Block vulnerable applications
Applies to:
- Microsoft Defender Vulnerability Management
- Microsoft Defender XDR
- Microsoft Defender for Servers Plan 2
Note
To use this feature you'll require Microsoft Defender Vulnerability Management Standalone or if you're already a Microsoft Defender for Endpoint Plan 2 customer, the Defender Vulnerability Management add-on.
Remediating vulnerabilities takes time and can be dependent on the responsibilities and resources of the IT team. Security admins can temporarily reduce the risk of a vulnerability by taking immediate action to block all currently known vulnerable versions of an application, until the remediation request is completed. The block option gives IT teams time to patch the application without security admins worrying that the vulnerabilities will be exploited in the meantime.
While taking the remediation steps suggested by a security recommendation, security admins with the proper permissions can perform a mitigation action and block vulnerable versions of an application. File indicators of compromise (IOC)s are created for each of the executable files that belong to vulnerable versions of that application. Microsoft Defender Antivirus then enforces blocks on the devices that are in the specified scope.
Tip
Did you know you can try all the features in Microsoft Defender Vulnerability Management for free? Find out how to sign up for a free trial.
Block or warn mitigation action
The block action is intended to block all installed vulnerable versions of the application in your organization from running. For example, if there's an active zero-day vulnerability you can block your users from running the affected software while you determine work-around options.
The warn action is intended to send a warning to your users when they open vulnerable versions of the application. Users can choose to bypass the warning and access the application for subsequent launches.
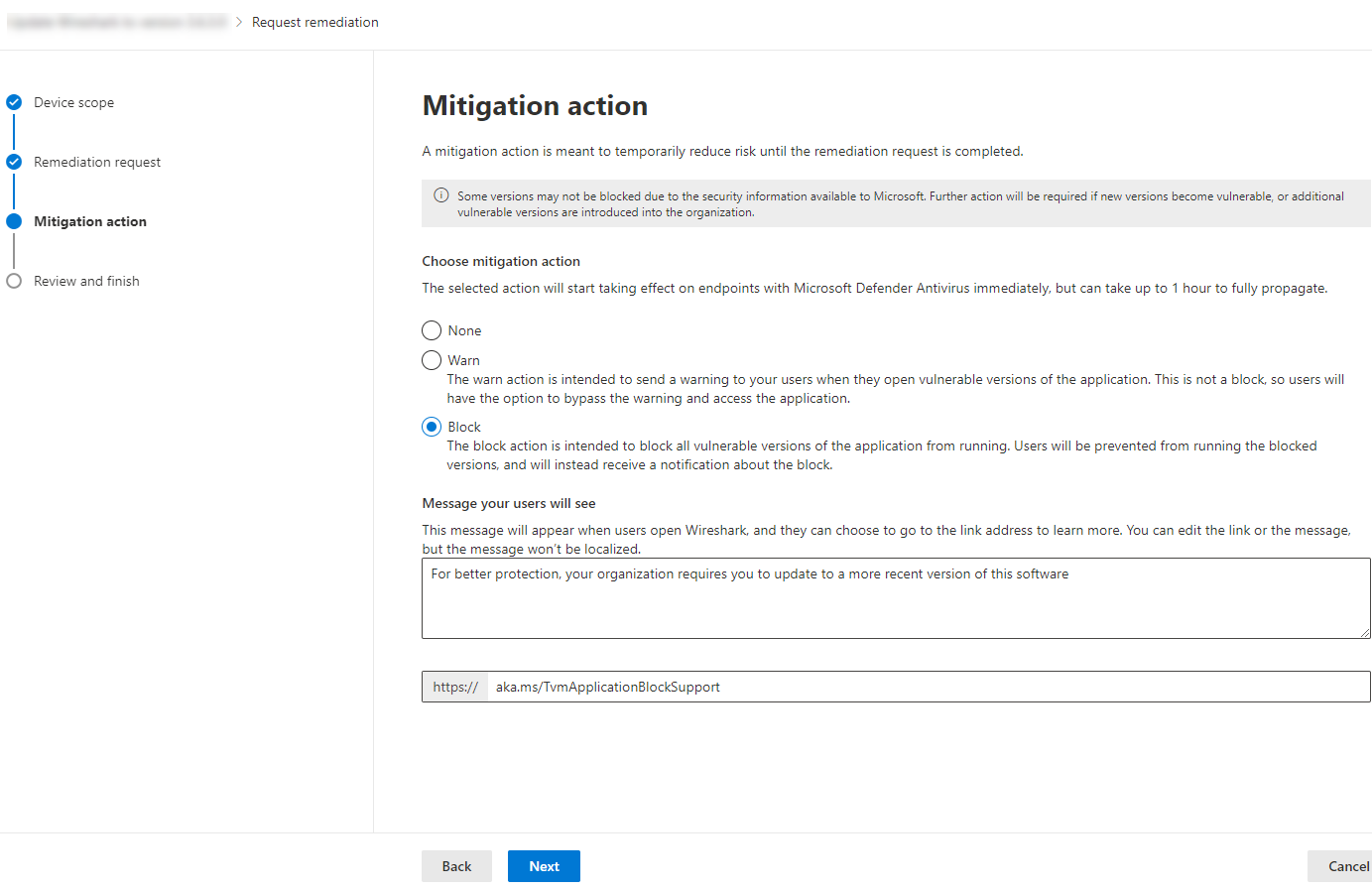
For both actions, you can customize the message the users see. For example, you can encourage them to install the latest version. Additionally, you can provide a custom URL the users navigate to when they select the notification. Note that the user must select the body of the toast notification in order to navigate to the custom URL. This can be used to provide additional details specific to the application management in your organization.
Note
The block and warn actions are typically enforced within a couple of minutes but can take up to 3 hours.
Minimum requirements
