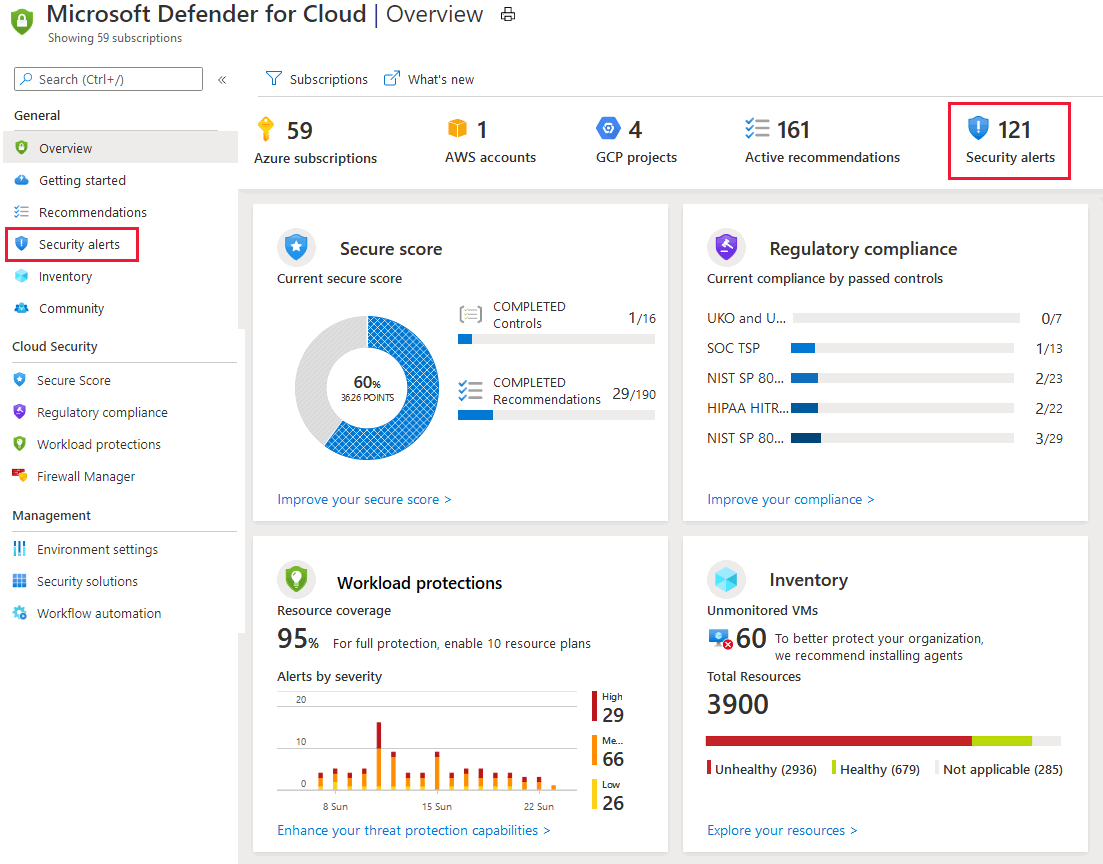
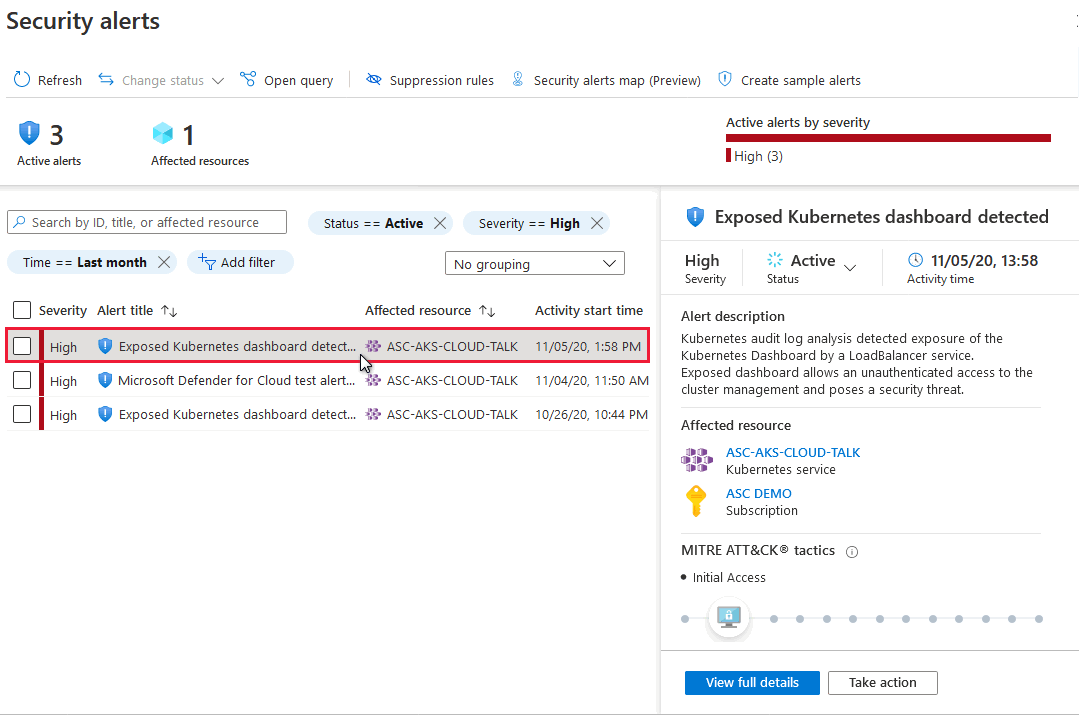
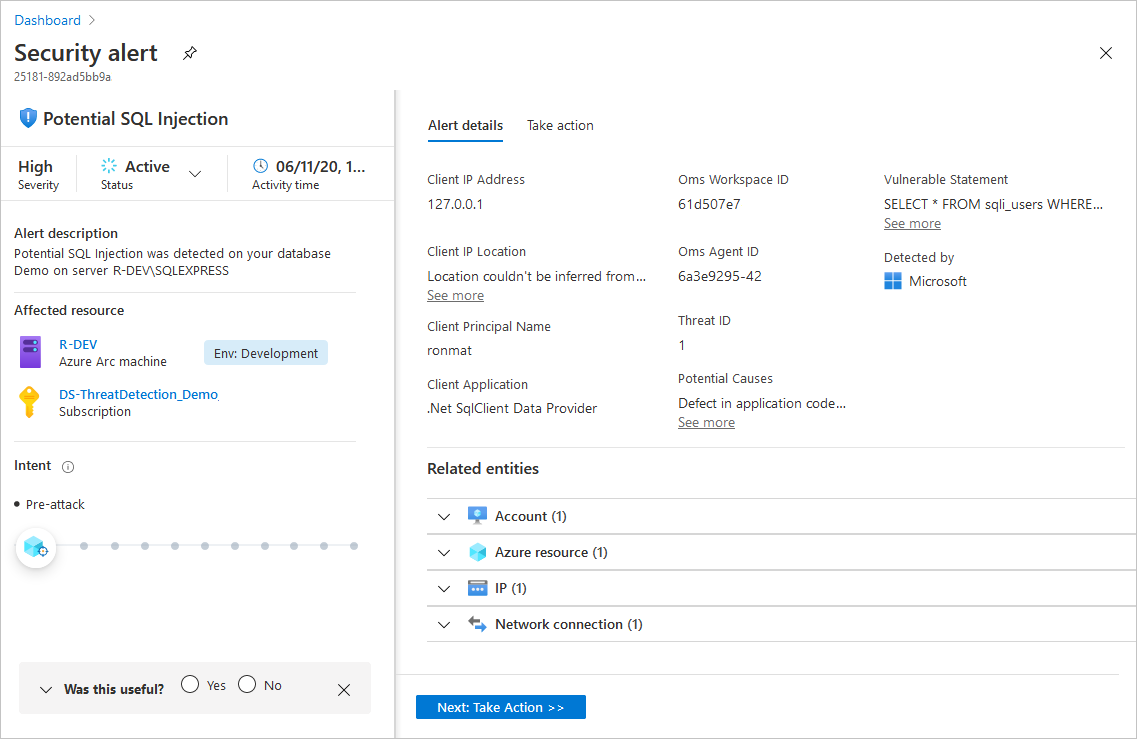
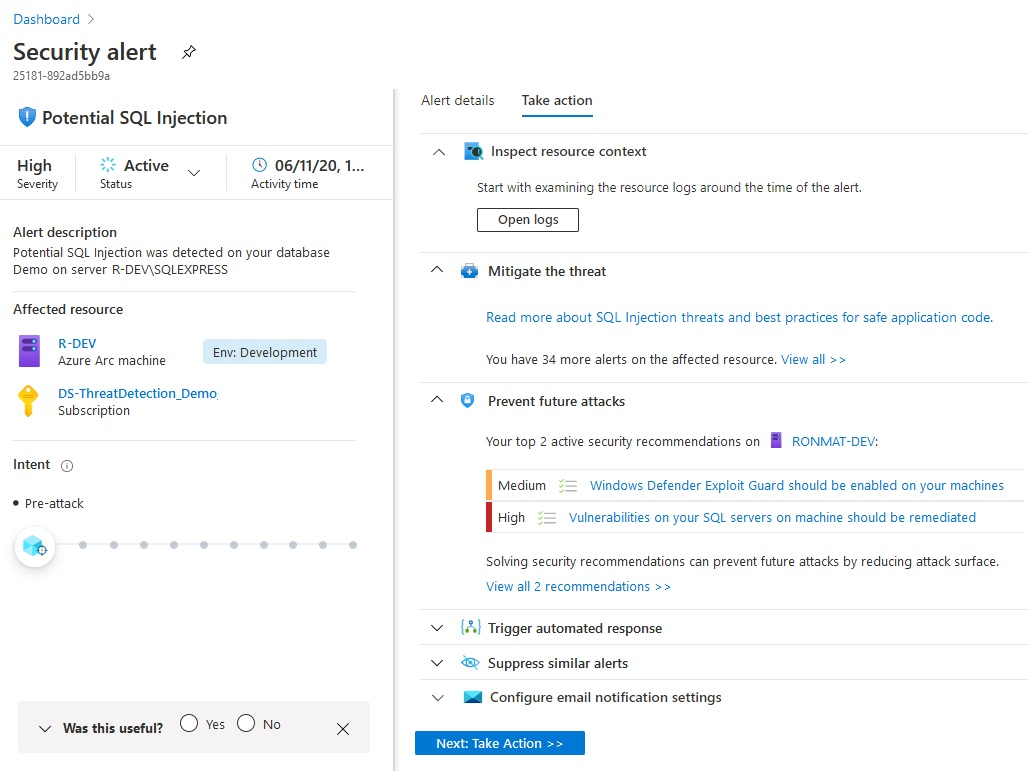
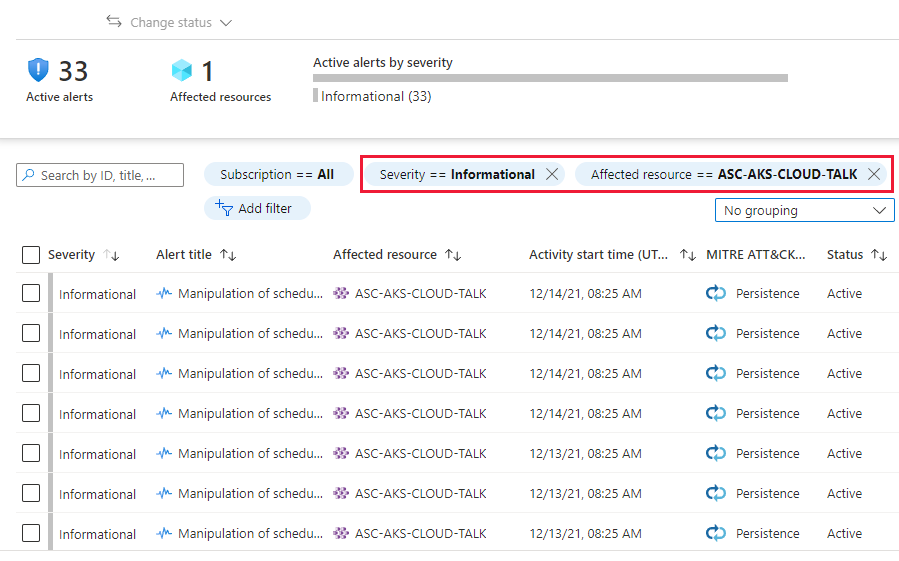
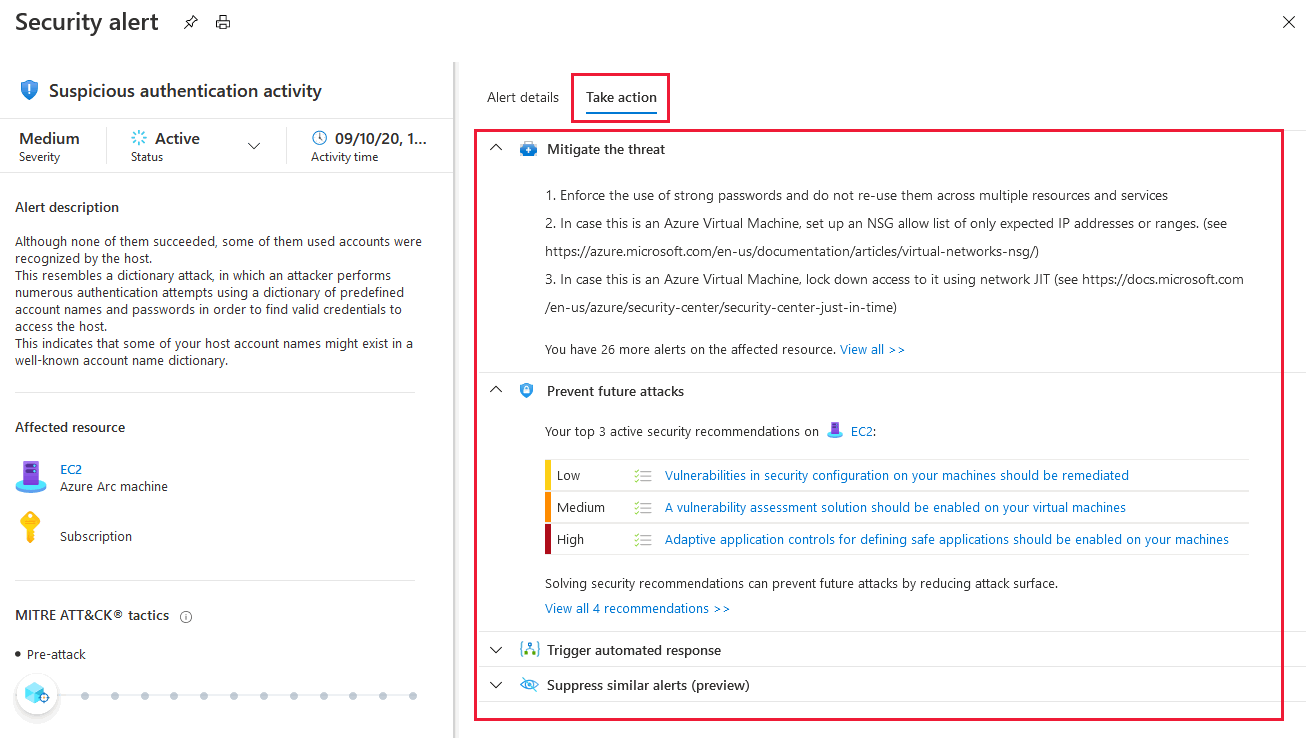
