Merk
Tilgang til denne siden krever autorisasjon. Du kan prøve å logge på eller endre kataloger.
Tilgang til denne siden krever autorisasjon. Du kan prøve å endre kataloger.
Important
This documentation has been retired and might not be updated. The products, services, or technologies mentioned in this content are not officially endorsed or tested by Databricks.
Azure Databricks supports Microsoft Entra ID conditional access, which allows administrators to control where and when users are permitted to sign in to Azure Databricks. For example, conditional access policies can restrict sign-in to your corporate network or can require multi-factor authentication. For more information about conditional access, see What is Conditional Access?.
This article describes how to enable conditional access for Azure Databricks.
Requirements
- This feature requires the Premium plan.
- Conditional access is available only in Microsoft Entra ID Premium. See Microsoft Entra Plans and Pricing for details.
- You must be a Conditional Access Administrator of your Microsoft Entra ID. See Microsoft Entra built-in roles for details.
Enable conditional access for Azure Databricks
In the Azure portal, click the Microsoft Entra ID service.
Click Conditional access in the SECURITY section.
Click New policy to create a new conditional access policy.
In Cloud apps, click Select apps, and then search for the application ID 2ff814a6-3304-4ab8-85cb-cd0e6f879c1d. Select AzureDatabricks.
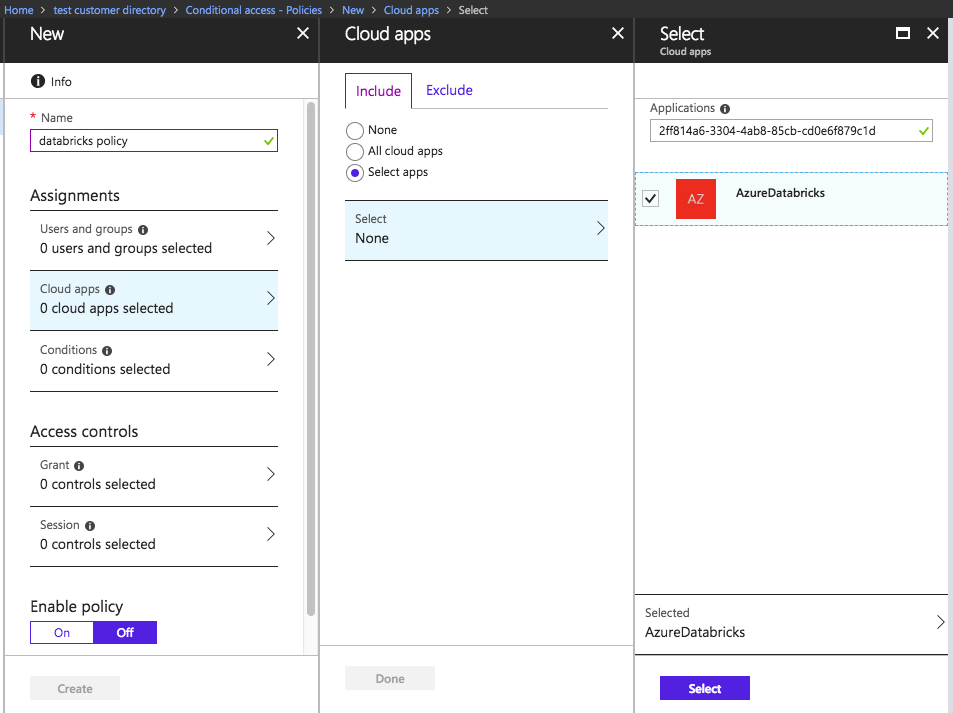
Enter the remaining settings according to your preferred conditional access configuration. See the Microsoft Entra Conditional Access documentation for tutorials and more information.