Vulnerable components
Applies to:
- Microsoft Defender Vulnerability Management
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
- Microsoft Defender for Servers Plan 1 & 2.
Important
Some information in this article relates to a prereleased product which may be substantially modified before it's commercially released. Microsoft makes no warranties, expressed or implied, with respect to the information provided here.
It's becoming increasingly difficult for security administrators to identify and mitigate the security and compliance risks associated with common, proprietary, and open-source software components and dependencies used in their organizations. To help address this challenge, Defender Vulnerability Management provides support to identify, report on, and recommend remediations for vulnerabilities found in components known to have had security issues in the past.
With visibility into which vulnerable components are present on a device, security administrators can focus their attention and resources on taking steps to reduce the associated risks.
Tip
Did you know you can try all the features in Microsoft Defender Vulnerability Management for free? Find out how to sign up for a free trial.
For an overview of the vulnerable components capability, watch the following video.
Navigate to the vulnerable components page
- Go to Vulnerability management > Inventories in the Microsoft Defender portal.
- Select the Vulnerable components tab.
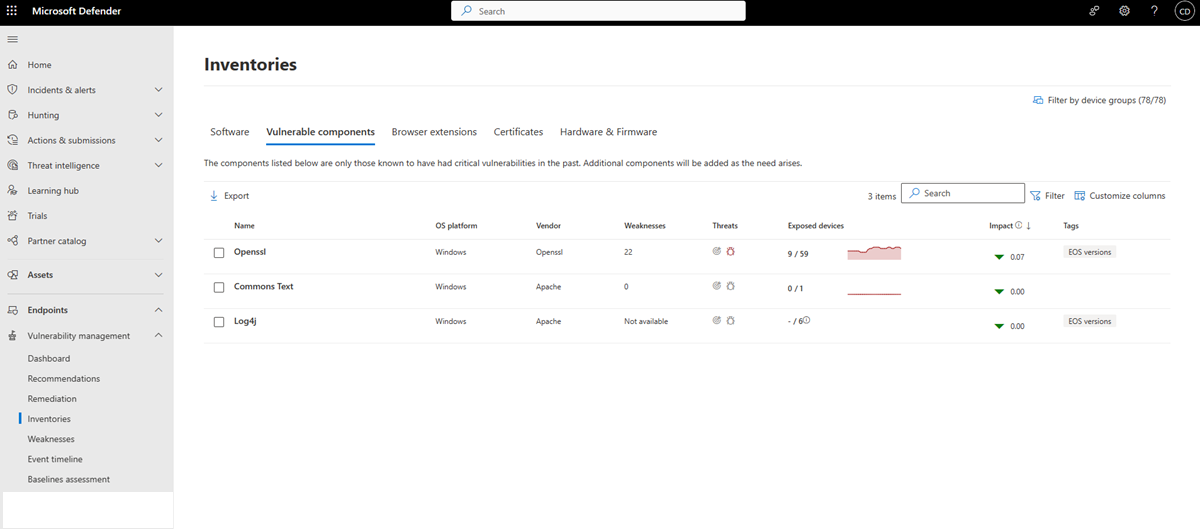
The Vulnerable components page opens with a list of known vulnerable components identified in your organization. It provides information including the component name and vendor, the number of weaknesses found for that component, and if there are active threats or alerts associated with it.
Note
Support is currently only available for the following vulnerable components:
- Apache Commons Text
- Apache Log4j
- Apache struts
- Ghostscript
- Libwebp
- LiteDB
- OpenSSL
- Spring Framework
- Tomcat
- Xz utils
Component details
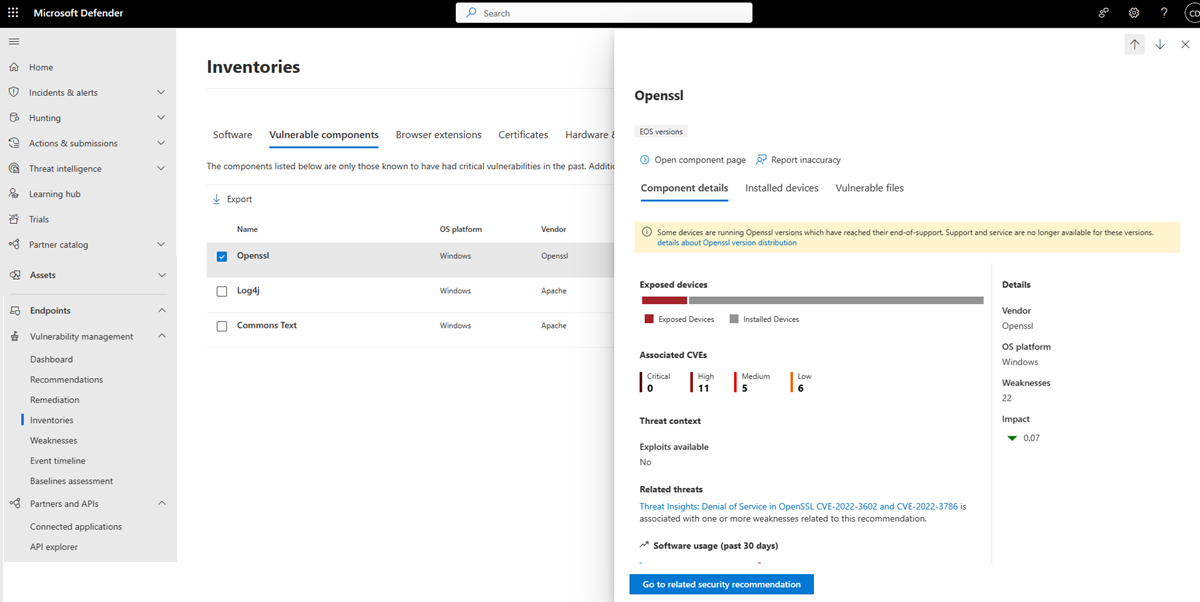
Select a vulnerable component to open a flyout pane where you'll find more information about that vulnerable component.