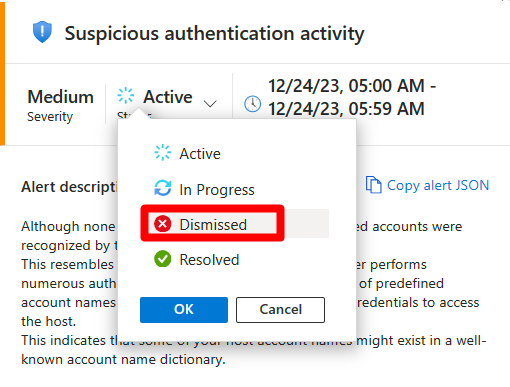
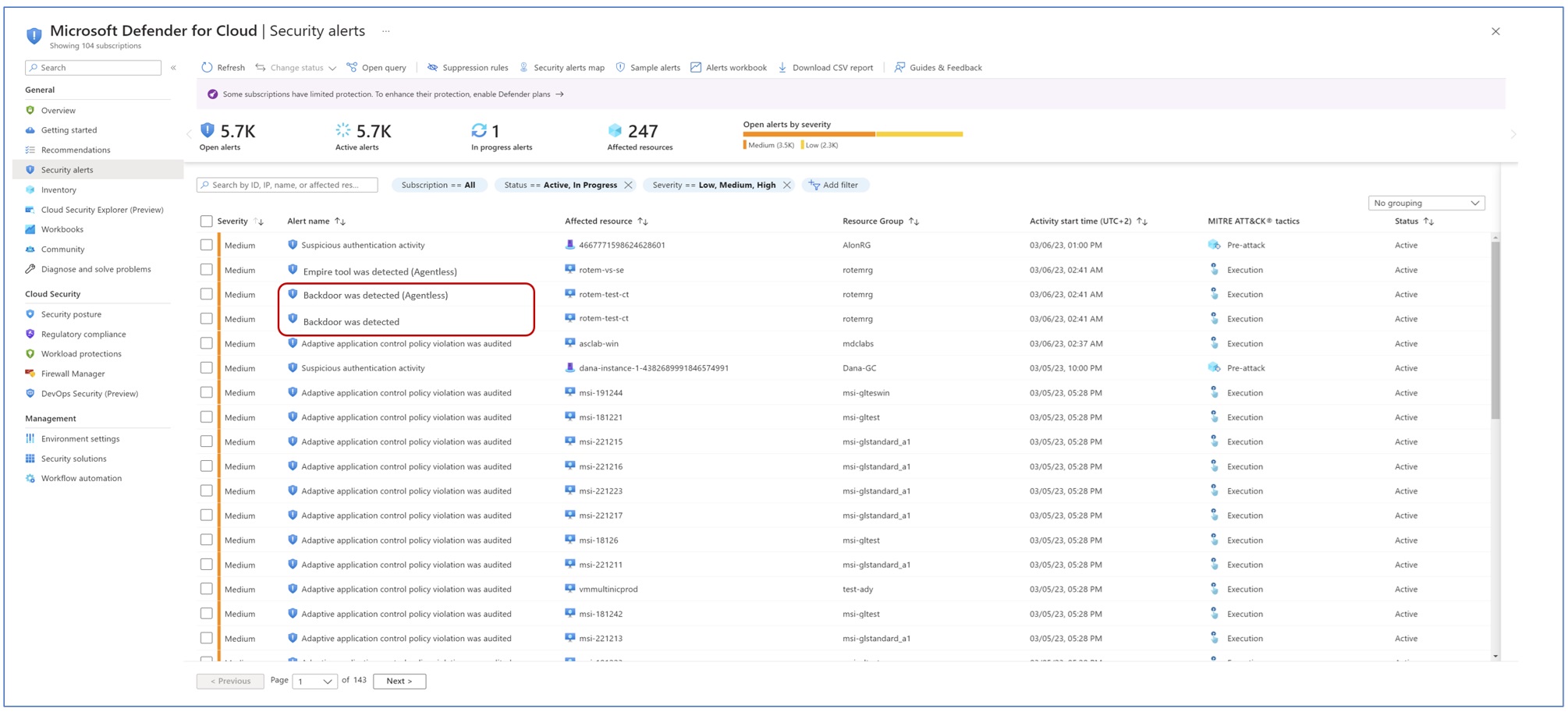
Defender for Cloud collects, analyzes, and integrates log data from your Azure, hybrid, and multicloud resources, the network, and connected partner solutions, such as firewalls and endpoint agents. Defender for Cloud uses the log data to detect real threats and reduce false positives. A list of prioritized security alerts is shown in Defender for Cloud along with the information you need to quickly investigate the problem and the steps to take to remediate an attack.
This article shows you how to view and process Defender for Cloud's alerts and protect your resources.
When triaging security alerts, you should prioritize alerts based on their alert severity, addressing higher severity alerts first. Learn more about how alerts are classified.
Tip
You can connect Microsoft Defender for Cloud to SIEM solutions including Microsoft Sentinel and consume the alerts from your tool of choice. Learn more how to stream alerts to a SIEM, SOAR, or IT Service Management solution.