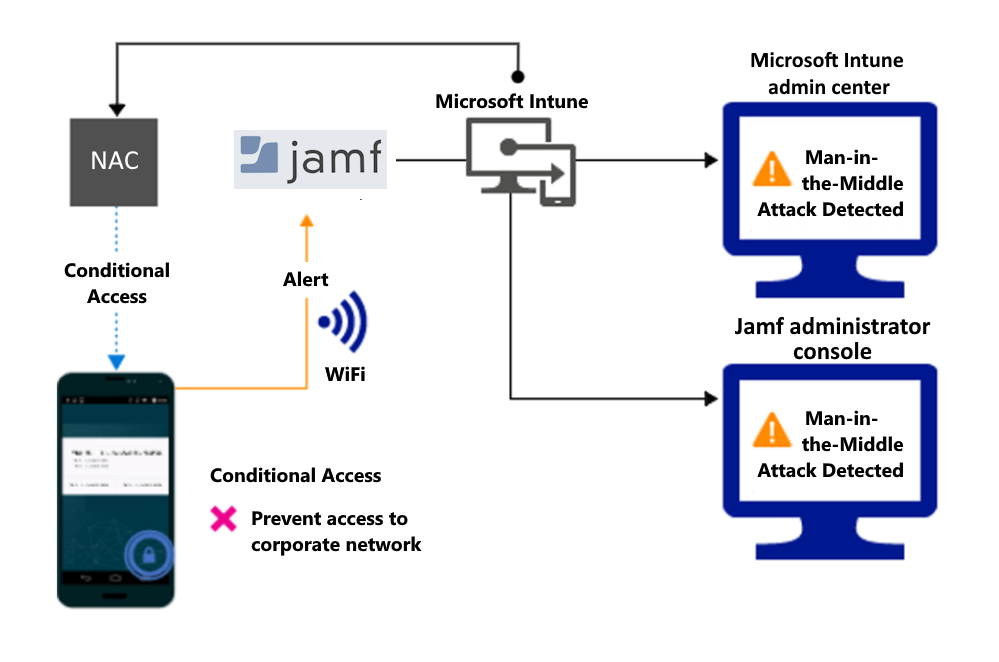
Access granted on remediation:
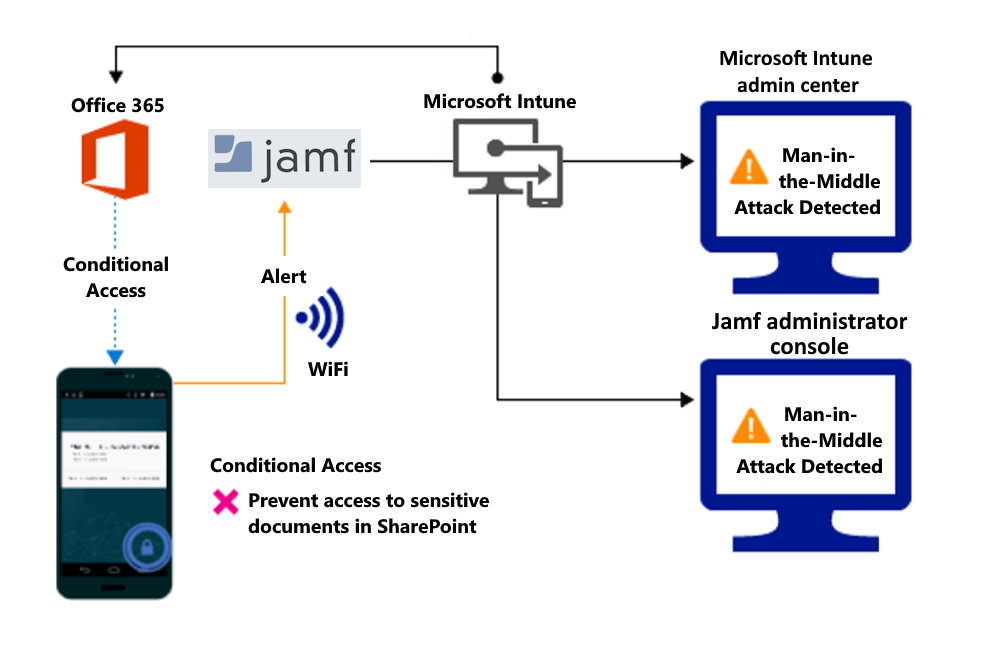
Control access to SharePoint Online based on threat to network
Detect threats to your network such as Man-in-the-middle attacks, and prevent synchronization of corporate files based on the device risk.