Select the Installed devices tab to see a list of devices the component is installed on.
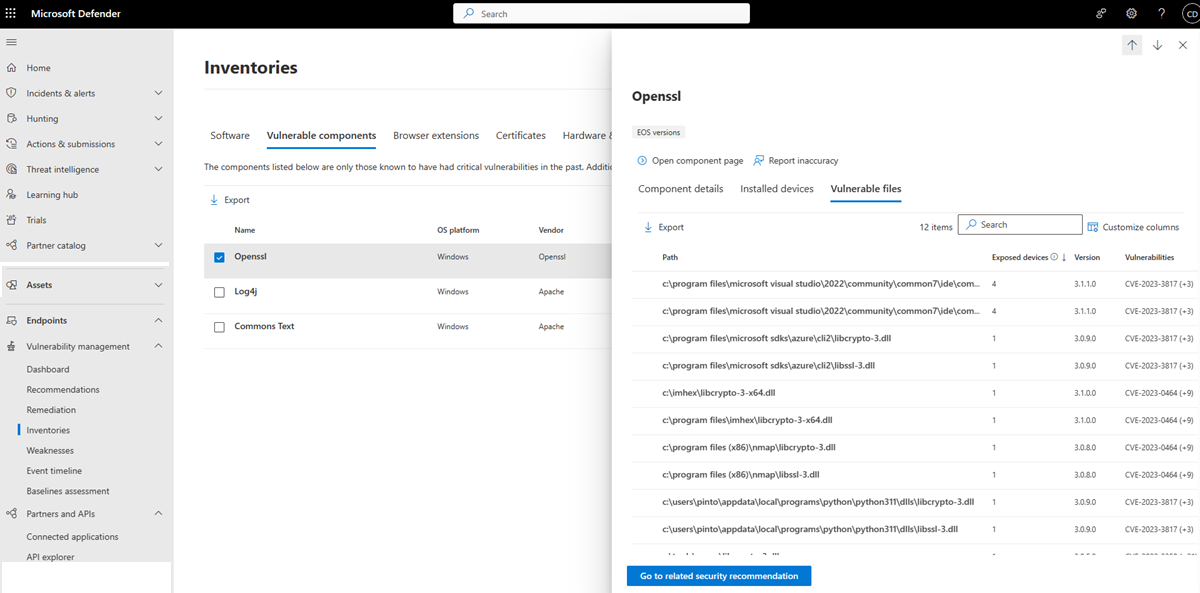
Select the Vulnerable files tab to see information on the vulnerable file paths and versions, the related vulnerabilities, and the exposed devices.
From the flyout pane, you can also dive deeper into the vulnerable component by selecting Open component page, see Vulnerable components page, or flag any technical inconsistencies by selecting Report inaccuracy, see Report inaccuracy.
