Cluster connect access to Azure Arc-enabled Kubernetes clusters
The Azure Arc-enabled Kubernetes cluster connect feature provides connectivity to the apiserver of the cluster without requiring any inbound port to be enabled on the firewall. A reverse proxy agent running on the cluster can securely start a session with the Azure Arc service in an outbound manner.
Cluster connect allows developers to access their clusters from anywhere for interactive development and debugging. It also lets cluster users and administrators access or manage their clusters from anywhere. You can even use hosted agents/runners of Azure Pipelines, GitHub Actions, or any other hosted CI/CD service to deploy applications to on-premises clusters, without requiring self-hosted agents.
Architecture
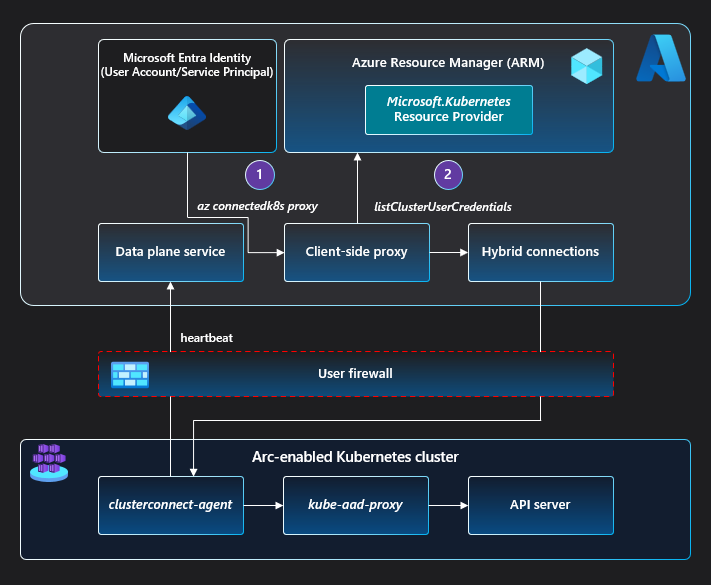
On the cluster side, a reverse proxy agent called clusterconnect-agent, deployed as part of the agent Helm chart, makes outbound calls to the Azure Arc service to establish the session.
When the user calls az connectedk8s proxy:
- The Azure Arc proxy binary is downloaded and spun up as a process on the client machine.
- The Azure Arc proxy fetches a
kubeconfigfile associated with the Azure Arc-enabled Kubernetes cluster on which theaz connectedk8s proxyis invoked.- The Azure Arc proxy uses the caller's Azure access token and the Azure Resource Manager ID name.
- The
kubeconfigfile, saved on the machine by the Azure Arc proxy, points the server URL to an endpoint on the Azure Arc proxy process.
When a user sends a request using this kubeconfig file:
- The Azure Arc proxy maps the endpoint receiving the request to the Azure Arc service.
- The Azure Arc service then forwards the request to the
clusterconnect-agentrunning on the cluster. - The
clusterconnect-agentpasses on the request to thekube-aad-proxycomponent, which performs Microsoft Entra authentication on the calling entity. - After Microsoft Entra authentication,
kube-aad-proxyuses Kubernetes user impersonation to forward the request to the cluster'sapiserver.
Next steps
- Use our quickstart to connect a Kubernetes cluster to Azure Arc.
- Access your cluster securely from anywhere using cluster connect.