Block SharePoint Online when network threats are detected:
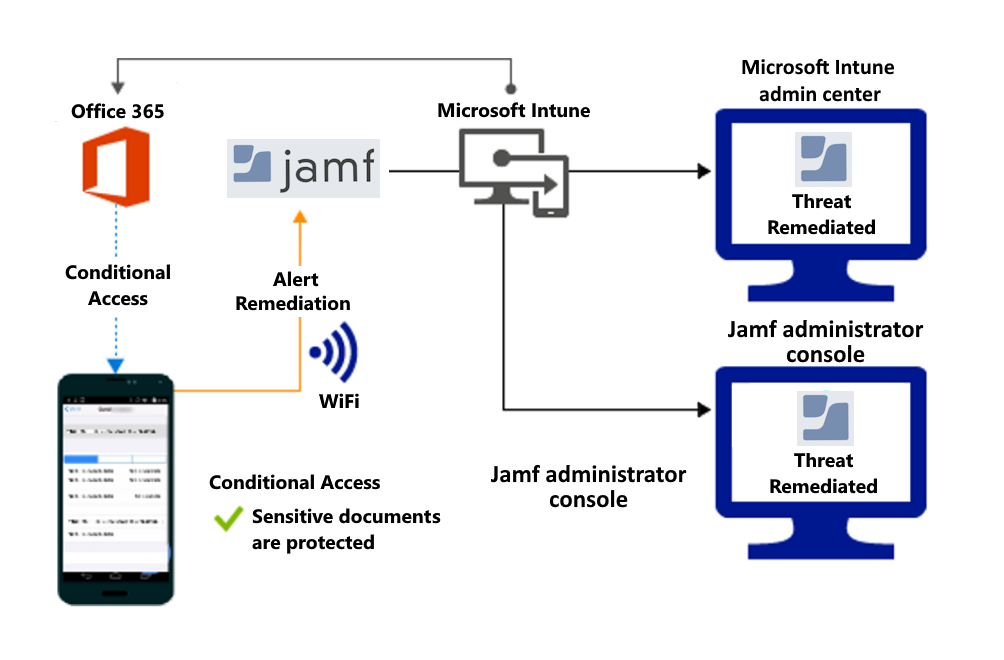
Access granted on remediation:
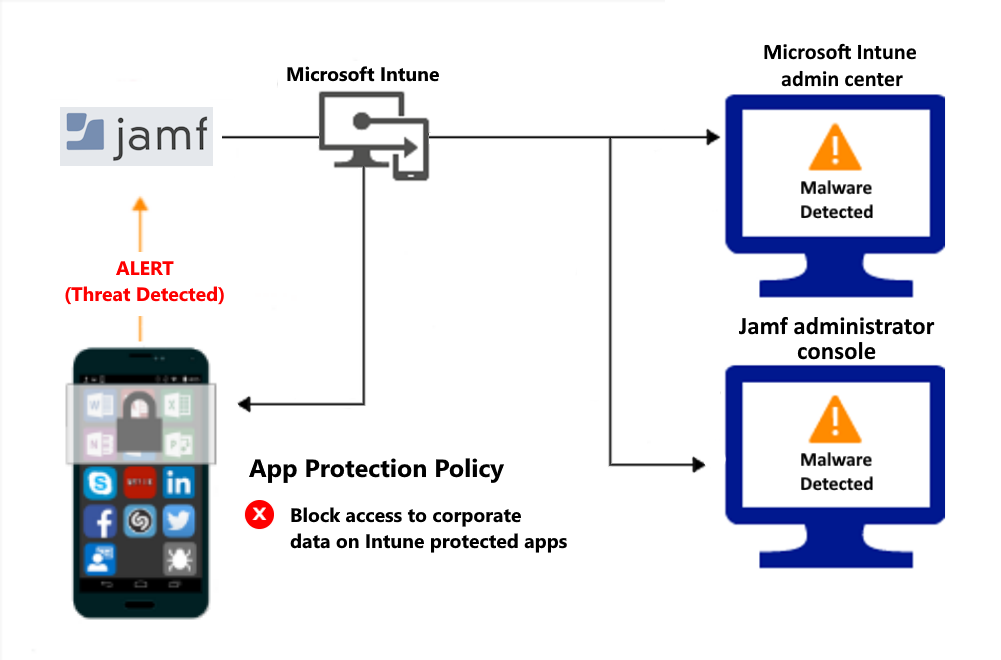
Control access on unenrolled devices based on threats from malicious apps
When the Jamf Mobile Threat Defense solution considers a device to be infected:
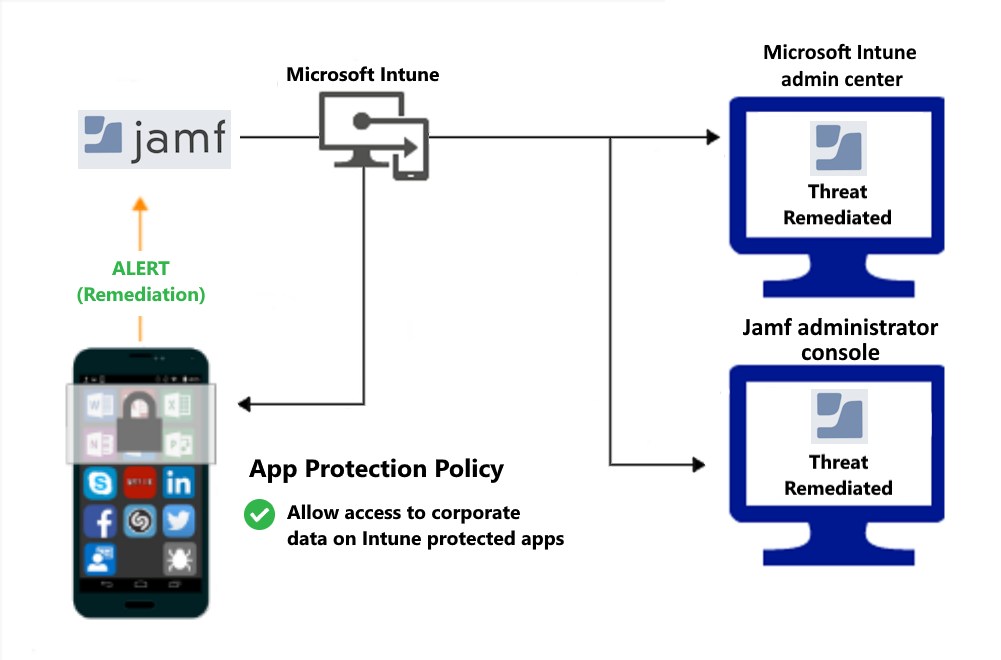
Access is granted on remediation:
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for