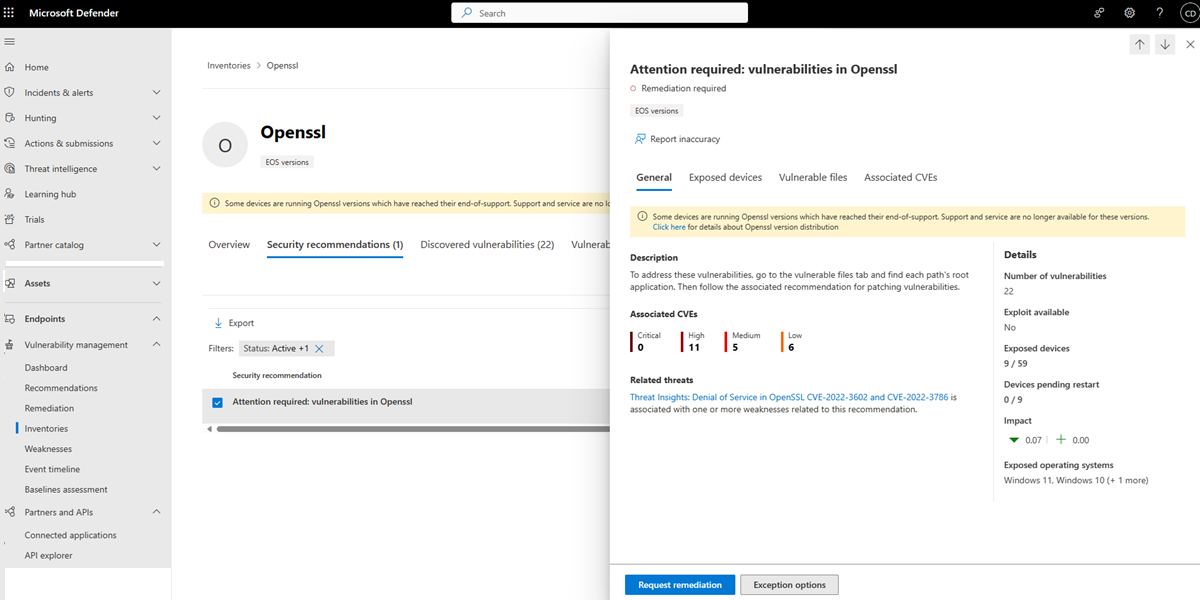
Vulnerable components page
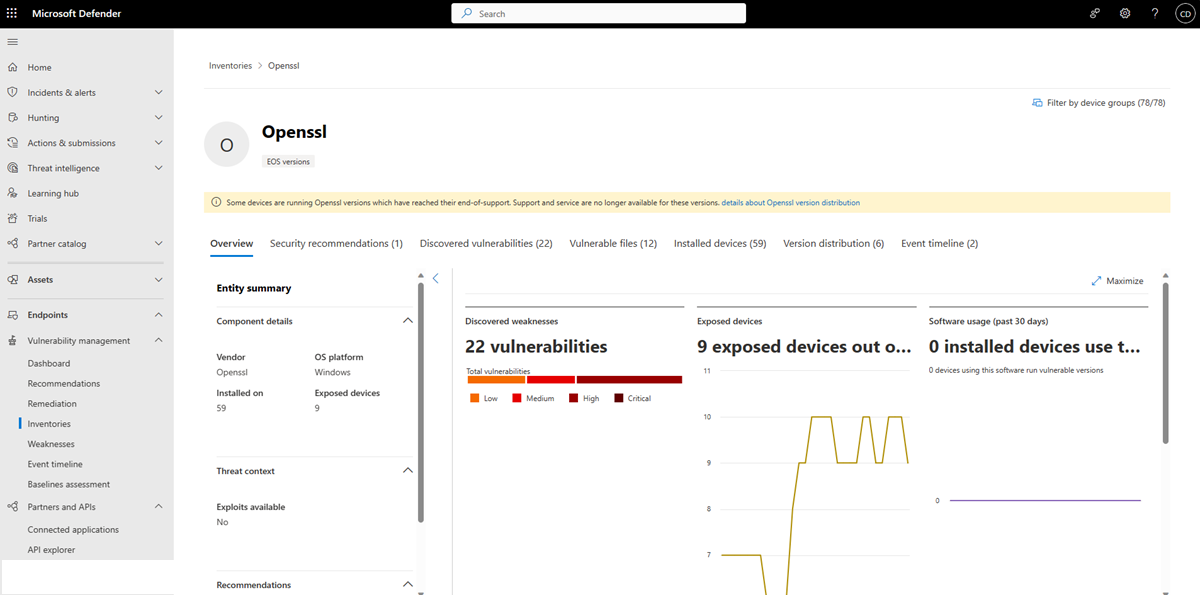
Select Open component page for a vulnerable component to see all the details for that component:
The page includes information on the component vendor, the devices the component is installed on, and data visualizations showing the number of discovered vulnerabilities and exposed devices.
Tabs are available with information specific to the vulnerable component, such as:
- Corresponding security recommendations for the vulnerabilities identified.
- Vulnerable files information including the vulnerable file paths and versions, the related vulnerabilities, along with the exposed devices.
View recommendations
To view the security recommendations for vulnerable components:
- Go to Vulnerability management > Inventories in the Microsoft Defender portal.
- Select the Vulnerable components tab.
- Select a vulnerable component and select Go to related security recommendation in the flyout pane.
Or select Open component page from the component flyout pane and select the Security recommendations tab from the component page.
When you select a security recommendation, you'll see in the flyout pane that the security recommendation is of type Attention required.
This is because there's no easy way to fix or patch a vulnerable component. The Attention required label allows security administrators to use the information about the vulnerable component to evaluate the effect of any proposed remediation on the whole organization.
Vulnerable components on devices
You can also view a list of vulnerable components on a device. With a device page open, select Inventories and then Vulnerable components to see a list of vulnerable components installed on that device.
Related articles
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for