- Microsoft Defender Antivirus (active mode): The detection of file execution events and blocking requires Microsoft Defender Antivirus to be enabled in active mode. By design, passive mode and EDR in block mode can't detect and block based on file execution. To learn more, see deploy Microsoft Defender Antivirus.
- Cloud-delivered protection (enabled): For more information, see Manage cloud-based protection.
- Allow or block file (on): Go to Settings > Endpoints > Advanced features > Allow or block file. To learn more, see Advanced features.
Version requirements
- The Antimalware client version must be 4.18.1901.x or later.
- The Engine version must be 1.1.16200.x or later.
- Supported on Windows 10 devices, version 1809 or later, with the latest windows updates installed.
- Supports Windows Server versions 2022, 2019, 2016, 2012 R2, and 2008 R2 SP1.
Permissions
- If you use Role-based access control (RBAC), then you need to have the Threat and vulnerability management - Application handling permission assigned.
- If you haven't turned on RBAC, you must have one of the following Microsoft Entra roles assigned: Security Administrator or Global administrator. To learn more about permissions, go to Basic permissions.
Important
Microsoft recommends that you use roles with the fewest permissions. Using lower permissioned accounts helps improve security for your organization. Global Administrator is a highly privileged role that should be limited to emergency scenarios when you can't use an existing role.
How to block vulnerable applications
Go to Vulnerability management > Recommendations in the Microsoft Defender portal.
Select a security recommendation to see a flyout with more information.
Select Request remediation.
Select whether you want to apply the remediation and mitigation to all device groups or only a few.
Select the remediation options on the Remediation request page. The remediation options are software update, software uninstall, and attention required.
Pick a Remediation due date and select Next.
Under Mitigation action, select Block or Warn. Once you submit a mitigation action, it's immediately applied.
Review the selections you made and Submit request. On the final page, you can choose to go directly to the remediation page to view the progress of remediation activities and see the list of blocked applications.
Important
Based on the available data, the block action will take effect on endpoints in the organization that have Microsoft Defender Antivirus. Microsoft Defender for Endpoint will make a best attempt effort of blocking the applicable vulnerable application or version from running.
If additional vulnerabilities are found on a different version of an application, you get a new security recommendation, asking you to update the application, and you can choose to also block this different version.
When blocking isn't supported
If you don't see the mitigation option while requesting a remediation, it's because the ability to block the application is currently not supported. Recommendations that don't include mitigation actions include:
- Microsoft applications
- Recommendations related to operating systems
- Recommendations related to apps for macOS and Linux
- Apps where Microsoft doesn't have sufficient information or a high confidence to block
- Microsoft Store apps, which can't be blocked because they're signed by Microsoft
If you try to block an application and it doesn't work, you might have reached the maximum indicator capacity. If so, you can delete old indicators Learn more about indicators.
View remediation activities
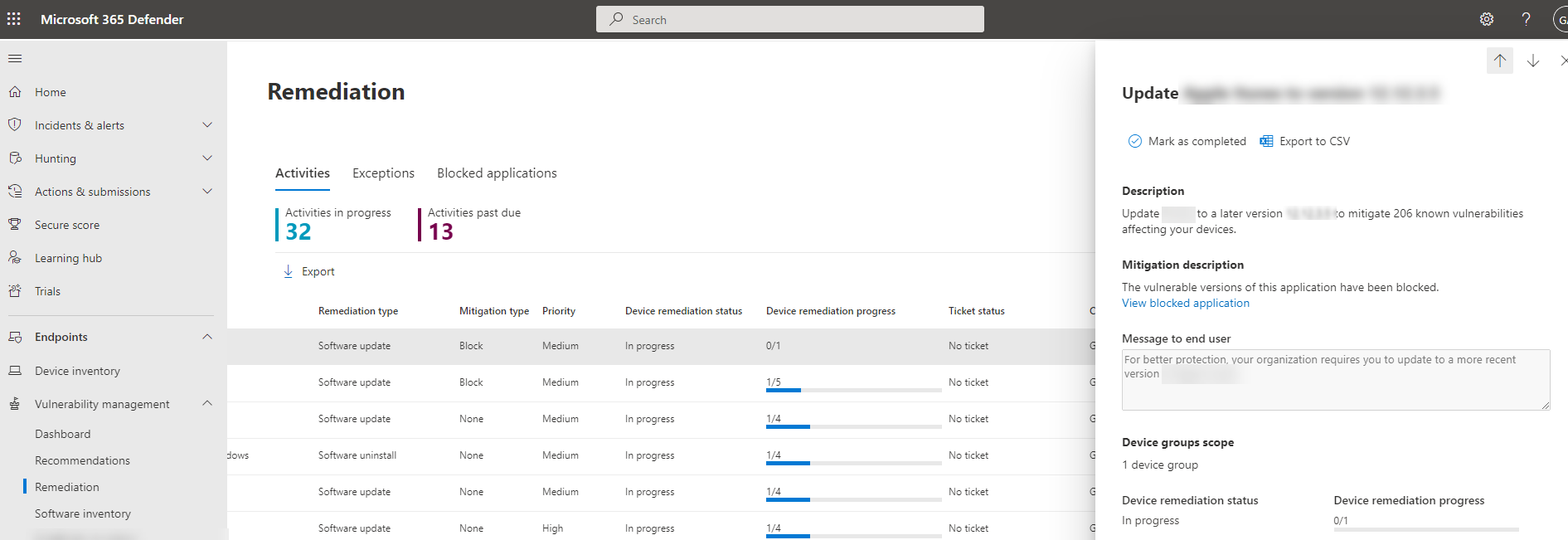
After you've submitted the request, go to Vulnerability management > Remediation > Activities to see the newly created remediation activity.
Filter by Mitigation type: Block and/or Warn to view all activities pertaining to block or warn actions.
This is an activity log, and not the current block status of the application. Select the relevant activity to see a flyout panel with details including the remediation description, mitigation description and the device remediation status:
View blocked applications
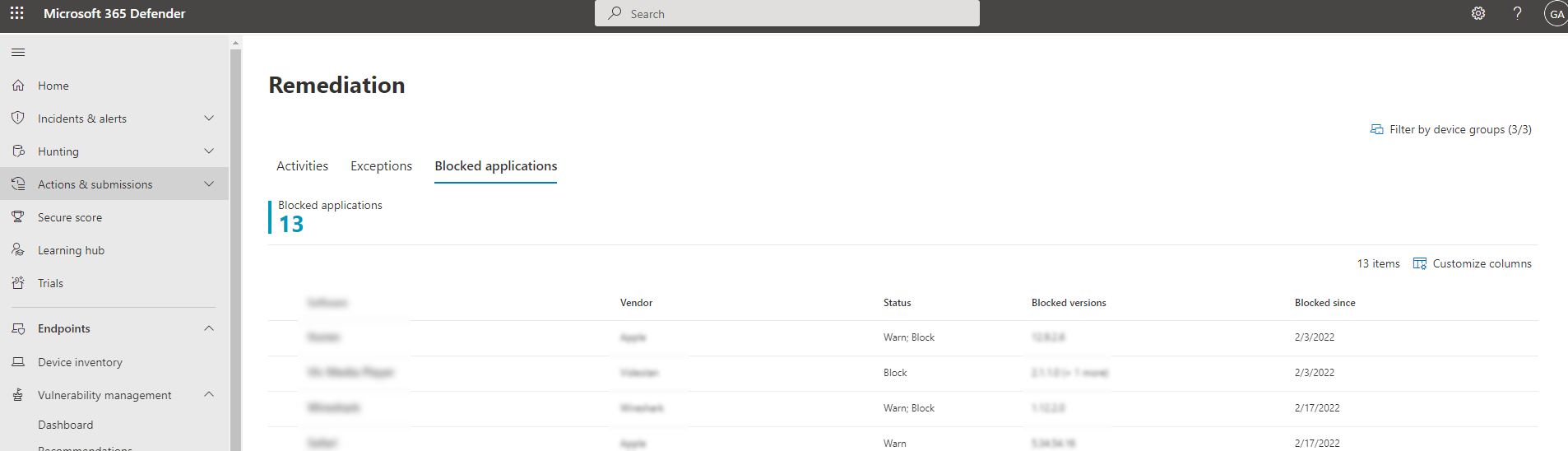
Find the list of blocked applications by going to Remediation > Blocked applications tab:
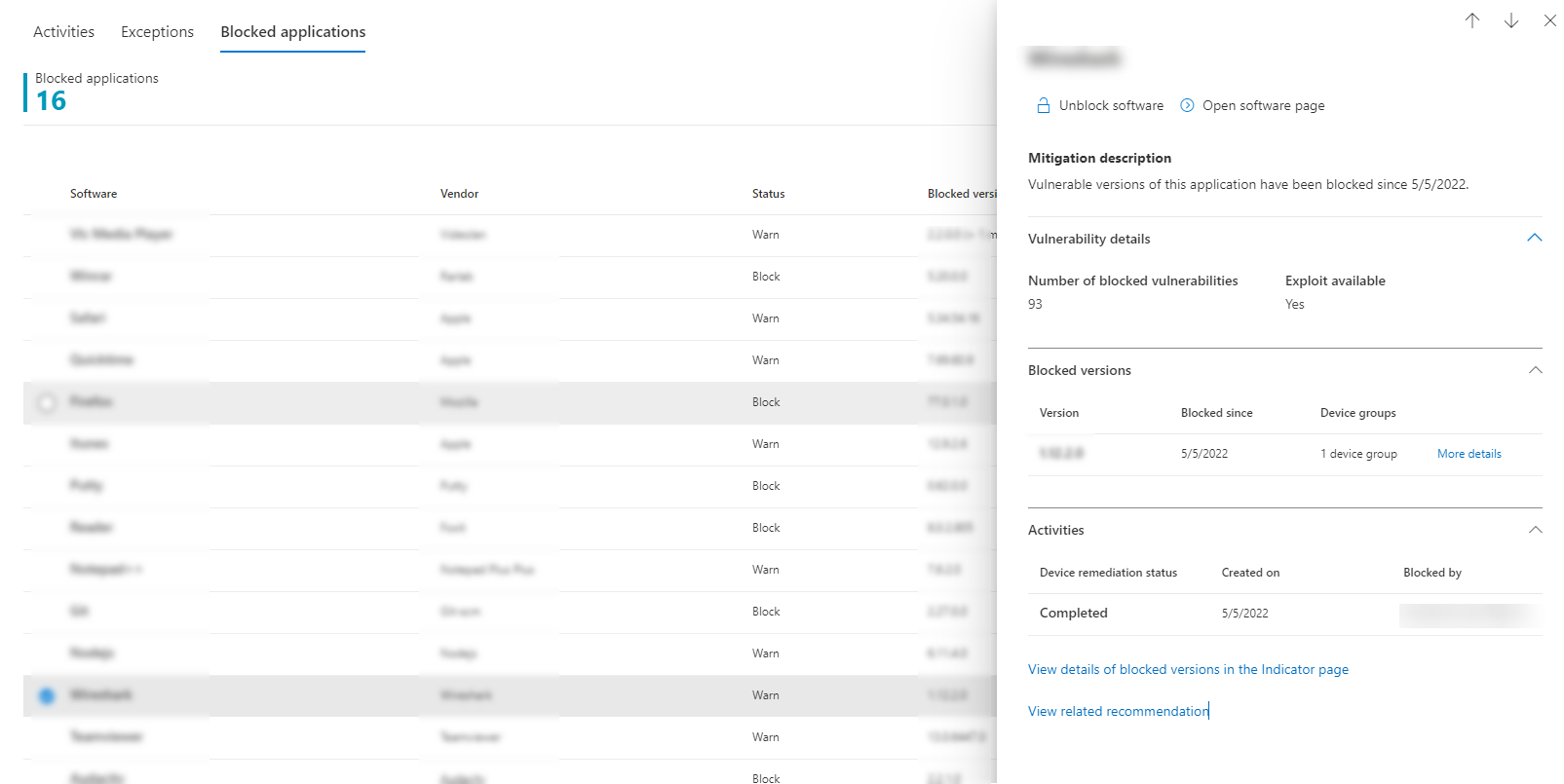
Select a blocked application to view a flyout with details about the number of vulnerabilities, whether exploits are available, blocked versions, and remediation activities.
The option to View details of blocked versions in the Indicator page brings you to the Settings > Endpoints > Indicators page where you can view the file hashes and response actions.
Note
If you use the Indicators API with programmatic indicator queries as part of your workflows, be aware that the block action will give additional results.
Currently some detections related to warn policies may show up as active malware in Microsoft Defender XDR and/or Microsoft Intune. This behavior will be fixed in an upcoming release.
You can also Unblock software or Open software page:
Unblock applications
Select a blocked application to view the option to Unblock software in the flyout.
After you've unblocked an application, refresh the page to see it removed from the list. It can take up to 3 hours for an application to be unblocked and become accessible to your users again.
Users experience for blocked applications
When users try to access a blocked application, they receive a message informing them that the application was by their organization. This message is customizable.
For applications where the warn mitigation option was applied, users receive a message informing them that the application has been blocked by their organization. The user has the option to bypass the block for subsequent launches, by choosing "Allow". This allow is only temporary, and the application will be blocked again after a while.
Note
If your organization has deployed the DisableLocalAdminMerge group policy, you may experience instances where allowing an application does not take effect. This behavior will be fixed in an upcoming release.
End-user updating blocked applications
A commonly asked question is how does an end-user update a blocked application? The block is enforced by blocking the executable file. Some applications, such as Firefox, rely on a separate update executable, which won't be blocked by this feature. In other cases when the application requires the main executable file to update, it's recommended to either implement the block in warn mode (so that the end-user can bypass the block) or the end-user can delete the application (if no vital information is stored on the client) and reinstalls the application.